You just know that when you have great recon results, it’s going to be a great day. To help you speed up your next engagement, let's look at how runZero can help you map out a target network–either internally or externally.
runZero was co-founded by HD Moore, the creator of Metasploit, one of the world's most popular penetration testing frameworks. HD knew from his firsthand experience as a penetration tester that organizations struggled to find, fingerprint, and manage assets on their networks. As a result, he spearheaded research efforts that would modernize unauthenticated active scanning capabilities, so that discovering and accurately fingerprinting all types of devices would be possible. This work led to co-founding runZero. While runZero is mostly used for asset inventory of large networks, it is also a great recon tool for pentesters.
Keep reading to learn more about how you can use runZero on your next engagement. If you want to test out runZero, sign up for the 21-day Enterprise trial–no credit card or sales conversation required.
Let’s begin our recon walkthrough #
runZero is an unauthenticated scanner, like nmap, but it’s based on a new proprietary scan engine. It packages a ton of HD’s pentesting parlor tricks gleaned from his research and pentesting experience into a user-friendly UI and makes use of the open source recognition fingerprinting database to provide fast, easy, and safe network scanning. runZero users can safely scan entire RFC 1918 address spaces in a night, and their targets include manufacturing OT, biomedical devices, and utility networks–as well as “Plain Old IT Networks.” runZero scanning traffic uses standard network packets without security probes that might potentially crash a fragile system.
You can either scan the network with a runZero Explorer that automatically pushes all scan results into the runZero console, or you can opt for a standalone command-line scanner that outputs a JSON file that you can either process manually or import into the console.

Despite being an unauthenticated scanner, runZero gives you a surprising level of detail on devices, even IoT and OT. It’s a rich source of information for the team to dig into to identify systems that look like a great foothold to start the penetration test.
Finding footholds into the network #
So once you’ve discovered the network and you have the big picture layout of the network, you’re ready to start finding some footholds. The best footholds are generally items most likely to fly under the radar from regular patches, updates, maintenance, and management. Once you find a device that looks interesting, you can tag it for follow up.
