What's new with runZero 3.0? #
- Meet our new brand: runZero!
- Sync assets, software, & vulnerability data from Qualys
Introducing runZero #
Rumble is officially runZero! This name change reflects our growth as a product and as a company. Over the past year, Rumble has added so many new capabilities, presenting an opportunity to evolve so that our brand reflects all of our existing and planned features. runZero continues our mission of making asset inventory easy, fast, and accurate, while giving us runway to grow our platform.
Read our brand announcement and FAQs to learn more.
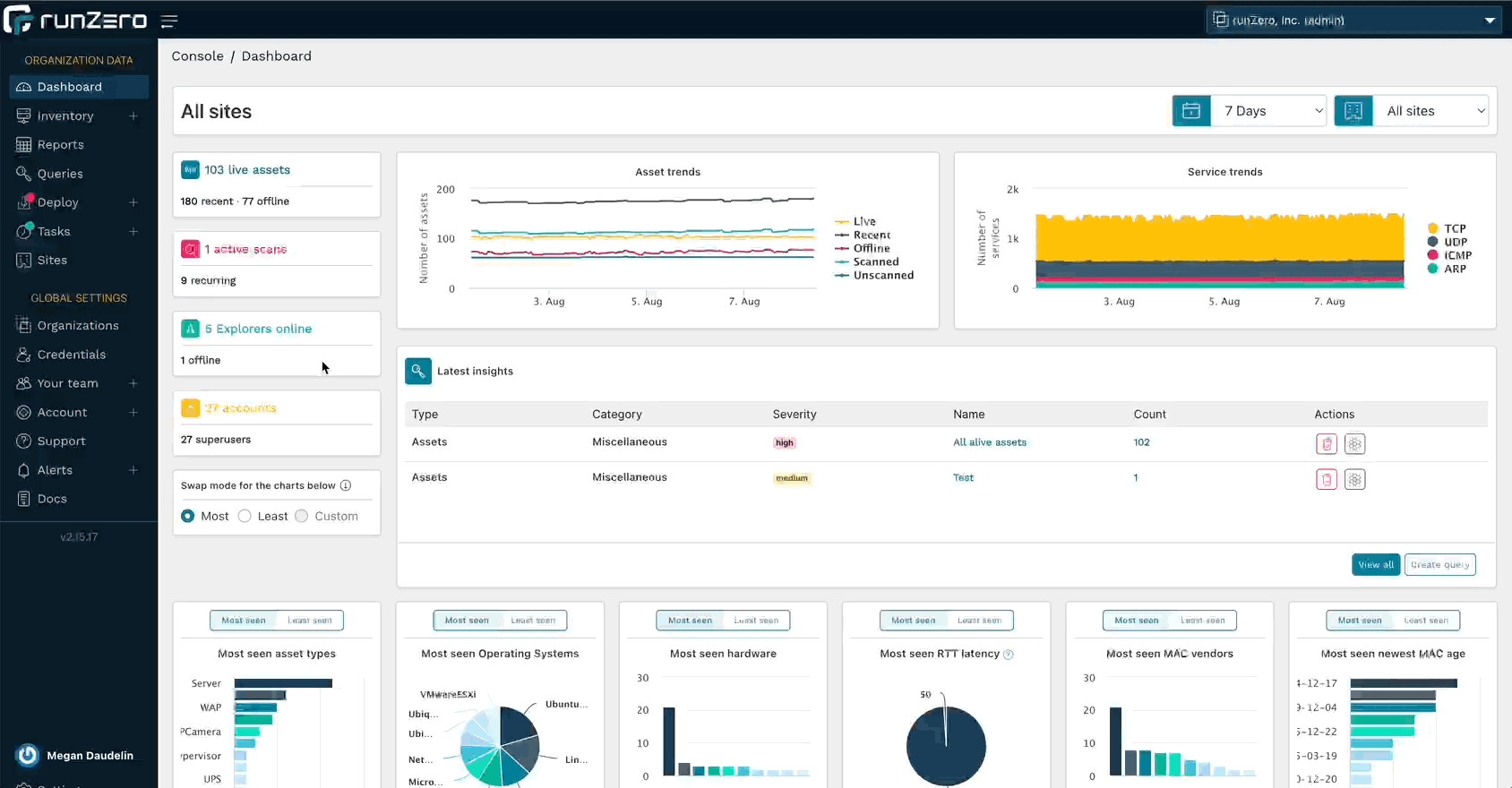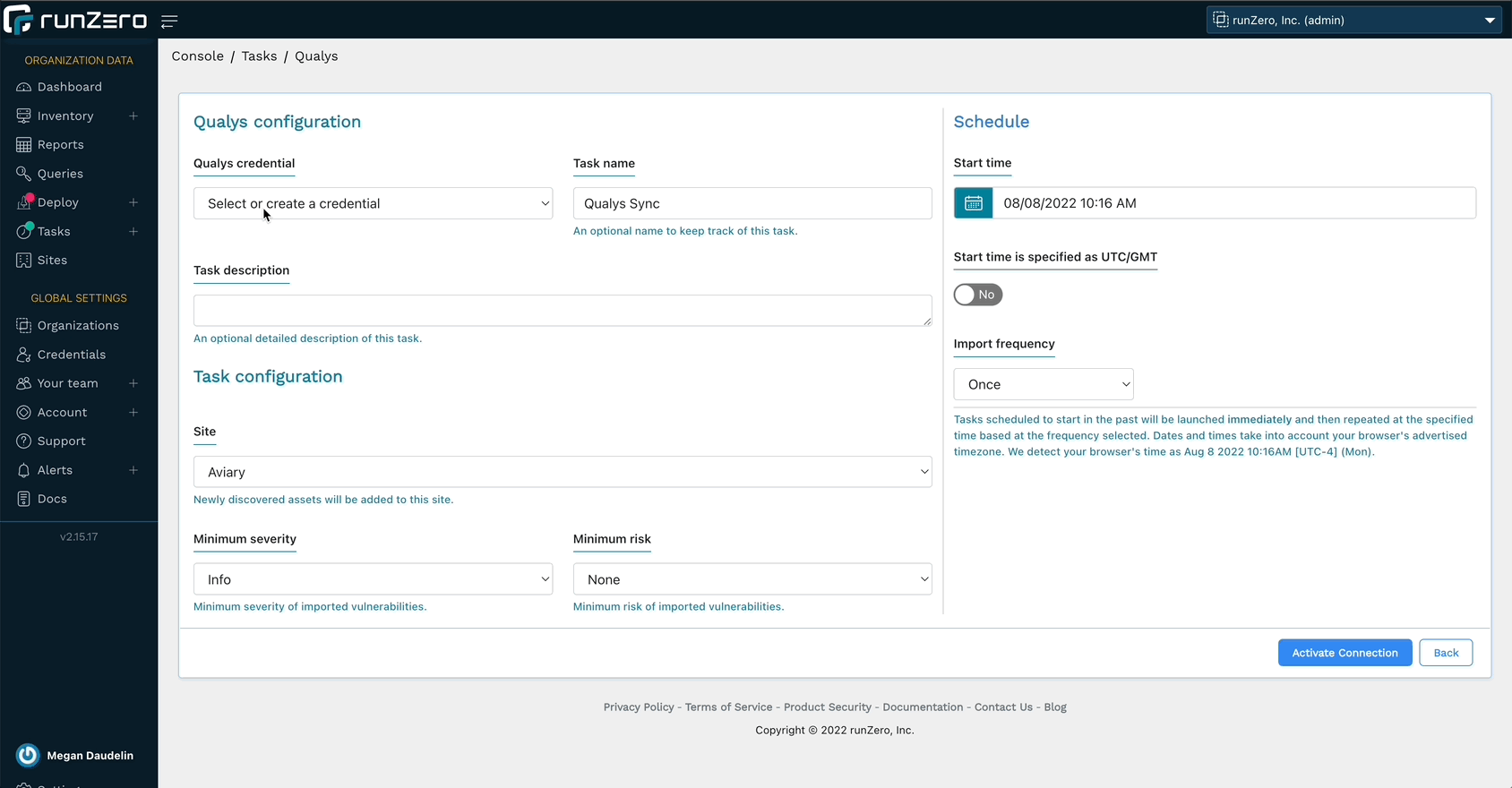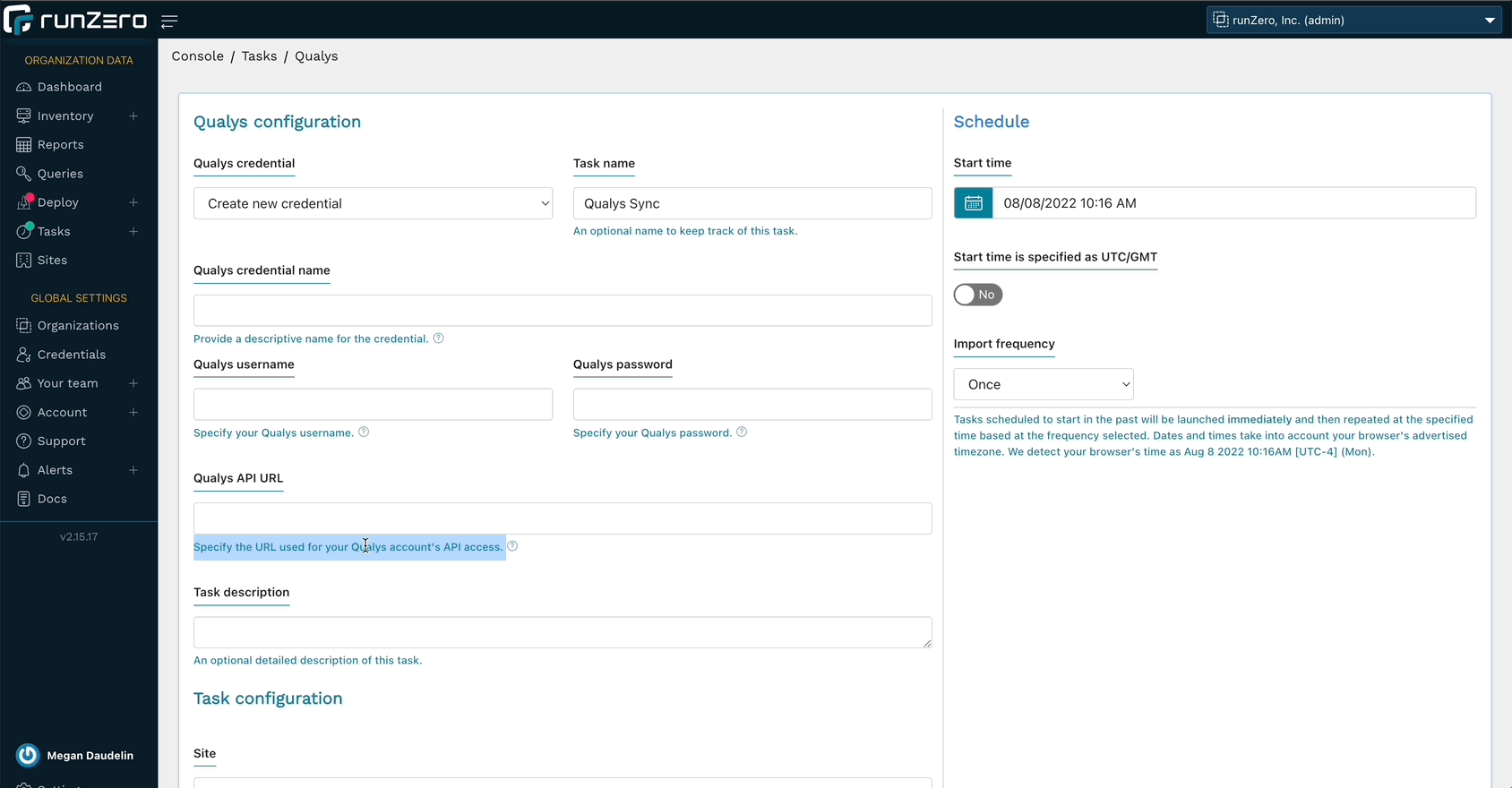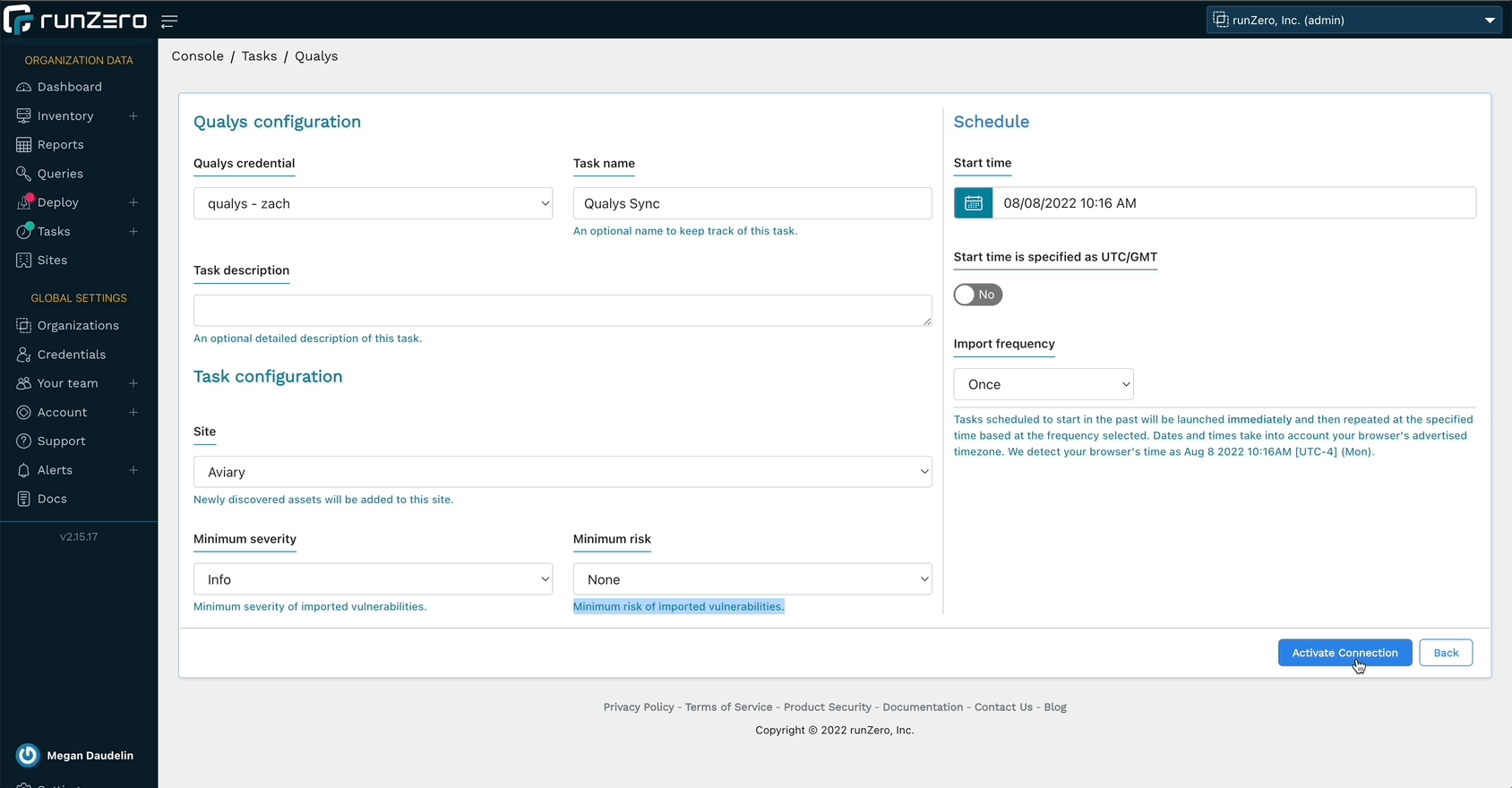
Gathering vulnerability data from Qualys #
runZero Enterprise users can now enrich their inventory with vulnerability data from Qualys. This allows you to search for Qualys attributes, software entries, and vulnerabilities in runZero, as well as find assets not scanned by Qualys. runZero automatically correlates Qualys assets to runZero assets based on unique fields. Vulnerability data can be viewed in the asset detail view as well as a dedicated inventory tab. Vulnerability attributes include CVSS score, relevant CVEs, vulnerability description, and any recommended remediations.
To get started, set up a connection to Qualys.
Release notes #
The runZero 3.0 release includes a rollup of all the 2.15.x updates, which includes all of the following features, improvements, and updates.
New features #
- Rumble is now runZero and the product UX has been updated to match.
- runZero Enterprise customers can now sync asset and vulnerability data from Qualys VMDR.
- Users can now specify a Default Organization in the profile settings page.
- A custom query to find DrayTek Vigor routers has been added.
- The Organization API now supports asset merging.
Product improvements #
- Outlier calculations and insight queries now automatically run as daily analysis tasks.
- Outlier calculations and insight queries can be regenerated on demand using the Metrics menu on the Tasks overview page.
- Merging assets with foreign attributes from the same source now retains all sets of foreign attributes.
- Software entries imported from SentinelOne and Tenable now report their service addresses.
- The Software and Vulnerabilities datatables now have a “view more details” button.
- The Asset and Service attributes reports can now be filtered by Site.
- API keys are now shown hidden by default and can be copied to the clipboard through a click.
