Overview
Manually contextualizing honeypot alerts is a time consuming process. Cybersecurity expert Justin Varner walks us through how to orchestrate GreyNoise, runZero, and Thinkst Canary together with Tines.
Justin’s solution automates triaging with GreyNoise, discovering the offending device with runZero, and consolidating data from all three sources into a single record in the runZero console. No matter if the offending machine is internal or external, Justin’s Tines story can reduce your time to investigate these high-fidelity alerts from Thinkst, enriched with up-to-date threat intel from GreyNoise and unparalleled asset detail from runZero.
Justin Varner has been in the security industry for the past 18 years. He shares his thoughts on the importance of asset inventory, and how it can be leveraged alongside SOAR, threat intelligence, and detection technologies. Justin is currently part of the Thinkst Canary Partner Program and is an active speaker on the security conference circuit.
Better Use of Your Tines: How to map Canary alerts to assets in runZero
As a Principal Solutions Architect, my job is to improve security programs and recommend ways companies can improve their breach detection capabilities.
One of use cases that comes up quite often is reducing operational overhead on incident response teams. These teams are usually overwhelmed with the number of alerts they’re getting and spend a ton of time chasing down false positives. In my role, I am constantly look for new ways to approach breach detection, and breaking away from the traditional paradigm of finding needles in a haystack. I often think about how teams can leverage automation to triage alerts more effectively and focus on the issues that are really going to impact them. How can I take a process, that is usually complex and manual, and streamline it so teams can stay on top of emerging threats?
There are an incredible number of tools out there that are in position to help teams who want to save time, and zero in on the critical issues affecting them. Some of these tools are changing the game in the asset inventory, threat intelligence, SOAR (security, orchestration, automation, and response), and detection technology space. Based on my experience using these tools, I am going to share how you can use Tines, a SOAR platform, to automate sending alerts generated by Thinkst Canary to GreyNoise for context. Then, extracting the metadata used by Greynoise to tag runZero assets, so that you can continuously maintain a comprehensive inventory with rich, full details.
Benefits of asset inventory and automation
Here are some of the reasons why these tools and this approach will help you:
- Maintaining an accurate asset inventory is critical to managing your attack surface. As the old saying goes, “You can’t protect what you don’t know.” runZero excels at making sure you know what you need to protect. It’s the first product that can accurately identify assets and continuously update them in real-time.
- Canary alerts are typically some of the most important alerts that your organization will receive. It’s imperative to quickly understand the full context of the alert to determine the severity of the threat (this is where GreyNoise comes in) and respond accordingly.
- A variety of emerging threats loom every day that could directly impact your organization in a significant way. Solarwinds and Log4J are two recent examples of major threats that wrecked a multitude of organizations. If you happened to use GreyNoise and runZero back then, you had the benefit of the most current threat intelligence from GreyNoise coupled with the ability for runZero to dynamically check assets that were potentially vulnerable by searching for the Apache logging framework across your inventory.
- Once you add Tines to the mix, you have the ability to stay on top of these emerging threats and respond swiftly to mitigate the potential impact to your organization. Tines is a powerful security automation platform, but you don’t need to understand advanced programming concepts to use it like most of the other SOAR products out there. This makes a previously complex task of integrating multiple services with disparate APIs easy with Tines.
Set up all the tools
The following walk-through shows how you can use Tines to automate sending alerts generated by Thinkst Canary to Greynoise to gather threat intelligence. Then, you’ll learn how to extract the metadata used by Greynoise to automatically tag runZero assets.
Let’s get everything ready.
Step 1: Create your Tines account
Start by creating a free Tines community account, which provides a generous allotment of resources.
Tines uses the concept of stories that consist of a variety of actions used to automate various routine tasks that people shouldn’t have to do. You have more important work to do. Let Tines handle the mundane and error prone tasks.
Learn more about Stories, Actions, and the other elements of Tines.
Step 2: Create your Thinkst Canary account
You’ll need a paid subscription to Thinkst Canary and the API must be enabled. Send an email to their amazing support team using support@canary.tools and they’ll get you sorted.
