As a follow-up to our recent post on the crucial role of attack surface visibility in M&A, we wanted to demonstrate how to apply runZero in an M&A transaction with a real-world example.
But first — not a hypothetical scenario, but a real runZero customer story. A conglomerate initially planned to use the runZero Platform to assess risk in M&A transactions. Upon completing a deal, they would scan the new subsidiary’s environment to better understand infrastructure risks. This allowed them to quickly identify issues, prioritize critical assets, and address vulnerabilities. Over time, this approach evolved into a full-scale asset discovery and exposure management service, now deployed across all subsidiaries to ensure continuous risk analysis and attack surface visibility.
Now let's go through a scenario about two fictional companies, RZ Corporation, who is in the process of acquiring ACME Corp.
Example Scenario: RZ Corporation's Acquisition of ACME Corp #
As in most cases, Legal teams from both organizations have agreed on terms as part of the M&A discussions and as part of those, important considerations has been put in place.
To illustrate the challenges of M&A security due diligence, let’s consider a scenario where RZ Corporation is in the process of acquiring ACME Corp. As is common in such transactions, legal teams from both organizations have negotiated and agreed upon the terms of the acquisition. Alongside these discussions, key considerations have been established to ensure a smooth transition:
ACME Corporation has given RZ Corporation the right to:
Perform internal and external attack surface discovery to inventory all network connected assets;
Perform an API integration with no more than three pre-selected solutions (CrowdStrike, Tenable and Wiz);
Provide access to the data to only a select number of RZ Corp security personnel as part of the security due diligence;
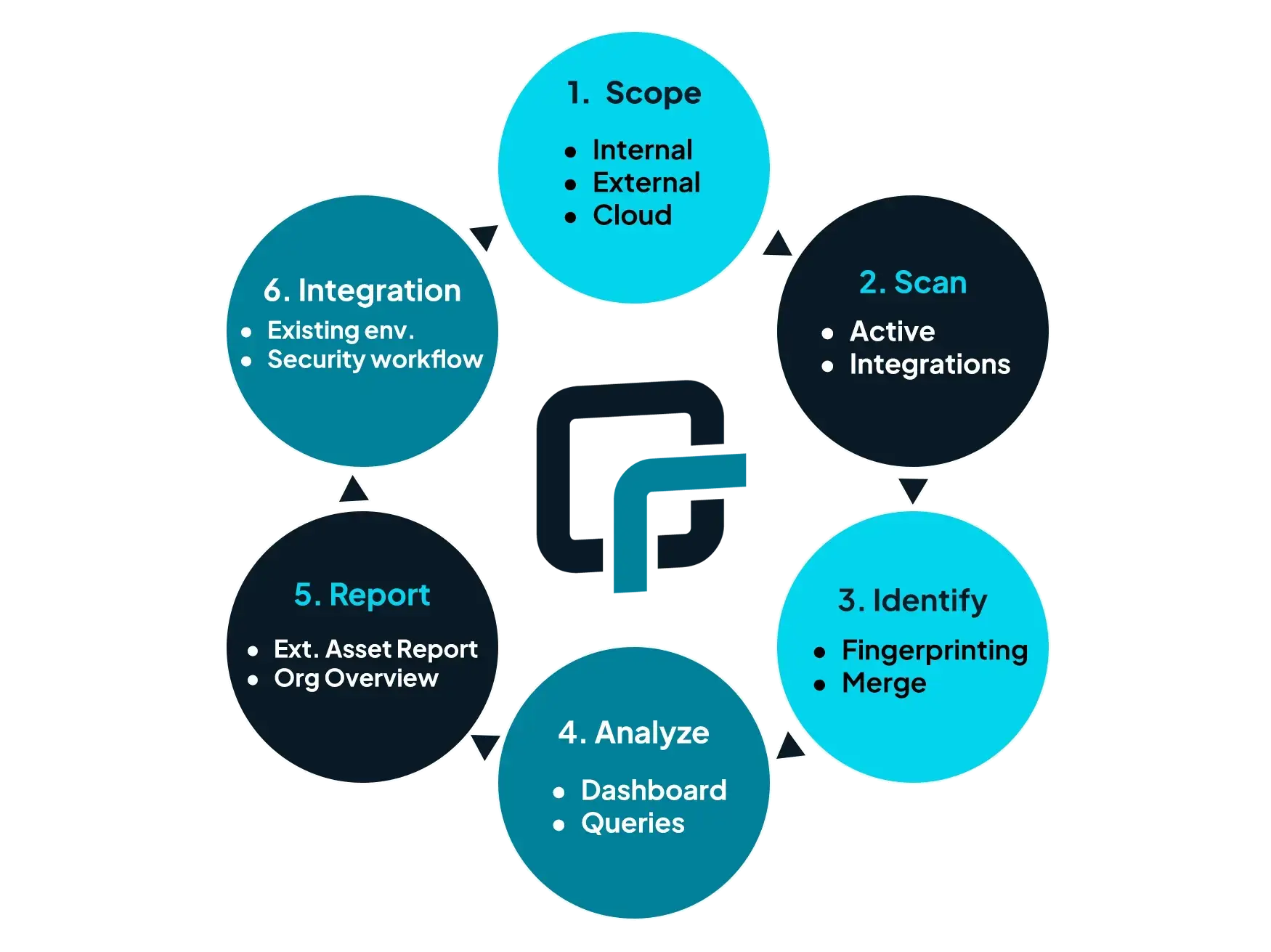
