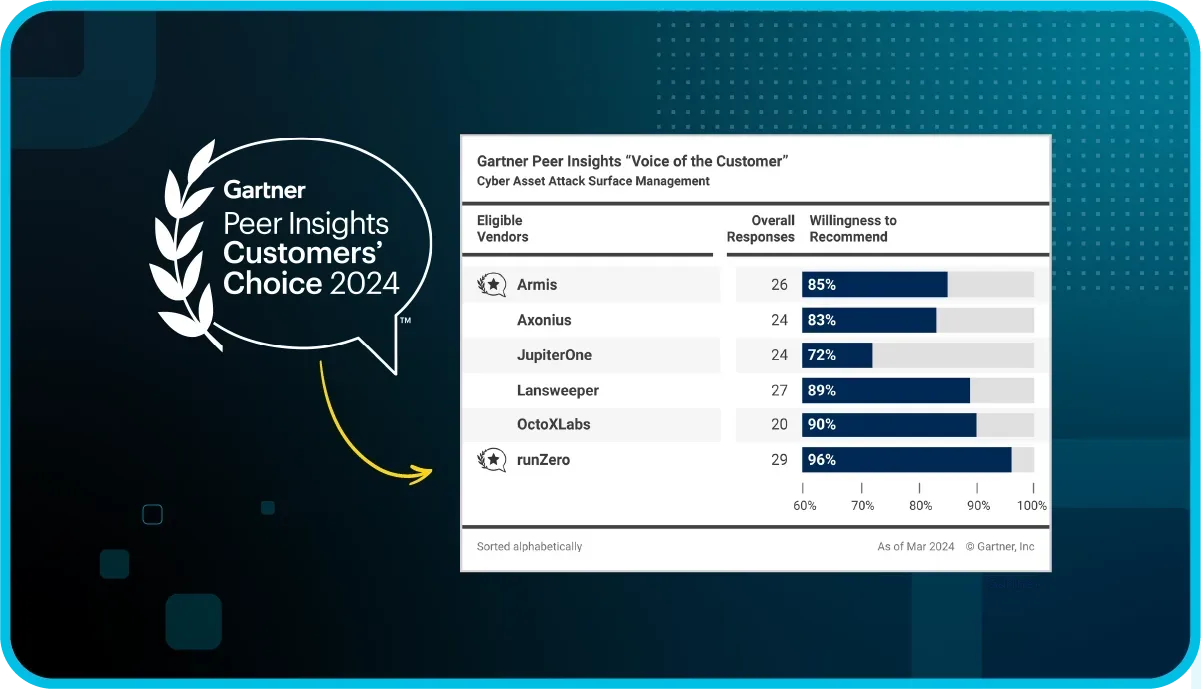
What's new with runZero 4.0? #
- New runZero Platform and Community Edition
- Build your inventory through passive discovery
- Discover assets the way you want to
- Integrate with Tenable Security Center
- Understand correlations quickly
- Improved new user workflow
New runZero Platform and Community Edition #
The new and improved runZero Platform represents the culmination of four years of innovation, so it’s only fitting this is version 4.0 of our technology! Over the last few years, runZero has evolved and matured from an innovative asset inventory and network discovery product to a world-class CAASM (cyber asset attack surface management) solution. We couldn’t have reached this major milestone without our community and our awesome customers, and we thank you for supporting us on this journey.
The new Platform introduces passive discovery functionality, making runZero the only CAASM solution to combine proprietary active scanning, native passive discovery, and API integrations. Unifying all of these approaches makes runZero unique in its ability to deliver comprehensive coverage across managed and unmanaged devices, including the full spectrum of IT, OT, IoT, cloud, mobile, and remote assets.
With the introduction of the runZero Platform, we also have a new Community Edition that will replace Starter Edition effective immediately. Community Edition is a completely free version of the runZero Platform that is perfect for small businesses, individuals, and security researchers who have 100 or fewer assets.
You might be asking, is this just a name change for the free version? It’s not. It’s much better than that! We want all runZero users to benefit from the full power of the runZero Platform and our new Community Edition makes that possible. See the details below.
We hope the new Platform will help you better manage risk and exposure by giving you the most complete visibility possible across all your environments. Let’s dive into the details.
runZero Platform, Community Edition: CAASM for everyone
The Community Edition is an improved version of the free Starter Edition. It now includes three important discovery approaches: unauthenticated active scanning, API integrations, and passive discovery.
