CAASM with its own powerful, proprietary active & passive discovery... not just the same old integrations.
-
Overview
The runZero Platform provides complete security visibility across IT, OT, IoT, cloud, mobile, and remote assets so that you can see and secure everything on your network.
-
Integrations
runZero seamlessly integrates with a wide variety of tools, enhancing network visibility, enriching asset data, and uncovering control gaps.
-
Community Edition
Our completely free version of the runZero Platform is ideal for home use and environments with fewer than 100 assets.
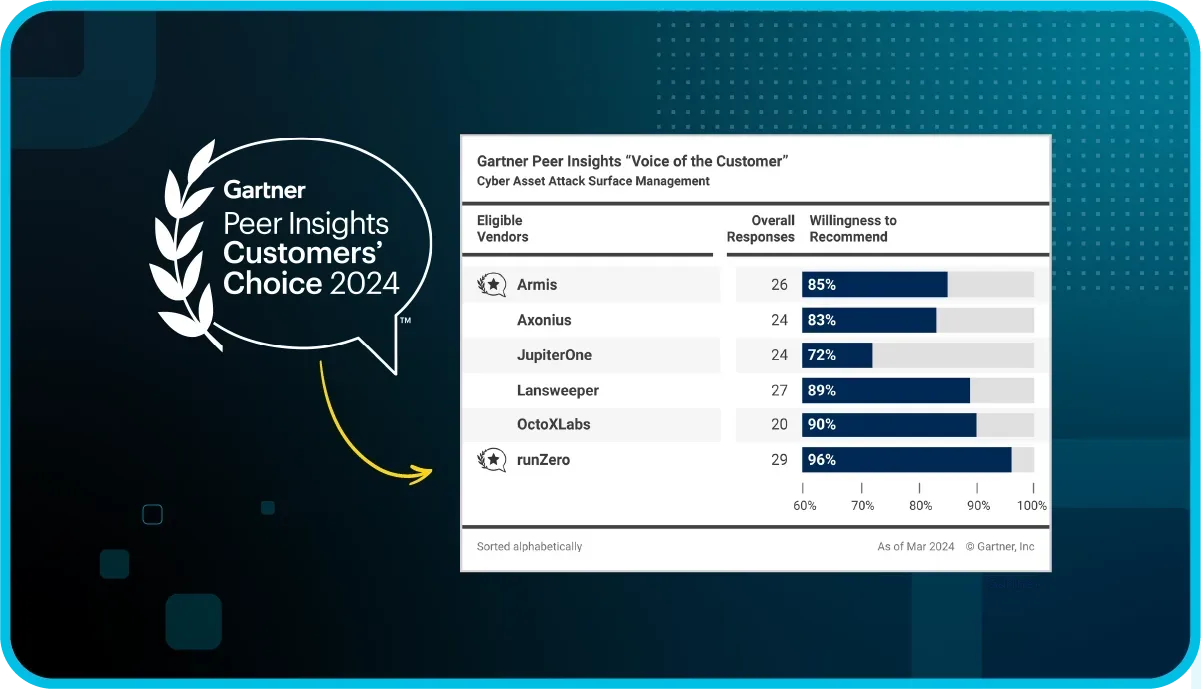
Gartner® Peer Insights™ Customers' Choice for CAASM
runZero has been recognized as a Customers’ Choice for cyber asset attack surface management (CAASM) in the 2024 Gartner Voice of the Customer report.
Explore our latest research, resources, & insights on all things exposure management.
-
runZero Blog
See what's happening at runZero and read up on the latest ideas, opinions, and articles from our experts and researchers.
-
runZero Research
Explore the world of exposure management through the runZero lens.
-
Resource Center
Dive into a treasure trove of resources to expand your exposure management knowledge.
-
Support Resources
Everything you need to maximize your experience with the runZero Platform.

SSHamble is now available!
Our researchers discovered a broad range of weaknesses across SSH implementations and applications that impact critical network security devices and software. These long standing issues have remained undiscovered due to the lack of tooling available. Enter SSHamble, our new open source tool.
See why the brands you know & love trust runZero.
-
Our Customers
Our customers are everything. We're super proud to be trusted by leading organizations around the globe to help them improve their security.
-
Case Studies
See how runZero has empowered security teams to take control of their networks, uncover their unknowns, and save significant time and money.
-
Testimonials
Read reviews of the runZero Platform and see how teams have improved their security with our technology.

New Report Published by the U.S. Department of Energy
CECA evaluations confirm runZero's active scanning enhances ICS visibility without performance impact on SCADA.
We're on a mission to create new solutions to solve persistent problems. Let's shake things up.
-
About Us
Wondering who the heck are these people? Meet the team and get the story behind runZero... once upon a time called Rumble.
-
Events
Track down runZero Yetis in the wild! Join us in-person or virtually at one of our upcoming events.
-
Investors
Meet the cybersecurity investors, trailblazers, and innovators who help us navigate our journey and the evolving security landscape.
-
Newsroom
Read the latest articles, announcements, and press releases from runZero.
-
Careers
Want to join our forces? We're looking for bright minds and passionate souls who want to write the next chapter in exposure management.

runZero Research Report: Volume 1
As a leading CAASM platform, runZero has a unique, insider’s perspective on the state of asset security. See the alarming gaps & unexpected exposures that our research team uncovered.
Believe customers always come first? Into innovation & the unconventional? We might be great partners.
-
Infinity Partner Program
See how we can work together to provide best-in-class security solutions and outcomes for our joint customers.
-
Trusted Advisor Program
Do you perform project-based consulting services and want to use runZero to deliver great insights? This program is designed for you!
-
Partner Directory
Explore our directory of trusted (and awesome) partners.
-
Partner Sign In
Sign in to our Infinity Partner Portal.

Join our Infinity Partner Program
Designed with a partner-first mindset, the runZero Infinity Partner Program offers incredibly valuable resources, relationships, and rewards to partners who choose to grow their business with us.