One of the first things to do prior to deploying runZero is agreeing on how the data will be organized, especially with data access requirements in place. There has to be data segregation between the M&A environment and any other tenants. The concept of runZero Organization and Project becomes very important.
Phase 1: Data Organization #
An organization in runZero refers to a distinct entity, which could be a business, a specific department within an organization, or even one of your customers. All actions, tasks, Explorers, scans, and other objects within runZero are associated with a specific organization and are kept separate from one another to ensure proper isolation.
In a similar manner, Projects function as a specialized form of organization, designed for temporary use. While Projects behave like organizations, they offer the added benefit of supporting up to five times the number of project assets as the total number of licensed live assets. For instance, if your runZero license covers 1,000 assets, you can manage up to 5,000 project assets. This feature is particularly valuable when dealing with mergers and acquisitions (M&A) environments, where the asset count may be unknown. The ability to scale up by 5x provides greater flexibility, helping to avoid concerns about exceeding license limits while effectively segregating different environments.
RZ Corporation creates a runZero Project for “ACME Corp” where they will populate all of the attack surface details and is completely separated from RZ Corporation’s attack surface.
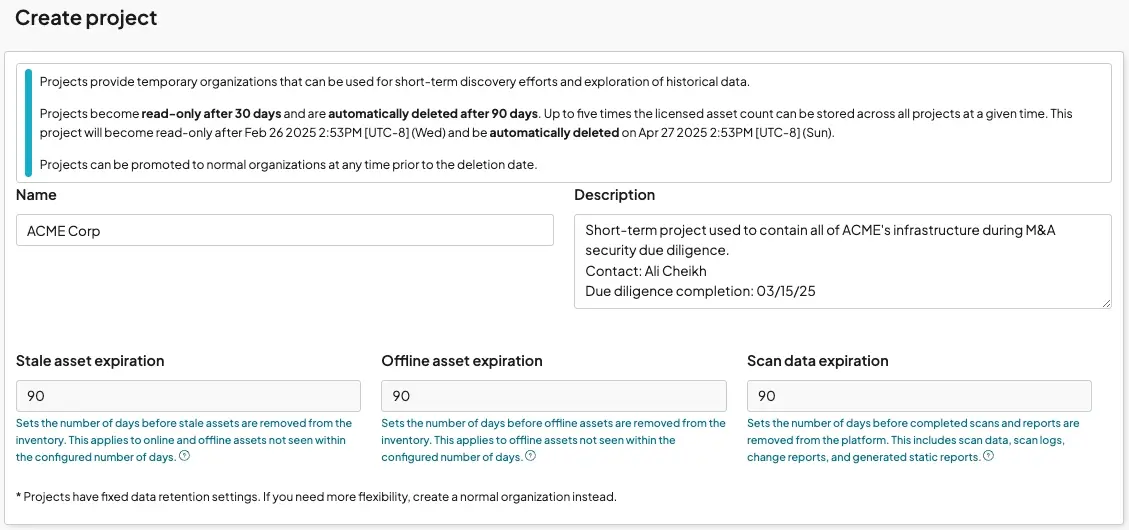
An additional critical aspect of segregating M&A data is enforcing a strict need-to-know access policy, ensuring that only a limited number of individuals can access sensitive information. This step is vital for due diligence, as it guarantees that confidential data is shared solely with those who need it to carry out their responsibilities. By limiting access in this way, risks are minimized, and the integrity of the transaction is better protected.