Here are some ways you can start looking for footholds in runZero:
- Outliers
- End-of-life assets
- Web services
- Saved queries
- Public-private network bridges
Let’s take you through the step-by-step on how to find these footholds with runZero.
Finding outliers on the network #
System administrators typically have a great handle of networked devices that they have a lot of, such as user laptops. What most admins have a much harder time configuring correctly and keeping up-to-date are rare devices that are only present once or twice on the network. These types of devices can easily fly under the radar and can present some good opportunities for pentesters–what isn’t managed properly is usually a good first foothold.
One way to start identifying these devices is from the runZero dashboard. The dashboard visualizes trend data and insights from your asset inventory, including data around the most and least commonly seen devices. These will display as cards on the dashboard, and each card can be drilled into for more details. The best starting place for outliers will be from the least common hardware, operating systems, and software pages.
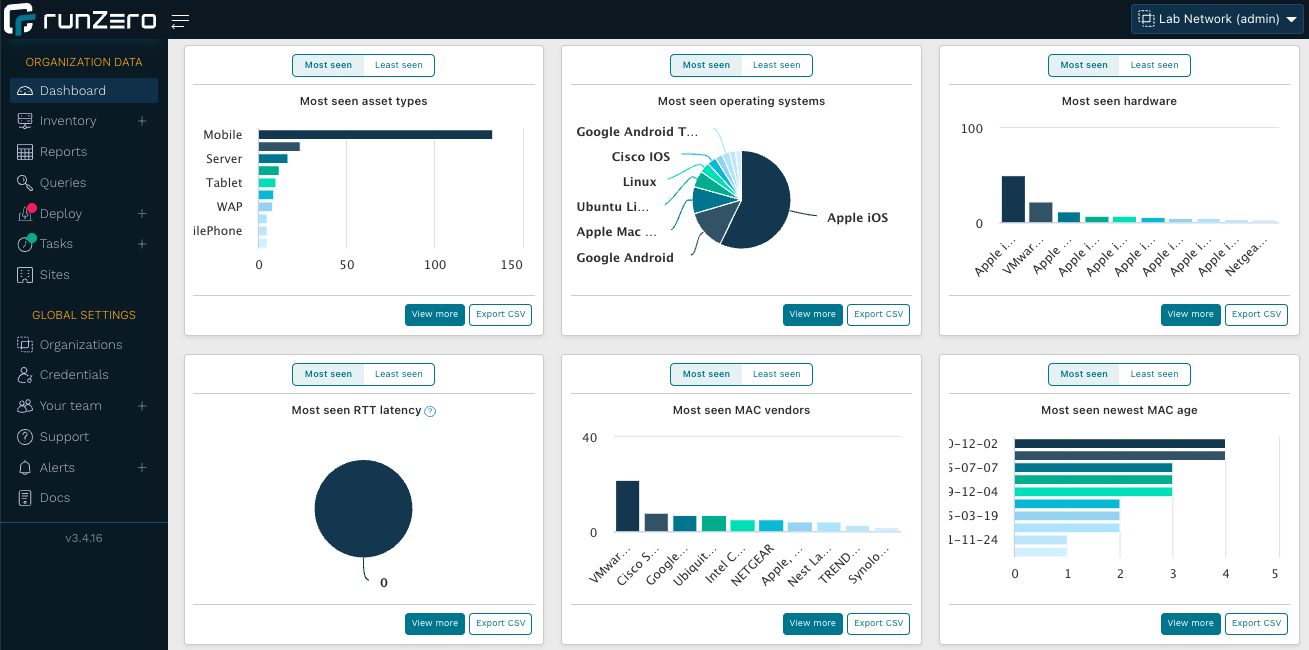
runZero’s outlier score is another way to find devices that exhibit unusual traits. Because it is a statistical analysis, this works best on networks of at least 1,000 assets. The asset outlier score ranges from 0 to 5. Typically, devices with an outlier score of 1 or higher are worth inspecting from a pentesting perspective. To find these devices, use the following query:
´outlier:>0´
When you open the asset details page for any asset, the outlier attributes will be highlighted in yellow to make them easier to identify.
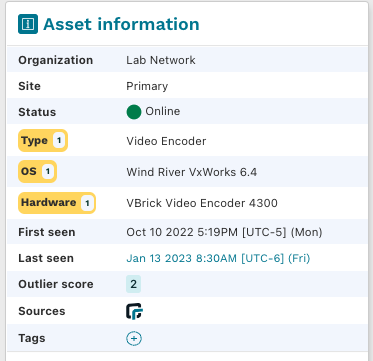
runZero will also consider unusual software versions (e.g., different patch level) or configurations (e.g., password authentication on SSH services) outliers in your infrastructure.
End-of-life assets make easy targets #
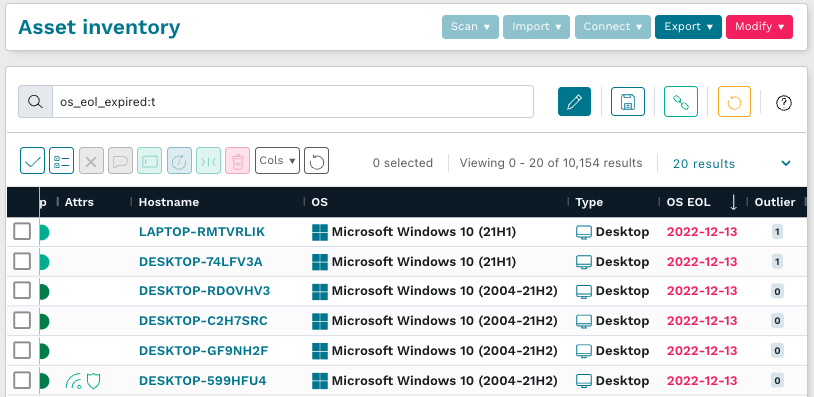
Operating systems or devices that have reached their end of life are particularly valuable to find because they can no longer be patched. runZero tracks the end-of-life dates (as well as the extended end-of-life) for major manufacturers. To find devices that have reached their end of life, use the query:
´os_eol_expired:t´(Note: “t” in the following query stands for TRUE.)
