What's new with runZero 3.6? #
- Organizational hierarchies
- CrowdStrike integration improvements
- Operating system CPE assignment
- New protocols and fingerprints
- New Rapid Response queries
Organizational hierarchies #
Organizational hierarchies help streamline user and permission management. When creating and editing organizations, you can define an organizational hierarchy that allows for inherited user permissions.
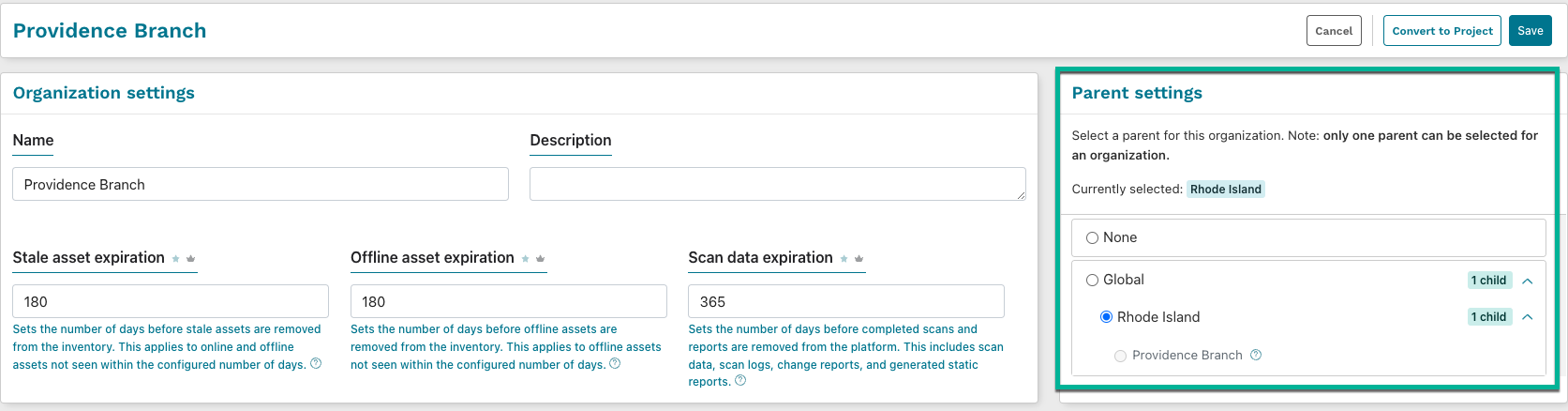
The users assigned to the selected parent organization will maintain the highest assigned permission in the child organization unless specified in their user permissions. For instance, if a user is a viewer in the parent organization, but an administrator in the child organization, they will maintain their admin status in the child organization when the parent-child relationship is created.
Organization hierarchies can be three levels deep, and user permissions in a child organization can be upgraded, not downgraded, from the currently set permissions in the parent organization.
CrowdStrike integration improvements #
The CrowdStrike integration now populates asset software information from Falcon Discover. Additionally, IP addresses imported by CrowdStrike are now considered primary addresses and will be used for correlation, and the CrowdStrike credential verification is now seperated by service.
Operating system CPE assignment #
The operating system Common Platform Enumeration (CPE) field is a string describing detected operating system software aligned to the CPE naming scheme. This field is queried using the syntax os.cpe23:<text>. In cases where runZero was able to fingerprint the operating system but the NIST database does not contain an official matching entry, an unofficial CPE will be generated and include r0_unofficial in the other field of the CPE.
New protocols and fingerprints #
The runZero scanner now reports legacy RDP authentication, decodes additional ISAKMP/IKEv2 fields, and improves the fingerprinting of AirPlay devices.
Additional fingerprints were added for products by 2N, Aastra, Alien Technology, AMI, Arista, Asterisk, Avaya, Canon, Cisco, D-Link, Dell, Eaton, Echelon, Fortnet, FreePBX, GAI-Tronics, Grandstream, Hillrom, Honeywell, HP, HPE, Intel, Jenkins, Lantronix, Lenovo, LG, Logic Controls, Logitech, Meinberg, Mitel, Moxa, Netgear, NetApp, Quantum, Palo Alto Networks, Panasonic, Poly, QNAP, Samsung, Sierra Wireless, SoundCom, Spectralink, STARFACE, Tektronix, Thomson, Ubiquiti, VTech, Wahsega, Yealink, ZTE, Zultys, and Zyxel.
