On November 18th, 2025, the United States Department of Defense (DoD) released authoritative guidance for implementation of Zero Trust (ZT) principles in operational technology (OT) environments, ZT for OT Activities and Outcomes. This guidance comes as a result of DTM 25-003, which mandated that all DoD components achieve, at minimum, Target Level Zero Trust for OT systems. The new guidance helps DoD components align their OT infrastructure to the broader ZT implementation across the DoD, specifically helping to define OT-specific ZT requirements.
All DoD components are expected to implement this guidance on control systems and operational technology (OT) across all unclassified and classified systems (including national security systems). The one caveat is that the guidance only extends to the boundary of Weapon Systems (WS) and Defense Critical Infrastructure (DCI). For example, the guidance applies to the electrical distribution system that provides power to the WS, but not the WS internal targeting or firing systems.
Applying zero trust to operational technology #
While the core principles of ZT – data protection, strong authentication, network segmentation, and threat monitoring – still apply to OT systems, "applying standard IT security approaches to OT environments can be ineffective and potentially dangerous" (source). OT and IT environments are fundamentally different, and therefore have different cybersecurity needs, risks, challenges, and outcomes. OT systems often prioritize availability, reliability, and safety over common IT principles of confidentiality and integrity. In addition, unique industrial control protocols, like DNP3, Modbus, or BACnet, are utilized as opposed to more ubiquitous IT protocols, limiting security controls. Thus, the goal of the guidance is to help address these critical differences, and "provide a precise and effective path to ZT implementation" in OT environments.
ZT for OT Activities and Outcomes is intended to be a set of high-level requirements for OT systems owners allowing for flexibility and adaptability in application. Because of this, an abstracted OT topology is utilized in the guidance as opposed to standards like the Purdue Model, or IEC 62443. Comprising two layers rather than the traditional five, the guidance collapses layers 3 and 4 of the Purdue Model into the Operational Layer and layers 0-2 into the Process Control Layer.
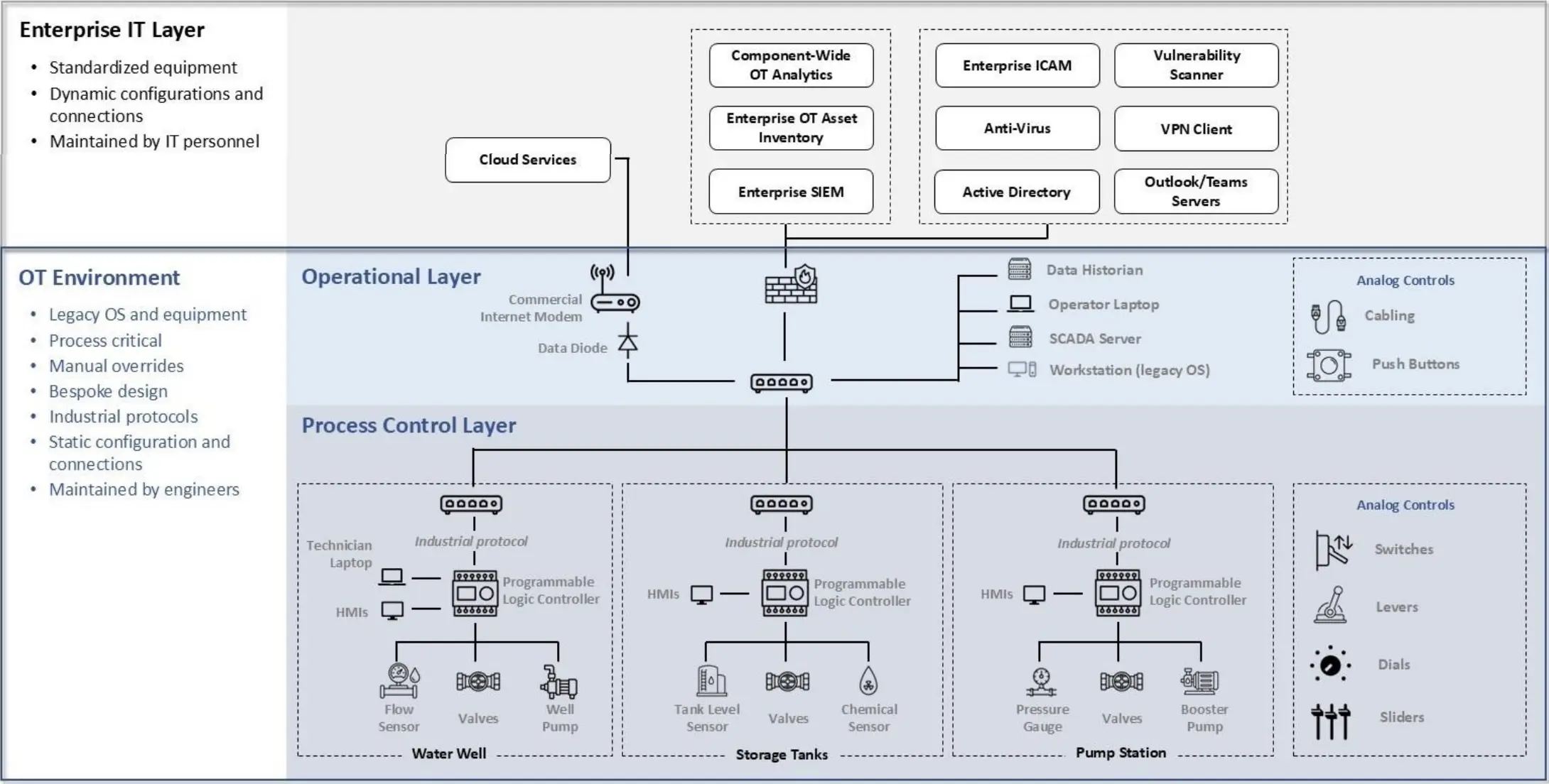
The Enterprise IT Layer contains general IT systems like email servers, VPN gateways, Active Directory servers, and credentialing services that exist across the entire DoD enterprise. An OT system does not need the Enterprise IT layer to function, but its efficacy could be reduced. runZero would advise that while the convergence of IT and OT systems certainly has increased certain aspects of usability, it also has increased the attack surface, and organizations should take extra care when connecting OT systems to Enterprise IT or cloud-based services.
