Hey internet! Back in early February, we told you about CISA's new BOD 26-02 on end-of-support (EOS) devices on federal networks – specifically, edge devices, like firewalls, VPNs, routers, switches, proxies, all that. You know, the first (and often last) line of defense you have standing between the world's criminal masterminds and super-spies, which really, really should be getting regular care and feeding.
At first, we were all very excited about this BOD. It reads a whole lot like BOD 22-01, which is the binding operational directive that spawned the KEV, which is one of the most useful, free-to-use vulnerability intelligence resources the US Government has ever produced (of course, only if you use it correctly).
Alas, CISA has decided to make their list of identified EOL edge devices private, rather than blasting it out to the world. This is a real bummer, but it really does highlight how special the CISA KEV really is. As a former federal employee, I am here to tell you that when it comes to civilian government (and most other large enterprises), the default stance is to keep your mouth shut. Even in the best of times, cybersecurity people are often stingy with any scrap of intelligence, lest you accidentally inform the enemy on what's up with your infrastructure, and the federal government, doubly so.
I do expect that the list that CISA is compelled to produce in the BOD will get out regardless, since they've already committed to share it privately with state, local, tribal, and territorial governments (SLTT) and critical infrastructure providers (CI), but it won't be published in a formal or referenceable (or remixable or collidable) as the KEV.
Find EOL/EOS devices with one simple query #
But in the meantime, we wanted to let runZero customers know how you can approximate the spirit, if not the letter, of what BOD 26-02 is after. It comes down to a fairly straightforward asset query:
os_eol_extended:<=now AND has_public:t AND NOT (type:Server OR type:Desktop OR type:Laptop)What this does is go over your already-collected inventory and looks for those devices that are a) in "EOL Extended" state, which is runZero's tag for those devices that are so end-of-life/end-of-service they will never see another security fix, b) exposed to the internet, and c) isn't a normal server, desktop or laptop.
Now, excluding (c) there is a little bit dubious – you probably also don't want EOS stuff that people are actually using to type email and surf the web, all naked and exposed to the wild and woolly internet – but this gets you to a place where you can seek out all those "devices" discussed on BOD 26-02, like so:
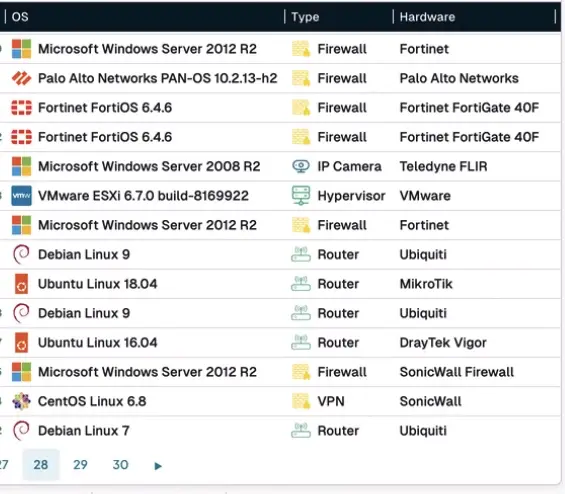
(This is a particularly dirty network, and yours is certainly not this awful, but you get the idea.)
At any rate, we'll be fiddling with this over the next couple of weeks, and have a pretty self-contained single push-button thing to get you ahead of any BOD 26-02 worries, much like how we do with Section 889 compliance. And if you don't already know about Section 889… the feds certainly do, so you probably should too.



