Step 3: Create a resource for Thinkst Canary in Tines
In your Canary console, navigate to the API section under global settings to retrieve the domain hash and auth token. You’ll need to add these values to Tines in order to successfully run the story.
In Tines, create a resource named canary_tools_tenant_id with the value of your domain hash and a credential named canary_tools_api_key with the value of your auth token.
Step 4: Create your GreyNoise account
GreyNoise provides a community API for free, but this particular story requires the GreyNoise enterprise API due to the metadata that we need to extract from the assets. Find your API key. You can start a 30 day trial to obtain a temporary API key.
Step 5: Set up a credential for Greynoise in Tines
Create a credential in Tines named greynoise_api_key with the value of your Enterprise API key.
Step 6: Create a runZero account
And finally you’ll need a runZero account. You can start a 21-day trial for access to all the features runZero has to offer, including the necessary API access needed for this tutorial.
Step 7: Set up a credential for runZero in Tines
Go to the runZero console, generate an API token for your organization by navigating to Organizations. Click your organization name, scroll down to the API tokens sections, and click Generate API Key. Copy the API token.
Then, in Tines, create a credential named runzero_organization_api_key with the value of your organization’s API token from runZero.
Pull everything together with Tines
Now, everything is in place to construct a Tines story that will orchestrate sending IPs from Thinkst Canary alerts to GreyNoise for context and tagging, and then finally, to runZero to build your asset inventory.
The following story is available in the Tines Story Library. Here is what the story will look like:
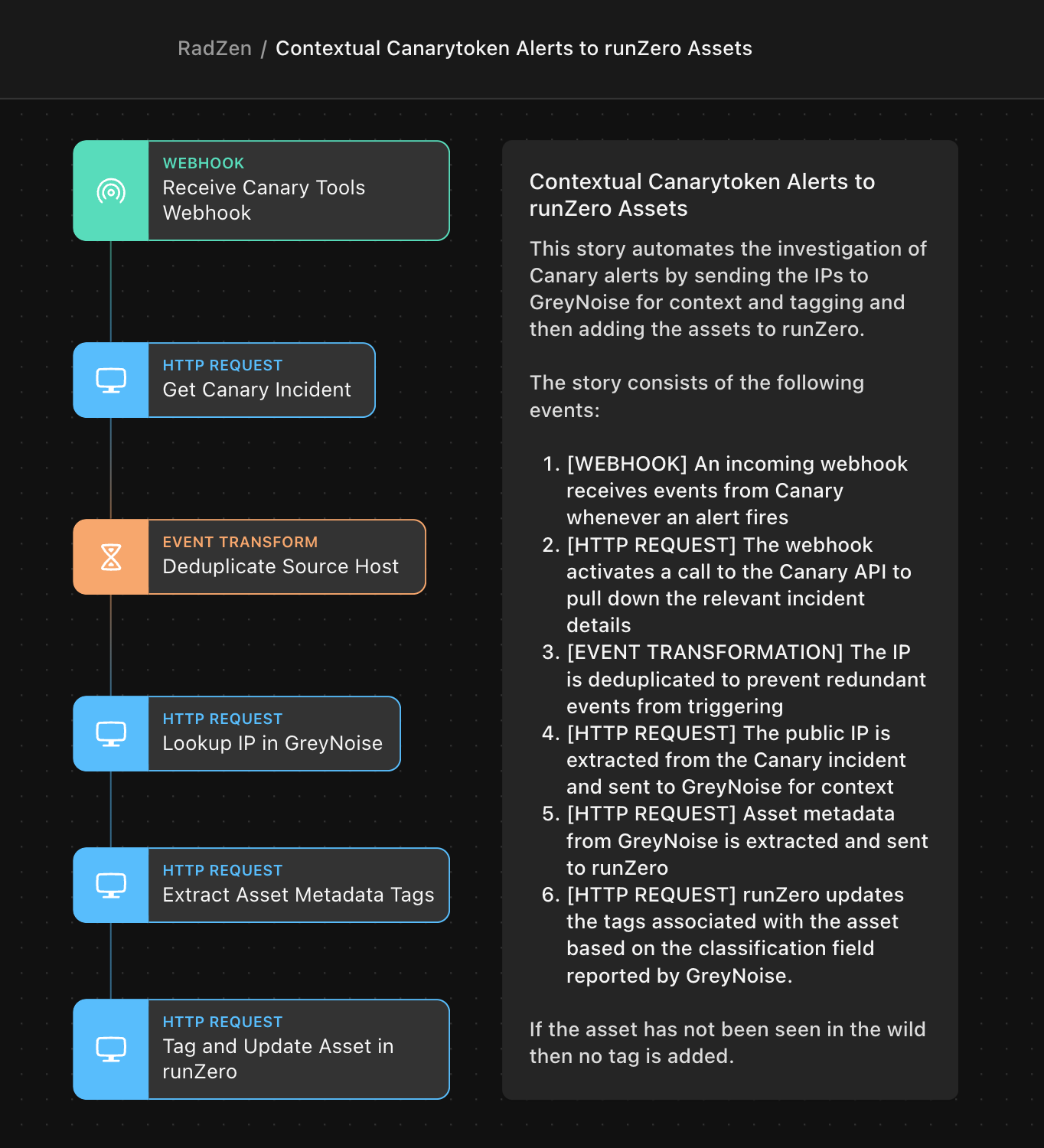
The story consists of the following events:
- [WEBHOOK] - An incoming webhook receives events from Canary whenever an alert fires
- [HTTP REQUEST] - The webhook activates a call to the Canary API to pull down the relevant incident details
- [EVENT TRANSFORMATION] - The IP is deduplicated to prevent redundant events from triggering
