In late June 2025, the Canadian government ordered Chinese camera manufacturer Hikvision to cease operations due to national security concerns. Industry Minister Melanie Joly stated that Hikvision’s presence was “injurious to Canada's national security.”
This move echoes global efforts to restrict Chinese-made telecommunications and security equipment, such as the U.S. ban under Section 889 of the 2019 National Defense Authorization Act (NDAA).
In 2019 and 2020, the U.S. Government via the Federal Acquisition Regulatory Council (FAR Council) published a list of companies whose devices cannot be used or purchased by the U.S. Government or government contractors—even if the usage is unrelated to a federal contract.1,2 These companies are prohibited because they are reasonably believed by the U.S. Government to be owned or controlled by the Chinese government.
In addition to the NDAA, the FAR and DFARS provisions are also in the final version of the Cybersecurity Maturity Model Certification (CMMC), making all Federal Civilian and Defense Industrial Base (DIB) contractors responsible for identifying and removing Section 889-covered devices from their inventories.
The ongoing challenge: you can’t fix what you can’t see #
Yet enforcement has proven challenging. A 2021 joint investigation by IPVM and The Intercept revealed that U.S. agencies had unknowingly purchased banned devices.4
As of March 2025, the FCC is still working to evaluate if ‘rip-and-replace’ efforts have successfully removed prohibited Chinese telecom equipment from U.S. networks.
The U.S. Government buying these products is obviously problematic, though it is important to emphasize they are not purchasing these items in defiance of the rules, but are being misled into purchasing them because someone is breaking the rules. The manufacturers of the products blame the sellers, the sellers blame the suppliers, the suppliers blame the manufacturers; it’s a twisted rock, paper, scissors, blame game.3
When it comes to supply chain risk, many organizations and agencies are already working to stop prohibited devices from entering the U.S. Government. But while those efforts continue, the question remains: how do you ensure the system that you own or manage does not contain an NDAA banned device?
How runZero can help #
runZero is an exposure management platform that can help any agency or contractor discover, identify, and remove prohibited devices across all of their networks (even OT) and different classifications.
For example, a few years ago, a major theme park operator experienced an abnormal activity in their network, specifically netflow traffic going to China. Their incident response team traced the source to a Hikvision surveillance camera.
When leadership asked how many similar devices were in use across all their parks, their existing tools couldn’t provide an answer. Luckily, they were in the process of deploying runZero.
Using the runZero console, they quickly identified a total of 1,240 cameras across their theme parks, 170 of them made by Hikvision. Even more alarming, several of these devices had unprotected web servers streaming a live feed, accessible to anyone with the right IP address.
Thanks to runZero, the security team was able to fully audit every instance, validate exposures, and remove all prohibited devices before they could be exploited.
See it in action #
Utilizing a pre-built asset inventory query, NDAA Section 889 devices can be rapidly identified in the network:
From the Risk Management Dashboard we can see that we have a Finding that reports 8 NDAA Section 889 devices in the network:
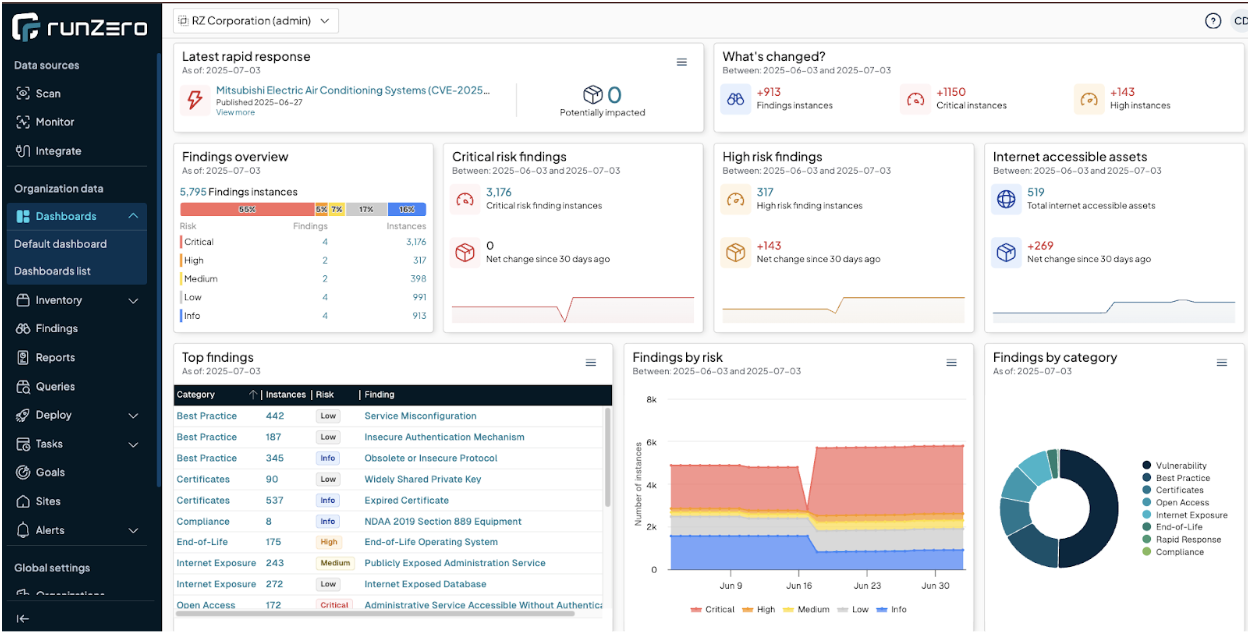
If we drill down into that Finding, we can learn more about why it was reported on, and see all of the devices that match. Already on this page we have enough information to know the hostname and network address on where to find this asset.