Here's why this is a significant leap forward:
Complete coverage: With three different discovery methods available, you can achieve a complete view of all your assets across IT, OT, IoT, cloud, mobile, and remote environments. runZero helps you uncover your unknowns and provides visibility across your internal network and external attack surface, consolidating everything into a single view.
Cost-efficiency: The Community Edition remains completely free, ensuring that advanced CAASM capabilities are accessible to organizations of all sizes and budgets.
runZero Platform: Unleash the full power of CAASM
Our new runZero Platform brings together all of the features you know and love from our legacy Enterprise Edition with new functionality like passive discovery that is designed to provide the most complete security visibility possible. It includes:
Complete feature set: The Platform provides you with every tool in the runZero arsenal, ensuring you can tackle all the CAASM use cases like building a comprehensive asset inventory, eliminating security controls gaps, understanding vulnerabilities and identifying insecure configurations in your attack surfaces.
Unparalleled flexibility: API integrations, active scanning, and passive discovery are seamlessly integrated, offering you unparalleled flexibility to manage exposures of your ever-evolving attack surfaces.
Priority support: Platform customers can unlock premium support, also known as runZero Care, which enjoys priority access to our support team, ensuring you have expert guidance whenever you need it.
Scale to fit your needs: The Platform is perfect for organizations that manage a large number of assets. Whether you have thousands, hundreds of thousands, or even millions of assets to manage, runZero Platform can handle the load.
Current customers will receive further information about migrations.
Build your inventory through passive discovery #
Unlike other CAASM solutions, runZero offers visibility into OT environments, through both safe active scanning and now a passive discovery capability called traffic sampling. Traditional passive network monitoring tools require significant effort to deploy and compute resources to collect and analyze all network traffic. runZero’s passive traffic sampling only examines a