Each runZero Project is equipped with its own role-based access control configuration, allowing not only the separation of data into distinct entities but also the enforcement of specific access permissions. Below is an example of a user, illustrating which Organizations or Projects they have access to and the roles they are permitted to perform within each.
Once the data organization is in place, the next step is to start discovering ACME Corporation. We will be leveraging two out of the three solution approaches, Active scanner and API integration as per the agreement.
Phase 2: Internal, External and Cloud Attack Surface discovery #
We will begin by deploying the runZero active scanner, known as "Explorer," at ACME Corp. There are multiple deployment options for the Explorer, including shipping a pre-configured Raspberry Pi with the Explorer installed or providing the Explorer binaries to ACME Corp for installation on a system, such as a laptop, server, or desktop. This approach eliminates the need for hardware shipments or the installation of agents on every asset, streamlining the data collection process.
runZero leverages an Explorer to perform the active scanning technology, proprietary unauthenticated active scanner. The Explorer can be installed on a VM server, laptop, desktop or even Raspberry Pi.
Ensuring the right Project is selected called “ACME Corp” and depending on the preferred OS and architecture. In our case we’ll pick a Red Hat Enterprise Linux (RHEL) virtual machine that ACME Corp has allocated for the M&A project and provided the required network access.
For air-gapped networks or environments where an offline data collection is required, runZero offers a command-line tool, CLI scanner, that can be used to discover those assets.
This ensures that regardless of the type of networks, runZero can provide visibility to the attack surface of the M&A organization.
Once the Explorer is deployed, the next step will be managed from the runZero Console to kick-off the network scans. We will start with the internal attack surface and will scan the full RFC1918 to discover all of the assets that exist at ACME Corp. We can also do targeted scans of certain networks that were provided by the M&A organization. Here is a screenshot showing the RFC1918 scan:
After scanning the internal attack surface, RZ Corporation will enhance the runZero active scanner data by integrating with existing security solutions. This integration will involve importing data from CrowdStrike and Tenable through the CrowdStrike Falcon and Tenable Nessus APIs. These integrations will enrich the asset inventory and provide valuable insights into vulnerabilities and software. An additional benefit of the integration is the ability to identify endpoints lacking an EDR agent and/or Vulnerability Management agent/scanner, further strengthening the organization's security posture.
Next will be discovering ACME Corp’s external attack surface by leveraging runZero’s Hosted Explorer that can scan all of the external IP ranges as well as all of the public IP addresses that were found by the internal scan.
From the scan configuration page below:
Choose US - New York as the Hosted zone (this is a runZero-hosted Explorer in the cloud).
- In the Discovery scope, enter the following data:
public:all:This will scan all the public IPs found with the internal network scanned with runZero.asn4:12345:Enter all ASNs in this format to target all IP addresses registered to this ASN. Note the digit 4 after ASN in the notation.domain:acme.org:Add all domains that you are targeting. runZero will add all subdomains connected to these domains.
Finally we will be covering the Cloud attack surface to complement the full ACME Corp environment and complete the visibility portion. We will leverage the API integration with AWS to pull in all of the cloud assets that exist in all of the accounts that belong at ACME Corp.
Once the integration is complete and the cloud asset inventory is established, we will proceed with a comprehensive external discovery of all publicly facing cloud assets. Using runZero, RZ Corporation can create a custom discovery scope that includes all AWS assets configured with a public IP range, as demonstrated in the query result below. This approach ensures a thorough assessment of external exposure across the organization’s cloud infrastructure.
source:aws and has_public:tYou can quickly kick-off an external scan task with all of the public IP ranges returned from the query above by selecting all of the resulting assets and clicking “Scan”.
Phase 3: Post-discovery review #
Dashboards & Outliers #
runZero’s goal is to empower security teams to fully manage the risk lifecycle: finding, prioritizing, and remediating all classes of exposures across internal and external attack surfaces, all in one place. As a single source of truth for exposure management across all of your M&A organizations.
Having the ability to highlight key post-discovery exposures and findings are critical to assess and understand the risk of ACME Corp
Typically one of the first available resources that our customers leverage for due diligence are Dashboards. They provide a customizable, visual view into your attack surface and can be created to serve different use cases such as compliance, vulnerability remediation, or asset visibility.
