
On October 3, 2022, the Cybersecurity and Infrastructure Security Agency (CISA) released the Binding Operational Directive (BOD) 23-01: Improving Asset Visibility and Vulnerability Detection on Federal Networks. This directive requires all Federal Civilian Executive Branch (FCEB) departments and agencies to comply with a set of cybersecurity requirements by April 3, 2023. Under the directive, asset visibility and vulnerability detection capabilities must be improved to meet the requirements outlined by CISA.
The BOD 23-01 strives to improve visibility and vulnerability detection on federal networks. However, the issues addressed by this directive are not exclusive to federal agencies. Asset inventory and vulnerability management are encouraged as best practices for all organizations, even though only FCEB agencies are legally required to comply by the April 3, 2023 deadline. In fact, CISA Director Jen Easterly told reporters, “Knowing what’s on your network is the first step for any organization to reduce risks.”
Asset visibility is foundational to cyber security #
Cyber security is a universal challenge where asset inventory plays a major role. In other words, knowing your asset inventory is necessary for effective cyber security practices to be implemented. Easterly also said, “While this Directive applies to federal civilian agencies, we urge all organizations to adopt the guidance in the directive to gain a complete understanding of vulnerabilities that may exist on their network. We all have a role to play in building a more cyber resilient nation.” Regardless of whether or not an organization is a federal civilian agency, asset inventory should be the first step in reaching meaningful risk mitigation.
Modern cyber security practices require multi-part defensive measures. As technology has evolved, so have the threats to our security. More recently, the diversification of network environments in the civilian workplace has made network security and tracking more difficult. What had been a gradual transition to hybrid networks as the norm escalated rapidly during the pandemic, forcing security teams to suddenly manage on-premise, hybrid, and cloud networks more quickly than they were prepared to do. Network visibility now faces new challenges as networking environments have shifted.
There are too many assets to be tracked via manual methods, like spreadsheets. Not to mention unknown assets that may have been missed by traditional discovery methods. If you don’t know about an asset, how can you scan it for vulnerabilities?
Asset visibility is a critical building block for security measures, allowing you to have context around every asset connected to your network. You can leverage this data to assess endpoint detection and response (EDR) and vulnerability scan gaps in your network security. Thus ensuring you have strong, comprehensive network security coverage.
BOD 23-01 requires asset inventory & vulnerability enumeration #
The number of assets has only continued to increase over time and CISA says “continuous and comprehensive asset visibility is a basic precondition for any organization to effectively manage cybersecurity risk.” In a 2021 US Senate report, federal agencies highlighted common asset and vulnerability challenges regarding their cyber security posture. That’s where CISA BOD 23-01 comes into play.
BOD 23-01 focuses specifically on asset discovery and vulnerability enumeration which, as indicated in the diagram above, are critical pieces of any cyber security program. By April 3, 2023, federal civilian agencies need to have taken steps to comply with the following requirements:
- Perform automated asset discovery every 7 days, covering a minimum of the organization’s IPv4 space.
- Ingest on-demand vulnerability scan reports within 72 hours of a CISA request and be able to present findings to CISA within 7 days.
- Perform vulnerability enumerations every 14 days with detection signatures that are no more than 24 hours old.
This criteria demands automated, on-demand, and rapid asset discovery capabilities. For many organizations, the volume of assets is too large for manual processing. BOD 23-01 aims to ensure federal agencies can keep up with their asset visibility and tracking. Automation must be able to report vulnerability data into a CDM dashboard to comply with BOD 23-01. CISA BOD 23-01 implementation guidelines specify what assets types fall within the scope of this directive, such as bring-your-own-device (BYOD) assets, communication devices, and more.
Asset discovery and vulnerability enumeration #
The CISA BOD 23-01 requires that asset discovery capabilities must be able to capture high-fidelity data for managed and unmanaged devices. This data must be readily available, and presented in a digestible format to be considered compliant with the new directive. But asset discovery is only half the battle. There are several agencies that use vulnerability scanners to conduct discovery in addition to the traditional use of conducting vulnerability assessments. Vulnerability scanners are not an effective way to meet the new CISA requirements for asset inventory because they have limitations in terms of when they can run and how long the scans can take. FCEB agencies, and other organizations are encouraged, need a discovery solution that enables same-day response.
Asset discovery and vulnerability enumeration are the focal points of BOD 23-01. These two aspects of cyber security empower organizations to “better account” for assets and risks that have previously been unknown, and therefore unprotected, within their networks. While the CISA BOD 23-01 aspires to discover and protect the critical infrastructure and networks of the government, the same values can be applied to networks at large, no matter how the network is structured.
