Think of the technological ecosystem an organization relies on to operate efficiently and effectively: desktop workstations, mobile devices, IT/IoT/OT devices, virtual systems, web apps, data, cloud infrastructure – just to name a few. Keeping track of every single one of these devices feels impossible.
As the number and types of assets continue to grow exponentially, organizations need help staying on top of these devices. Left unmanaged, these devices can act as potential footholds for malicious actors. Security teams need to be able to discover and identify unmanaged cyber assets if they ever want to secure or protect them. How could they effectively secure and protect their organization if there are assets they don't know about – what they do, where they are, or what their status is?

Cybersecurity frameworks and regulations start with a comprehensive asset inventory #
Asset inventory is the foundation of a strong cybersecurity posture. It is often considered the first step in identifying potential risks to your organization's security. This is why it is a key recommendation in many cybersecurity frameworks, including the NIST Cybersecurity Framework (CSF) and CIS Controls. By maintaining an up-to-date inventory of all hardware, software, users, and digital assets across your organization, you can better understand your attack surface and take proactive measures to protect against potential threats.
Let's take a look at some of the major frameworks and regulations that require an asset inventory.
CIS Controls #
The Center for Internet Security (CIS) provides a list of recognized standards for defending your systems and data against modern cyber threats. Cybersecurity professionals and subject matter experts use a consensus-based process to establish these controls. Organizations such as ISC2 and the SANS Institute contribute to the process.
You can consider the CIS Controls an essential safety check that ensures you have your house in order by following security best practices. It speaks volumes that the first control on the list, seen as foundational for good cyber hygiene, is "Inventory and Control of Enterprise Assets." The rationale is that you need an up-to-date inventory to know what to monitor and protect within the enterprise. An asset inventory also helps you identify unauthorized and unmanaged assets to remove or remediate.
NIST CSF #
The NIST Cybersecurity Framework (NIST CSF) is a set of cybersecurity guidelines developed by a non-regulatory agency of the United States government. The NIST CSF is about guidance and best practices with a framework centered around five core functions: Identify, Protect, Detect, Respond, and Recover.
It's in the Identify function of this framework that asset inventories get flagged as vital for modern cybersecurity programs. According to the framework, the Identify function is all about "risk to systems, people, assets, data, and capabilities." A big part of this is knowing what assets you actually have.
SOC2 #
SOC2 is a voluntary compliance standard, but it's often required to land vendor contracts, particularly with SaaS and B2B companies. Compliance with SOC2 shows clients and partners that your company maintains the highest standards of information security. Meeting SOC2 requirements can make all the difference in whether you succeed in various industries and types of services.
Effective IT asset management is pivotal for obtaining SOC2 certification. In particular, the certification looks for your ability to safeguard assets against unauthorized access and reliably assign owners and users to assets.
HIPAA #
Compliance with the Health Insurance Portability and Accountability Act (HIPAA) is essential in the healthcare industry. High standards of security must protect sensitive patient healthcare information. Violations of HIPAA are costly from a financial standpoint, and the penalty involved depends on the level of negligence.
Healthcare providers and business associates need IT asset inventories in order to track the location of electronic health information (ePHI). This reliable, up-to-date asset inventory helps comply with the regulation's Security Rule.
PCI DSS #
The Payment Card Industry Data Security Standard (PCI DSS) is a mandatory regulation aimed at protecting cardholder data. Companies that store, process, or transmit cardholder data must comply with PCI DSS. In requirement 2.4 of PCI DSS, the regulation requires companies to maintain an inventory of physical devices, software, user accounts, and more.
The elusive single-source-of-truth for assets #
An asset inventory is like the blueprint of a house–without it, there isn't a clear understanding of what needs protecting. But just like how blueprints can change over time with additions and renovations, an inventory can also become outdated as assets get added or removed from the network.
Networks change constantly, with users logging into enterprise platforms from personal devices or rapidly spinning up new cloud infrastructure that often gets forgotten about. Unsanctioned shadow applications get stood up or accessed by different departments. Add remote work and the continued proliferation of IoT devices to the mix, and you have a more complex IT ecosystem that's harder to track than ever.
A couple of statistics that drive home the challenges include:
- Shadow IT cloud usage is estimated to be 10x the size of known cloud usage.
