What's new with runZero 3.8? #
- Identify and triage risky assets
- Public preview of goal tracking
- Protocol improvements
- New and improved fingerprints
- Passwordless logins
Identify and triage risky assets #
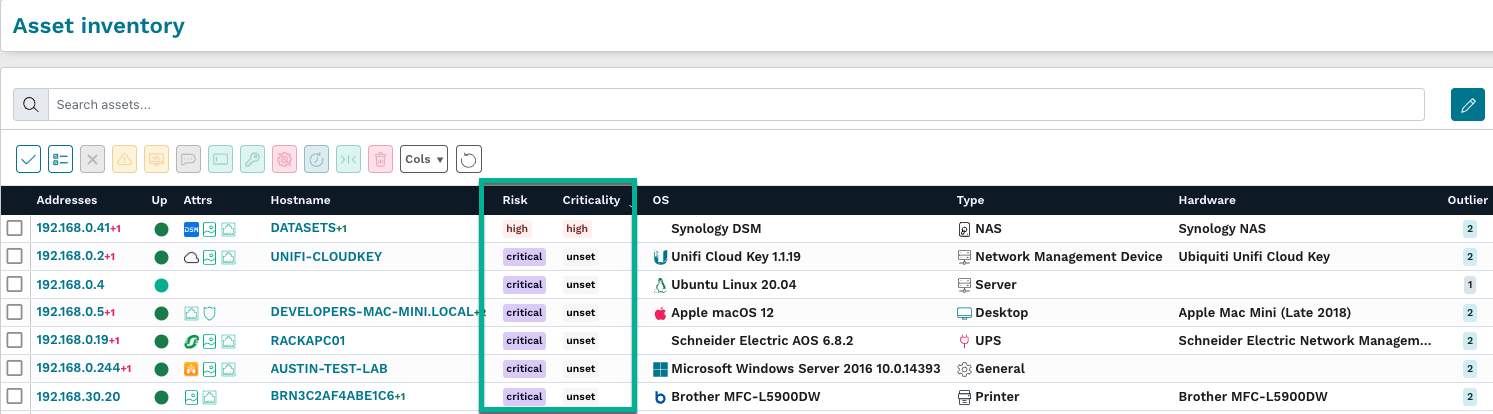
runZero customers can now identify risky assets across their environment and assign them to users for triage and remediation. Asset risk and criticality are presented as new fields in the inventory that can be used for both queries and alerts. The asset risk field is automatically set to the highest risk level of associated vulnerabilities; this data can be sourced from third-party vulnerability management imports as well as runZero queries. Asset risk can be overridden individually in the asset detail page or by applying a new risk level to assets matching a query. In addition to the changes above, a new Asset risk report is now available, which summarizes asset risk across each level of criticality.
The 3.8.0 release includes 34 new queries that automatically apply vulnerability records to matching assets. These queries are shown in the screenshot below and the full list can be found at the end of this post.
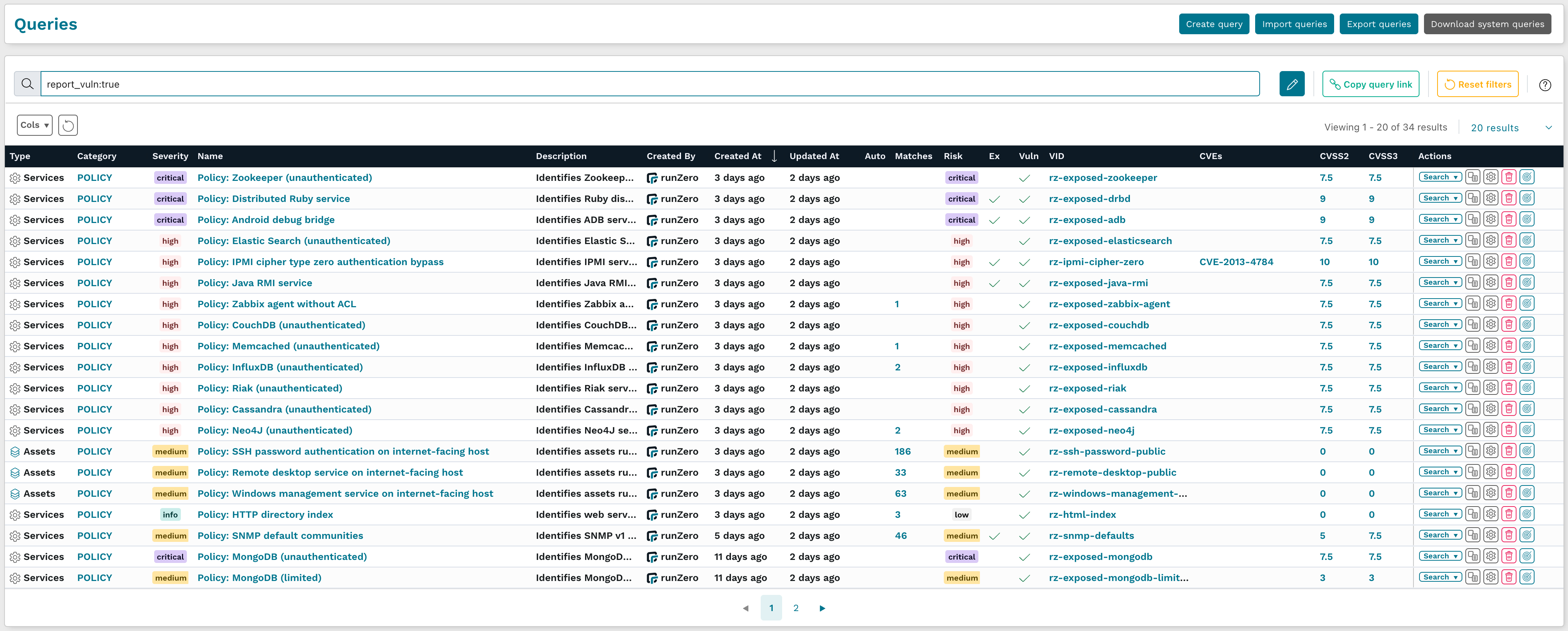
Although the new runZero queries are focused on unintended exposure, any query can be used to associate vulnerabilities to the corresponding asset, which also updates the asset risk level, and ties into the Security Ownership model for triage.
These queries can run against the assets, services, software, and vulnerability inventories. If you are importing software inventory through an integration, you can now create a query that automatically associates a vulnerability with assets with specific software installed.
As an example, if you would like to identify and remove all instances of Photoshop in your environment, create a new software query for name:photoshop, enable the new vulnerability association setting, and provide a unique vulnerability ID for the query. On the next update, a new vulnerability will be associated with every matching asset, and these vulnerabilities can be assigned through the console.