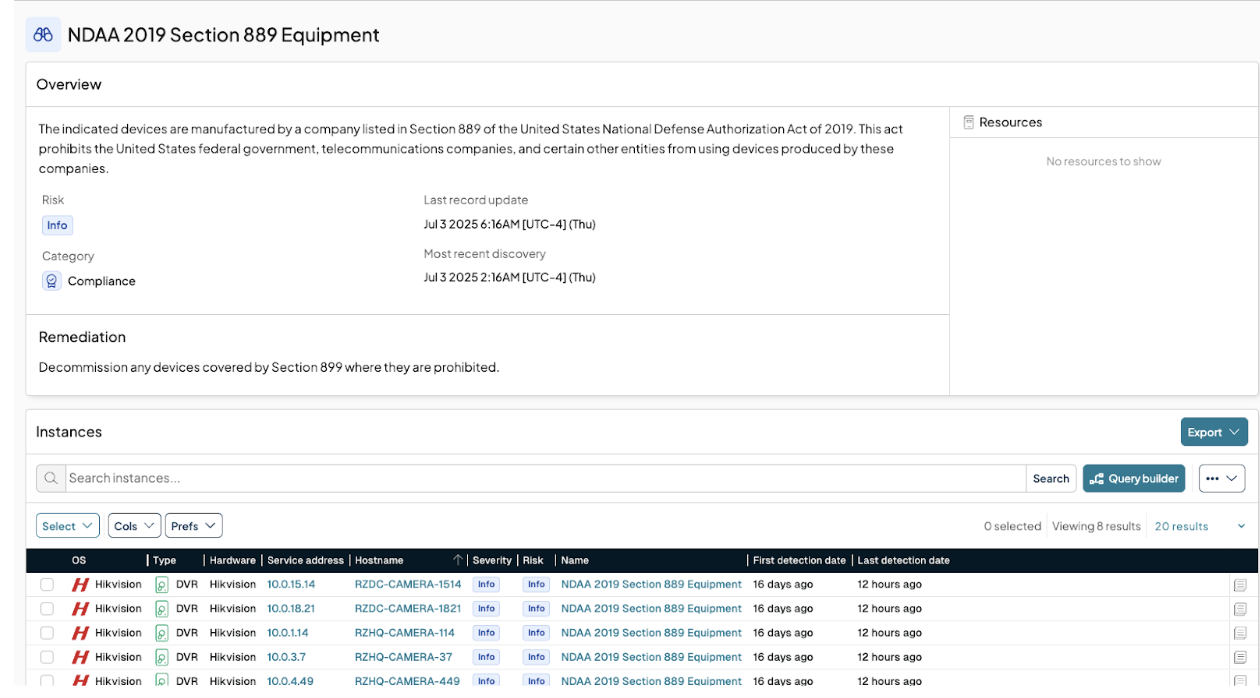
If we drill down again to an individual asset, we can see an even deeper view of the asset, and uncover that this asset is currently on the network:
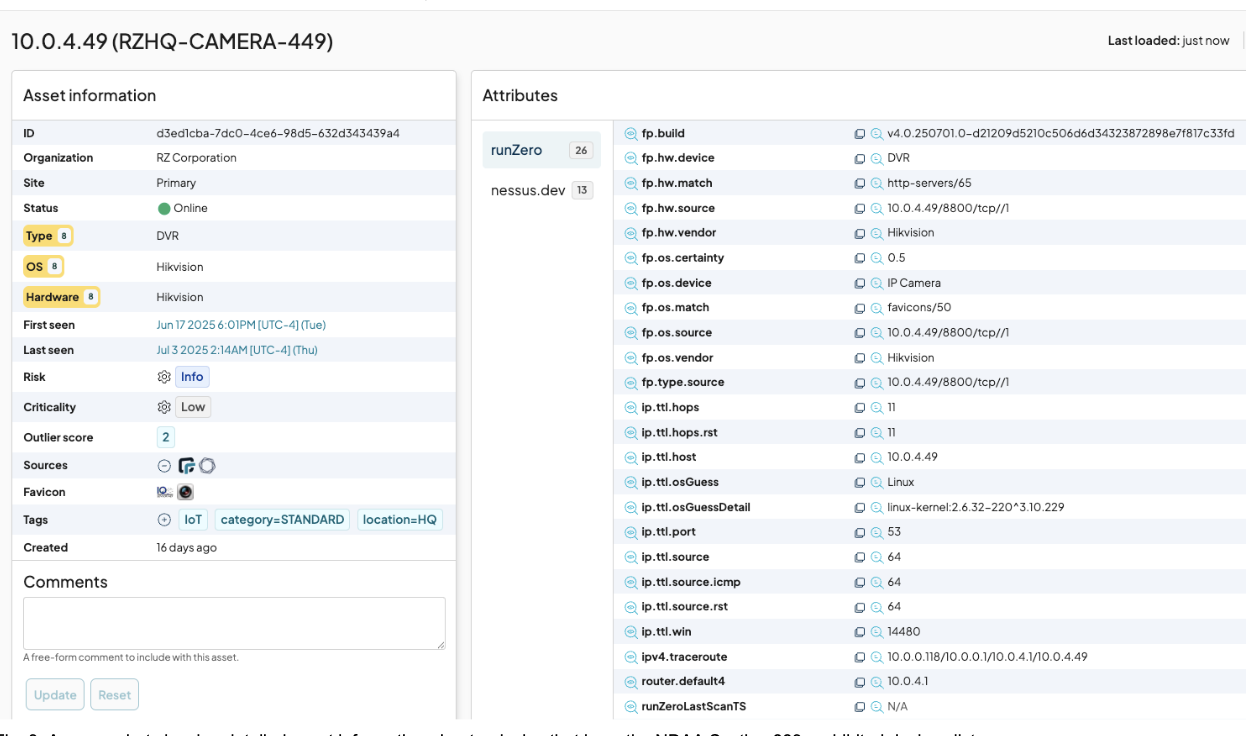
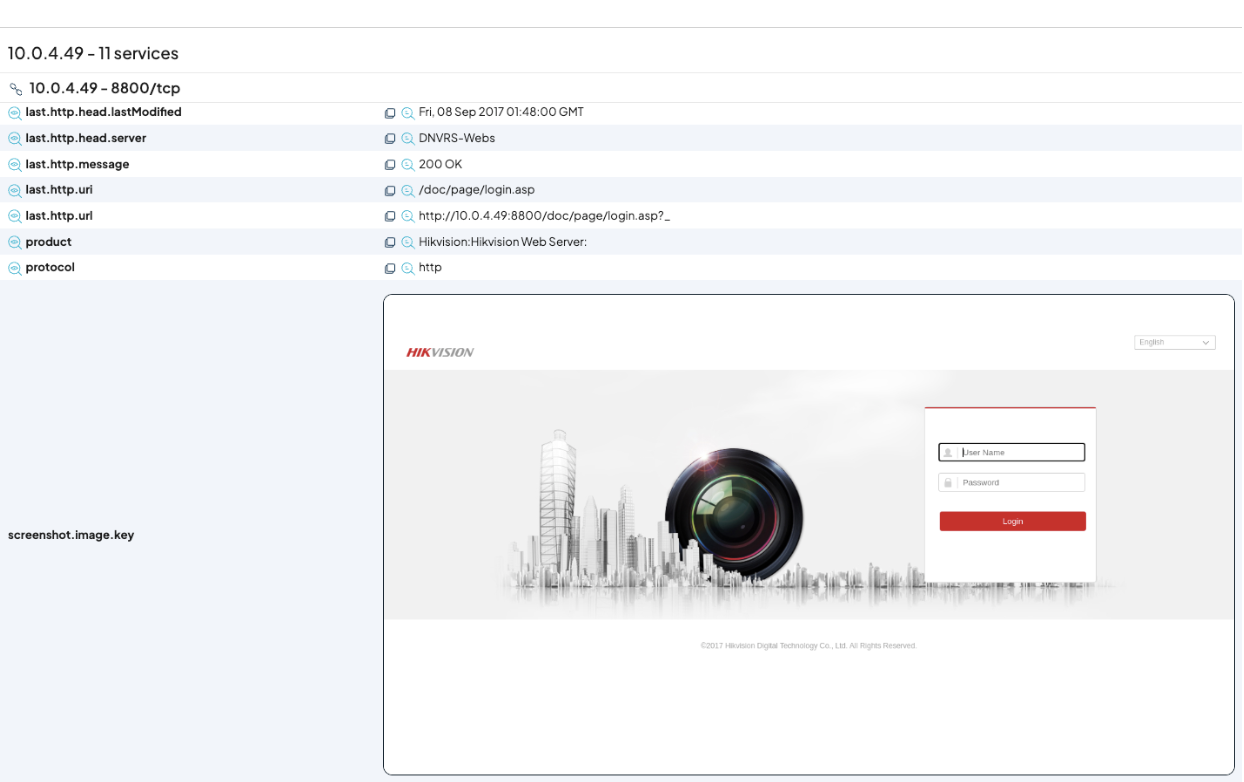
And we can also see that this asset is presenting a web portal for authentication. Based on what we learned earlier, this is a perfect target for a bad actor to gain initial access into the network through exploitation of a vulnerability.
Do you know what’s really on your network? #
With runZero, you can quickly discover every asset, across IT, OT, IoT, and cloud, and identify NDAA Section 889-prohibited devices before they become a risk. Start your free trial or request a demo today.
Resources:
