The Risk Management Dashboard is your centralized hub for taking action on risks, delivering actionable, data-driven insights with advanced findings widgets and customizable visualizations. As a cornerstone of runZero’s holistic exposure management, it provides comprehensive visibility and actionable context to help your team minimize exploitability windows, optimize resources, and reduce operational risks.
A wide range of visualization widgets is available to display operational information, trends, insights, goals, sources, and the most and least observed data. Additionally, you can create custom widgets based on specific queries to surface the exact data you need, which can be displayed as either a trend line or a latest count.
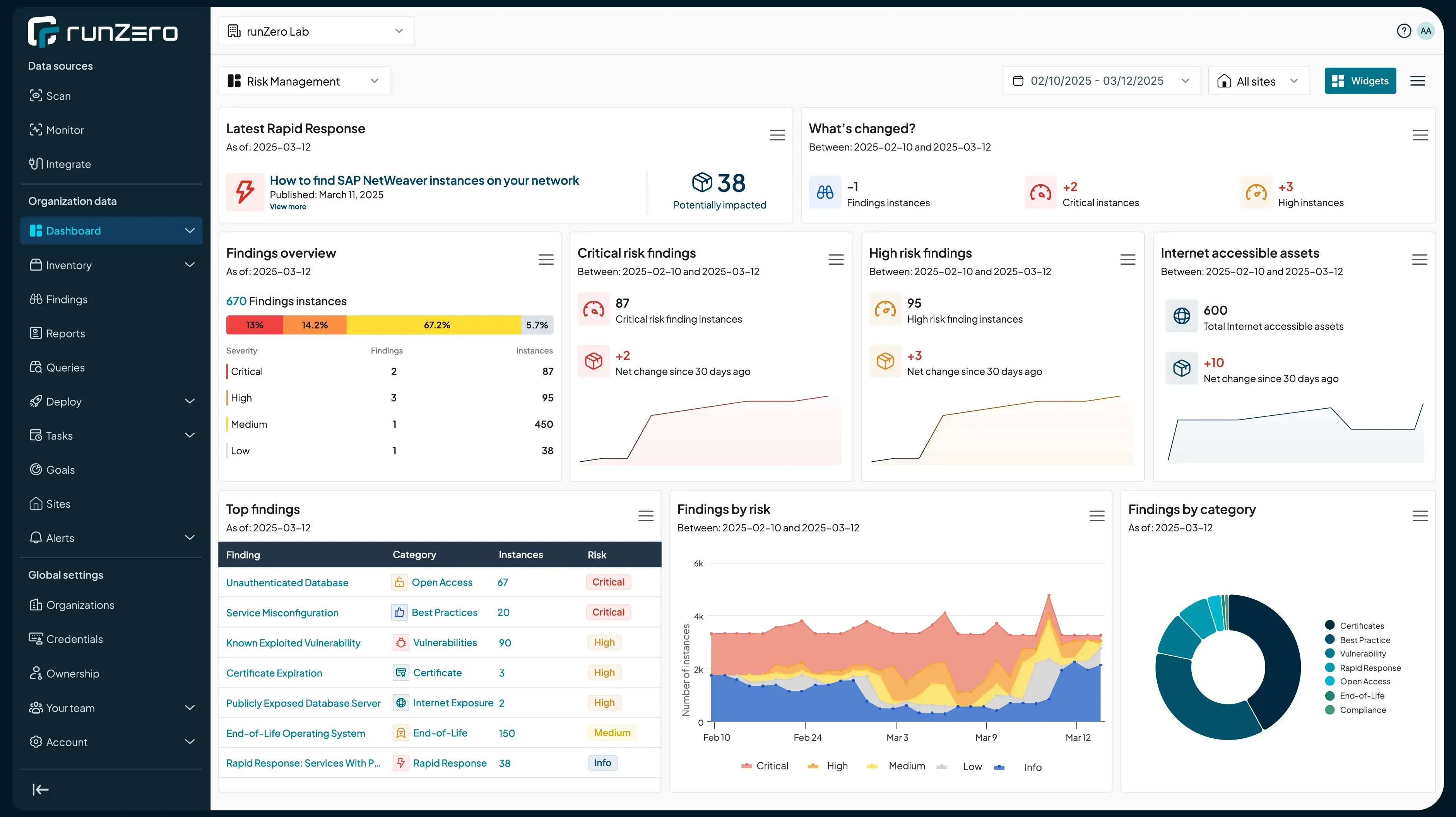
The Risk Management dashboard streamlines the entire risk management and remediation lifecycle by organizing exposures by type, mapping them to affected assets and services, applying context-driven criticality, and enabling tracking over time.