Queries can also be used to prioritize existing vulnerabilities. To add a critical finding when a low-risk vulnerability is reported on an asset with a public IP address, create a new vulnerability inventory query using the public:true asset filter, add additional conditions for the specific vulnerabilities that you would like to match, provide a unique vulnerability ID, and finally set the risk to Critical. On the next update, any assets with the specified vulnerabilities will have an additional critical risk finding attached if they also have a public IP address.
Users can find a list of assigned assets in the asset and vulnerability inventory pages by clicking their owner name in the inventory table or by viewing their user detail page under Your Team > Users.
Once a vulnerability has been remediated, the next update will remove the vulnerability from the asset and update the risk of the associated asset. Risky asset triage and query-based vulnerability associations are available to all runZero Professional and runZero Enterprise users.
Public preview of goal tracking #
Measuring progress toward your security and organizational goals can be challenging and difficult to communicate to leadership. With the introduction of goals, runZero customers can set time-bound and query-driven goals that are customizable to what matters most to your team. Goals can be used with new features like asset risk as well as existing features like asset ownership. If you can query for it in runZero, it can now be a goal!
Some examples of goals could include:
- Managing expiring TLS certificates
- Remediating critical risk vulnerabilities on assets within a set timeframe
- Keeping insecure management services off external networks
This feature is in a public preview and we would love your feedback via email or through the in-product support form.
Protocol improvements #
The default TCP port list has grown to almost 600 ports (from ~500) for better coverage. Protocol support has been added for Brother's proprietary scanner protocol, allowing us to identify Brother scanners or Brother multi-function devices that include a scanner. SNMP enumeration is more configurable through the disable-bulk-walk and max-repetitions settings in the advanced scan configuration. Protocol detection has also been improved for TNS Listener and Android Debug Bridge services.