Web service screenshots provide a fast visual queue #
runZero takes screenshots of any web servers it finds on the network. Screenshots are embedded in the asset detail pages but you can also just open the Screenshots menu and skim through the entries. Custom or rare applications or devices will stand out to you like a sore thumb.
For example, we conducted a scan and found a screenshot with an IIS7 web server that appeared to be outdated which means it’s more likely to be vulnerable.
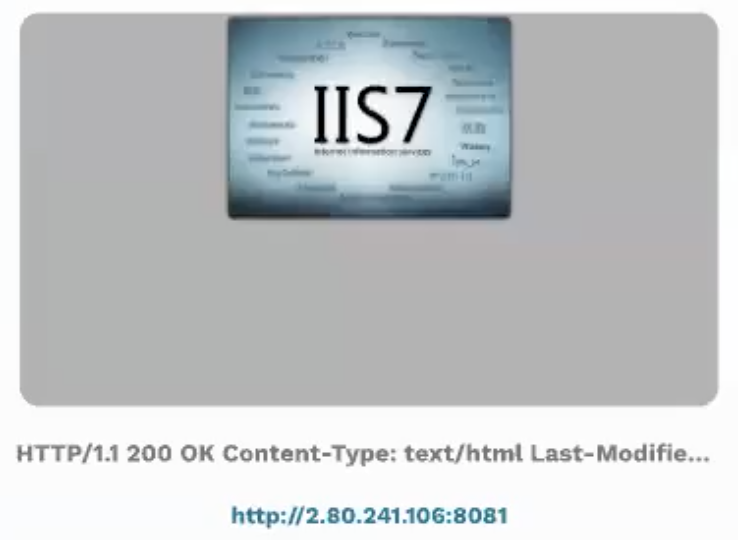
These screenshots provide a lot of information about the environment of the company. Phone service companies, active vulnerabilities, outdated, old, or forgotten services that are no longer being maintained, can all be unearthed with screenshots from your network scan.
Uncovering vulnerable systems through saved queries #
runZero uses a powerful query language to dig into assets, services, and many other aspects of your enumerated devices. A great way to get fast results is to look at saved queries, which are accessible from the Queries menu.
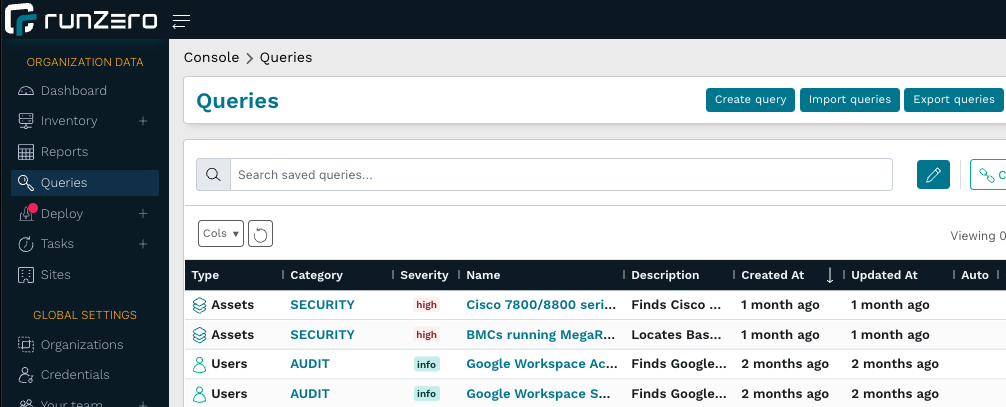
Many of the available queries can help surface potentially vulnerable systems. While runZero is a cyber asset attack surface management solution (aka CAASM) and not a vulnerability scanner, it may be worth pointing out some differences between these solution types.
Vulnerability scanners conduct vulnerability checks on each host while scanning the network; by contrast, runZero scans the network with a focus on asset inventory, collecting as much information about each asset as it can. You can then run queries against this database to identify systems potentially vulnerable to new zero-day vulnerabilities without having to rescan the network. This makes runZero a very useful tool for fast zero-day response because you don’t need to wait for the release of a new vulnerability check and because you don’t need to rescan the network. However, runZero is less useful weeks or months after the event when many systems have already been patched because it may not always be able to tell the patch level of the system.
