Introduction #
VMware customers have had a tough time lately; Broadcom’s changes to licensing have pushed folks to seek alternatives and many are turning to the open-source Proxmox Virtual Environment (VE) as a replacement. Proxmox builds on the Linux KVM stack and provides a turn-key virtualization with simple clustering and high-availability features. Already popular with home labs, Proxmox is starting to gain serious traction within enterprise organizations.
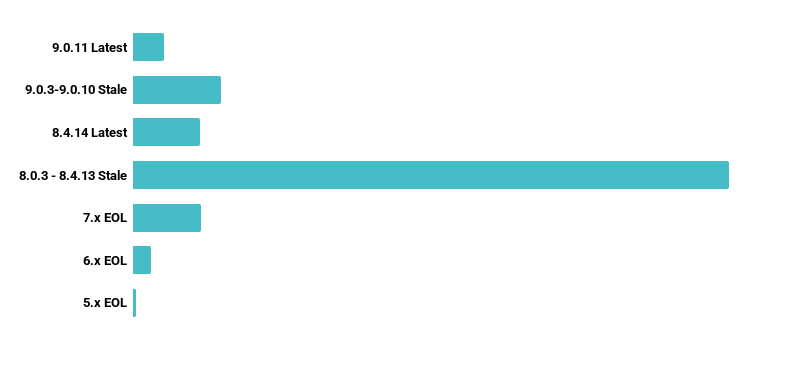
Over the last year, we’ve seen a massive increase in deployed Proxmox VE systems, but also a worrying trend: an increase in out-of-date and end-of-life installations. At the time of writing, the two latest versions of Proxmox VE are 9.0.11 and 8.4.14. All versions of Proxmox prior to 8 are End-of-Life (EoL); importantly, the entire operating system no longer receives security updates, not just the Proxmox VE software. This means that every new vulnerability in Debian may also impact these older versions, including supporting services like OpenSSH.
The graph below shows the frequency of specific Proxmox VE versions. Of note are the EoL systems running 7.x or older and the bulk of 8.x and 9.x systems hovering around early revisions of each minor release. Only a small minority of users are keeping up with patches.
The software undead #
Of all the vulnerabilities reported by runZero, End-of-Life (EoL) status is arguably the most significant. Once an operating system, hardware device, or software component goes out of support, the creator stops tracking vulnerabilities. The longer a system has been EoL, the more likely it is vulnerable to attack, and the more attractive it becomes to attackers. The lack of data makes risk management incredibly difficult. If you would like to learn more about EoL issues, check out our recent research paper, Undead by Design, as well as the October 2025 runZero Hour webcast.
Only you can stop zombies (software) #
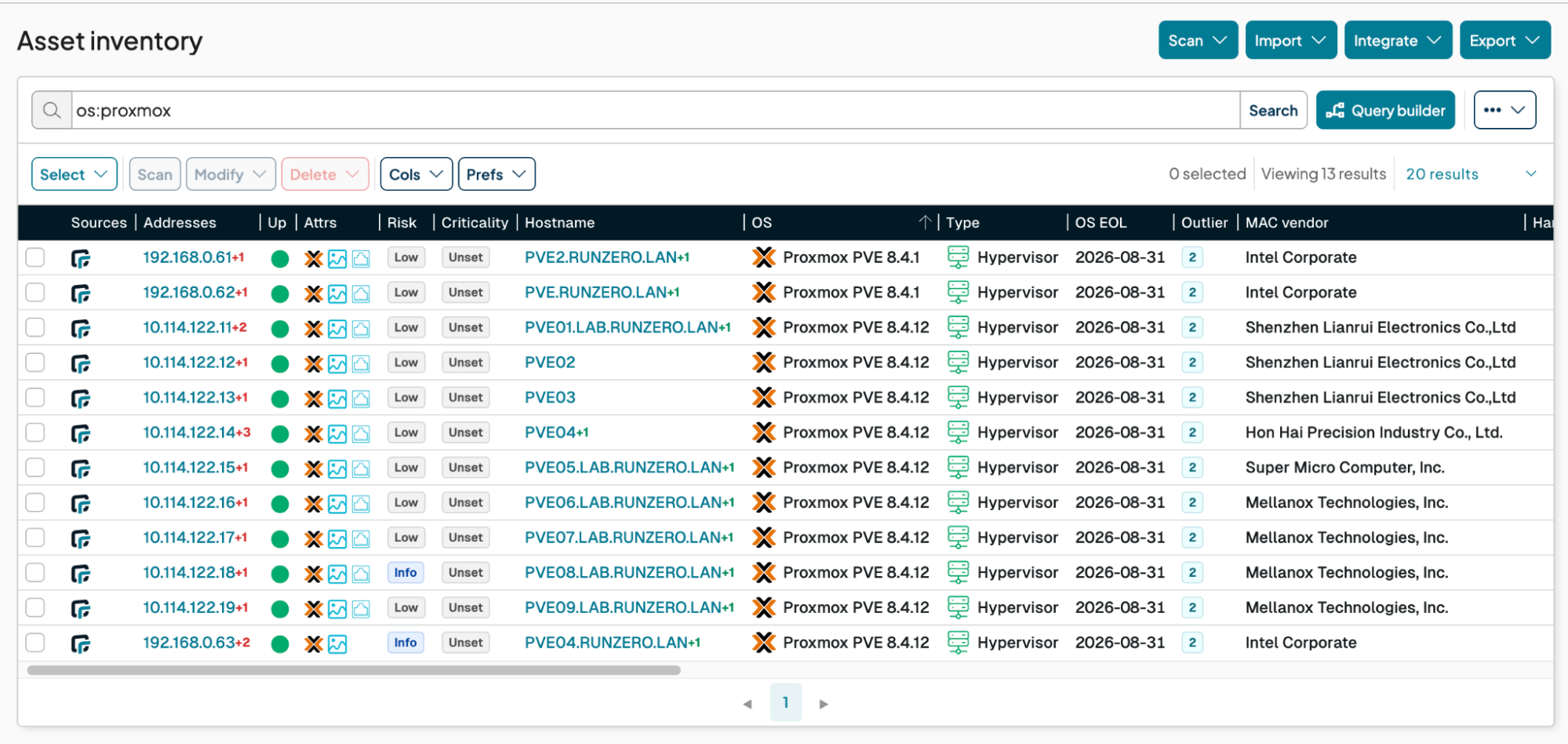
