Overview #
Version 1.6.0 of Rumble Network Discovery is live with support for configurable scan grace periods, data retention policies, additional protocol support, enhanced fingerprint coverage, new search keywords, and much more.
Scan Grace Periods #
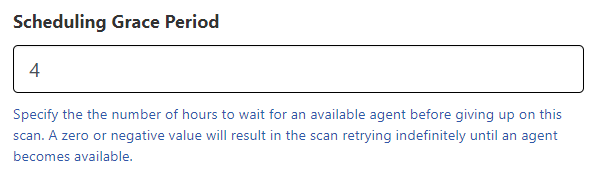
Starting with the 1.3.2 release, Rumble would automatically cancel a scheduled or recurring scan if the intended agent was not available after four hours. This fixed grace period prevented scans from stacking up in the case of a slow scan or offline agent, but it didn't work for all use cases, and this is now configurable at the scan level. Every new scan (created by the UX or the API) can now specify how long it should wait for the specified agent to become available. A value of zero will allow the scan to wait indefinitely. For folks with large numbers of scans scheduled on a small number of agents, extending the grace period can prevent scheduling timeouts from interfering with the scan.
Data Retention Controls #
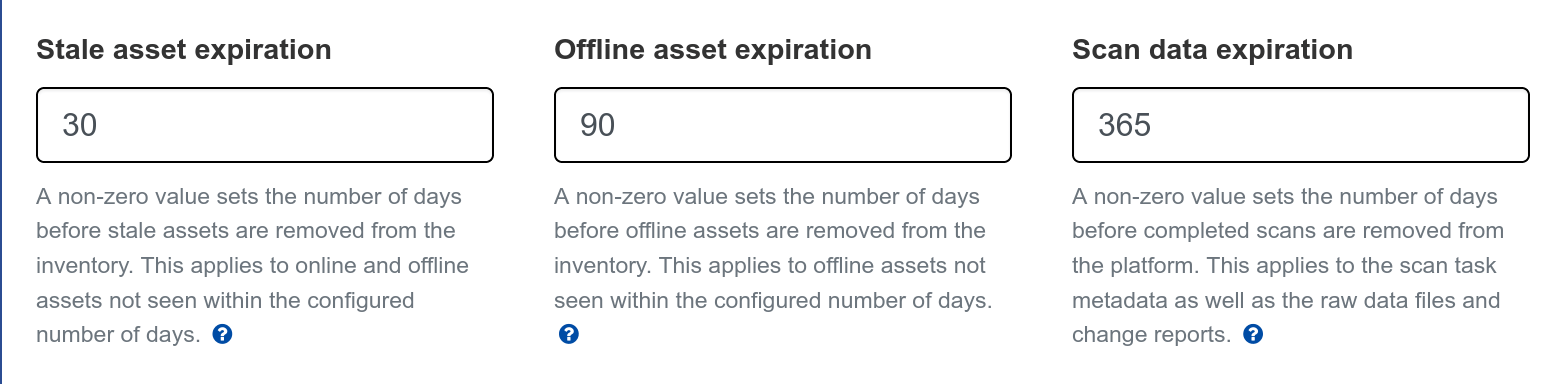
This release adds support for three new data retention controls. These are set at the Organization level (on the Organization Settings page) and can be used to automatically remove old offline assets and scan data. If your organization mandates certain data retention policies from your service providers, these controls make it easy to stay in compliance. For folks with short DHCP leases or that scan guest networks often, the Offline Asset Expiration setting can be used to remove old offline assets at a configurable time period (30 days, 90 days, etc). For additional information, please see the documentation.
Search Improvements #
The 1.6.0 release adds a number of new keywords and prefixes to support an even wider set of use cases.
The default search behavior is to perform a partial match. This release adds support for exact matches by specifying the = prefix to the search term.