When a new zero-day vulnerability comes out, the runZero team typically publishes a new saved query and an associated rapid response blog post. A good recent example is a vulnerability on Cisco phones.
Other saved queries can surface risky misconfigurations on your network, such as RDP on public IP addresses. For example, here's the query you can run to zero in on these assets in in your inventory:
has_public:t and protocol:rdp
You can also build your own custom query. For example, when the next zero-day vulnerability is published for Microsoft Exchange, simply use the following query:
product:exchange
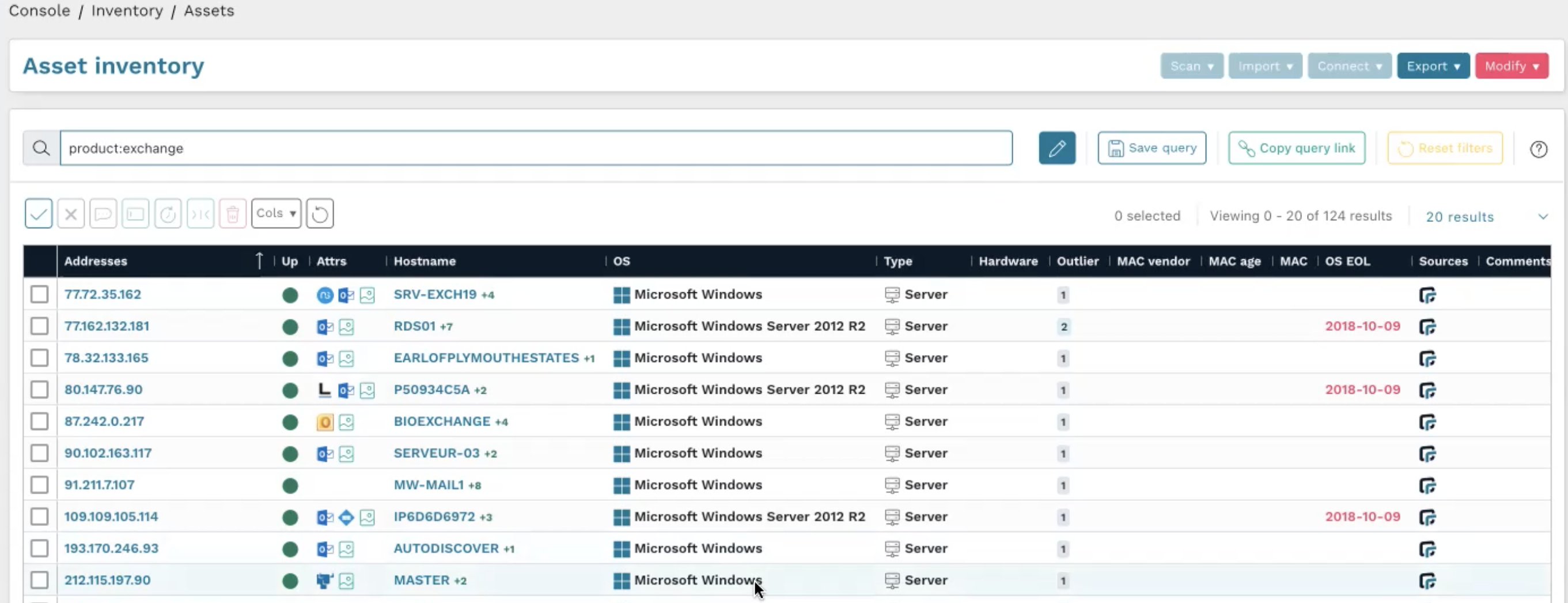
This enables you to quickly find all Exchange servers on the network.