small fraction of network traffic for asset discovery and fingerprinting, which customers can leverage with existing Explorers. This feature allows companies who have a policy against active scanning to build an asset inventory by analyzing traffic observed through SPAN ports, TAP interfaces, and broadcast. Passive traffic sampling is also helpful for organizations with scan windows that are too short to enable active discovery of the entire environment. Both active and passive approaches use the same fingerprinting database that was developed using data collected across tens of thousands of environments and OT devices.
We are very excited to introduce this novel approach to passive discovery as a complement to our reinvention of active scanning. We love a good challenge and like to rethink how we can improve on what’s already out there. Unlike traditional passive discovery solutions, runZero’s passive traffic sampling is faster, easier, and more cost-effective to deploy — and doesn’t require expensive dedicated hardware appliances. Our innovative approach to traffic sampling enables runZero Explorers to process existing network traffic as a software deployment on existing hardware or virtual machines.
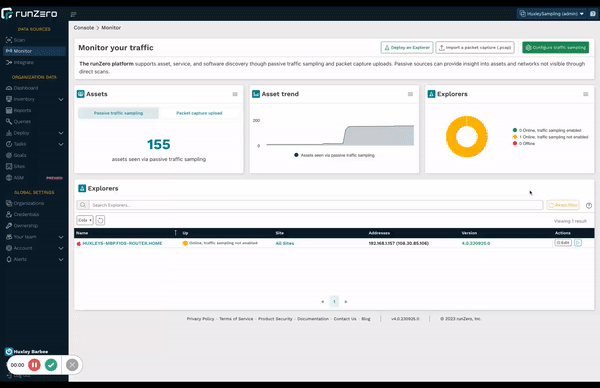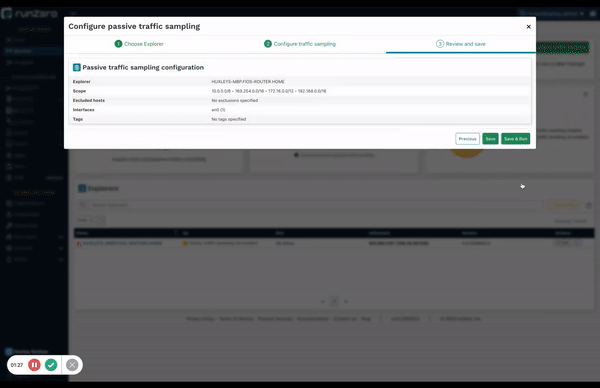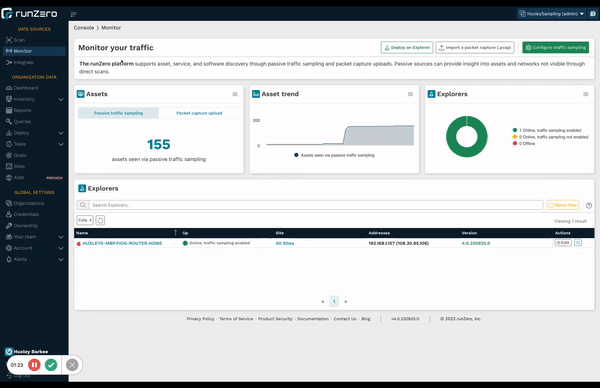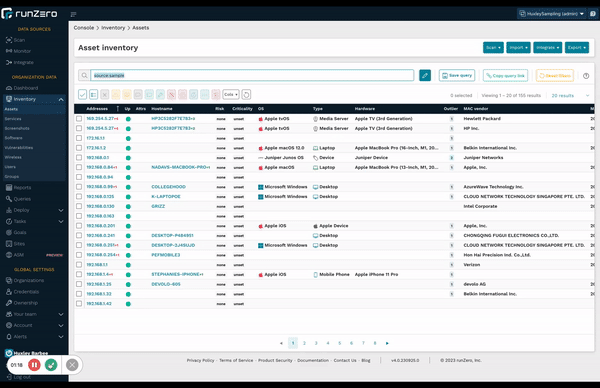
Learn more about passive traffic sampling
Discover assets the way you want to #
Updates to the runZero interface make it easier than ever to leverage all the flexible discovery capabilities available to you. runZero is the only CAASM solution that provides comprehensive asset inventory coverage for managed and unmanaged devices, including IT, OT, IoT, cloud, mobile, and remote assets. This is only possible by combining three specific data sources: proprietary active scanning, native passive discovery, and API integrations. These combined capabilities give customers ultimate flexibility in a single, unified solution, eliminating the need for multiple siloed tools.
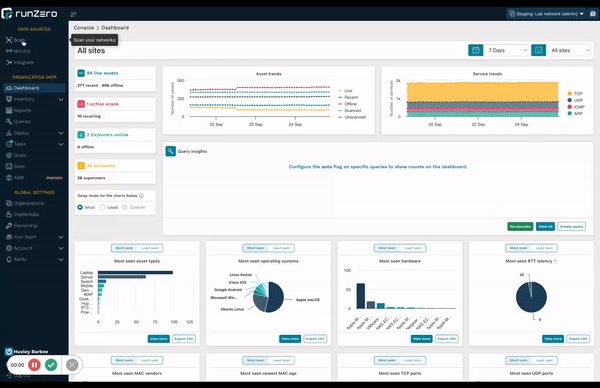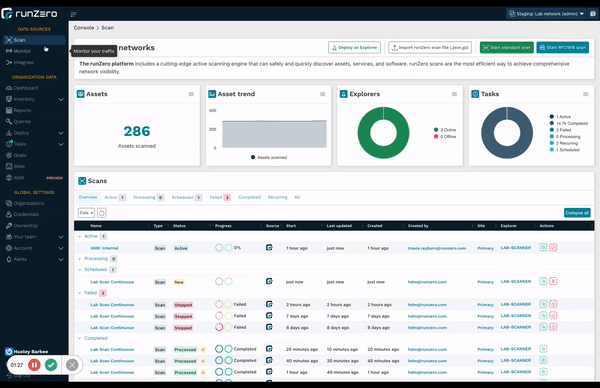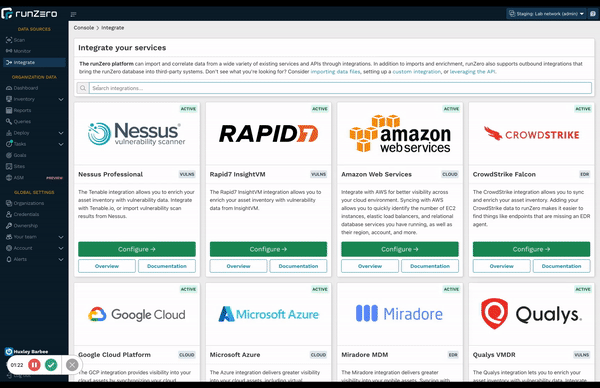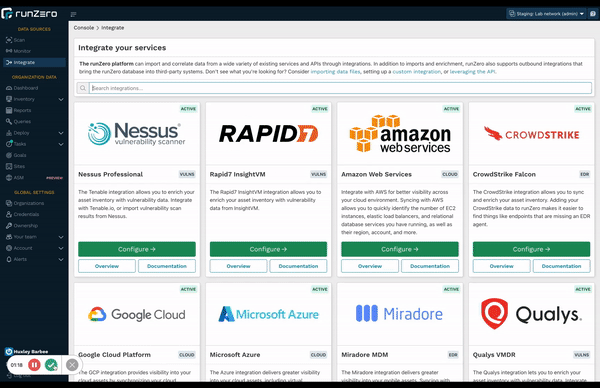
Check out the new start pages for API Integrations, active scanning, and passive discovery.