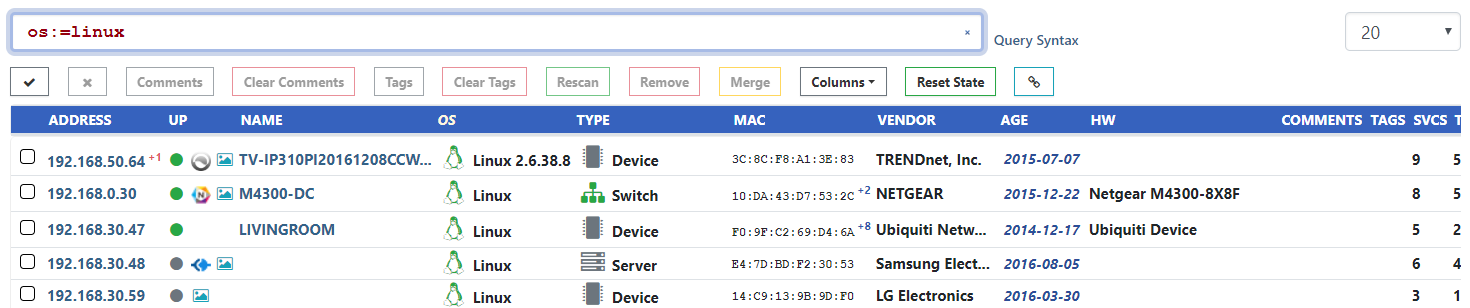
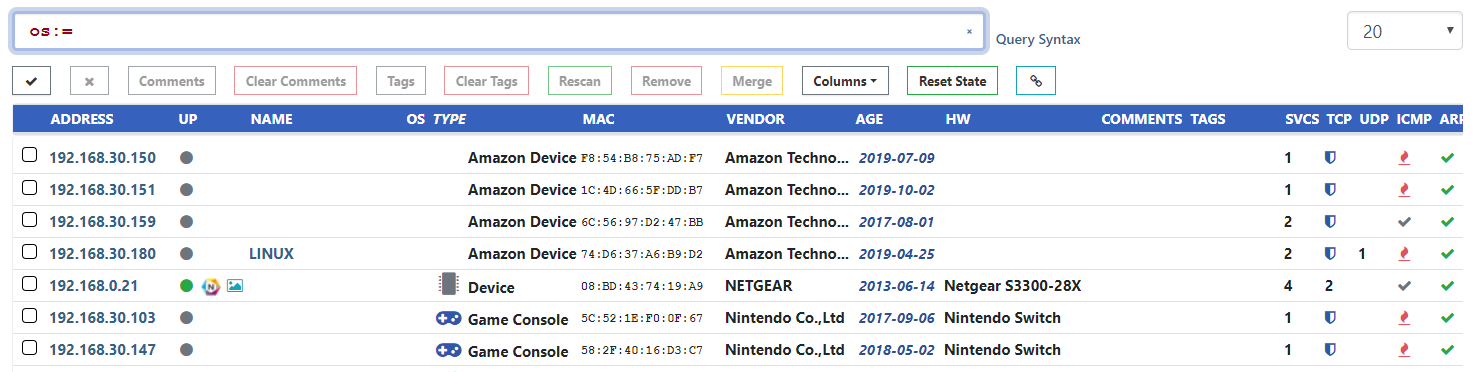
For example, to find all assets with an identified operating system of just Linux, but not identified as specific flavor of Linux, the query os:=Linux can be used.
Exact matches also work for empty fields. To find all assets with no identified operating system, the query os:= can be used.
Four new search keywords have been added to help filter assets by IP address. These are haspublic, hasprivate, hasipv6, and haslinklocal.
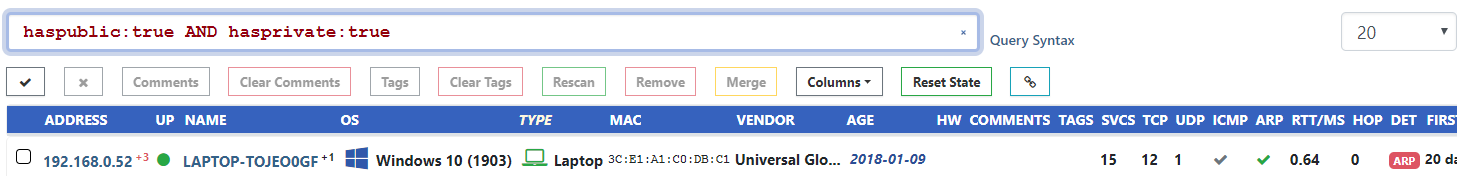
Looking for all assets that have both a public and private IP address? The search query haspublic:true AND hasprivate:true will extract these.