New and improved fingerprints #
New fingerprints were added for products by Advantech, Amazon, Apache, ASUSTeK, AV Costar, Avaya, AVM, Bosch, Canon, Canonical, Cisco, Citrix, Codonics, Cognosys, CostarHD, Cradlepoint, Cubic Transportation Systems, DataDirect Networks, Dahua, Daktronics, Datamax, Debian, Dell, DigitalOcean, Eaton, Econolite, EnGenius, Entrust, EVGA, ExaGrid, F5, Fortinet, Getinge, Glenayre, Grandstream, HP, HPE, Huawei, iCAD, Kali, LAVA, March Networks, Microsoft, Moen, MSI, MultiTech, Multitone, Netgear, Oce, Okidata, OpenLogic, The Ottawa Hospital Cancer Center, Palo Alto Networks, Panasonic, PaperCut, Proxim, Prusa, Qualys, Red Hat, RICOH, The Royal Marsden NHS Foundation Trust, Saulmatics, Schneider Electric, Somfy, Sonos, SUSE, Ubiquiti, VMware, and ZTE.
Other research improvements #
We published a Rapid Response post and new query for finding servers running the PaperCut MF and ND software.
In addition to the above protocol and fingerprinting improvements, we improved our normalization of x509 certificate issuer and subject values, allowing us to more consistently apply fingerprints regardless of ordering/formatting variants found in the field or due to tech stacks.
Passwordless logins #
We don't want your password.
From the beginning, runZero has supported single sign (SSO) for all users, including the free Starter Edition. From this version (3.8.0) of runZero onward we now support using a one-time authentication link in addition to any configured MFA token.
This feature is no less secure than an email-based password reset and prevents runZero from storing even the hashed and encrypted passwords on our servers. If you are unable to set up SSO, using passwordless logins with a WebAuthn token is the next best thing.
See runZero 3.8 in action #
Watch the video to see a demonstration of the newest features in runZero, including asset risk and criticality, goal tracking, and applying vulnerabilities from queries.
Release notes #
The runZero 3.8 release includes a rollup of all the 3.7.x updates, which includes all of the following features, improvements, and updates.
New features #
- Risk and criticality levels can now be assigned to assets through third-party integrations, the asset inventory, and custom rules.
- runZero Preview Program: Goal tracking helps users with Professional and Enterprise licenses track progress toward completing their security initiatives. Use built-in goals for asset ownership coverage or system queries, or create goals with custom queries to fit your needs.
- runZero system and custom queries can now be used to create vulnerability records.
- Passwordless authentication is now available, allowing users to request one-time authentication links via email rather than storing a password. This provides a secure authentication alternative when SSO cannot be configured.
- Added support for Azure and Intune GCC, GCC High, and DoD environments.
- Improved compatibility with WireGuard and Tailscale on macOS and *BSD.
- Added support for searching software attributes.
- Alert channels now support more than one email address.
- Asset limit warnings have been updated to be more clear about whether or not scans will be affected.
New vulnerability queries #
- Application: Apache HTTP Server versions vulnerable to CVE-2021-41773 or CVE-2021-42013
- Application: HPE iLO 4 authentication bypass
- Application: HPE iLO 5 firmware versions known to be vulnerable
- Application: OMI WSMAN versions vulnerable to OMIGOD
- Application: OpenSSH servers vulnerable to CVE-2023-25136
- Application: SolarWinds Serv-U MFT
- Application: VMware ESXi vulnerable to CVE-2021-21974 (OpenSLP)
- Hardware: Accellion legacy file transfer appliances
- Hardware: Cisco VPN routers vulnerable to CVE-2022-20825
- Policy: Android debug bridge
- Policy: Cassandra (unauthenticated)
- Policy: CouchDB (unauthenticated)
- Policy: Distributed Ruby service
- Policy: Elastic Search (unauthenticated)
- Policy: HTTP directory index
- Policy: InfluxDB (unauthenticated)
- Policy: IPMI cipher type zero authentication bypass
- Policy: Java RMI service
- Policy: Memcached (unauthenticated)
- Policy: MongoDB (limited)
- Policy: MongoDB (unauthenticated)
- Policy: Neo4J (unauthenticated)
- Policy: NFS world-readable exports
- Policy: Redis (unauthenticated)
- Policy: Remote desktop service on internet-facing host
- Policy: Riak (unauthenticated)
- Policy: SMB signing not required
- Policy: SMB v1 enabled
- Policy: SNMP default communities
- Policy: SSH password authentication on internet-facing host
- Policy: SSLv2 / SSLv3 services
- Policy: Windows management service on internet-facing host
- Policy: Zabbix agent without ACL
- Policy: Zookeeper (unauthenticated)
Product improvements #
- Improved error message when attempting to delete a scan template twice
- Grace period for tasks can now be configured from the task template page.
