Asset inventory is foundational to security: before you protect a device, you must know about it. You may rely on data from your network access control (NAC) and associated network aggregation tools to provide your asset inventory. However, if you’ve found compromised assets but can't find them in your asset inventory, you may have realized that NACs aren’t the best at asset discovery. Allowing or denying access to the network on Layer 2 is their primary function, but finding everything on your network is a different problem. Let's examine why.
NACs have limited visibility to endpoints on the network #
Cyber asset attack surface management aims to maintain a complete inventory of everything connected to your network, from IT to OT, cloud to remote devices. NACs, such as ISE, FortiNAC, CounterACT, and Portnox, employ discovery methods that miss and mis-fingerprint devices.
- Listening to broadcasts
NACs listen for endpoint attributes directly via a couple of broadcast protocols: CDP/LLDP and DHCP. Cisco Discovery Protocol (CDP) and its vendor-agnostic cousin Linked Layer Discovery Protocol (LLDP) primarily provide information about networking devices or phones only. The standard Dynamic Host Control Protocol (DHCP) only provides information about an endpoint's IP address, operating system, and MAC addresses. - Direct network calls
NACs collect attributes from individual hosts rather than a network-wide scan. They use many protocols: DNS, HTTP, RADIUS, and SNMP. Remote Authentication Dial-In User Service (RADIUS) also provides low-level information like MAC, IP address, and location information. Domain Name System (DNS) only provides information about hostnames and IP addresses. If a web service exists, Hypertext Transfer Protocol (HTTP) can provide additional details like application type, operating system, software vendor, and software revision. DNS and HTTP must work alongside other discovery methods since NACs require IP-to-MAC mappings for each endpoint. - Nmap
Nmap is the gold standard for ad-hoc network scanning. Network discovery and security auditing are frequent use cases for this free and open-source utility. However, it has some challenges for general asset discovery at scale. - Passive network monitor
Deploying one or more appliances on a network to eavesdrop on network traffic is a common technique. To make it work, you must send network traffic to the appliance(s) through switch reconfiguration or tap insertions. It's important to note that network location matters. Eavesdropping at a network "choke point" is ideal since it ensures visibility into all traffic. However, the fingerprints lack precision and accuracy if an asset rarely talks on the network or is terse. As more devices encrypt traffic, the fingerprinting accuracy gets worse. - NetFlow
NetFlow is a (marginally) cheaper and easier alternative to a passive network monitor. It collects and stores only Layer 2-4 information, such as source and destination IP and ports, as well as MAC address. - Agent
All NAC vendors provide agents (e.g., AnyConnect, FortiNAC agent, SecureConnector, AgentP). Even NAC solutions that claim to be agentless include them. Running software on the endpoint provides a wealth of details that help NACs apply granular policies, which works well for managed devices if IT can install the agent. - Credentialed queries
Some NAC will log in to a device via Windows Management Instrumentation (WMI) to profile it. Similar to agents, this approach gives a lot of details. Unfortunately, you need to know the credentials first, which means this only works well for managed IT devices.
Note: Organizations rarely use CDP and Nmap in production for NACs, but I’ve included them here for completeness.
Incomplete asset inventory: why NACs fall short #
The current methods of discovery may overlook assets and incorrectly identify them. Broadcasts aren’t propagated over the network and don’t give a broad view of assets. Direct network calls and Nmap (as used by NACs) only provide additional details about devices already known to the NAC. Passive network monitors and NetFlow collectors, despite the effort invested, provide limited detail. Agents are great, but only for managed IT devices.
- Unmanaged IT machines
NACs do not cover these servers, laptops, and desktops. Either the installation got missed, or nobody knew that these machines existed. The other methods won’t tell you much more than an IP address, MAC address, and operating system. - Corporate IoT
Offices contain many IoT devices that can't install an NAC agent because the platform is not supported. The NAC uses alternative discovery methods to identify a device only as a Linux machine or an IoT platform device (such as Espressif or Raspberry Pi). But they could be anything. Think of your printer, IP phone, video conferencing device, thermostat, surveillance camera, and door controller that lets you in when you swipe your access badge. Knowing the hardware matters in a security investigation. - OT equipment
Usually, industry-specific operational technology (OT) includes warehouse technology, production lines, biomedical equipment, and energy transmission. A programmable logic controller (PLC) that controls the production-line robot does not support installing an agent.
