Here’s a spooky stat for you: The most commonly accidentally exposed web management interface in the world isn’t on a router, or a printer, or a firewall. It’s the lowly IP camera, which is a favorite target of all major botnets these days. And how did it get there? Almost certainly via UPnP, which brings us to our tale….
As we approach my favorite holiday of the year (I like candy and ghost stories), we also approach the end of National Cyber Security Awareness month. It seems only fitting that in this spookiest of months, we tell a harrowing tale of discovery and mischief. So everyone sit back and listen to the story of…UPnP!
⛈️ thunder rumbles in the background ⛈️
UPnP? more like Boo! PnP #
UPnP™ is a standard suite of protocols and conventions that allow different devices on a home network to work together, much like the comet from Maximum Overdrive when it helped all the machines on Earth work together to throw off the yoke of human dominance. UPnP has definitely made configuring home networks easier, but at what cost?
The Bad Old Days #
UPnP, surprisingly, doesn’t officially stand for anything. However, the name is derived from “Universal Plug-n-Play”, which plays (and plugs?) off the Plug-n-Play buzz of the late 1990s and early 2000s.
Those of you of a certain age might remember the time before computer peripherals would “just work” when you connected them (often, they still don’t, but I digress). Back in the Before Times, configuring peripherals on a computer was often a very manual affair: you’d have to install drivers, deconflict IRQs (whatever those are), maybe even set a few jumpers on circuit boards. While this provided all sorts of fun for the people who enjoy that sort of thing, it wasn’t exactly easy.
There had been various attempts to make peripherals automatically configure themselves over the years, some more successful than others. However, it was Windows 95 that launched the term “Plug and Play” into the popular zeitgeist. You could, more often than not, connect something to your computer and it would just work! Once consumers got a taste for this, there was no going back!
From Computers to Networks #
Much like configuring devices all connected to one computer was relatively arcane in Ye Olden Days, configuring devices that were connected to lots of different computers at once was often even more arcane, bordering on eldritch.
Early home networking required users to manage IP addresses and set default routes. Early network-accessible devices like printers often needed manual configuration via cumbersome on-device interfaces and further manual configuration on the computers that were going to use those printers to print or scan or route.
“But wait!” the users cried. “Why can’t my networked devices also be plug-n-play?”
The industry heard their cries and, again, many different mechanisms and protocols sprung up.
UPnP, version 1.0 of which was published in 2008, builds on top of existing technologies (IP, HTTP, XML, SOAP, …) and provides a standard mechanism for devices on the same network to communicate, discover, and (sometimes) configure one another.
This was a major step forward. If your printer and computer both supported UPnP, you could ask your computer to search for printers and (with any luck), your printer would be found! It often wasn’t quite that simple, but it was still light years ahead of what came before.
The Call Is Coming From Inside The House! #
UPnP standardizes different device profiles. There are tons of profiles out there (see the Open Connectivity Foundation's list), ranging from printers to routers to scanners to telephones and more.
One of the more commonly supported profiles out there is a little profile I like to call the Internet Gateway Device Profile, because that’s its name. This profile is often supported by home routers and allows devices on the local network to discover information about the home network’s Internet connection.
This provides a standard mechanism for a lot of common problems. Computers on the local network can ask the router what the public IP address of the router is (since essentially all home networks use some form of Network Address Translation). They can ask the router for all sorts of information about its connection to the Internet, and about the local network. All of this can be done more-or-less automatically.
However, there is one bit of functionality in the Internet Gateway Device Profile that is…well, not evil per se but more “beyond our mere human conceptions of good and bad.” This functionality allows for systems on the local network to punch holes in the router’s firewall configuration and set up traffic forwarding.
“But Rob!” I hear you say. “Punching holes in firewalls is bad!” You’d think so, wouldn’t you? Well, when all this was happening, the Internet was a simpler, more innocent place. Some systems need to act, more or less, as servers on the Internet. While this was more common in the early days of the Internet, it’s not unheard of today.
Systems like video game consoles and VoIP phones want to listen to traffic coming in from the Internet to see if someone wants to join their game or make a phone Ring. Most home networks have every device masquerading behind a single public IP address and, as such, there’s no good way to figure out where to send new incoming connections and traffic.
