Keeping assets safe is a big part of security programs. But how can you keep your assets safe if you don't even know about them? That's where asset inventory comes in. Some people try to build an asset inventory using vulnerability scanners. Others combine that vulnerability data with information about their unmanaged assets, even orphaned and rogue devices. That’s what cyber asset attack surface management (CAASM) is about.
Ways vulnerability scanners fail at asset inventory #
Theoretically, security teams can scan their entire local network for vulnerabilities. In practice, it’s too difficult operationally. Let’s dig into this.
- Corporate IoT and OT equipment
Many vulnerability scan configurations exclude IoT and OT devices. Offices contain many IoT devices like your printers, thermostats, and surveillance cameras. Robotic arms, biomedical devices, and traffic signs are examples of operational technology (OT) devices. They often rely on archaic or uncommon network stacks that can’t handle unexpected input from an aggressive security probe. The device easily freezes or crashes, so security teams exclude them from most vulnerability scans. Some vulnerability scanners are smart enough to detect and automatically exclude fragile devices, but in doing so they also leave a gap in the asset inventory. - Long scan times
Vulnerability scanners need to cover hundreds of thousands of exposures, each of which requires time and bandwidth to complete. Extrapolate this requirement to your entire enterprise and it’s not a surprise that some vulnerability scans can take weeks to complete. These slow scan cycles lead to stale asset data, and becomes even more so when a scan needs to be split across multiple maintenance windows. - Phantom assets
Some vulnerability scanners have trouble differentiating between a response from an actual device and an intermediate firewall response or proxy reflecting the traffic. You end up with non-existent devices in your inventory, sometimes even with operating system details.
The point of cyber asset attack surface management is to have a full and accurate inventory of what is connected to your network, from IT to OT, cloud to remote devices. If your data is incomplete or inaccurate, it’s just a list of some assets, not an inventory. Leading vulnerability scanners do not provide a full, accurate, current asset inventory in everyday practice.
Insufficient details from credential-less vulnerability scans #
Many vulnerability scanners support a discovery-only mode, or “host discovery mode”, that avoids using credentials and security probes. While it avoids using credentials, is faster, and can uncover more unmanaged devices, the results are only marginally better than an ICMP response.
Here’s an example of device details detected by a discovery-only scan of a leading vuln scanner:
- IPv4 address: 192.168.40.248
- MAC address: 00:0c:29:59:c4:65
- Public: No
- First seen: 05/24/2023 10:39AM
- Last seen: 05/24/2023 10:39AM
It essentially only includes the IP and MAC addresses of the discovered device – not enough information to be useful for asset inventory.
Potential vuln scanner limitations for managed devices #
Vulnerability scanners are a giant collection of security probes you hope can find all the vulnerabilities before the adversary. A vulnerability scanner should be able to collect a ton of information on the devices it can log into. However, vulnerability scanners are not purpose-built for asset inventory and don’t collect as much information as you need in a cyber asset inventory.
Here are the details for the same device as above with a standard authenticated scan by the same product:
- IPv4 address: 192.168.40.248
- MAC address: 00:0c:29:59:c4:65
- Public: No
- First seen: 05/24/2023 10:39AM
- Last seen: 05/24/2023 10:39AM
- Installed software:
- cpe:/a:apache:http_server:2.4.41
- cpe:/a:apache:http_server:2.4.99
- cpe:/a:openbsd:openssh:8.2
- cpe:/a:elasticsearch:logstash:7.17.6
- Vulnerabilities:
- High, Ubiquiti UniFi Network Log4S…, 10, 9.3, 05/24/2023
- Medium, TLS Version 1.0 Protocol Det…, , 6.1, 05/24/2023
- Medium, SSL Certificate Cannot Be Tru…, , 6.4, 05/24/2023
- Medium, SSL Medium Strength Cipher…, 6.1, 5, 05/24/2023
- Medium, SSL Certificate Cannot Be Tru…,, 6.4, 05/24/2023 125 additional vulnerabilities…
Asset information from this leading scanner includes more details on software and vulnerabilities but few additional asset details, such as exact operating system version or hardware platform.