Here’s an example of device details detected by a leading NAC:
- Hostname: dev
- Operating system: Windows 7 SPI1
- VLAN: 77
- Current switch:
1.1.1.1 - Connection: Up
- Location: Office
- First Seen: 05/24/2023 at 10:39 AM
- Last Seen: 05/24/2023 at 10:39 AM
- IPv4 Address:
192.168.40.248 - MAC Address:
00:0c:29:59:c4:65
By contrast, runZero provides a great deal of detail by default:
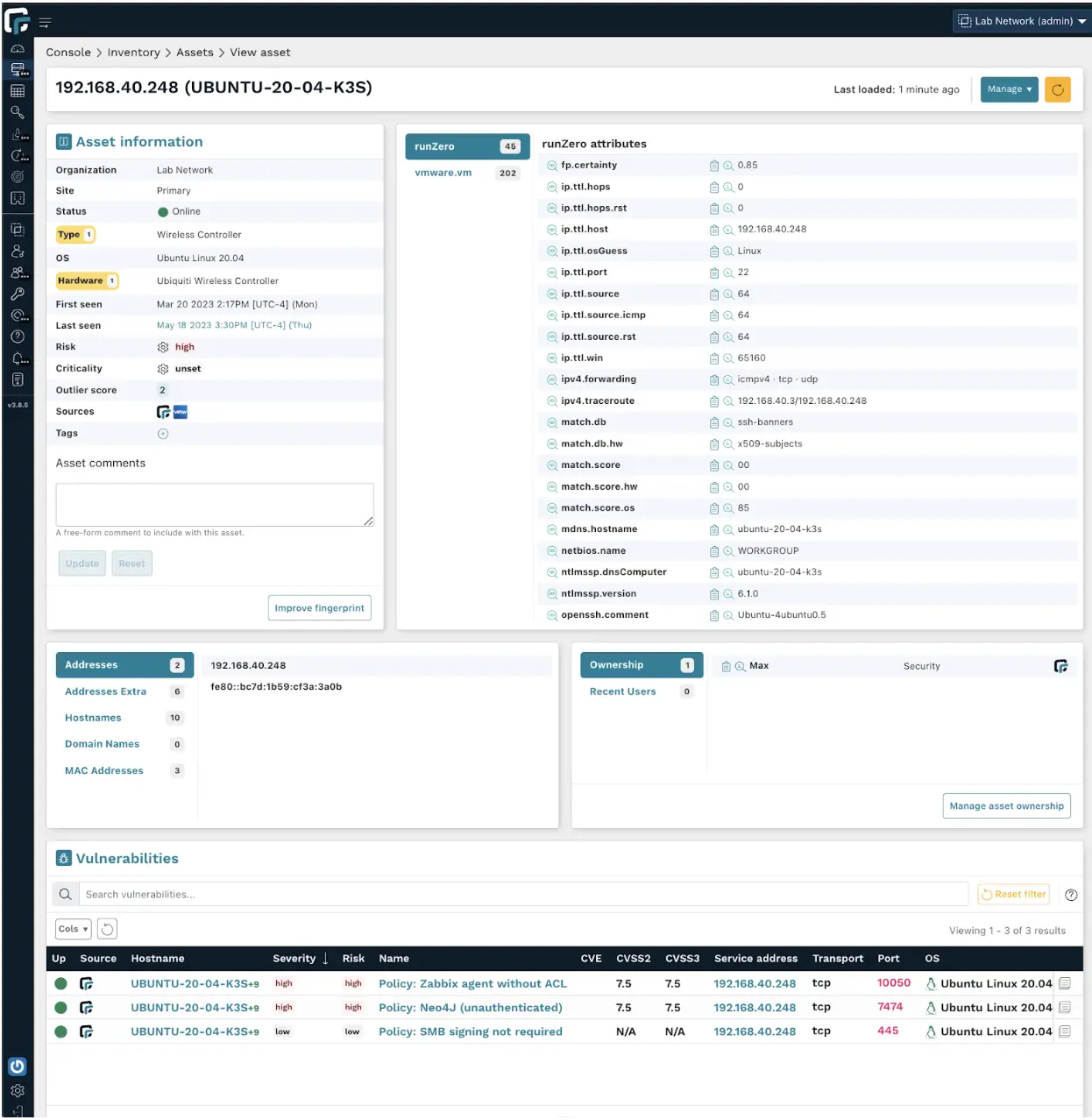
Asset detail comparison: Leading NACs vs. runZero #
Let’s compare and contrast what each solution found:
| Leading NACs (without agents or credentialed queries) |
 |
|
|---|---|---|
| First seen | ⏺ | ⏺ |
| Last seen | ⏺ | ⏺ |
| IP address | ⏺ | ⏺ |
| Secondary IPs | ○ | ⏺ |
| MAC address | ⏺ | ⏺ |
| Seen by sensor/scanner | ⏺ | ⏺ |
| Device type | ◐ | ⏺ |
| Operating system | ⏺ | ⏺ |
| Hardware | ○ | ⏺ |
| Risk | ○ | ⏺ |
| Outlier score | ○ | ⏺ |
| Vulnerabilities | ○ | ⏺ |
| Hostnames | ⏺ | ⏺ |
| Domain names | ○ | ⏺ |
| Ownership | ○ | ⏺ |
| Recent user | ○ | ⏺ |
| Open ports | ○ | ⏺ |
| Searchable banners | ◐ | ⏺ |
| Protocols | ○ | ⏺ |
| Software products | ◐ | ⏺ |
| Upstream switches & ports | ⏺ | ⏺ |
| Location | ◐ | ⏺ |
Missing devices or mis-fingerprinting them become even more problematic when using NACs for enforcement. Suppose a NAC incorrectly identified an IP camera as a Linux server. Your NAC is applying policy to a camera when it’s clearly not.
Underutilizing NAC features to handle all types of devices #
Allowing and denying access to individual endpoints is a central selling point for NACs and an essential control as part of a larger zero-trust networking strategy. Organizations do one of two things to meet the challenge of partial asset inventory and vague fingerprinting regarding their NAC.
- Partial enforcement
Without a full and accurate asset inventory, you risk booting legitimate, business-critical assets off the network. Many organizations selectively enforce based on the relative number of unmanaged devices. Enforcement is commonplace on wireless segments, more miss than hit on wired IT segments, and rare on OT segments. - Exclude MAC addresses