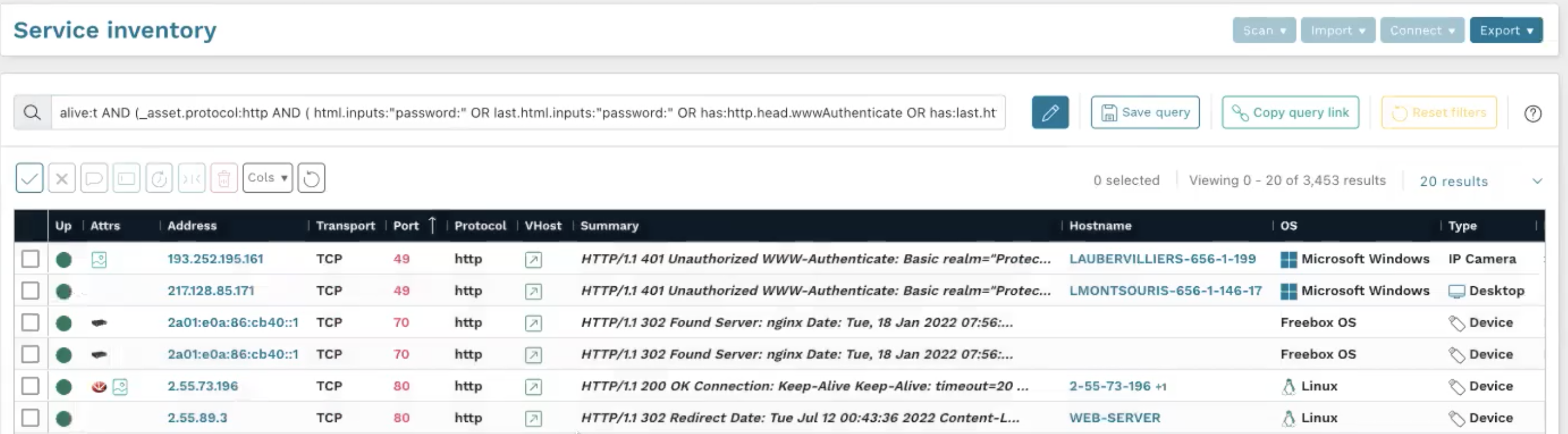
You can also use a query to find more generic things, such as authenticated web services that lack TLS encryption:
_asset.protocol:http AND protocol:http AND ( html.inputs:"password:" OR last.html.inputs:"password:" OR has:http.head.wwwAuthenticate OR has:last.http.head.wwwAuthenticate )
Find machines with legacy operating systems that bridge public and private IP spaces #
In many cases, runZero can detect secondary network interfaces, even if only one interface is scanned, to identify potential pivot points