And the same device scanned by runZero:
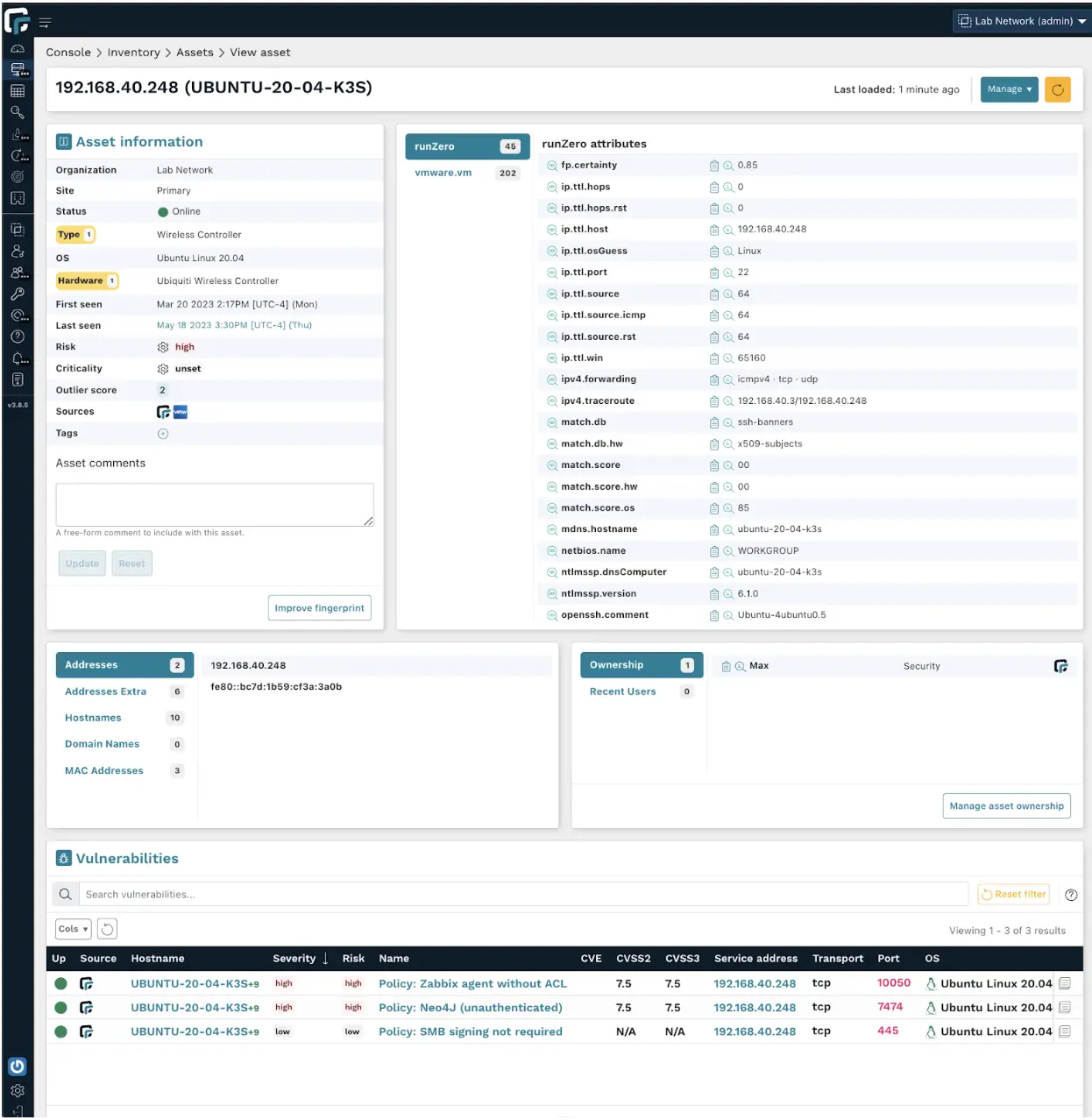
Comparing scans #
Let’s compare and contrast what each solution found:
| Host Discovery Scan | Full Vuln Scan | runZero | |
|---|---|---|---|
| First seen | ⏺ | ⏺ | ⏺ |
| Last seen | ⏺ | ⏺ | ⏺ |
| IP address | ⏺ | ⏺ | ⏺ |
| Secondary IPs | ○ | ○ | ⏺ |
| MAC address | ⏺ | ⏺ | ⏺ |
| Seen by sensor/scanner | ⏺ | ⏺ | ⏺ |
| Device type | ○ | ○ | ⏺ |
| Operating system | ○ | ○ | ⏺ |
| Hardware | ○ | ○ | ⏺ |
| Outlier score | ○ | ○ | ⏺ |
| Vulnerabilities | ○ | ⏺ | ⏺ |
| Hostnames | ○ | ○ | ⏺ |
| Domain names | ○ | ○ | ⏺ |
| Ownership | ○ | ○ | ⏺ |
| Recent user | ○ | ○ | ⏺ |
| Open ports | ○ | ○ | ⏺ |
| Searchable banners | ○ | ○ | ⏺ |
| Protocols | ○ | ○ | ⏺ |
| Software products | ○ | ⏺ | ⏺ |
| Upstream switches & ports | ○ | ○ | ⏺ |
runZero creates an asset inventory from multiple sources, one of which is its proprietary scanner, which does not require credentials. Though it’s an unauthenticated, active scanner, it gathers more details than a vulnerability scanner’s authenticated active scanner because it was purpose-built for asset inventory.