Integrate with Tenable Security Center #
With 4.0, you can now enrich your inventory with an authenticated API connection to Tenable Security Center, similar to existing integrations with Tenable.io and Nessus. This allows you to search for Tenable attributes, and vulnerabilities in runZero, as well as find assets not monitored by Tenable Security Center. runZero automatically correlates Tenable assets to runZero assets based on unique fields. Vulnerability data can be viewed in the asset details, as well as a dedicated inventory tab. Vulnerability attributes include CVSS score, relevant CVEs, vulnerability description, and any recommended remediation actions.

Learn more about the integration or set up an API connection to Tenable Security Center today!
Understand correlations quickly #
You asked and we delivered. Now you can quickly see the matching field that runZero used to merge data into existing records. Consolidating asset and exposure information from disparate sources into a single normalized view makes it easier for you to manage your ever-changing environment. As networks grow in complexity, sometimes it is not obvious how the correlation engine merges data from a new source and this important quality-of-life improvement shows what field and value was used, as well as the specific task, and time of the merge.
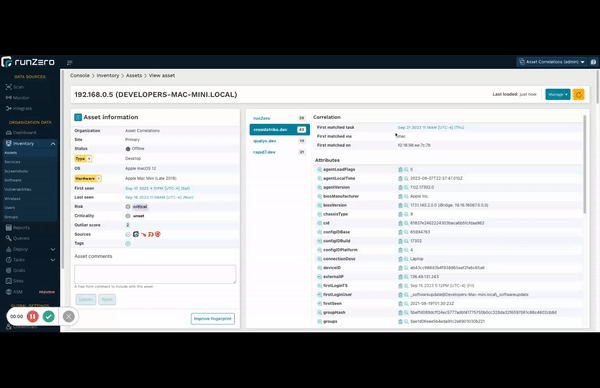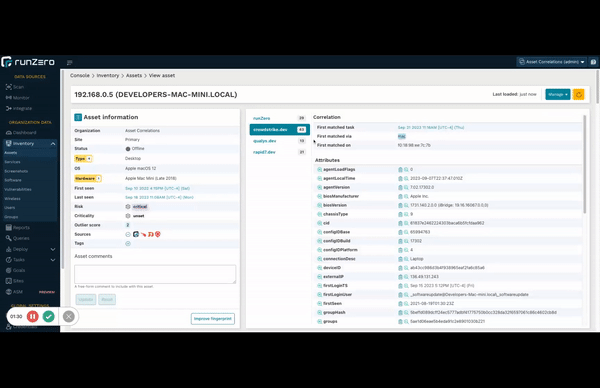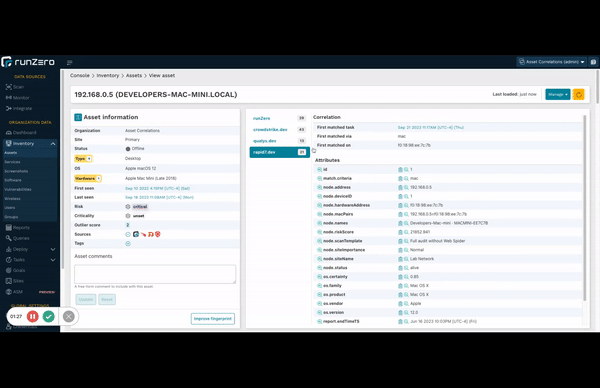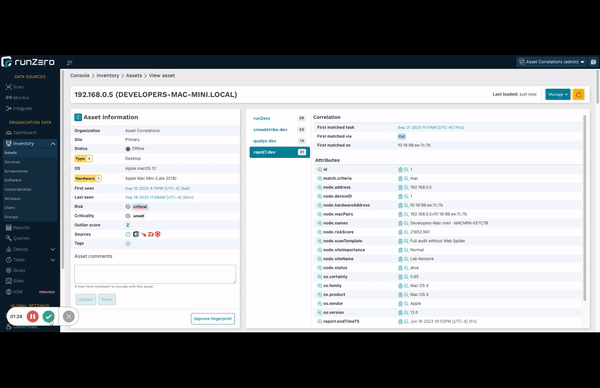
Take a look at any recently-updated asset with multiple sources to check it out!