Asset discovery is a foundational security measure #
The BOD 23-01 states, "Asset visibility is the building block for operational visibility." Organizations must be able to identify IP addresses directly in the network as well as associated IP addresses. BYOD, cloud, and other assets are included in this identification requirement. IPv4 addresses need to be accounted for in their entirety at a minimum, though full visibility of other IP addressable assets are highly encouraged.
There are several ways to perform asset discovery, including active, passive, and external scanning. Each method will bring certain assets to light, but these methods also come with their own challenges.
- Active: An active scan transmits network packets or queries local hosts and then analyzes responses. In other words, active scanning creates traffic for the network. If you are scanning a network with fragile devices, ensure that you pick a scanner that has been designed to safely scan these devices.
- Passive: These scans observe traffic that traverses the network adapter the scanner is configured to listen in on. Passive scanning collects data about the assets actively talking on a limited section of the network, limiting visibility to a singular “choke point” and active assets. Passive collection is difficult to deploy across a sprawling organization. Encrypted protocols have made passive asset inventory increasingly harder.
- External: External attack surface management (EASM) tools provide a perimeter view of IP addresses outside your network. Scanning external attack surfaces helps with gaining visibility to external hosts or exposed services, reconnaissance in penetration testing, and more. However, network owners can opt to hide their IP ranges, preventing those assets from showing up on your scan. Additionally, these are conducted without direct access to the network so visibility may be limited even further.
Effective asset discovery capabilities will deliver visibility into both internally and externally facing assets. As a result, you’ll have a more comprehensive asset inventory, allowing you to quickly identify and track when assets come online or go offline.
Critical vulnerabilities must be enumerated within 72 hours #
Cyber security programs must be able to identify asset-specific vulnerabilities on-demand to comply with BOD 23-01 requirements. This applies to any information technology or operational technology asset that is accessible via IPv4 or IPv6 networks. BOD 23-01 mandates that agencies enumerate vulnerabilities across all discovered assets, such as operating systems, software and versions, potential misconfigurations, and missing updates. However, vulnerability enumeration has its own challenges and limitations with fingerprinting.
On top of struggling to meet data requirements, vulnerability management solutions lack the ability to meet the requirements outlined in CISA BOD 23-01, particularly, the 72 hour response timeline. Vulnerability scan times can vary greatly, depending on the business restrictions in place. Oftentimes, teams need to wait until the new vulnerability checks are available in order to scan for the newest security flaw. The solutions then need to scan the network again, which often requires waiting for the next maintenance window. This makes the required 72 hour response time extremely challenging to meet.
A modern approach to identifying potentially vulnerable systems much faster is to decouple the network scan from the vulnerability analysis. A modern asset discovery solution will be able to scan the hardware and software assets on the network with enough detail that it already contains enough information to identify potentially vulnerable systems. As a result, security teams can identify potentially impacted systems in minutes by querying the database. This approach is much faster than the traditional path of waiting for updated vulnerability checks, updating the scanners, scanning the network, and running reports on the new vulnerability.
Reducing the network security threat surface through asset inventory and vulnerability management solutions is critical to one’s overall security posture. One tool without the other is not enough to comply with the recent directive. Asset inventory and vulnerability management solutions work together to provide a clearer picture of an organization's security posture.
How runZero helps comply with BOD 23-01 #
runZero is a cyber asset attack surface management solution that uses active, unauthenticated scanning capabilities as well as the ability to pull in third-party data, for example from vulnerability scanners, for a full picture of your network. runZero was founded by HD Moore, the creator of Metasploit, with cyber security fundamentals in mind. The runZero scan engine was designed from scratch to safely scan fragile devices.
runZero can help with administering asset discovery and inventory management in several ways including:
- Discover the entire IPv4 space in less than 7 days: BOD 23-01 requires that the entire RFC 1918 space is scanned every 7 days for asset inventory. Most scanning technologies, especially vulnerability scanners, will struggle to cover an entire agency in this amount of time. runZero can cover the entire internally addressable RFC 1918 space overnight. runZero can also scan the agency’s external perimeter.