- [HTTP REQUEST] - The public IP is extracted from the Canary incident and sent to GreyNoise for context
- [HTTP REQUEST] - Asset metadata from GreyNoise is extracted and sent to runZero
- [HTTP REQUEST] - runZero updates the tags associated with the asset based on the classification field reported by GreyNoise.
If the asset has not been seen in the wild then no tag is added. You can optionally send these alerts to a third-party endpoint of your choice like Slack or Jira.
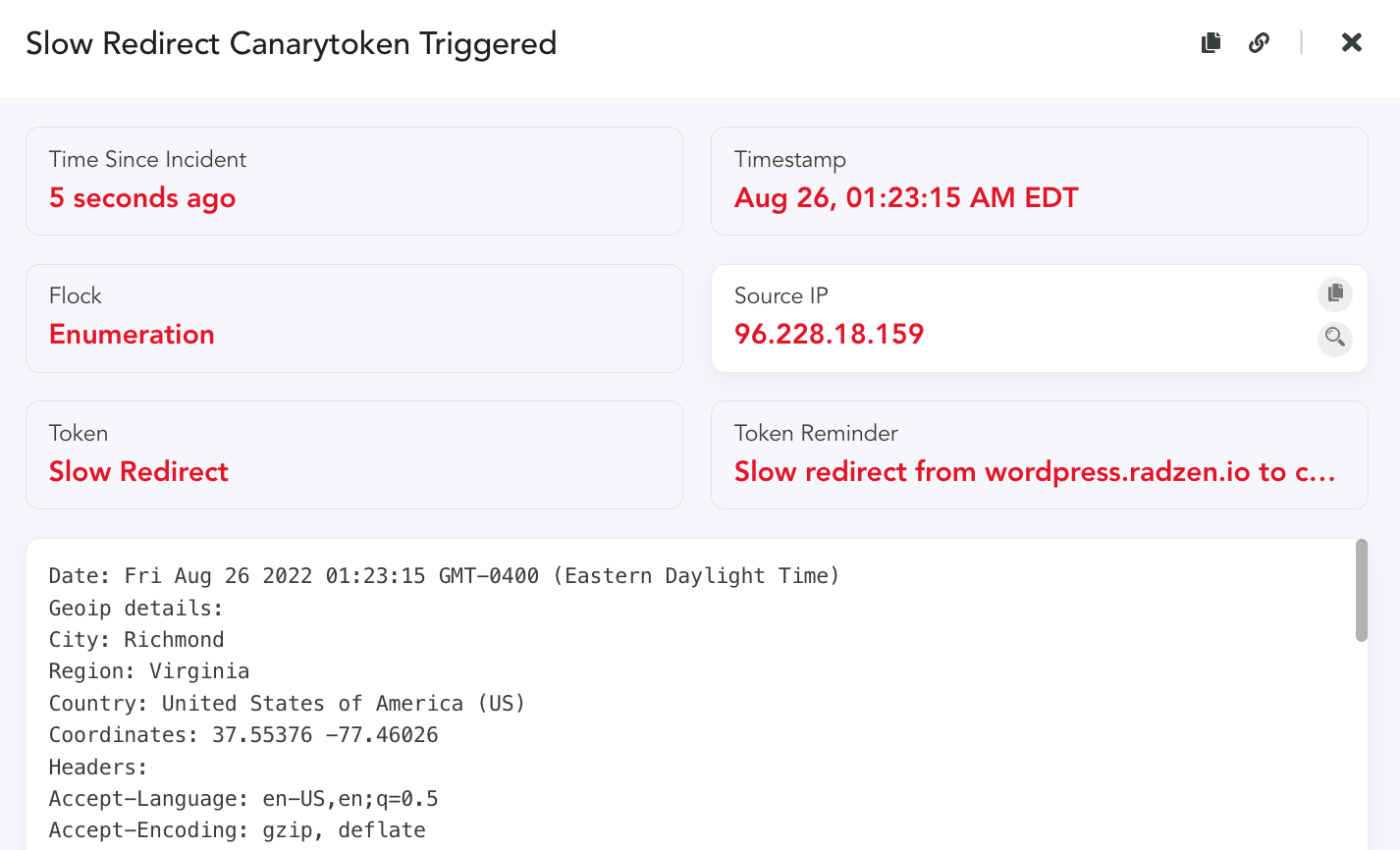
Test this story by generating a web bug token and then pasting the URL in your browser and hit enter. The Canary alert will look similar to the following:
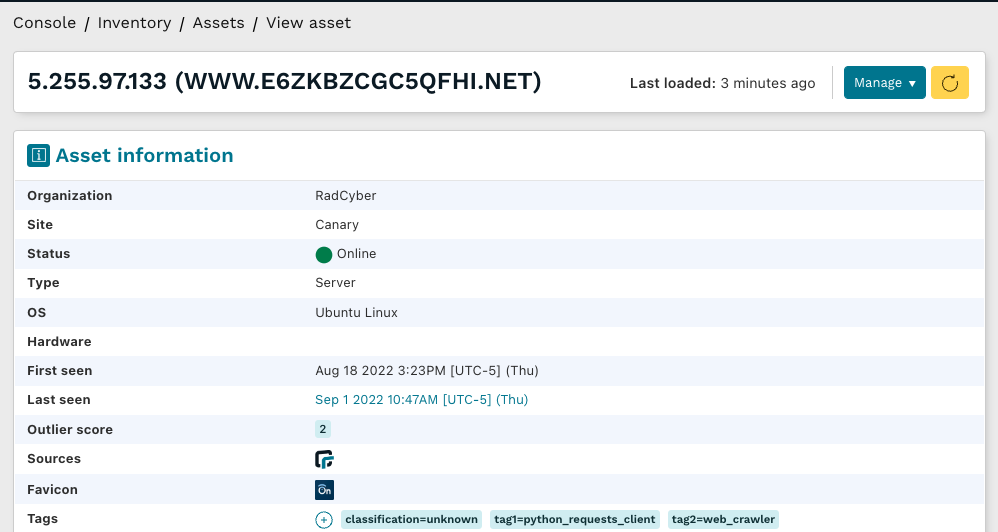
And now we see the corresponding asset in runZero added and tagged with the data from Greynoise. Now, you’ve automatically added data from Greynoise into runZero, all orchestrated by Tines. Next time an alert triggers for this asset, your runZero inventory will automatically be updated. Automation FTW!
Get the latest news and expert insights delivered in your inbox.