Rumble considers all non-reserved IPv4 space to be public and all RFC1918 space to be private. Filtering based on other IP ranges can use the existing net:<cidr> syntax.
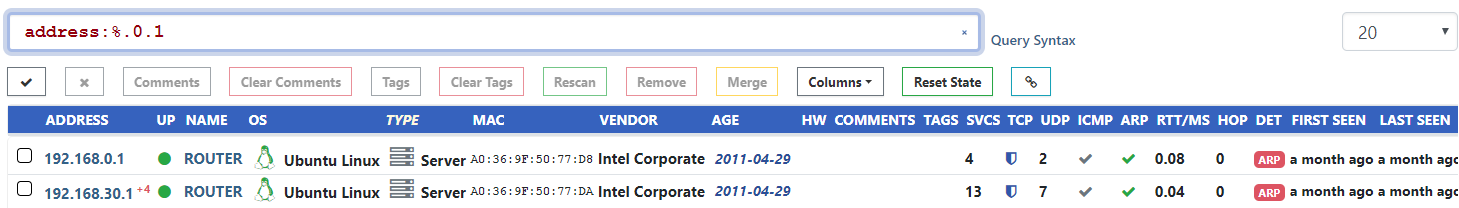
The net:<cidr> search keyword works great for prefix filtering, but sometimes you need to filter based on IP suffix instead.
If you use a standard addressing convention and want to find all assets that have an IP address ending in a specific octet, this is now possible using the address:%.<octet> syntax.
This syntax works for any part of the address.
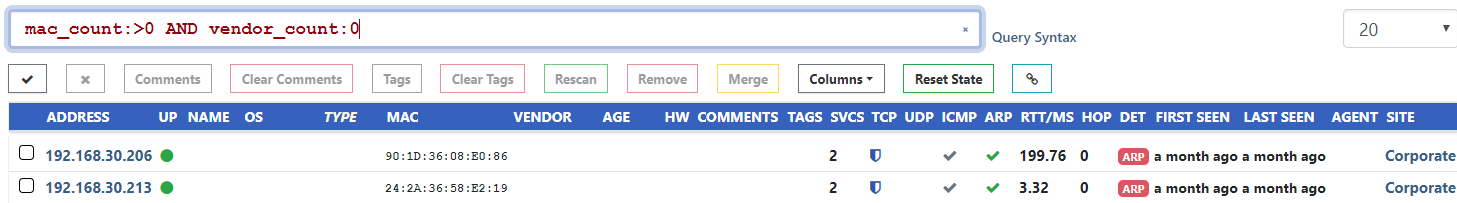
The 1.5.0 release introduced new count keywords, but did not cover the MAC Vendors field. This has been corrected and it is now possible to search based on the number of unique MAC address vendors associated with an asset.
One use case is identifying assets that use unregistered MAC prefixes: mac_count:>0 AND vendor_count:0.
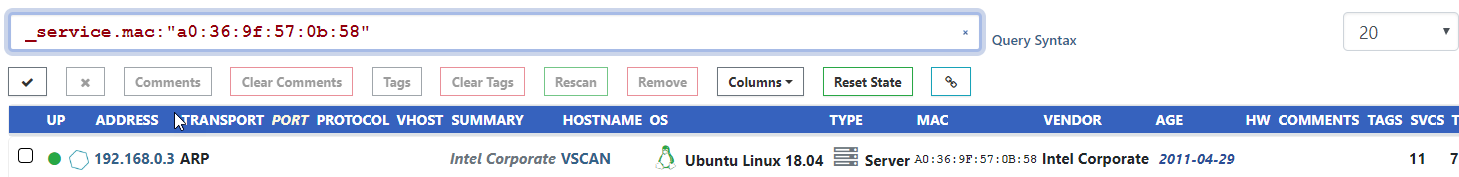
Occassionally an asset or service attribute will have the same name as a search keyword. For example, if a service reports an attribute named mac and a search is performed for mac:pattern, this will
match the asset MAC attribute instead. To disambiguate these, this release adds the _asset. and _service. prefixes. These can be prepended to any keyword to limit the search to the
asset or service attribute respectively. In the previous example, the search query would become: _service.mac:pattern.
In addition to the changes above, a bug that prevented searches for less than one hostname has been fixed (name_count:0 and name_count:<1), and the screenshot inventory now sorts by IP Address and not Port by default.
