This is the second post in a blog series looking into the Australian Government's 2023-2030 Cyber Security Strategy. You can find the first post in the series here.
In our first installment, we introduced the Australian Cyber Security Strategy and discussed how runZero operationalizes Cyber Shield 2. Part two now examines Cyber Shield 4 and the mandate for a Critical Infrastructure Risk Management Program.
Legislative background #
Since 2018, the Australian Government has enacted key cyber security legislation, starting with the Security of Critical Infrastructure Act of 2018 (SOCI Act). The SOCI Act established a framework to safeguard critical assets and paved the way for the subordinate laws that factor into Cyber Shield 4.
The Security Legislation Amendment (Critical Infrastructure) Act 2021, or SLACI Act, expanded the scope of the SOCI Act from 4 critical infrastructure sectors to 11 sectors, including communications, data storage and processing, financial services, water and sewage, etc.
The Security Legislation Amendment (Critical Infrastructure Protection) Act of 2022, or SLACIP Act, established the requirement to create and maintain a critical infrastructure risk management program (CIRMP) and introduced a new framework of enhanced cyber security obligations (ECSO) for operators of systems of national significance (SoNS). Rules for the CIRMP requirements were implemented in 2023, which defined the four hazard vectors that must be addressed by the CIRMP - cyber and information security, personnel, supply chain and physical.
Cyber Shield 4 - Protected critical infrastructure #
As a core component of the 2023-2030 Australian Cyber Security Strategy (the Strategy), Cyber Shield 4 focuses on strengthening the resilience and defense of the nation’s most vital systems. The central goal of this shield is to ensure that Australia's critical infrastructure and essential government systems can withstand and bounce back quickly from cyber attacks. By 2030, the aim is for every Australian to have peace of mind knowing that essential services — such as the electricity grid, water supply, and banking systems — are able to prevent, respond to, and be resilient against hazards that could disrupt their functions. The Australian Government plans to achieve this through the following initiatives.
Initiative 13: Clarify the scope of critical infrastructure regulation #
While the SLACI Act expanded the SOCI Act to 11 critical infrastructure sectors, recent incidents identified several gaps. Initiative 13 seeks to clarify and strengthen cyber security obligations, with emphasis placed on strengthening requirements for aviation and maritime sectors. Steps have already been taken to achieve this objective with the passage of the Transport Security Amendment Bill 2024, which aligned aviation and maritime cyber security requirements with those of other critical infrastructure sectors. A subsequent amendment in 2025 implemented requirements across the four hazard vectors for the aviation and maritime sectors.
Initiative 14: Strengthen cyber security obligations and compliance for critical infrastructure #
The SLACIP Act introduced a framework for safeguarding Systems of National Significance (SoNS). One of the goals of Initiative 14 is to expedite the implementation of the Enhanced Cyber Security Obligations (ECSO) Framework. The ECSO includes:
Developing cyber security incident response plans to prepare for cyber security incidents
Undertaking cyber security exercises to build cyber preparedness
Undertaking vulnerability assessments to identify vulnerabilities for remediation
Providing system information to develop and maintain a near real time threat picture
In April 2025, the Australian Government published updated guidance on implementation of the ECSO. This guidance states that a vulnerability assessment can include a documentation-based review, a hands-on assessment or automated scanning with software tools. This will be especially relevant when we dive into how runZero can help with achieving compliance with the ECSO.
This initiative also calls for increased outreach to critical infrastructure owners and operators to ensure they are aware of CIRMP and ECSO obligations and it calls for increased compliance monitoring.
Initiative 15: Uplift cyber security of the Commonwealth Government #
The Australian Government recognizes it is a major owner and operator of critical infrastructure and holds some of the nation's most sensitive data about its people, economy and national security. It must hold itself to the same high security standards it expects of industry. The core problem Initiative 15 seeks to address is the enduring and low levels of cyber maturity across many government entities, which have revealed major gaps in the security posture. The Australian Government plans to take action by enforcing higher security standards, building upon the Australian Signals Directorate's Essential Eight, and conducting regular reviews of the cyber maturity of Commonwealth entities.
