Latest Cisco phone vulnerability #
Cisco recently published vulnerability details which affect their 7800 and 8800 series of IP (VoIP) phones. These phones are sold across many different model numbers and can be found in businesses and organizations of varying sizes. Originally reported to Cisco by Qian Chen of the Codesafe Team of Legendsec at QI-ANXIN Group, this vulnerability does not require authentication for successful exploitation and can provide attackers remote code execution and/or denial-of-service (DoS) capabilities.
What is the impact? #
Cisco assigned a CVSS “high” rating to this vulnerability (tracked as CVE-2022-20968) and has acknowledged that proof-of-concept exploitation code exists. Firmware for all 7800 and 8800 series IP phones (with the lone exception of Cisco Wireless IP Phone 8821) contains this vulnerability, which resides in the input validation logic of received Cisco Discovery Protocol packets. Attackers who have presence in the same VLAN or network segment as vulnerable devices can send specially-crafted Cisco Discovery Protocol packets to trigger a stack overflow, resulting in a denial-of-service condition or potential code execution.
Are updates available? #
All firmware versions (14.2 and prior) for these 7800 and 8800 series IP phones contain this vulnerability (CVE-2022-20968), and Cisco is not planning on releasing patched firmware --which is currently expected to be version 14.2(1)-- until next month (January 2023).
In the meantime, Cisco does offer the following mitigation for vulnerable IP phones:
Administrators may disable Cisco Discovery Protocol on affected IP Phone 7800 and 8800 Series devices. Devices will then use LLDP for discovery of configuration data such as voice VLAN, power negotiation, and so on. This is not a trivial change and will require diligence on behalf of the enterprise to evaluate any potential impact to devices as well as the best approach to deploy this change in their enterprise.
You can find the full details around this mitigation in the associated Cisco Security Advisory (see “Workarounds” section).
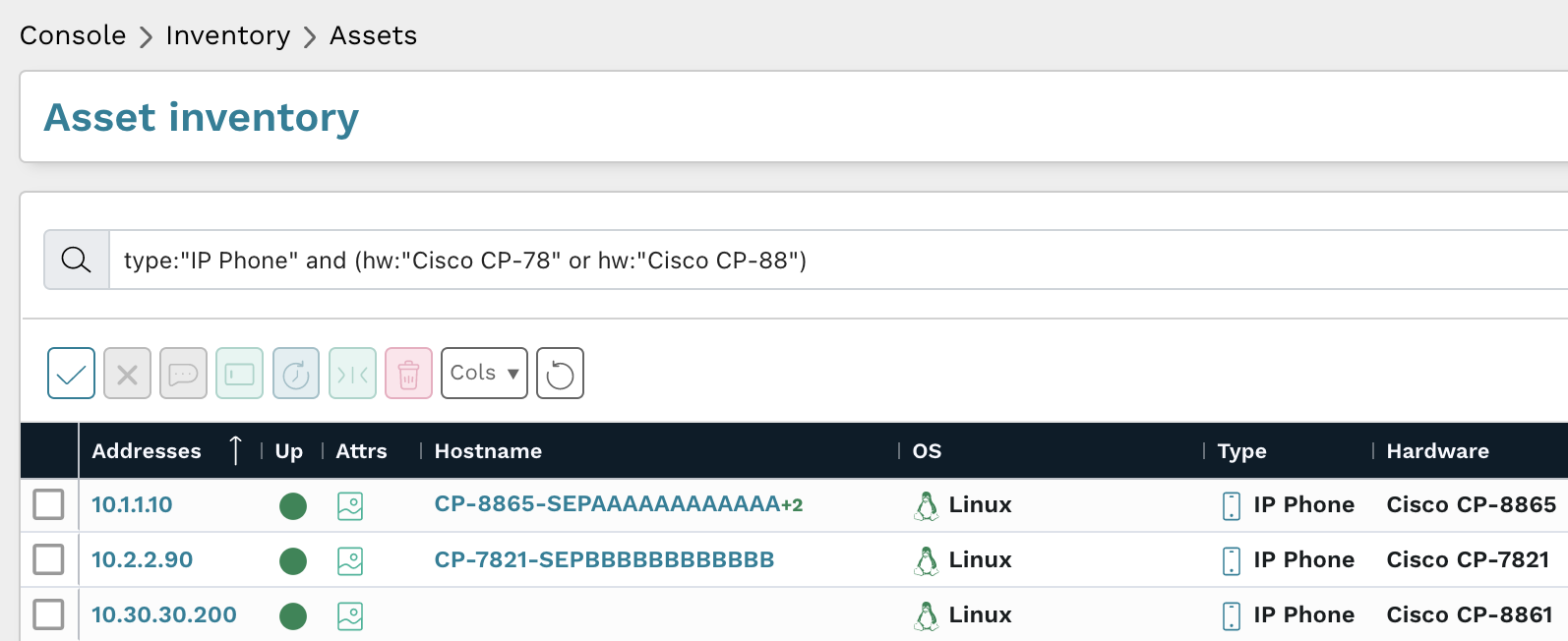
How do I find potentially vulnerable Cisco 7800 and 8800 series IP phone assets with runZero? #
From the Asset Inventory, use the following pre-built query to locate Cisco 7800 and 8800 series IP phone assets which may need remediation:
type:"IP Phone" and (hw:"Cisco CP-78" or hw:"Cisco CP-88")
As always, any prebuilt queries are available from our Queries Library. Check out the library for other useful inventory queries.
Get runZero for free #
Don’t have runZero and need help finding potentially vulnerable Cisco IP phone assets? Start your runZero trial today.
















