What is network segmentation? #
Network segmentation, in its simplest form, is the act or practice of dividing a computer network into smaller parts, subnetworks, or network segments. In recent years,it has evolved into a foundational enterprise control to improve network performance and security. However, without effective verification strategies like Cyber Asset Attack Surface Management (CAASM), network segmentation can be easily undermined by misconfigurations and multi-homed machines.
Let’s explore a practical comparison to network segmentation – a house with an open floor plan. This design ensures ease of movement and makes the space feel larger, but presents a challenge for achieving privacy and security. You likely don’t want everyone that enters your home to have unfettered access to all areas. Adding walls and changing the architecture of a home is much harder after it's been built; however, doors and locks can help add security controls while maintaining the original functionality. For example, if a contractor is scheduled to work on the garage, doors and locks add a level of segmentation that ensures access is only granted for the area where the work needs to be done. Lateral movement into the house is unlikely and garage repair alone does not merit access to other areas. Essentially, network segmentation is akin to a house with defined areas of access to make safe and secure spaces when needed.
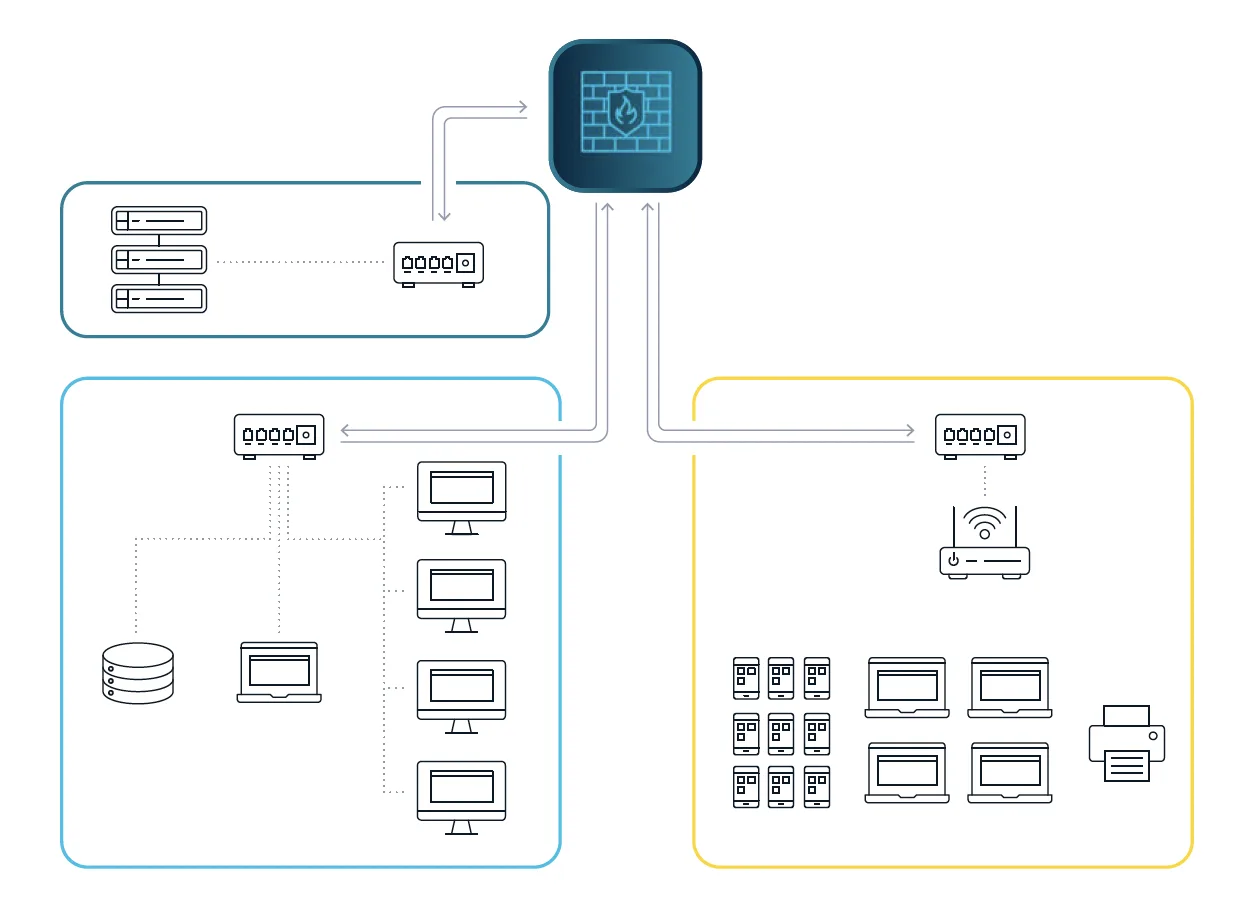
What are the benefits of network segmentation? #
Better operational performance Segmentation reduces network traffic congestion.