between two network segments. On Windows machines, this can be achieved through information leaks in DCE RPC and Netbios. Networking gear may have default SNMP community strings that disclose secondary network interfaces.
Combined with the ability to fingerprint the operating system version, pentesters can run a query that finds the ideal initial pivot point: machines that have both a public and private IP address and an operating system that is end of life. This can be found in the Network Bridges report page.
has_public:t AND has_private:t AND os_eol_expired:t
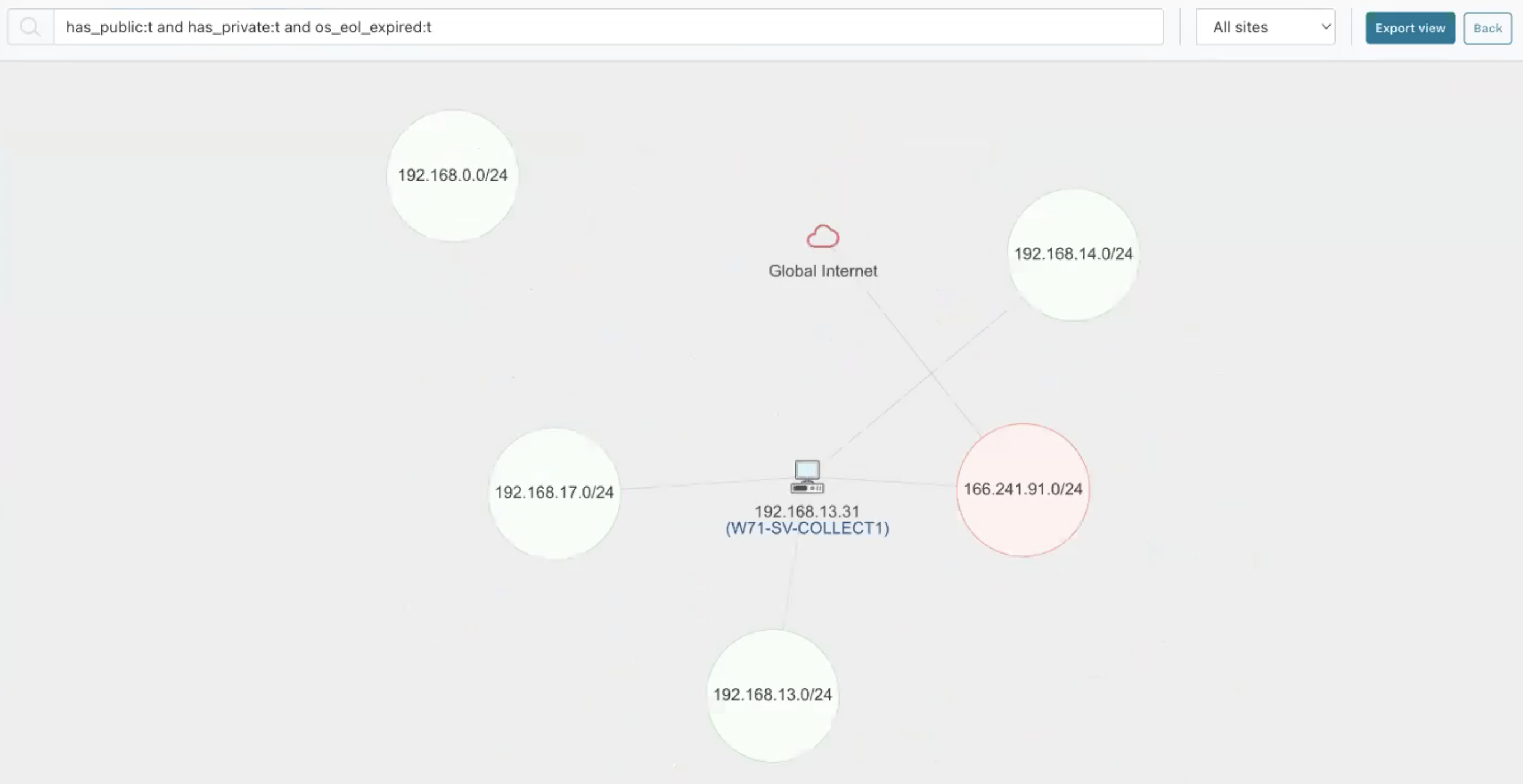
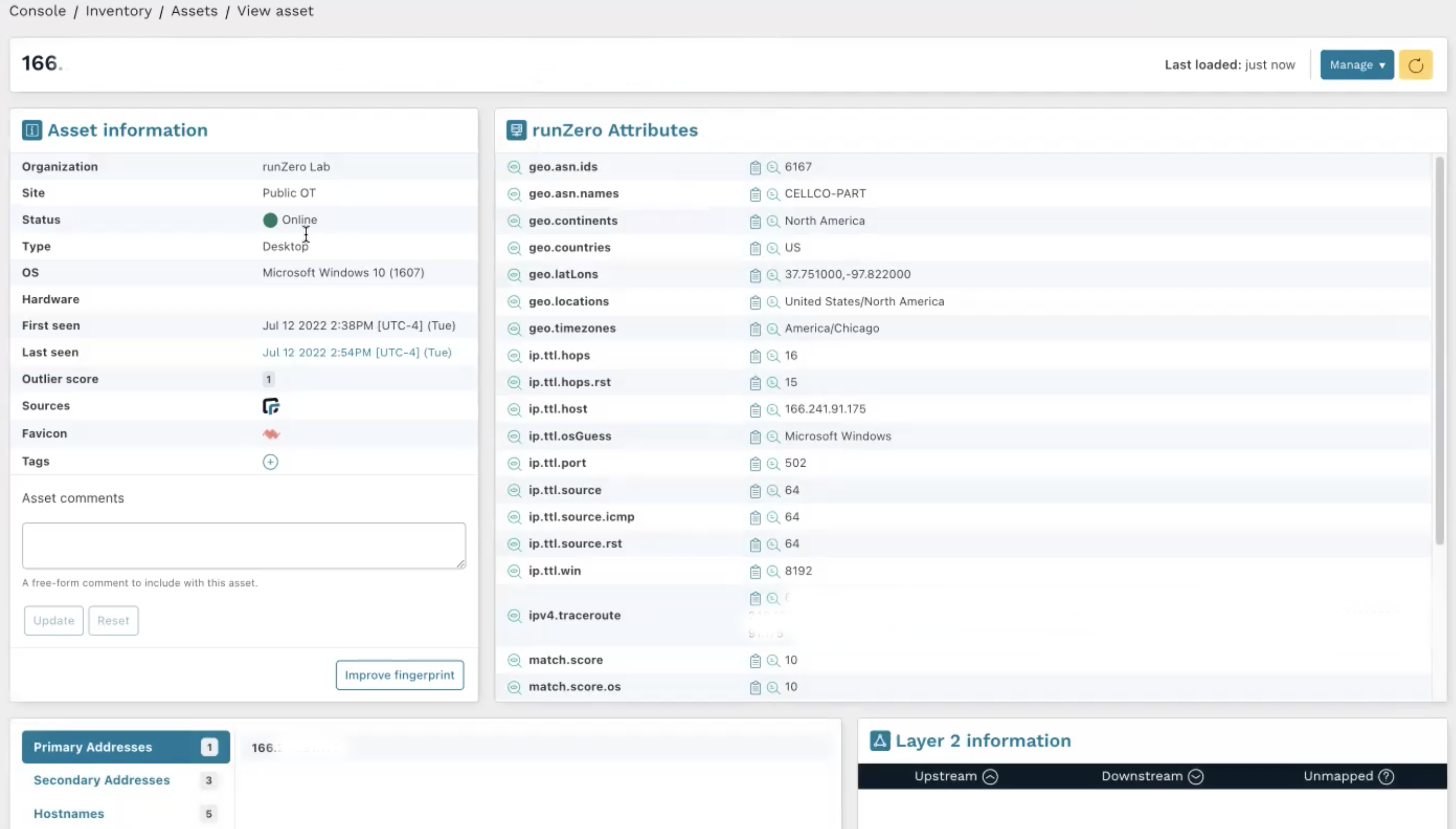
Let’s now take a closer look at this asset. Clicking on the device icon and viewing its asset details shows that it's a Microsoft Windows 10 machine that we scanned on a public IP address (which is now listed as the primary IP).
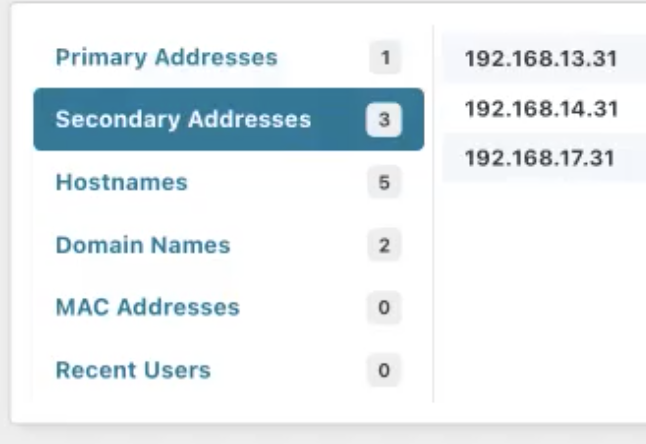
The secondary addresses show the three internal networks and their IP addresses, which have been detected by scanning the public IP address.
Let’s now take a look at the services on this device.