Improved new user workflow #
New to runZero? You’ll be greeted by an updated onboarding flow that introduces all of runZero’s discovery capabilities and makes it easier than ever to get started.
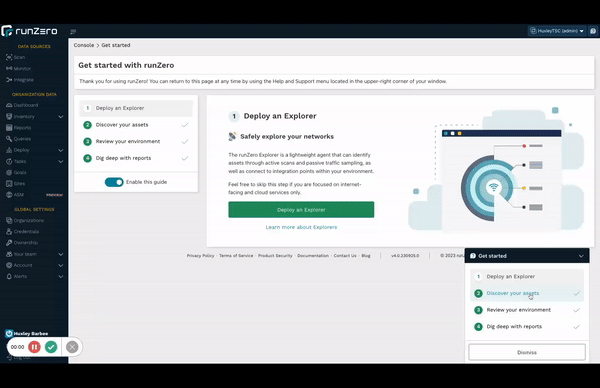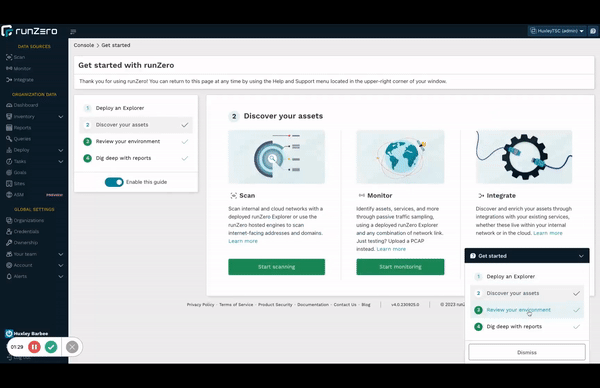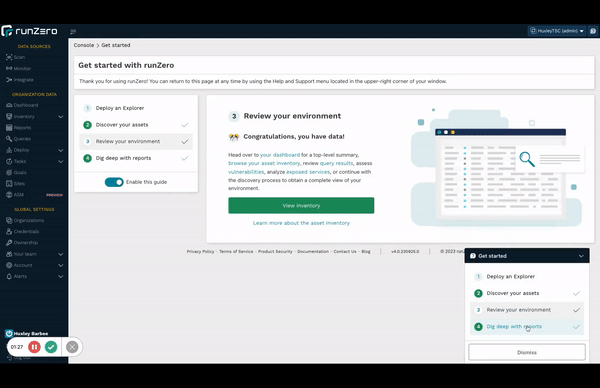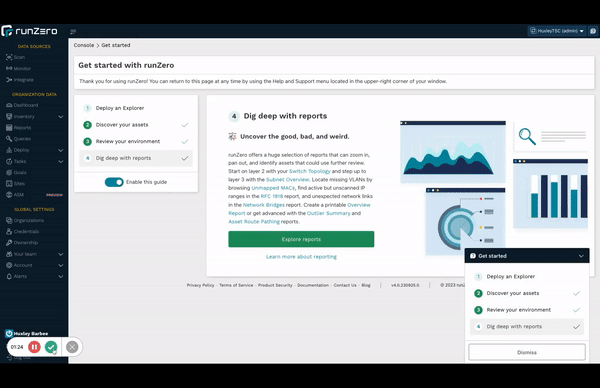
New users will automatically see the new flow. Existing users can check it out too.