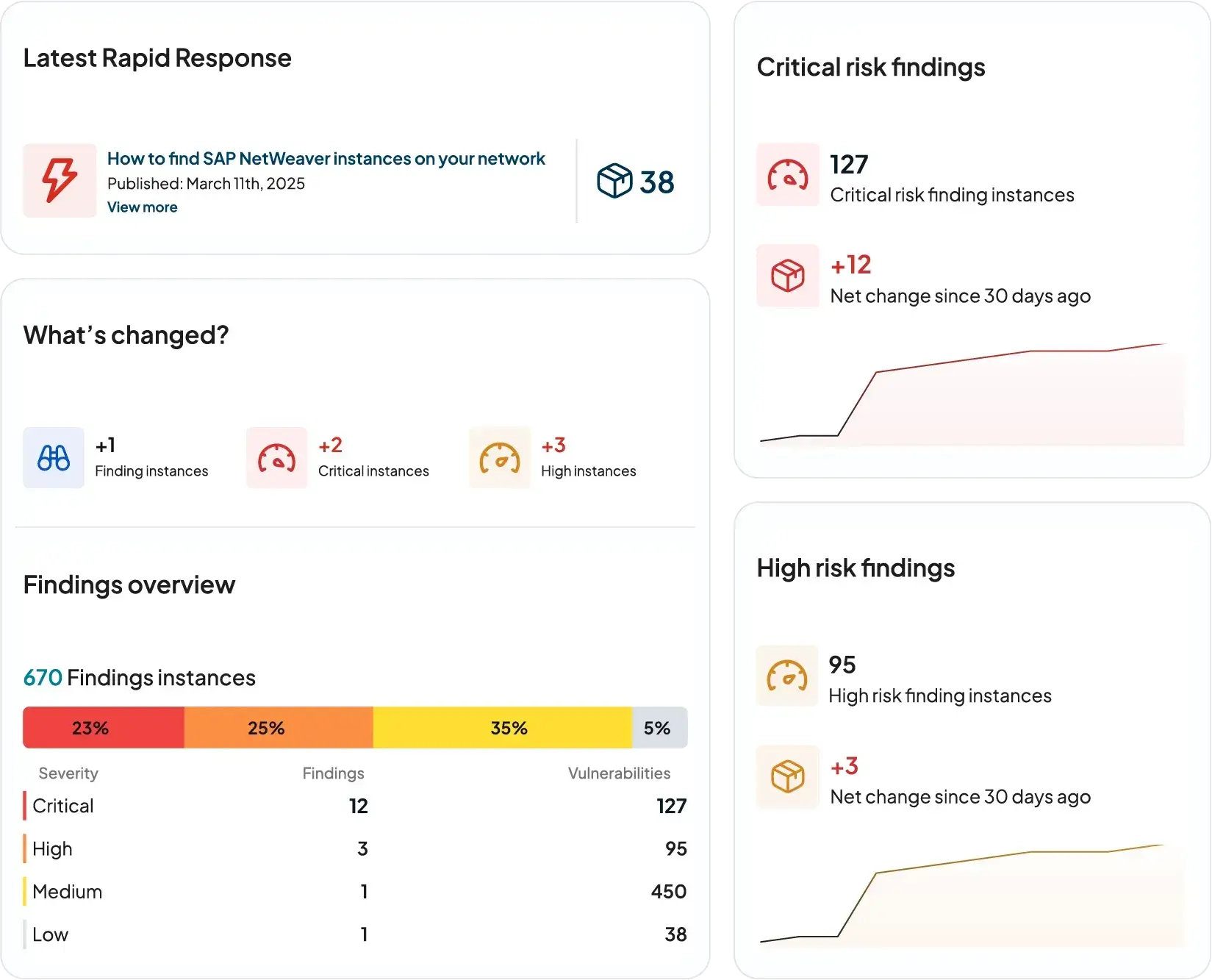
Let’s drill down a bit further into the Dashboard data. While exploring the available dashboard widgets, we focused on the Operating Systems and Type widgets, which provide a side-by-side comparison of the most and least observed OS/Type instances.