UPnP allows systems to automatically request that port forwarding be set up. Any traffic sent to such a port on the router’s outside will get sent to a specific machine on the router’s inside. Problem solved! What’s even more fun, a lot of the routers given by ISPs to their customers come with UPnP enabled by default, residential and business! Your router might even have UPnP enabled right now! Dun dun dunnnnn!
Secret Passages, Ghost Printers, and Found Footage #
Of course, this system of allowing arbitrary port forwarding can be abused. The Conficker worm, one of the largest botnets ever, used UPnP to open ports on home routers, letting infected computers serve as proxies for the real command-and-control servers for the botnet.
Some home printers may appear haunted (I’d argue most home printers are haunted) when they request ports from the public Internet be forwarded to them so that they can print whatever anyone feels like sending them. IP cameras are notorious for opening ports on networks so that you (and anyone else who can get by their often weak security) can watch document in real time the descent into madness that occurs when you go hunting for witches outside of Burkittsville, Maryland.

Who ya gonna call? #
UPnP is still very common on home networks. It’s still commonly used to discover printers, scanners, media players, and other devices automatically so that you can stream your horror movie marathon from your phone to your TV.
But with all that power comes great responsibility, and that responsibility is often ignored. Devices will open your network’s gooey insides to the harsh outside world and forget to close things up. They can expose vulnerable systems to remote attacks that you’d think they were protected from. They can, in short, bypass a lot of the protections your firewall is supposed to provide. 😱
The good news is, runZero knows all about UPnP. We use UPnP (among many others) to discover devices on your home network. We can often detect if a device on the inside of your network is visible to the public Internet. We can tell you if a device is bridging two networks!
If you’d like to see all the UPnP on your network, just hop on to your handy runZero console and search up protocol:upnp. Behold!
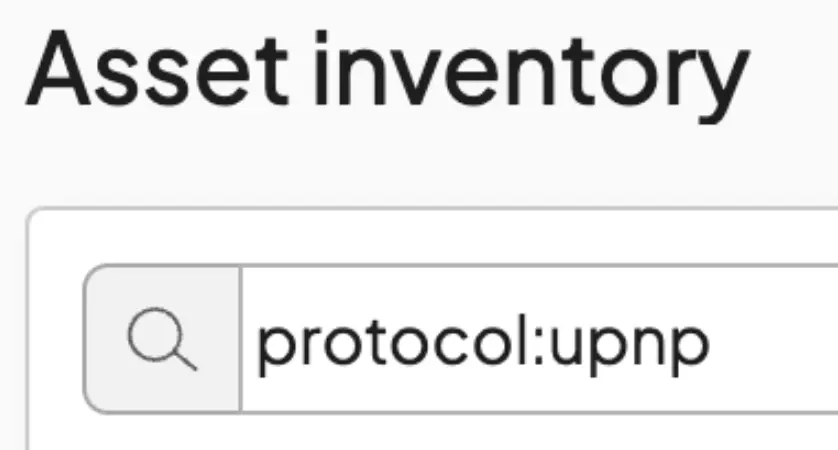
Look at all those devices in the runZero Lab!
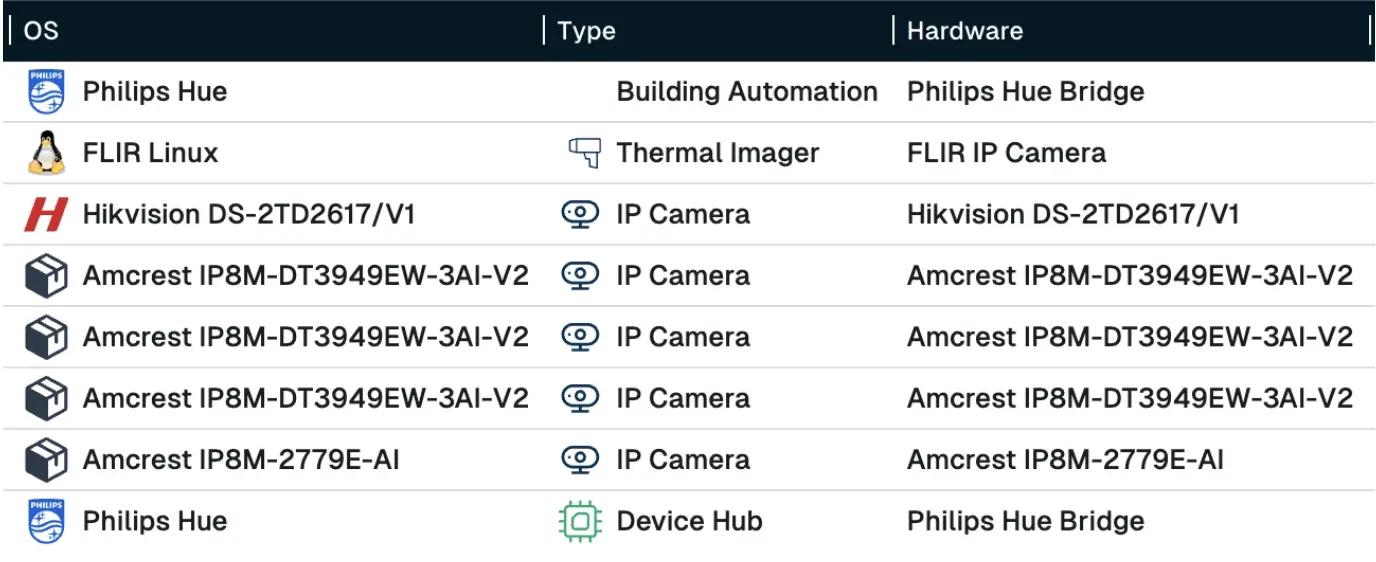
runZero isn’t satisfied just telling you that a device is running UPnP, though, take a look at all the extracted detail:
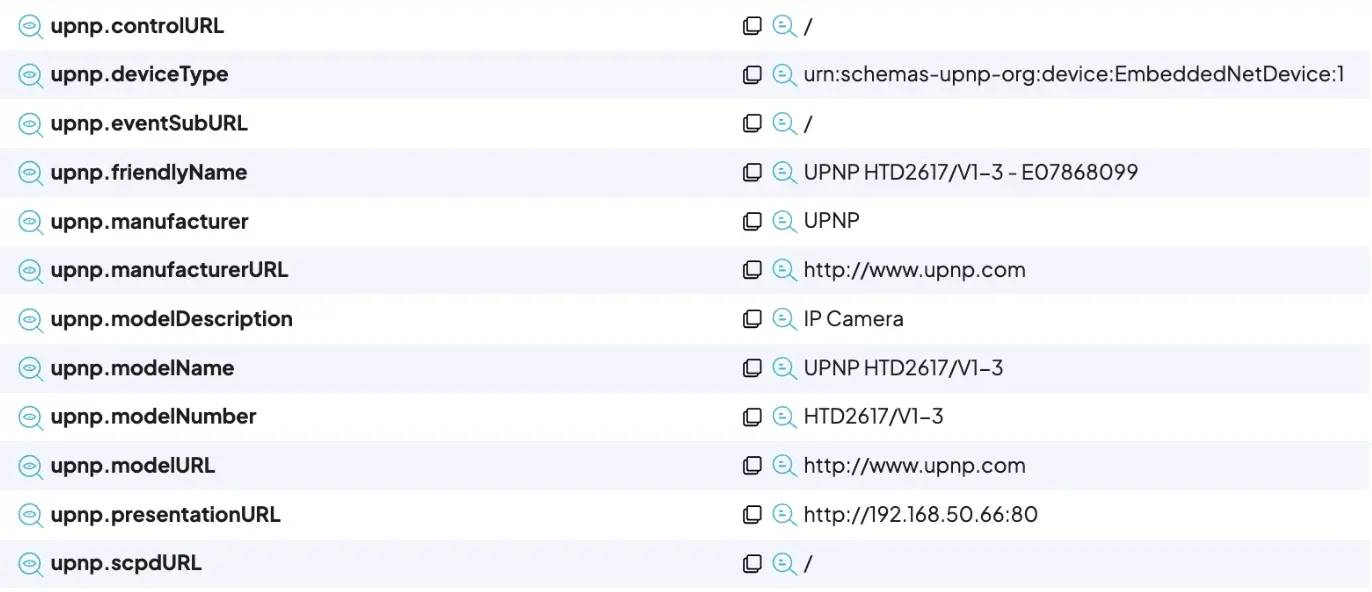
Remember, UPnP started out as a mechanism to discover devices on the network, so they’re often more than happy to tell you all about themselves!
The End…Or Is It? #
So, while UPnP can be scary, there is no reason to fear it on this All Hallow’s Eve (and National Cyber Security Awareness Month), because you can always give runZero a try!
