New Rapid Response queries #
A new query was added to quickly identify OpenSSH 9.1 Servers affected by a memory double-free vulnerability.
See runZero 3.6 in action #
Watch the video to see a preview of some of the newest features in runZero, including organizational hierarchies, research updates, software inventory from CrowdStrike, and OS CPE information.
Release notes #
The runZero 3.6 release includes a rollup of all the 3.5.x updates, which includes all of the following features, improvements, and updates.
New features #
- Organizational hierarchies are available allowing for permissions to be inherited by child organizations based on an established parent.
- runZero now identifies the CPE associated with fingerprinted assets and assigns an unofficial CPE where an official match is not found in the NIST database.
Product improvements #
- A new query was added for OpenSSH 9.1 servers affected by a memory double-free vulnerability.
- Improved SNMP fingerprint coverage capabilities and added new attributes for SNMP protocol version (at the asset level) and authentication details (at the service level).
- Improved handling of invalid multi-valued subjectAlternativeNames on x.509 certificates.
- The scanner now supports identifying RDP authentication methods, including legacy and NLA, supported by target hosts.
- The scanner now supports the ability to decode ISAKMP/IKEv2 replies
- A new canned query for OpenSSH 9.1 servers which contain a memory double-free vulnerability has been added.
- Performance of the Active Directory (LDAP), Azure AD, and Google Workspace integrations has been improved.
- SNMP protocol versions are now tracked at the asset level.
- SNMP services will now keep track of how they authenticated and using what protocols.
- Hostname extraction from malformed subjectAlternativeNames on TLS certificates has been improved.
- Site scopes with subnets ending in /32 (for IPv4) and /128 (for IPv6) are no longer parsed to single IPs and will appear as CIDR entries in the subnets list.
- Improved error validation UX around email addresses when setting up an email alert channel.
- Services, Screenshots, and Software inventory pages now include associated site subnet tags.
- runZero now identifies the CPE associated with fingerprinted assets and assigns an unofficial CPE where an official match is not found in the NIST database
Integration improvements #
- Improved fingerprinting of operating systems imported via the LDAP and VMware integrations.
- Stability and performance of VMware asset correlation has been improved.
- VMware assets are now merged across sites.
- The Intune integration has been improved to better handle Intune API rate limiting.
- IP addresses reported by CrowdStrike are now considered primary addresses, and will be used for asset correlation.
- CrowdStrike credentials verification is now separated by service
Bug fixes #
- A bug that could prevent automatic metric calculations from completing has been resolved.
- A bug that could prevent stale assets from being automatically removed on subsequent task runs has been resolved.
- Several minor bug fixes and UX improvements have been made to the redesigned task page.
- A bug that prevented OS fingerprinting and information extraction over RDP has been resolved.
- A bug preventing users from copying or editing connector and analysis tasks has been resolved.
- A bug causing new recurring tasks to display an incorrect first run date has been resolved.
- A bug causing the dashboard asset trends graph tooltips to appear away from the graph has been resolved.
- A bug causing task page inspection cards to automatically collapse has been resolved.
- A bug that could result in build-up of frequently recurring tasks has been resolved.
- A bug that could cause extremely large tasks to remain queued for processing indefinitely has been resolved.
- A bug that could prevent export of service attribute reports has been resolved.
- A bug preventing license requirement indicators from being visible on some pages has been resolved.
- A bug preventing saving of credentials due to bad org-access settings has been resolved.
- A bug preventing recalculation of the next scheduled run time for a scan has been resolved.
- A bug that could cause inaccurate asset counts in the Organization Overview report has been resolved.
- A bug that could cause site import to fail when missing optional fields has been resolved.
- A bug that could prevent the VMWare connector task page from loading has been resolved.
- A bug that could cause duplicate MSDefender attributes on an asset has been resolved.
- A bug where firewalls (and similar devices) responding to many non-asset IP addresses during scanning would lead to unexpected assets in inventory has been resolved.
- A bug preventing the active scans dashboard widget from navigating to the associated task on click has been resolved.
- A bug preventing site subnet tags from appearing in the dashboard Asset tags widget has been resolved.
- A bug that could cause CrowdStrike tasks to fail when missing software permissions has been resolved.
- A bug that could prevent bogus services from certain firewalls from being completely filtered has been resolved
- A bug that could lead to a browser crash in the latest release of Chromium based browsers on MacOS has been circumvented.
