Security & Authentication #
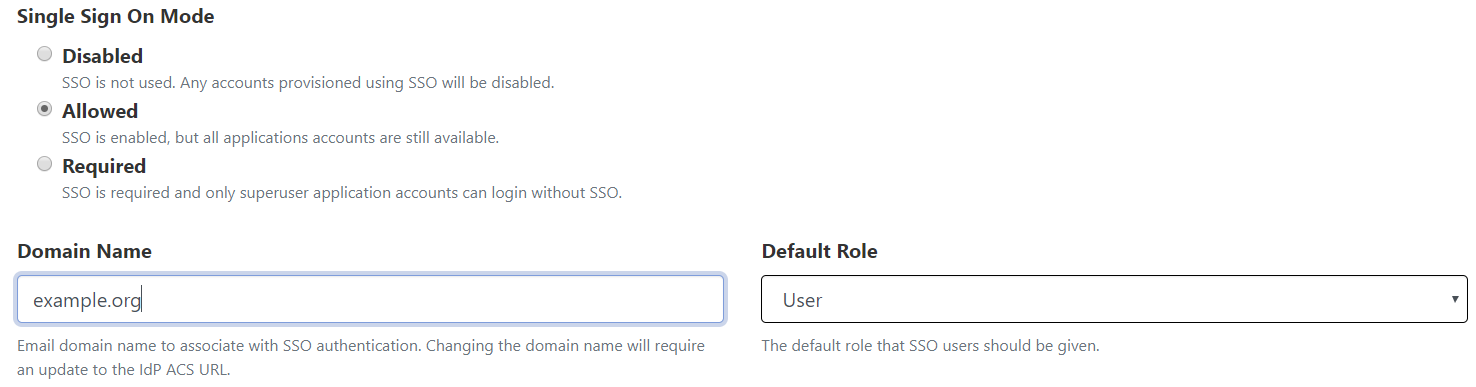
Single Sign On users can now specify the default organization role of SSO-enrolled users. Additionally, a bug that prevented superusers from logging in directly when SSO was in required mode has been resolved.
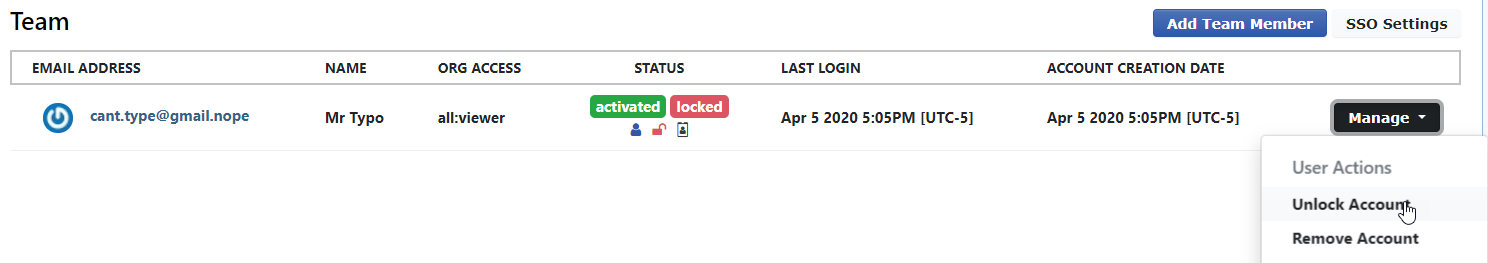
Temporary account lockouts are now enforced after 10 failed login attempts. This only applies to non-SSO users and resets each day. Locked out accounts can be manually unlocked by any superuser from the Team page.
