Progress MOVEit Transfer scanning #
GreyNoise Intelligence has published a report identifying a surge in scanning activity that is targeting MOVEit Transfer systems exposed to the public Internet. The increase in scanning activity started on May 27, 2025 with near-zero activity prior to this date.
What is the impact? #
This elevated activity potentially signals an emerging threat.
Are any updates or workarounds available? #
Prioritize ensuring that MOVEit Transfer installations are running the latest version available, audit any unexpected public exposure of MOVEit Transfer, and monitor for unusual activity. Note that MOVEit Transfer zero-day exploitation is historically a favored vector for ransomware gangs, as reported by CISA and the FBI.
How do I find Progress MOVEit Transfer installations with runZero? #
From the Software Inventory, use the following query to locate potentially impacted assets:
_asset.protocol:http AND protocol:http AND vendor:="Progress Software" AND product:="MOVEit MFT"June 2024: CVE-2024-5805 and CVE-2024-5806 #
Progress software has disclosed two new vulnerabilities in the MOVEit Gateway (CVE-2024-5805) and MOVEit Transfer (CVE-2024-5806) products.
These vulnerabilities affect the SFTP (Secure File Transfer Protocol) module of the MOVEit Gateway and MOVEit Transfer products. Attackers may exploit these vulnerabilities to bypass authentication on vulnerable systems, gaining unauthorized access to these systems.
Note that these vulnerabilities further underscore the uptick in attacks on border devices described in the runZero Research Report. Attacks on this class of device have been especially prevalent recently, as they often provide high-value targets that can reveal large amounts of critical and private information to attackers.
What is the impact? #
Successful exploitation of these vulnerabilities would allow an attacker to access the vulnerable system without authentication. Note that, according to several sources including Watchtowr Labs, exploit information for this vulnerability is publicly available.
How runZero users found potentially vulnerable Progress MOVEit Gateway services #
From the Service inventory, runZero users took the following query to locate all Progress MOVEit Gateway web services across their network:
product:MOVEitJune 2023: CVE-2023-34362 #
Reports of active exploitation of a zero-day vulnerability in the MOVEit file transfer software made the rounds in June 2023. The vendor, Progress Software, released an advisory and the issue was assigned CVE-2023-34362. Attackers were abusing a SQL injection vulnerability in the web interface of MOVEit to deploy a web shell and gain access to the data stored within the platform.
What was the impact? #
Multiple security service providers, including Rapid7, reported active exploitation of this issue, with the attack resulting in the installation of a 'web shell', often accessed through the path '/human2.aspx'. Progress Software's advisory stated that users should have looked for indicators of compromise (IoCs) going back at least 30 days, indicating that this issue might have been actively exploitable for weeks and had only just come to light. A compromise of the MOVEit server could lead to full exposure of all files managed by the service, access to the user database of the service, and could provide a foothold into the organization's network, depending on network segmentation rules.
On May 31st, 2023, Progress posted an advisory, including a download link to a patch. This advisory also described some of the indicators of compromise and what paths and types of logs to look for to determine if the system was breached.
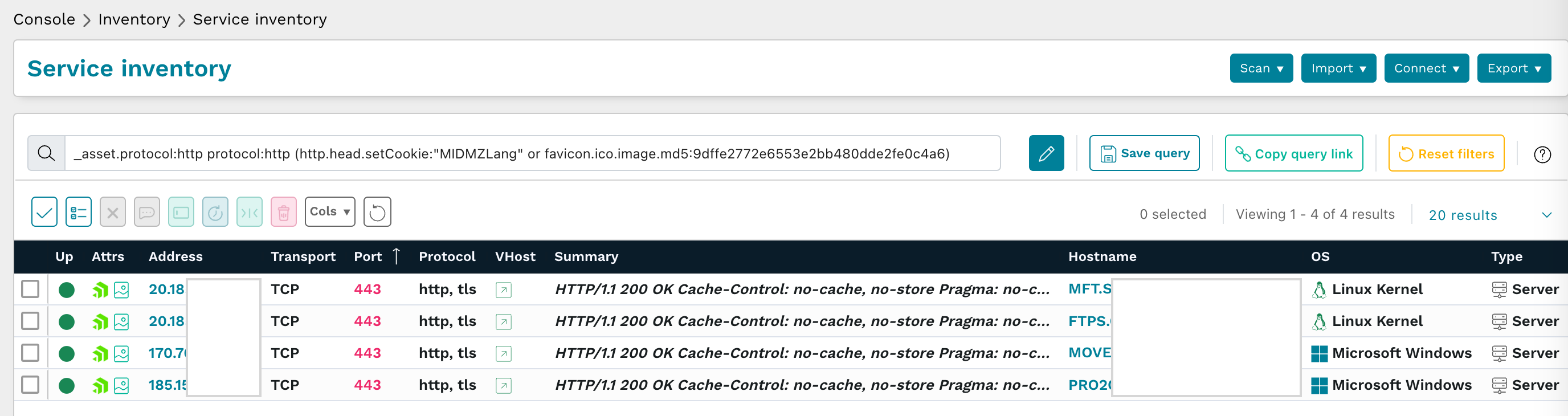
How runZero users found potentially vulnerable Progress MOVEit Managed File Transfer services #
From the Service inventory, runZero users took the following prebuilt query to locate all Progress MOVEit Managed File Transfer web services across their network:
_asset.protocol:http protocol:http (http.head.setCookie:"MIDMZLang" OR favicon.ico.image.md5:9dffe2772e6553e2bb480dde2fe0c4a6)
As always, any pre-built queries are available from your runZero console. Check out the documentation for other useful inventory queries.




