The Essential Eight was originally developed in 2017 and has been regularly updated since. It outlines key mitigation strategies that should be implemented to prevent, limit and recover from cyberattacks. The most recent update occurred in November 2023 to strengthen requirements around patch management, multi-factor authentication and privileged access among others. The Essential Eight Maturity Model works in conjunction with the Essential Eight to provide a prioritized approach to implementation. Maturity Level One includes automated asset discovery and vulnerability scanning, which we will touch on later.
This initiative also calls for the identification of Systems of Government Significance, similar to previously discussed SoNS, and the development of standards to protect these assets. In July 2025, the Australian Government Protective Security Policy Framework Release 2025 was published along with Systems of Government Significance Standard. As of the date of this publication, the SoGS Standard does not appear to be publicly available.
Initiative 16: Pressure-test critical infrastructure to identify vulnerabilities #
While the Australian Government has learned a lot of lessons from past incidents and taken many steps to strengthen its national security posture, it also recognizes that it must be more proactive in the future in order to stay ahead of malicious actors. Initiative 16 calls for a National Cyber Exercise Program to proactively exercise incident response plans and communications channels at a national level. It also calls for the development of incident response playbooks based on lessons learned from these exercises.
The runZero advantage #
runZero supports Cyber Shield 4: Protected Critical Infrastructure by helping organizations bridge the gap between the Strategy's policy intent and operational execution, specifically regarding visibility, risk management, and compliance obligations. In each of the maturity levels in the Essential 8 Maturity Model, there are several mitigation strategies that call for having “An automated method of asset discovery [...]”.
Let’s take a closer look at how runZero can help achieve that.
Unified insight of attack surfaces #
runZero’s own unique ubiquitous discovery comes from combining the best of API connectors and our active and passive scanner. The proprietary, unauthenticated scanner safely elicits information as a security researcher would, extracting asset details and accurately fingerprinting operating systems, services, and hardware. Our passive traffic sampling can be used as an always-on discovery continuously listening to traffic especially when runZero is not actively scanning the network. That can be beneficial for environments where you have sensitive and fragile OT/IoT devices, especially in organizations deemed as part of Critical Infrastructure. The 3rd party connectors provide even more comprehensive insight into your cyber assets by ingesting and correlating with cyber asset data from IT and security tools in your technology stack.