Rapid Responses #
- Finding Fortinet SSL VPN
- How to find MegaRAC BMCs
- How to find Citrix NetScaler
- How to find Ivanti EPMM (MobileIron Core)
- How to find OpenSSL 1.1 instances
Protocol and fingerprint improvements #
We continue to add new methods of discovery and to improve fingerprinting. Here’s what’s new in this latest version:
- Support for EtherNet/IP probing and the MODBUS/TCP protocol, improving discovery and fingerprinting for OT networks.
- Support for MQTT, improving discovery and fingerprinting for IoT devices constrained by resources or bandwidth
- Improved fingerprinting of devices using the Mopria Alliance eSCL protocol, such as paper scanners and multifunction printers
- Improved discovery for VoIP endpoints using the Voice Services Discovery Protocol (VSDP)
- Improved fingerprinting for SMBv1 endpoints, assets based on AzureAD, Microsoft Intune, Microsoft 365 Defender, and NFS data, BACnet devices, devices that provide UPnP information, and devices that use Spotify Connect
See runZero 4.0 in action #
Release notes #
The runZero 4.0 release includes a rollup of all the 3.10.x updates, which includes all of the following features, improvements, and updates.
- Moved to a new versioning scheme for the Console and Explorers,
<major>.<minor>.<yymmdd>.<revision>.
New features #
- Build your inventory through passive discovery
- Discover assets the way you want to
- Integrate with Tenable Security Center
- Understand correlations quickly
- Improved new user workflow
Integration improvements #
- A bug that could cause some long-running connection tasks to restart repeatedly has been resolved.
- A bug that could prevent Intune assets from merging with other sources has been resolved.
- A bug that could prevent Tenable Security Center syncs from completing has been resolved.
- A bug that could result in an incorrect ts attribute for Azure AD, Google Workspace, and Microsoft Intune has been resolved.
- A bug that could result in invalid Shodan credentials still validating has been resolved.
- A bug that prevented some queries from correctly matching Intune assets has been resolved.
- A bug where existing assets were incorrectly fingerprinted after importing data from Microsoft 365 Defender has been resolved.
- A performance regression when processing third-party assets has been resolved.
- A rotation date for stored credentials is now available through both console and API via a new
secret_updated_atfield. - CrowdStrike and Azure AD assets will no longer be merged if they have a different globally unique ID. This may lead to more offline assets being generated if devices are frequently reimaged and given new GUIDs.
- Custom Integrations now support the
exclude unknownoption. - Error logging for the Shodan integration has been improved.
- Improved handling of API request retries for the Microsoft Intune integration.
- The Tenable integration has been updated to reduce the possibility of asset and vulnerability export timeouts.
- The Tenable integration has been updated to reduce the possibility of vulnerability export timeouts.
- The request timeout has been increased for the Microsoft Intune and Azure AD integrations.
Inventory management improvements #
- A bug causing inconsistent navigation for Explorer configuration editing has been resolved.
- A bug causing incorrect assertion of Microsoft Defender for Endpoint in
edr.namehas been resolved. - A bug causing pending new tasks to be seen as editable has been resolved, so that only new tasks scheduled to start in the future can be modified.
- A bug causing project expiration to be miscalculated has been resolved.
- A bug causing tasks in the process of stopping to be seen as dismissible has been resolved, so that only failed and completely stopped tasks can be dismissed.
- A bug that could cause foreign service attributes to be attributed to the wrong source has been resolved.
- A bug that could cause tasks to be copied with an incorrect discovery scope has been resolved.
- A bug that could lead to improper stale service removal on rescan has been resolved.
- A bug that could lead to orphaned tasks when an Explorer is removed has been resolved.
- A bug that could prevent import of wireless networks has been resolved.
- A bug that could prevent in-scope, unscanned addresses from being cleared on runZero assets has been resolved.
- A bug that could prevent queries containing mixed-case search terms from returning results has been resolved.
- A bug that could result in an unnecessary screenshot warning for connector tasks has been resolved.
- A bug that could result in duplicate service warnings has been resolved.
- A bug that could result in duplicate software entries for some sources has been resolved.
- A bug that could result in orphaned tasks when removing an explorer has been resolved.
- A bug that enabled SNMP credentials when modifying or copying existing scan tasks has been resolved.
- A bug that prevented SNMPv3 credentials from being saved has been resolved.
- A bug that prevented the
scan.explorer_idvalue from being populated in alert templates has been resolved. - A bug that prevented the
Find assets in this siteicon from working properly in some cases has been resolved. - A bug that resulted in the Nmap XML Export having a zero start time has been resolved.