- No credentials required: BOD 23-01 states that “asset discovery is non-intrusive and usually does not require special logical access privileges.” runZero features a proprietary unauthenticated active scanner that was designed with asset inventory in mind. Many other solutions require credentials to obtain enough information about systems
- Respond rapidly to imminent threats: BOD 23-01 requires agencies to “develop and maintain the operational capability to initiate on-demand asset discovery and vulnerability enumeration to identify specific assets or subsets of vulnerabilities within 72 hours of receiving a request from CISA and provide the available results to CISA within 7 days of request.” After a new vulnerability story breaks, vulnerability scanners often take 1-2 weeks to create a vulnerability check for new vulnerabilities before agencies can even start testing. In most cases, you can use runZero’ existing scan data to find affected systems in a matter of seconds without having to rescan.
- Get asset context on enumerated vulnerabilities: runZero integrates with Tenable, Rapid7 and Qualys to import vulnerability data into the asset inventory to provide contextual information on what assets a vulnerability was found on as well as the network context of the asset. In addition, runZero makes it easy to check that your vulnerability scanners are covering all of your subnets, highlighting any security control coverage gaps.
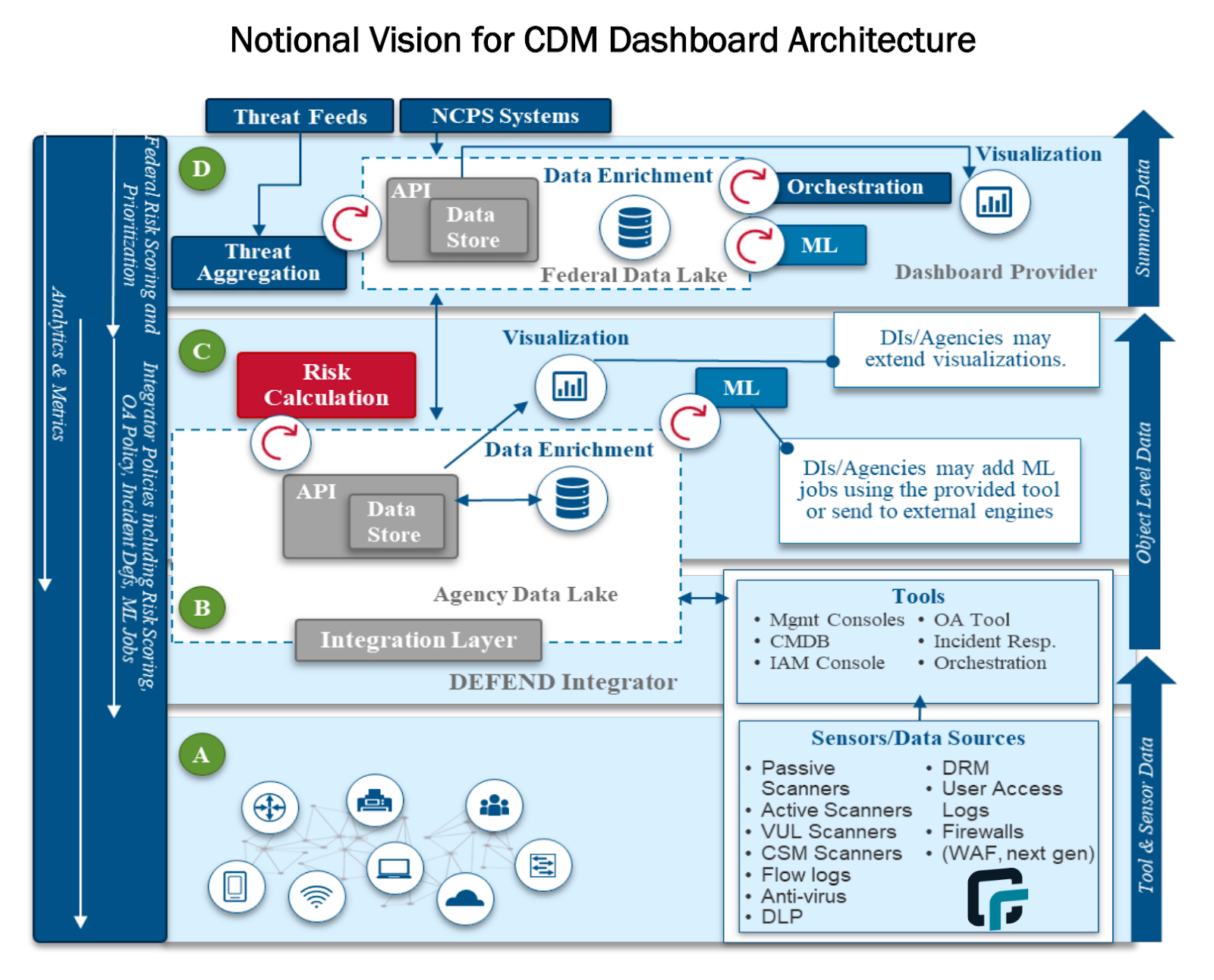
- Import asset inventory data to the CMDB or Agency Data Lake: According to the CISA CDM architecture diagram, active scanners should push their data into the CMDB, which publishes data to the agency data lake that feeds the CDM. runZero integrates with CMDBs (e.g. ServiceNow). Some agencies that do not have an existing CMDB may even choose to aggregate data in runZero directly and feed the Agency Data Lake from there. runZero integrates with vulnerability scanners, endpoint detection and response (EDR) solutions, mobile device management (MDM) software, Microsoft Active Directory / Azure AD, attack surface management vendors, and cloud hosting providers to aggregate and consolidate all asset data in a single platform. It then offers a simple JSON export API to pull the asset inventory into a data lake.
