In the world of Operational Technology (OT), you can’t defend what you don’t know exists. Yet, across critical infrastructure — including energy, water, transportation, manufacturing — many organizations still struggle to answer a fundamental security question: What assets do we actually have, and how are they connected?
On August 13, 2025, the Cybersecurity and Infrastructure Security Agency (CISA), in collaboration with the EPA, NSA, FBI, and international partners from Australia, Canada, Germany, the Netherlands, and New Zealand, released new joint guidance for Foundational OT Cybersecurity.
This succinct resource provides a clear, actionable framework for building and maintaining a complete OT asset inventory, which is a foundation for any modern, defensible OT cybersecurity architecture.
5 steps to build an OT asset inventory #
The CISA guidance suggests a five-phase approach to developing an OT asset inventory and taxonomy:
- Define scope and objectives
- Define an authority over the OT asset inventory, determine stakeholders, assign roles and responsibilities, and set boundaries for the program.
- Identify assets and collect attributes
- Using both physical and logical surveys, compile a comprehensive list of OT assets and their attributes as well as their network dependencies.
- Identify and prioritize attributes such as protocols, asset criticality, manufacturer, and operating system.
- Create a taxonomy to categorize assets
The guide outlines five steps to building a taxonomy:
- Classify assets
- Categorize assets and their communications pathways
- Organize structure and relationships
- Validate and visualize
- Periodically review and update
The guide includes a full breakdown of these elements, with examples for oil and gas, electricity, and water and wastewater organizations.
- Manage and collect data
- Ingest and store additional asset information sources (e.g., vendor manuals, handbooks, configuration specs) in a centralized database.
- Implement life cycle management
- Define asset lifecycle stages and develop policies for maintenance schedules, replacement plans, and backup strategies.
CISA’s roadmap beyond OT inventory #
Building an OT asset inventory is only the first step. CISA’s guidance outlines five key areas organizations must address after creating their inventory:
- OT cybersecurity and risk management
- Identify known vulnerabilities and cross-reference with resources like CISA’s KEV Catalog.
- Prioritize threats based on risk and implement a strong security architecture.
- Maintenance and reliability
- Incorporate vulnerability findings into maintenance planning and patching schedules.
- Performance monitoring and reporting
- Continuously monitor OT performance and network health with diagnostics and reporting mechanisms.
- Training and awareness