- Improved asset correlation for multi-source assets.
- Public API endpoints to view hosted zones have been added.
- The API endpoints for managing scan tasks now accept an argument to select a hosted zone.
- Validation for stored queries has been improved to prevent saving queries with warnings or errors.
- Excerpts of task log messages are now available on the task details page for tasks that are in error status.
- The display of datagrid warning and error messages has been improved.
- Improved asset processing when FortiGuard endpoints with "Policy Override Authentication" enabled are present.
- Self-hosted installs now support an option to disable TLS validation between Explorers and the console application
- The max-repetitions and disable-bulk parameters have been added to SNMP probes.
- Task failures are now reported in the Task details pane.
- All queries, including runZero-provided system queries, can now be copied.
- The configuration for runZero-provided system queries can be modified.
Integration improvements #
- Credential verification is now allowed only after all required fields have been completed.
- Third-party vulnerability integrations now support a more granular risk filter.
- Third-party integrations now support more granular vulnerability filters.
- Crowdstrike will now use Connection IP and Connection MAC for asset matching.
Bug fixes #
- A bug preventing explorer reassigned to a previous organization and picking up assigned tasks has been resolved.
- A bug causing software search links to navigate to a 404 page has been resolved.
- A bug causing task-failed events to ignore the site restriction has been resolved.
- A bug causing the hostname override tag to not update the hostname displayed has been resolved.
- A bug that prevented clearing Insights from the dashboard has been resolved.
- A bug where the copy scan button was cut off in the recurring tasks tab has been resolved.
- A bug that could result in a panic while performing a scan has been resolved.
- A bug that could prevent the API from creating valid scan tasks has been resolved.
- A bug that negatively impacted fingerprinting via TLS certificates has been resolved.
- A bug preventing TLS negotiation in some cases has been resolved.
- A bug that was triggered when submitting Azure credentials for verification with a subscription ID has been resolved.
- A bug that could cause deadlocks in the TCP LDAP probe and Active Directory integration has been resolved.
- A bug that caused an infinite redirect when clicking on site breadcrumbs has been resolved.
- A bug causing recurring tasks to be incorrectly sorted by start time on the tasks page has been resolved.
- A bug allowing “Verify & save” on the credentials update page to error has been resolved.
- A bug where Dell laptops were identified as desktops or servers has been resolved.
- A bug preventing TLS negotiation in some cases has been resolved.
- A bug that caused imported queries to be parsed improperly has been resolved.
- A bug with the default webhook Slack alert template has been resolved.
- A recent update in Explorer and Scanner behavior which could inadvertently trigger CrowdStrike EDR detection has been disabled
- A bug regarding Intune rate limiting and intermittent failures has been resolved.
- A bug where certain tasks could not be edited has been resolved.
- A bug regarding erroneously returned results from unscanned runZero assets when searching the asset inventory has been resolved.
- A bug marking assets "unscanned" has been resolved.
- A bug that resulted in a 500 error when running the asset attribute report has been resolved
- A bug that could prevent custom integration results from merging into existing assets has been resolved.
- A bug that could cause the save button on the credential edit form to be disabled has been resolved.
- A bug where clicking links on the Query page of a self-hosted instance may return a 500 has been resolved.
- A bug where clicking links in the Tasks column of the Credentials page would result in an error has been resolved.
- A bug where paginated results could display Viewing 0 - N for the first page has been resolved to now display Viewing 1 - N.
- A bug that could result in duplicate offline assets has been resolved.
- A bug that prevented CSV exports of assets when using free text search has been resolved.
- A bug where the number of hops could be incorrectly set to zero when ARP is present as a service has been resolved.
- A bug that prevented searching assets using the task search key has been resolved.
