Discover internal and external assets #
runZero discovers internal and external assets, providing the high-fidelity context needed to fulfill BOD 23-01 requirements. Set up recurring unauthenticated scans to keep your asset inventory awareness up. Alerts for new asset connections or existing asset changes can be easily added to your scans. You can also conduct on-demand scans as needed and get the asset contextualization you need in minutes, complete with downloadable, digestible reports that you can present to your team (or CISA).
To meet the requirements outlined in BOD 23-01, your asset discovery solution needs to be able to quickly capture high-fidelity asset data on everything within your firewall as well as exposed services to properly assess your asset vulnerabilities. runZero can give you a strong picture of your external attack surface. Through active scanning and integrations, runZero augments data found by taking inputs from internal IPs that have been discovered and identifying public-facing hosts. Additionally, our unauthenticated scans can discover assets on a network without requiring a username/password. This approach is unobtrusive, because it doesn’t require credentials and agent deployment is time consuming and only covers managed assets.
Build a comprehensive asset inventory #
A complete asset inventory includes unmanaged devices, internal and external assets, and having relevant data available on all of these assets. This level of visibility is essential both for strengthening your security posture and for meeting BOD 23-01 requirements. Unauthenticated scanning is the best way to quickly capture this information without having to worry about system fragility or resource-intensive setup like with agent-based solutions.
runZero creates a comprehensive picture of your asset inventory through on-demand unauthenticated scans and integrations, giving you more accurate fingerprinting of your assets, including those you don’t know about. You can find unmanaged devices and see when assets come on or offline in your network. Additionally, runZero gives you full control of your scans and queries, including the ability to create custom queries, generating alerts for specific assets in your scan results.
Enrich assets with vulnerability data #
runZero leverages asset data from multiple sources, as well as its own unauthenticated scanner, to deliver full visibility into assets across any environment. Integrations with vulnerability scanners, like Tenable, Qualys, and Rapid7, will help you:
- Add additional asset context to your vulnerability data
- Find gaps in your vulnerability scan coverage
- Respond to emerging vulnerabilities faster
Search web screenshots for oddities, identify outliers, and see assets that may need to be patched with on-demand custom queries. For example, let’s assume developers were aware of Log4Shell on the first day. They weren’t able to immediately go into their systems to find and fix the vulnerability because no one had checks available on day one. As a result, teams typically had to wait for their vuln scanner to have the checks available and then wait for a maintenance window to scan their targets resulting in delays in their ability to assess and remediate issues.
During one of our case studies, a customer that had been using ServiceNow ITOM (IT Operation Management) realized they struggled with getting all of the asset data they needed. This was especially true for their unmanaged assets, but they didn’t have the desired data for their managed assets either. The customer said, “The team looked at Qualys as an alternative data source for ServiceNow Discovery, but the system (scanned through appliances) was too slow.”
Log4Shell highlighted the importance of having the ability to quickly search an existing inventory to find assets that may be impacted by a new vulnerability without having to run a new vulnerability scan. runZero was able to provide prebuilt queries to help customers find potentially affected assets before vulnerability scanners had checks available for products and services using the Log4J.
runZero exceeds the asset visibility requirements of BOD 23-01 #
CISA BOD 23-01 was created to strengthen the overall cyber security posture of federal civilian agencies by requiring improvements around asset inventory and vulnerability management. With several tools and methods being used to conduct these practices, the new timeline requirements will force agencies to evaluate existing processes to comply with BOD 23-01 runZero will unify and enrich asset data from your existing security tools to deliver visibility across your internally and externally facing assets. You can take runZero for a test run with our free 21-day Enterprise trial or get a demo to learn how runZero can help your business. Contact us if you’d like to test our self-hosted version.
