- Train staff and run awareness programs for all stakeholders.
- Continuous improvement
- Use feedback loops and change management to track OT asset changes, and conduct regular reviews and audits.
Creating an actionable OT inventory with runZero #
Through safe unauthenticated active scanning, passive traffic sampling, and third-party integrations, runZero can build, define, and maintain a comprehensive asset inventory for OT environments and their IT/IoT interdependencies. It can fingerprint and identify assets, hardware, firmware, and software versions, protocols, and more.
With this data, runZero helps organizations categorize assets by risk, criticality, location, ownership, and more. Continuous monitoring ensures visibility into changes, shadow IT, and unmanaged assets. Robust integrations with SIEM, SOAR, and AI tools improve overall programs.
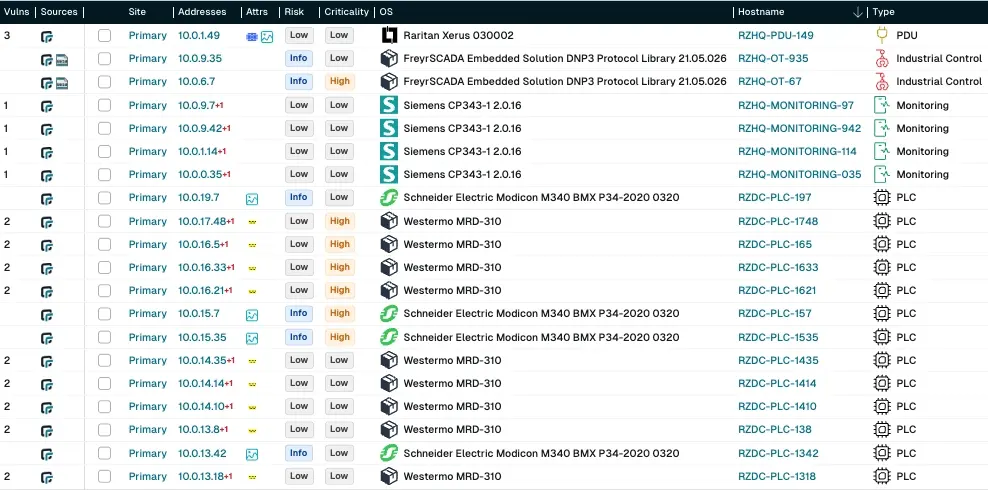
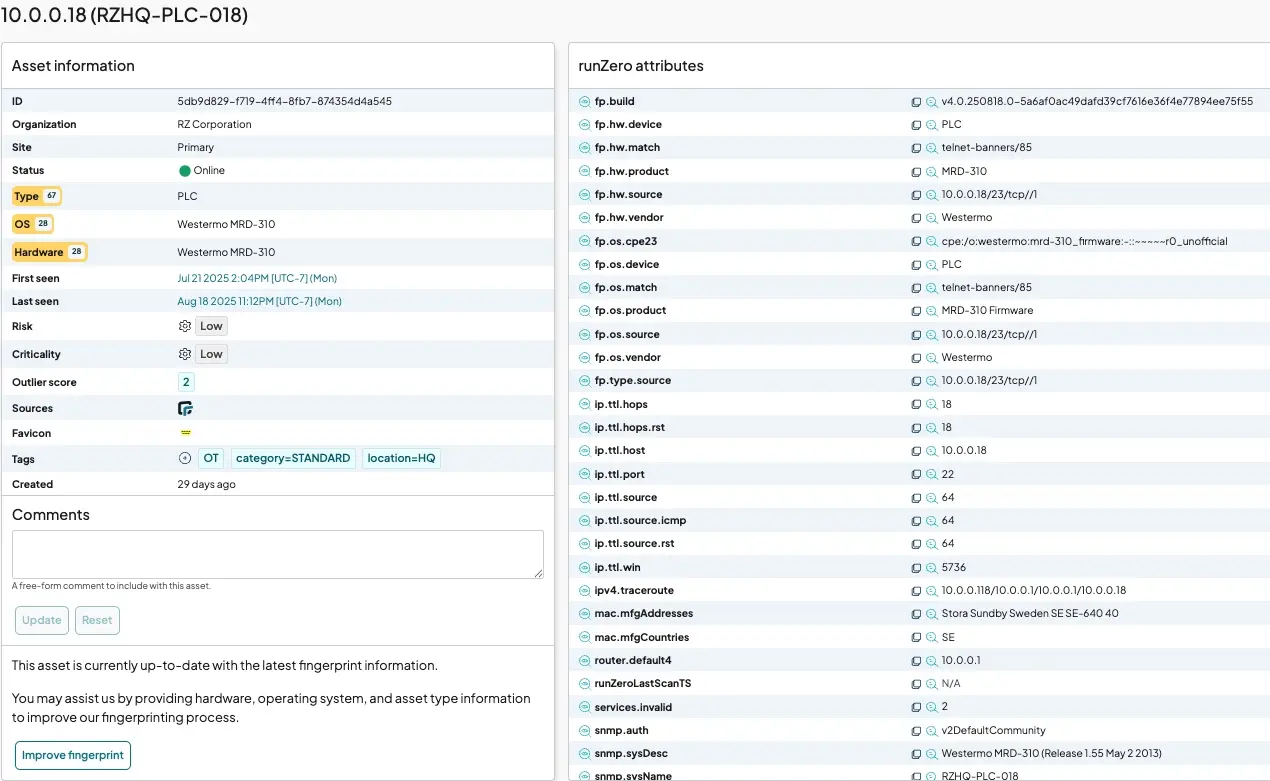
CISA highlights the importance of taxonomy creation, which often requires manual entry. runZero integrates with NetBox to ingest manual attributes like baseline image or manufacture date. See this example attribute list.
In 2022, CISA mandated that all Federal Civilian Executive Branch agencies implement asset visibility and vulnerability detection (BOD 23-01). The common theme across this OT guidance and BOD 23-01 is the need for a complete asset inventory across IT, OT, and IoT. If you don’t know what you have, you can’t protect it.
For more, see our blog on CISA BOD 23-01 requirements.
Real-world case study #
Inductive Automation, a leading industrial automation software company best known for its flagship SCADA platform, Ignition, supports thousands of organizations worldwide across manufacturing, energy, water, and other critical infrastructure sectors.
When Jason Waits, CISO at Inductive Automation, discovered runZero, he decided to start with a free trial.
"I checked the runZero website and saw the free trial — which I love. I downloaded it and immediately scanned a couple of subnets. The UI/UX was user-friendly, and the asset classification was incredibly detailed."
With runZero, Inductive Automation discovered over 50% more assets on their network than previously known. The team now uses runZero to accelerate remediation efforts, leveraging the platform’s robust set of out-of-the-box queries to speed up incident response and gain deeper visibility across their OT environment.
Check out their full case study for more details.
Closing thoughts #
A complete OT asset inventory is foundational to cybersecurity, especially as critical infrastructure increasingly becomes a target for cyberattacks. Without visibility, you’re flying blind. With runZero, you see everything before it becomes part of an incident. Ready to see everything in your OT environment? Connect with our team to learn more.

















