Overview
Episode 2 of the runZero Hour webcast took a quick survey of new IoT devices that showed up on the network over the holidays at the end of 2023. Did you know that crockpots are now on the network?! We also took a deep dive into Transport Layer Security (TLS). The latter discussion included a look at how fingerprinting is done in general.
There are three primary ways to gather information for fingerprinting: self-identification, attribute-based, and behavior-based. Self-identification is just whatever the target responds with about itself and is typically the first step in asset identification. It’s also the naive method because:
- The target service or protocol may not support any form of self-identification.
- The “target” may be an intervening device that may modify or redact that identification.
- The target itself may respond with an incorrect identification or not granular enough to be useful.
- Sometimes, users can configure services to omit the identification.
The next two are proxy indicators, which allow you to learn something without a full and potentially intrusive examination. For example, eyeglasses are a proxy indicator telling you that someone might have vision impairment even though you didn’t perform an eye exam.
With TLS, the client sends a Client Hello with a list of protocols, ciphers, and extensions it supports. In the response, the Server Hello, the server specifies which ones it wants to use. By sending varying combinations of these options and observing which the server has selected, we can learn much about the target TLS stack.
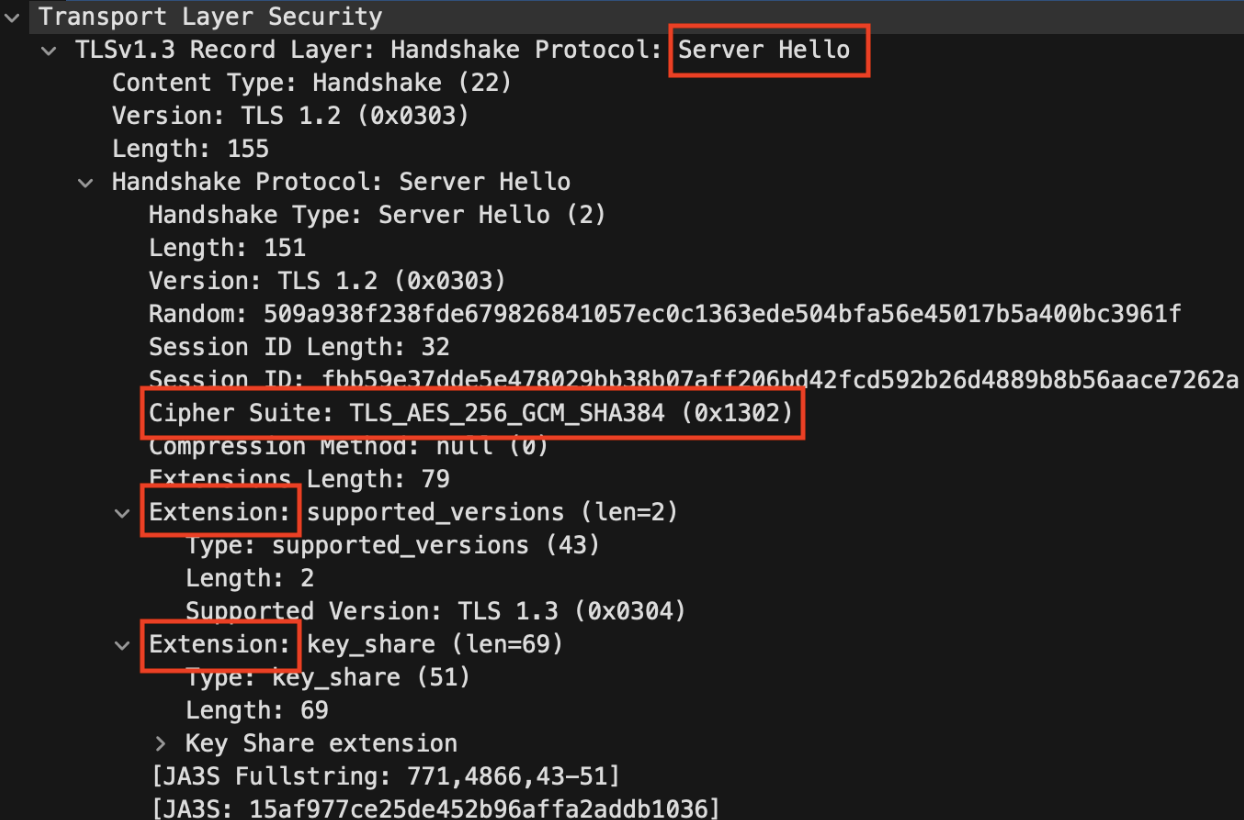
Finally, there is behavior-based, where the scanner varies its operation at the connection level to elicit tell-tale reactions from the server. Typically, when the client side of a TCP connection unexpectedly terminates, the client OS sends a TCP FIN packet–this state is known as a half-close. How does the TLS endpoint respond to half-closes? Interestingly, some versions of OpenSSL do not respond, while others respond with an TLS alert message. Other TLS stacks, such as GnuTLS, may respond with entirely different TLS alert messages. Want to know which version does which? Watch the full to find out and learn additional insights on funky protocols, oddball devices, and more in-depth details about TLS.
Get the latest news and expert insights delivered in your inbox.


