runZero was built to support different environments, you can easily deploy scanners, called Explorers, to scan assets that are inside your network behind the firewall but also discover your external attack surface. Our Explorer can be installed inside your cloud instances to scan your virtual machines or leverage our integrations with the major cloud service provider to easily import relevant instances into runZero.
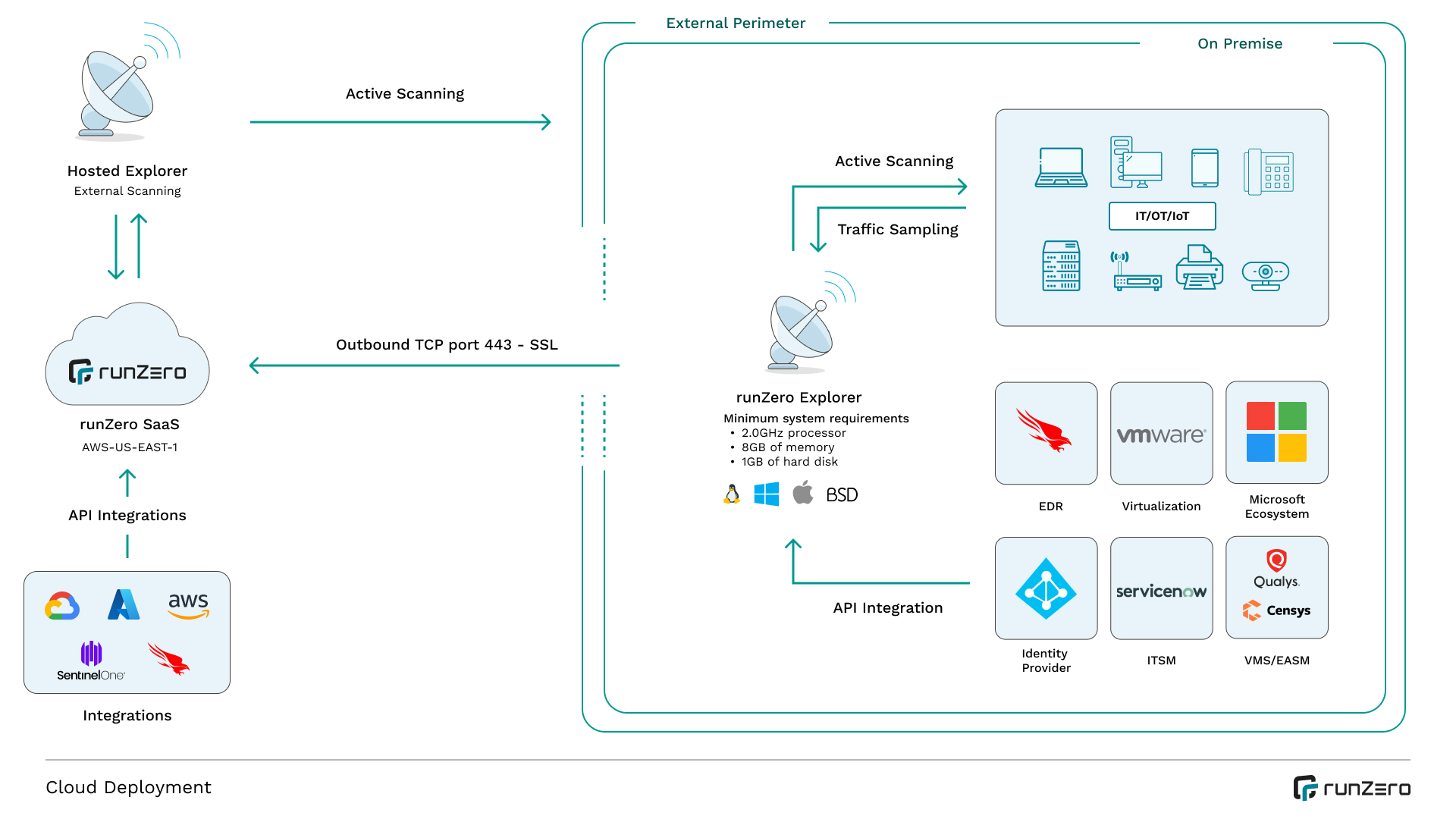
When it comes to scanning your external attack surface, we provide a runZero-hosted Explorer in the cloud that will discover external-facing assets and show what ports and protocols are visible from the internet. We support different data points for discovery scope such as public IP ranges (AS), country codes, ASN numbers and domains.
Mitigate exposure before compromise #
All three Maturity Models of the framework call for “Operating systems that are no longer supported by vendors are replaced.” and that is across Microsoft Windows-based internet-connected networks (especially ones running Windows 10 EOL operating systems) and runZero can help meet that for not only external or cloud perimeter but also internal that are non-Windows based. With our advanced search capability, you can easily and quickly surface assets running end of life operating systems including IT/IoT/OT devices. We also track extended OS end of life for certain operating systems that have extended support via the manufacturer. Simply typing has_os_eol:t will build a list of assets in the environment that were discovered by runZero but also imported via third party solutions that are running end of life OS.
You can easily export the result of that query or consume it via APIs to feed the list of unsupported OS to your remediation tools to upgrade the operating system.
As it relates to the Patch applications Mitigation Strategy, runZero can ensure you are accounting for all of your assets to confirm the relevant applications are patched and updated. The framework specifically calls out blocking Internet Explorer 11 which can be easily surfaced by using runZero’s software query vendor:="Microsoft" AND product:="Internet Explorer" and version:11. With third party integrations with EDR/MDM solutions, runZero can surface what applications are installed on the discovered assets.