- Vulnerability details are now available on the Vulnerability Inventory screen.
- Improved ability to extract Microsoft Windows information from web services.
- Improved ability to extract information from NetBIOS, including new detection of Domain Controller roles.
- Hosted Zone scan limits have been increased.
- The runZero Explorer now logs configuration file loading and reports any syntax errors.
- Hostname identification from LDAP responses has been improved.
- Filtering of non-unique MAC addresses has been improved.
- Inconsistent SNMP data handling has been improved for certain classes of devices.
- The API now returns all attributes, sources, and subnets for a single asset.
- The runZero Explorer now runs as a delayed auto start process on Windows to increase reliability after reboots.
- The Organization Overview report now includes navigation links to return to the top of the report.
- Click-to-copy functionality has been restored for MAC addresses displayed on inventory pages.
- Asset export query errors now return HTTP 400 status code with descriptive bodies.
Performance improvements #
- The Queries datatable has been redesigned and is now more performant.
- The Route Pathing report is now more performant and aborts early in out-of-memory scenarios.
- Processing speed for large Nexpose and Tenable imports has been improved.
- Improved support for processing very large scans.
- Improved performance of the software and vulnerabilities tables.
Fingerprinting changes #
- Improved operating system fingerprints for Amazon, Azure, and GCP integrations.
- Improved operating system fingerprints for Red Hat Enterprise Linux / CentOS, Fedora, Rocky, and Ubuntu releases.
- Improved fingerprints for Windows operating system.
- Added the ability to fingerprint McAfee ePolicy Orchestrator (ePO) and Agent.
- Improved NetBIOS, NTLM, and LDAP fingerprinting logic.
- Improved coverage for networking gear, including vendors Cisco, Dell, and Extreme Networks.
- Improved NTP banner fingerprints.
- Printer detection has been improved.
- OS fingerprinting will now use Rapid7 fingerprints, when Rapid7 is the only data source.
- Additional support for products by 2N, Axis, D-Link, DrayTek, FortiNet, Foscam, FrontRow, Hisense, Impinj, Kentec, OleumTech, Schneider Electric, SEL, Synology, and VMware.
Integration improvements #
- Improved hostname-based merging for Rapid7 imports.
- Improved support for processing very large Rapid7 imports.
- Software will now be populated from Rapid7 imports.
- Rapid7 foreign attributes have been adjusted for clarity.
- Services will now be populated from Censys.
- The InsightVM integration now supports larger imports.
Bug fixes #
- A bug in the AWS Configuration UI causing the “Lambda instances” option to not persist has been resolved.
- A bug that could prevent external users from being directed to their main SSO login page has been resolved.
- A bug which could cause stale software entries to be retained has been fixed.
- A bug in the Insights table which could render very large buttons has been fixed.
- A bug that could lead to a 500 error when accessing the users endpoint of the organization API has been resolved.
- A bug that could cause tooltips to persist on the screen has been resolved.
- A bug that could cause the vulnerabilities table to appear empty when sorted by the details column has been fixed.
- A bug that could cause the HTTP probe to abort early has been resolved.
- The asset tag update and bulk asset tag update APIs now work as documented.
- Fixed a bug which prevented all org admins from deleting other users.
- The User Last Activity date now shows the correct date.
- A bug that could prevent connector tasks from running in parallel while connecting to third-party APIs has been resolved.
- A bug that prevented organization administrators from deleting other users has been resolved.
- A bug affecting inventory multi-select operations has been resolved.
- A bug preventing inventory column selection has been resolved.
- A bug that could indefinitely stall a task has been resolved.
- A bug affecting license warning banners has been fixed.
- A bug affecting macOS Explorer upgrades on M1 systems has been fixed.
- A bug that prevented importing VMware assets has been fixed.
- When a templated task fails due to an Explorer being unavailable, copying the failed task now retains the connection to the template.
- A bug in the Overview report which showed blank addresses for Unscanned assets has been resolved.
- A bug that caused scan copies to get assigned to a different site has been resolved.
- A bug that prevented OS icons from showing on inventory tables has been resolved.
- A bug that prevented copying or updating Nessus connector tasks has been resolved.
- A bug that could lead to an error in the External Asset Report when no assets were present has been resolved.
- A bug that could cause the Export API to return a 500 instead of 400 for invalid queries has been resolved.
- A bug that caused some Explorer updates to fail on Windows has been resolved.
