- Improved security:
Limit the damage done by cyber attacks: Segmentation improves cybersecurity postures by limiting how far an attack can spread by reducing lateral movement. For example, segmentation keeps a malware outbreak in one segment from spreading to systems in another.
Protect vulnerable devices: Segmentation can prevent harmful traffic from reaching devices that are unable to protect themselves. For example, on a factory floor that contains OT/ICS devices that were not designed with advanced security defenses, segmentation can stop harmful Internet traffic from reaching them.
Containing network problems: Segmentation minimizes the impact of local failures on other parts of the network. When localized problems arise, network segmentation helps to minimize production downtime and decrease corporate latency due to misconfigurations.
Controlling access: Access can be controlled by creating VLANs to segregate the network. For example, visitors can access a “guest network”, so they can access the Internet, but not the corporate network itself. Another example is separating networks during a corporate divestiture, so that employees only have access to the corporate network of their company and not the other.
Meet industry compliance standards Regulations are a driving factor in network segmentation. For example, businesses subject to Payment Card Industry Data Security Standard (PCI DSS) requirements must validate cardholder data environment (CDE) segmentation during the security audit process. The PCI guidance on scoping and segmentation describes a common CDE administration model.
How do you verify network segmentation is implemented correctly? #
Verifying that segmentation is working correctly can be challenging, especially across large and complex environments. Common techniques to validate segmentation, such as reviewing firewall rules and spot testing from individual systems can only go so far, and comprehensive testing, such as running full network scans from every segment to every segment, can be time intensive and are rarely performed on a regular basis.
Verifying safe network segmentation with CAASM #
Network bridge detection #
Network bridge detection is a useful tool when validating the effectiveness of network segmentation and testing whether an attacker can reach a sensitive network from an untrusted network or asset. Examples of this include laptops plugged into the internal corporate network that are also connected to a guest wireless segment, or systems connected to an untrusted network, such as a coffee shop’s wireless network that also have an active VPN connection to the corporate network.
The runZero Platform detects network bridges by looking for extra IP addresses in responses to common network probes (NetBIOS, SNMP, MDNS, UPnP, and others) and only reports bridges when there is at least one asset identified with multiple IP addresses. Typical hardening steps, such as desktop firewalls and disabled network services are limiting factors that will usually prevent multi-homed assets from being detected by runZero; however, the click-through demo below shows how to use network bridge detection to search for multi-homed assets in the runZero inventory.
Identifying Potentially Risky Network Bridges #
This runZero network bridge report is an interactive view of possible paths that can be taken through the network by traversing multi-homed assets. When detected, single IP addresses are omitted to keep the graph practical and actionable for defenders.
runZero enables you to click through asset and subnet details within the external (red) and internal (green) networks. Clicking a bridged node once will highlight the networks it is connected to and show a link which leads to the full asset details for that node. Alternatively, clicking a network once will highlight the connections to bridged nodes and show a link to the Asset Inventory page with a CIDR-based inventory search.
This report helps you see where segmentation may be broken, and can cut down on the number of surprises encountered in a future security audit.
The Asset Route Pathing Report #
The runZero Platform also enables you to visualize potential network paths between any two assets in an organization by creating the asset route pathing report. This unique methodology identifies surprising and unexpected paths between assets that may not be accounted for by existing security controls or reviews.
The report generates a graph of multiple potential paths by analyzing IPv4 and IPv6 traceroute data in combination with subnet analysis of detected multi-homed assets – without requiring access to the hosts or network equipment.
With a view of potential paths between assets, security professionals can verify whether a low-trust asset, such as a machine on a wireless guest network, can reach a high-value target, such as a database server within a cardholder data environment (CDE). Another example would be an OT asset (such as an engineering workstation) being able to access the IT network. This feature highlights potential network segmentation violations and opportunities for an attacker to move laterally from one segment to another.
Summary #
In summary, there are many benefits of network segmentation, and fact checking proper implementation can be a difficult, arduous task. runZero is here to help by reducing the burden of misconfigurations and/or improperly defined network boundaries, subnets and VLANS.
Not a runZero customer? Download a free trial today and achieve comprehensive asset inventory and attack surface visibility in minutes.
If you would like to read more about network segmentation and what runZero has found in the wild, check out Chapter 4 of the runZero Research Report that talks about the decay of segmentation.

