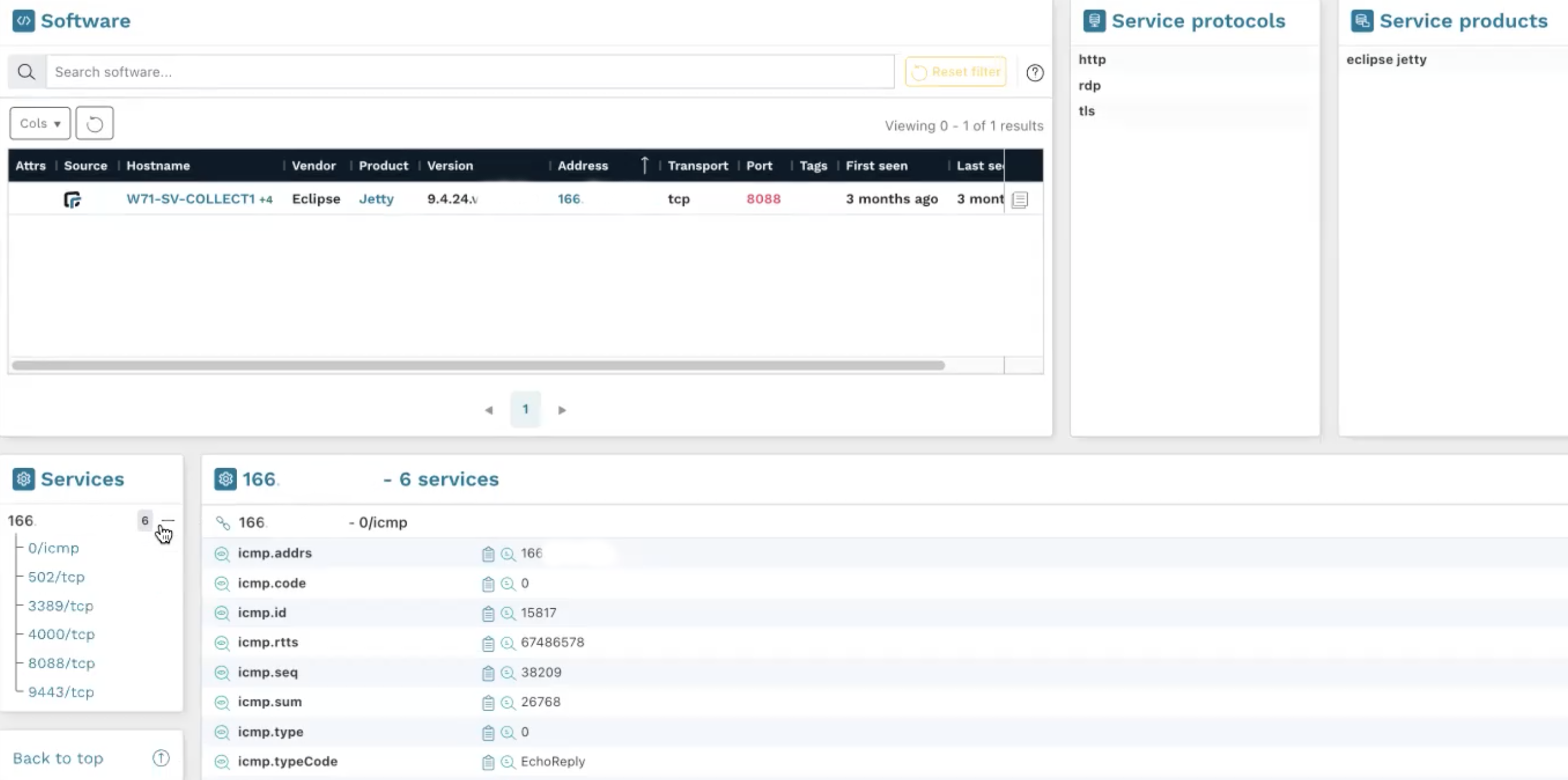
We see an open service on port 3389 that indicates that this machine likely uses RDP on a public port: a perfect way in.
Generate a full asset inventory report #
First the bad news: runZero cannot write a report on how you got in as well as recommendations on how to mitigate the risk. However, you can generate PDF reports that can serve as an appendices to your pentesting report, such as an external assets report or a full asset inventory report.
Licensing for pentesters #
Penetration testers don’t always know how many assets they’re going to find in the recon phase. Because of this uncertainty, runZero has created a special licensing provision in the Professional and Enterprise Editions. While most companies will want to use organizations to scan their asset inventory on a continuous basis, pentesters will typically only need short-term, temporary projects.
With a project, you can add data for 30 days, but it will be deleted after 90 days. However, you will have five times the amount of assets available under your license. For example, if you are licensed for 1,000 assets for continuous monitoring, you will have an additional 5,000 assets available for projects. The moment you delete your project, your full 5,000 asset license is available again. Of course, you can export and archive your asset inventory before moving on to your next project.
To start a new recon project, go to Organizations in the left navigation and click the Create project button.