In the OS breakdown, we identified a few Hikvision cameras, which are listed as prohibited vendors for RZ Corporation due to NDA Section 889, as well as some legacy operating systems, such as Microsoft Windows CE.
As for the Type breakdown, nothing alarming jumped at first, but might require a bit more analysis, specially with the likes of Camera and DVR, making sure that those types of devices are being monitored by the ACME Corp security team or at least aware of it.
The breakdown of least seen and most seen dashboard widgets for the different datapoints (there are also breakdowns for Products, Protocols, MAC vendors to name a few) are very good at finding Outliers or anomalies in the network that are typically unmanaged or missed by security teams. Helping pinpoint what should be investigated first by the due diligence team.
runZero also offers the ability to create custom widgets, enabling users to track key metrics across their attack surface. Customers often configure different dashboards tailored to the specific aspects of the attack surface that are most relevant to their needs, such as Incident Response, Attack Surface Management, or M&A activities. runZero delivers the visibility and insights necessary to ensure that any security program or use case effectively covers the entire attack surface.
Reports #
Some of the out-of-the-box reports that are leveraged during due diligence are the External Asset Report and the Organization Overview Report.
The External assets report provides a point in time overview of your external assets. It shows all external facing assets and services in the organization.
The Organization Overview report offers a snapshot of the entire organization at a specific point in time, including details on the types of assets discovered and, optionally, information on each asset, such as screenshots. This report is valuable for internal stakeholders, providing an at-a-glance understanding of the attack surface's state at any given moment. It can also be scheduled for regular distribution (weekly, monthly, quarterly, etc.) to key stakeholders who need to review the report.
Inventory and Queries #
One of the unique propositions that runZero offers is the full depth and breadth of your total attack surface. The platform delivers superior visibility across IT, OT, IoT across on-prem, external, remote and cloud environments ensuring you have a complete understanding of your assets and their risk. runZero’s advanced fingerprinting goes deeper to uncover critical insights into services, connections, ownership, hygiene and more, building detailed profiles of each asset leveraging a library of almost 1,000 attributes. This unparalleled level of detail provides the insights you need to clearly understand what’s in your environment, identify vulnerabilities, expose risks, and act quickly to secure your networks.
Here we are showing an asset details page scanned by a runZero Explorer and not found in other security platforms we integrated with. As you can see, the level of details collected by the unauthenticated active scanner is second to none, providing insight into OS, Type, Hardware as well as additional information.
The following asset has been scanned by the runZero Explorer but also found in ACME Corp current tools (CrowdStrike/Tenable Nessus/AWS). runZero doesn’t only show the Explorer collect details but also cross references the datapoints from the 3rd party integration so at any time, users can view the CrowdStrike attributes, or Tenable Nessus attributes straight from the runZero Console without having to jump between 3 to 4 different consoles.
The screenshots above only show a section of the asset details page, more information is available such as what vulnerabilities are impacting that asset, what software is installed and what services/protocols/ports are exposed on the network.
Due to runZero’s unique ability to combine safe active scanning, passive discovery and API integrations, RZ Corporation is able to understand blind spots, or assets that are missing critical security controls. Examples are what compute endpoints are missing the Crowdstrike agent that should have it.
The below query surfaces unmanaged endpoints that were not managed by Crowdstrike that runZero’s Explorer found in ACME Corp’s network.
source:runzero AND NOT source:Crowdstrike (type:server or type:desktop or type:laptop or type:mobile)From the runZero console the results of the query shows you the list of assets that match:
Another exposure that RZ Corporation were keen to uncover were whether there are any risky or mis-configured assets such as potential bridges. Essentially assets bridging public and private networks but also running any remote management protocols such as RDP with an end-of-life operating system.
has_public:t and has_private:t and has_os_eol:t and protocol:rdpThe same query can be used in conjunction with runZero’s Network Bridges report that represents the resulting assets in a topology format. Please refer to this blog post that speaks to how runZero finds unmanaged devices for more details.
New to runZero? Start a free 21-day trial. runZero scales up to millions of devices, but it’s easy to try. The trial will downgrade to a free version for personal use or organizations with less than 100 devices.
Happy scanning!
