- One survey found just 28 percent of companies thought their asset inventories were more than 75 percent complete.
Why do asset inventories pose such a challenge for so many organizations? Part of the challenge is that many companies use outdated processes, like spreadsheets, for tracking and managing their cyber assets. As a result, gaps in visibility emerge regularly in today's dynamic IT ecosystems and risky security scenarios are commonplace. For these reasons, it's crucial to have a system in place that allows for continuous discovery and monitoring of assets.
The risks of not having an accurate asset inventory #
If you're not proactively maintaining and analyzing your asset inventory, you're putting your organization at risk. An up-to-date and comprehensive asset inventory is essential for you to make informed business decisions and ensure operational efficiency. Let's take a look at some of the common issues you'll encounter when your asset inventory is lacking.
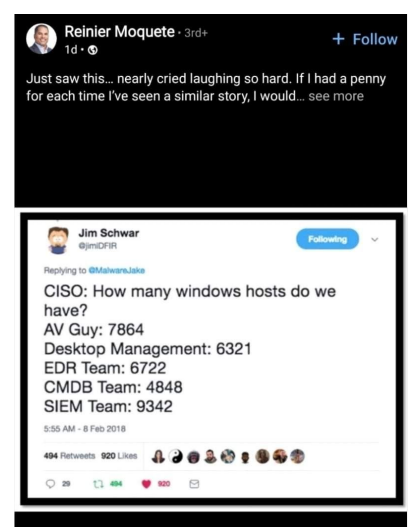
Issue 1: Misalignment between IT and security teams #
IT and security teams end up counting different numbers of assets, depending on how they track and update their inventories. This makes it hard to discern the truth of what your IT ecosystem looks like and reduce risks.
Issue 2: Weak security controls coverage #
Given the lack of a single source of truth, gaps are more likely to arise in security control coverage. Different teams take responsibility for various areas of security. If these teams lack alignment you'll end up with a lack of visibility into security controls coverage, leaving you unaware of:
- Endpoints not covered by an endpoint detection and response solution (EDR), such as CrowdStrike.
- Missing hosts from the SIEM tools used by security operations teams to correlate events and proactively respond to more advanced threats.
Issue 3: Failure to manage risky assets #
An asset inventory is crucial for identifying and responding to security risks. Not all assets pose the same level of risk, and a comprehensive inventory helps to identify those that do. For example, an isolated device with encrypted traffic may be less risky than an internet-facing asset with insecure configurations. By keeping track of all assets, organizations can respond quickly to zero-day vulnerabilities that require immediate attention. For example, the Log4 vulnerability affected up to 3 billion devices, highlighting the importance of maintaining an up-to-date inventory for efficient vulnerability response.
Issue 4: Lack of asset ownership #
Asset ownership is a critical component of asset inventory, as it defines who is responsible for managing and securing each asset. The Equifax breach serves as a prime example of the consequences of not having proper asset ownership in place–without clear ownership over a legacy internet-facing system, no one took responsibility for ensuring that it was scanned and patched regularly. To avoid similar incidents, organizations must prioritize establishing clear lines of asset ownership and incorporating them into their overall security program.
Build the foundation for your security program #
Given the modern threat landscape and the fluid nature of IT environments, organizations must regard an accurate and up-to-date asset inventory as a basic tenet of an effective security program. Given the challenges and risks involved, it's time to move on from manual processes that provide point-in-time static snapshots that often don't resemble the true state of your network.

Take the first step towards improving your security posture by moving to cyber asset attack surface management solutions that can keep pace with the assets connected to your network. A truly effective CAASM solution offers advanced fingerprinting techniques and leverages asset data from multiple sources to provide a comprehensive view of your asset inventory – from IT to OT devices, on-premise to cloud to remote environments.
How runZero can help #
runZero can help you to gain visibility into all the assets connected to your network, so you can proactively defend against cyber threats. First, you can identify all the assets connected to your network, including those that may have been forgotten or overlooked. Second, you can track changes made to these assets over time. Third, you can assess the risk associated with each asset and prioritize remediation efforts accordingly. As a result, you can improve your organization's overall security posture by having a complete understanding of your asset inventory.
Ready to take the next step? runZero is the fastest and easiest way to get to full asset inventory across IT, OT, on-premise, cloud, and remote environments.