- An issue that caused the asset details page to load very slowly has been resolved.
- An issue that could result in an empty dashboard until a metrics recalculation was triggered has been resolved.
- An issue that could result in an empty dashboard when selecting a single site has been resolved.
- An update for improved asset matching for tasks importing both scan and third-party data sources has been added.
- An update to the runZero Explorer now logs when the host operating system receives an interrupt or terminate signal, such as when the OS reboots.
- Event rules now support conditions for Explorer and task type, where relevant.
- Exports of task data now include timestamps which differentiate time spent acquiring data from time spent processing data.
- Improved merging of assets with NetBIOS or SMB services.
- Improved performance when deleting large organizations, projects, or sites.
- License-based size limits are now applied to file imports.
- Recurring tasks now stop with an error if they use a task template that has been deleted.
- Task name and description can now be modified for tasks created via file imports.
- Task processing times are improved.
- Tasks in the stopping state are now included in the Processing section of the Tasks overview.
- The maximum number of ownership types has been increased from 10 to 25.
- The tasks CSV export now includes the template_name column.
- The tasks JSON export and API responses now include the
site_name,agent_name, andtemplate_namecolumns.
New vulnerability queries #
- Hardware: MegaRAC BMC
- Hardware: Citrix NetScaler
Scan and monitor engine improvements #
- A bug that could cause a memory leak in the Explorer between stopped tasks has been resolved.
- A bug that could lead to bogus assets appearing in scans through Fortigate proxies has been resolved.
- A bug that could prevent bogus services from certain firewalls from being completely filtered has been resolved.
- A bug that could prevent some Windows-based Explorers from connecting with the same ID has been resolved.
- A bug that could prevent the Explorer from reading the .env configuration file has been resolved.
- A number of small parsing bugs in the protocol parsing engine have been resolved.
- A bug which could leave SYN and LAYER2 probes in a perpetual error condition loop has been resolved.
- A warning is now recorded for scan tasks if a host is ignored for responding on too many ports.
- An issue that could result in stalled scans has been resolved.
- Improved automatic asset filtering for certain web proxy assets.
- Improved detection of spurious services when scanning certain firewalls.
- Passive traffic sampling tasks now set
source:sampleinstead ofsource:passivefor assets. - The Explorer now uses the “runZero” brand by default (and matching filesystem/registry locations).
- The TCP SYN scanner is now friendlier to stateful firewalls in the network path.
- The scanner now supports a new
syn-reset-sessionsoption that can be used to reduce session usage in middle boxes.
Self-hosted platform improvements #
- The self-hosted console now defaults to PostgreSQL 15 and provides an install option to select a version.
- The self-hosted console now uses the “runZero” brand (and
runzeroctlcommand) by default.
Security and user management improvements #
- A bug causing the user details page to display permissions incorrectly has been resolved.
- A bug in the user permissions display interface has been resolved.
- A bug preventing some users from being able to manage their user’s group membership has been resolved.
- A bug that could cause scan templates to be hidden when configured with invalid permissions has been resolved.
- A bug that could prevent new SSO users from authenticating has been resolved.
- A bug that could result in the wrong hostname being used in password reset links has been resolved.
- A bug where users logging in for the first time with SSO would not have access to any organizations from the SSO group mappings has been resolved.
- A security improvement has been added to clear password reset tokens after a password change or when link-based authentication is requested.
- An issue that could result in login errors for invited users using Single Sign-On has been resolved.
API improvements #
- The
api/v1.0/org/sites/{site_id}/importroute now returns the proper 400 http status code error when the request body is empty instead of a status code 500.
UI/UX improvements #
- A bug causing app banners to not be visible has been resolved.
- A bug causing the datepicker to close when navigating by year has been resolved.
- A bug preventing columns from retaining their custom ordering has been resolved.
- A bug that prevented display of the user permissions table in the User Details screen has been resolved.
- A bug that prevented download commands from being displayed on the redesigned scanner page has been resolved.
- On-screen text explaining the interaction between a user’s default organization role and the granted per-org role is clearer.
- The Explorer and scanner download pages have been redesigned for improved UX and performance.
- The Integrate page now shows active and suggested integrations for the current organization.
- The asset details screen now has pagination when viewing an asset with more than 30 services.