Protocols & Fingerprints #
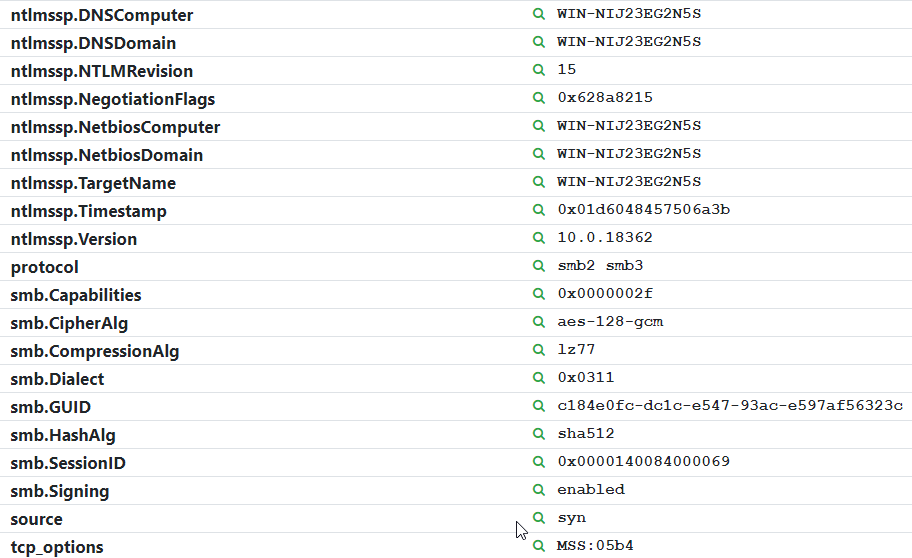
A ton of new fingerprints and protocol improvements were included in this release. At the protocol level, additional data is gathered for SMB, HTTP, and RDP services, including support for SMB1 detection, and explicit reporting of SMB3 support. The SMB probe also reports the supported encryption and compression methods. For a deep dive into our SMB3 research, take a look at our blog post about SMB2 session prediction.
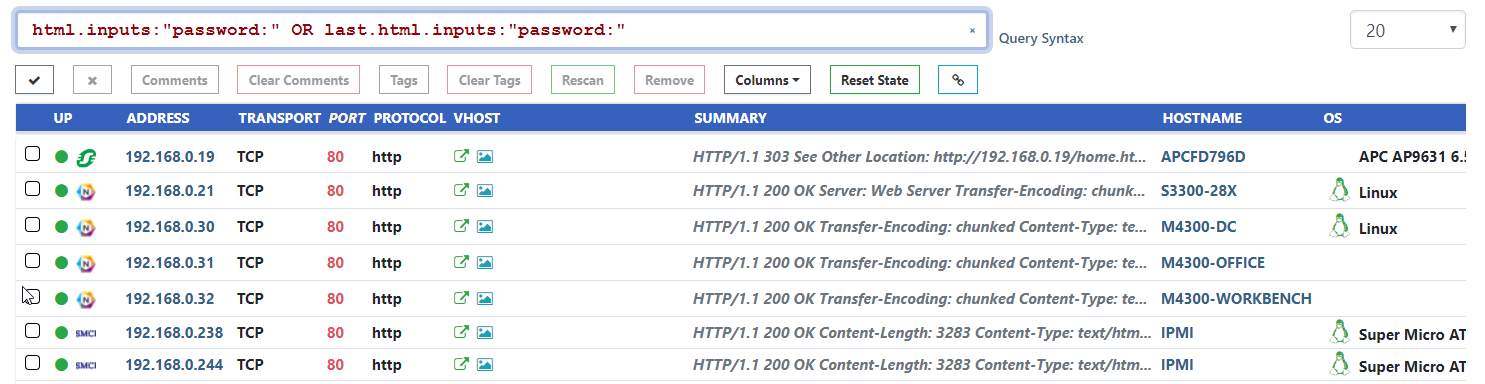
The HTTP probe also received big updates in this release, with a number of bug fixes and reliability improvements. HTML forms and inputs are now reported via the html.forms and html.inputs service keys. These fields can be used to find devices with login pages across the network. An example query that finds all web services with a password field would be: html.inputs:"password:" OR last.html.inputs:"password:".
Rumble uses the open source Recog project as the primary fingerprint database in addition to non-public methods and heuristics. The development branch of our fork is the easiest way to keep up with Rumble fingerprint updates. Since the 1.5.0 release, fingerprints have been added for HTTP, x509, SSH, FTP, and SIP protocols. This release includes a big update to Crestron, Ubiquiti, Extron, Cisco, VMware, and ShoreTel fingerprints.
Release Notes #
The complete release notes for v1.6.0 can be found in our documentation at the links below.
If you haven't had a chance to try runZero before, or would like to play with the new features, sign up for a free trial and let us know what you think!