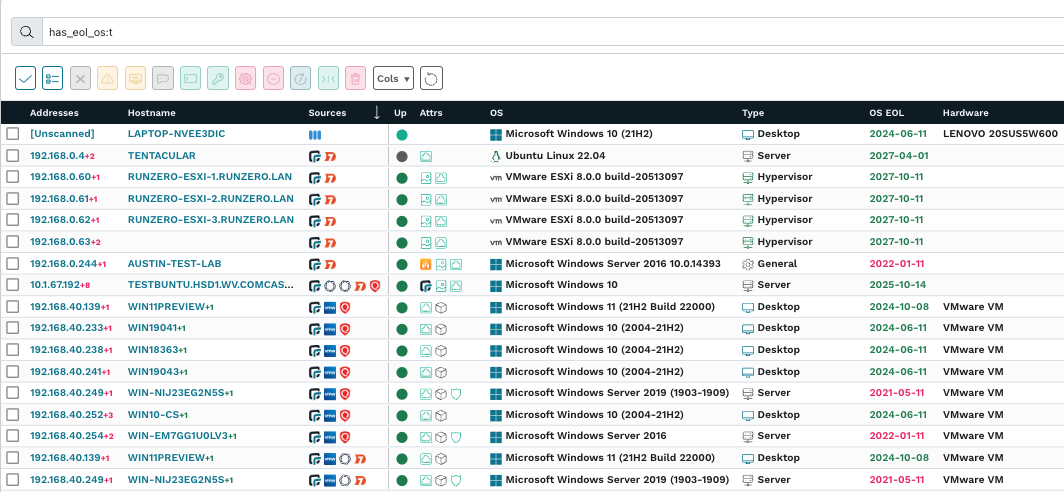
e also track extended OS end of life for certain operating systems that have extended support via the manufacturer. Simply typing has_os_eol:t will build a list of assets in the environment that were discovered by runZero but also imported via third party solutions that are running end of life OS.
You can easily export the result of that query or consume it via APIs to feed the list of unsupported OS to your remediation tools to upgrade the operating system.
“An automated method of asset discovery is used at least fortnightly to support the detection of assets for subsequent vulnerability scanning activities.” - Essential Eight Maturity Model
There is a reason why the asset discovery piece was decoupled from the vulnerability scanning activity and that’s because vulnerability scanners don’t do a good job discovering and keeping an accurate inventory of assets.
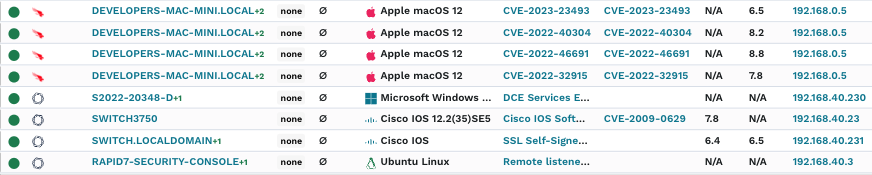
By unifying runZero’s native vulnerability discovery alongside our integration with Nuclei-based scanning and third-party vulnerability data ingestion, you will get unparalleled context for your security posture. This integration allows organizations to identify blind spots in scan coverage and expedite the response to emerging threats. That will improve the decision making required to implement security controls needed to be in place with the other solutions to reach the different maturity levels.
As the regulatory landscape tightens under Cyber Shield 4, the mandate for comprehensive risk management is clear: you cannot secure what you cannot see. Meeting the rigorous standards of the SOCI Act and the Essential Eight requires more than just policy — it requires absolute clarity into your digital environment. By automating asset discovery and unifying visibility across IT, OT, and cloud infrastructure, runZero provides the foundational data needed to bridge the gap between legislative intent and operational resilience.
Start your free trial today.

