The Operational Layer comprises components that might resemble Enterprise Layer components, but are specific to the OT system and thus should be treated differently. An example of this is a firewall that lives with the OT system specifically inspecting OT protocols that could be exempt from Enterprise IT patching schedules to ensure adequate testing is done before an update, to reduce the chance of a disruption in the environment. The operational layer also contains components like the data historians or SCADA servers.
The Process Control Layer contains the devices that interact with the real world like sensors and motors, Programmable Logic Controllers (PLCs), and Human Machine Interfaces (HMIs). While this layer of the OT system is usually isolated or air-gapped, the guidance in ZT for OT Activities and Outcomes should be applied to mitigate attack vectors like insider threats, supply chain attacks, or data transfer attacks, which are still possible.
Zero trust attainment #
The DoD specifies two levels of attainment of ZT activities for both IT and OT systems: Target and Advanced (source).
Target Level ZT #
"Target Level ZT is the minimum set of ZT capability outcomes and activities necessary to secure and protect the Department's Data, Applications, Assets, and Services (DAAS) to manage risks from currently known threats".
Target level activities are expected to be implemented across all DoD components and are considered to be feasible amidst design, development, and testing within OT systems.
Advanced Level ZT #
"Advanced Level ZT capabilities include the complete set of identified ZT capability outcomes and activities that enable adaptive responses to cybersecurity risk and threats and offer the highest level of protection".
Advanced level activities are considered to be additional long-term goals but do not carry the deadline of the Target timeline and may require capabilities that are not possible in all OT systems or within strict time frames.
Physical security considerations for OT environments #
The ZT for OT Activities and Outcomes provides a framework for a cybersecurity approach to securing OT systems. While it does not cover physical security or physical access components, without physical safeguards in place, cybersecurity controls are insufficient to prevent compromise. "A layered approach is recommended to achieve the outcomes defined by the ZT for OT Activities". Physical security, while not a pillar of Zero Trust, is essential to ensure a "holistic and effective ZT implementation, strengthening the resilience of critical OT environments".
How runZero can help #
The Department of Defense's guidelines might have just been released, but it’s never too early to get a start on protecting your OT environment. See how runZero can help you protect your OT environment and help you align with the ZT for OT Activities and Outcomes guidance from the Department of Defense.
