runZero tracks EoL status across dozens of operating systems, hardware devices, and software components and recently added support for Proxmox VE. runZero identifies the Proxmox VE version from an unauthenticated network scan and then populates the OS EOL column in the asset inventory. This simplifies the process of identifying systems that are already EoL and highlights which will become so soon without intervention. The following screenshot shows how to find Proxmox systems in the Asset Inventory and then sort the results by their EoL date; these are your soon-to-be-zombies.
Proxmox support schedule #
One of the reasons that we love Proxmox is that it’s tightly linked with the Debian release schedule, including EoL status and support. Typically this means that every major version of Proxmox VE is supported for three years. For example, Proxmox VE 8, the previous major version, is supported until June of 2026, three years after the Debian 12 (Bookworm) release. You can find the latest EoL table at: https://pve.proxmox.com/pve-docs/chapter-pve-faq.html#faq-support-table
The road ahead #
EoL is just one of the time-relative attributes tracked by runZero. Sorting your inventory by EoL is a great way to see the zombie horde gathering — but it's not the only field. TLS certificates are another type of time bomb that needs active defusing. You can find these by browsing to the Certificates inventory and sorting based on the expiration date. Going forward, we plan to expand EoL coverage to even more operating systems, hardware devices, and software components.
Proxmox virtual machines in runZero #
If you’re interested in syncing runZero directly with Proxmox, we now offer a custom integration:
This integration will import all Proxmox VMs, including IP information of the qemu-agent installed within the guest operating system.
runZero at home #
Did you know that runZero is free for small networks, including home labs? Head over to https://www.runzero.com/try/ now to start a trial account that can be converted to our free Community Edition; our free tier covers up to 100 assets, supports dozens of integrations, active scanning, passive traffic sampling, and a full suite of reports and queries. Love runZero at home? Bring us to work by reaching out to our team via this form – we would love to show you how to build an amazing exposure management program with runZero!
