Organizations that attempt enforcement at scale must maintain a list of MAC addresses that bypass enforcement control. Keeping that list up to date is time-consuming and error-prone without a bespoke tool, which accents the depth of the problem, especially in OT environments.
NAC focuses on the LAN #

The security posture of a device viewed by the attacker is not in the scope of a NAC. They adjudicate network access which worked well in a time when most of an organization was in the corporate office. A cyber asset attack surface management solution, on the other hand, provides an inside-out and outside-in view of the inventory. This view includes the external attack surface of an asset, which can be valuable information, such as when RDP is active on a public IP.
Risks and slowdowns due to missing devices #
If you are missing assets in your inventory, you can’t actively manage your security posture. You can only successfully find EOL devices, insecure configurations, and vulnerabilities if you know about all your network's devices.
Asset inventory gaps can impede quick action by causing delays when identifying potentially compromised devices on specific IP addresses. Still, you can’t figure out what that device is. You lose valuable hours while the bad guys get deeper into your network.
An accurate, complete cyber asset inventory is crucial.
A cyber asset attack surface management solution that covers assets from IT to OT, cloud to remote devices #
runZero is a cyber asset attack surface management solution. It combines integrations with EDR and other sources with a proprietary network scanner that is fast and safe even on fragile IoT and OT networks.
runZero scales up to millions of devices, but it’s easy to try. The free 21-day trial even downgrades to a free version for personal use or organizations with less than 256 devices. Find out what’s connected to your network in less than 20 minutes.