Beyond a lack of detail, vulnerability scanners sometimes simply get it wrong. A large telecom customer used a leading vuln scanner and runZero to scan the same device. The leading vuln scanner fingerprinted it as a CentOS Linux device, but runZero accurately identified it as an F5 load balancer, which happened to be running a CentOS-based firmware. Though the vulnerability scanner was superficially accurate, the shallow detail misled the security team to de-prioritize the risk from that device. A public-facing load balancer and a smart light bulb with a private IP address are meaningfully different for a security team. Knowing the operating system is simply not enough.
Unintended risk exposure while verifying vulnerabilities #
Vulnerability scanners must use authenticated active scanners to get onto devices to verify on-box vulnerabilities. Unfortunately, if an adversary has compromised or added any device on the network, they can collect and reuse those credentials for privilege escalation or lateral movement. Limiting the scan scope and only scanning trusted devices makes sense, but that further widens the gaps in your asset inventory.
Risks and uncertainty due to missing devices #
You can't even pretend to manage your security posture if you don't have a full asset inventory. How can you find end-of-life (EOL) devices, insecure configurations, and vulnerabilities if you don't even know what's on the network?
Gaps in your asset inventory mean uncertainty. Vulnerability scanners are superb at probing devices to verify the presence of CVEs, as long as you scan everything you should. Scoping scans without knowing where all devices are means you are not scanning your whole network. It is no surprise that the assets missed by vulnerability scans are often unmanaged devices that are behind on patches; after all, the scanner doesn’t have the credentials to authenticate to them so it cannot do a full assessment. These are the types of devices that an adversary hunts for when looking for a foothold in the environment.
CAASM solutions leverage vulnerability data but go far beyond. #
You now understand why vulnerability scanners alone cannot answer the question of asset inventory. However, they can be part of the solution.
CAASM solutions combine vulnerability data with other sources:
-
Corporate security solutions via APIs: Many CAASM solutions integrate with EDR, MDM, vulnerability management solutions, and even productivity tools such as Google Workspace to cover all managed devices.
-
Modern network scanners: Some of the best CAASM solutions also use specialized network scanners optimized for asset inventory to find unmanaged IT and OT devices.
As a best practice, all organizations should scan for vulnerabilities wherever possible, prioritize quickly, and remediate them swiftly. An effective vulnerability management program is an essential defensive undertaking for any mature security organization. A full asset inventory stands alongside vulnerability scanning as a core component of the overall program. Learn more about how asset inventory can improve vulnerability management.
runZero covers assets from IT to OT, cloud to remote devices #
runZero is a cyber asset attack surface management solution. It combines integrations with vulnerability management and other sources with a proprietary network scanner that is fast and safe even on fragile IoT and OT networks.
runZero scales up to millions of devices, but it’s easy to try. The free 21-day trial even downgrades to a free version for personal use or organizations with less than 256 devices. Find out what’s connected to your network in less than 20 minutes.
















