Transport Layer Security (TLS) is a widely used protocol for securing communications between two or more applications over an otherwise insecure channel. TLS is used in many applications, but is best known for its role in securing HTTPS. When combined with X.509 certificates, TLS and certificates provide confidentiality (data is encrypted so that unauthorized parties cannot read it), integrity (data is protected against tampering by others and data arrives complete and unmodified) and authenticity (data originated from its purported source). When TLS is properly configured, it is considered very secure. However, TLS can be misconfigured in ways that reduce, or even eliminate, its effectiveness. Finding misconfigurations can be tricky, but runZero helps you identify and remediate these faster than ever.
runZero finds TLS services and X.509 certificates across both your external and internal networks. It identifies insecure TLS configurations and helps you remediate them, ensuring your services and applications remain secure. runZero makes it simple to search all X.509 certificates on your network and can be used to find expired or expiring certificates. With the CA/Browser Forum’s decision to limit the validity period for certificates to less than 100 days by 2027 and less than 47 days by 2029, runZero helps you identify certificates that are not set up for automatic renewal.
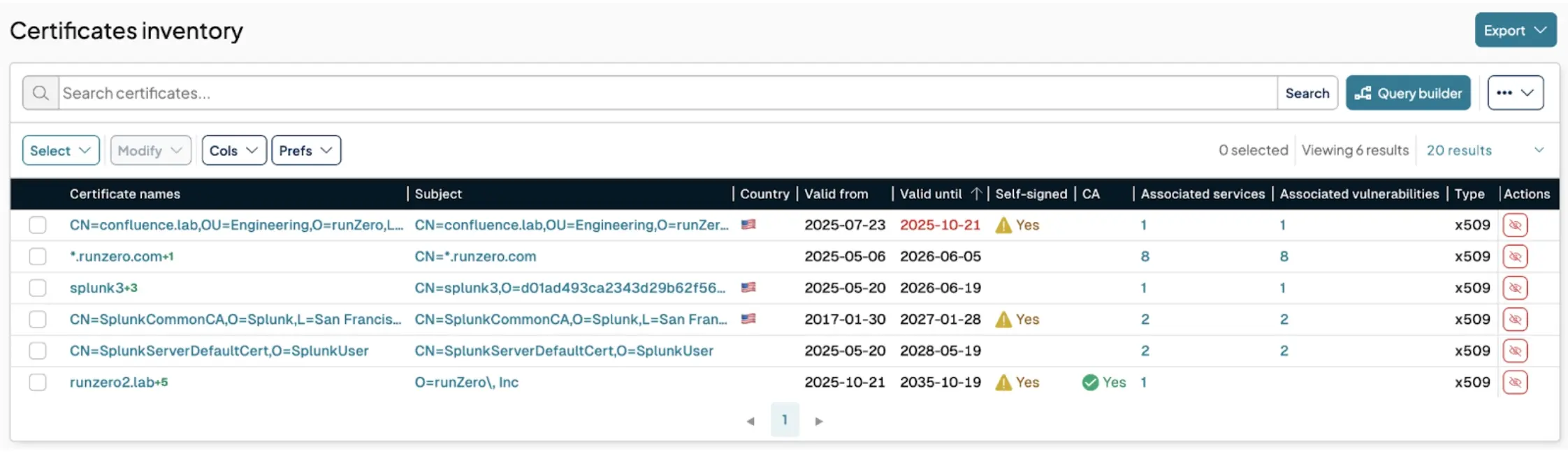
runZero’s Certificate Inventory is a central repository showing all X.509 certificates used by TLS services across your enterprise environment, including certificates found on non-standard ports and used by various applications and services. runZero’s “Certificate and TLS Service Risks” finding identifies, groups, and helps you prioritize remediation of insecure configurations, expiring certificates, and best practices.
Improved visibility #
runZero originally launched Certificates Inventory in March 2025. In October, we updated the look and feel to provide better visibility of certificate details, misconfigurations and risks.
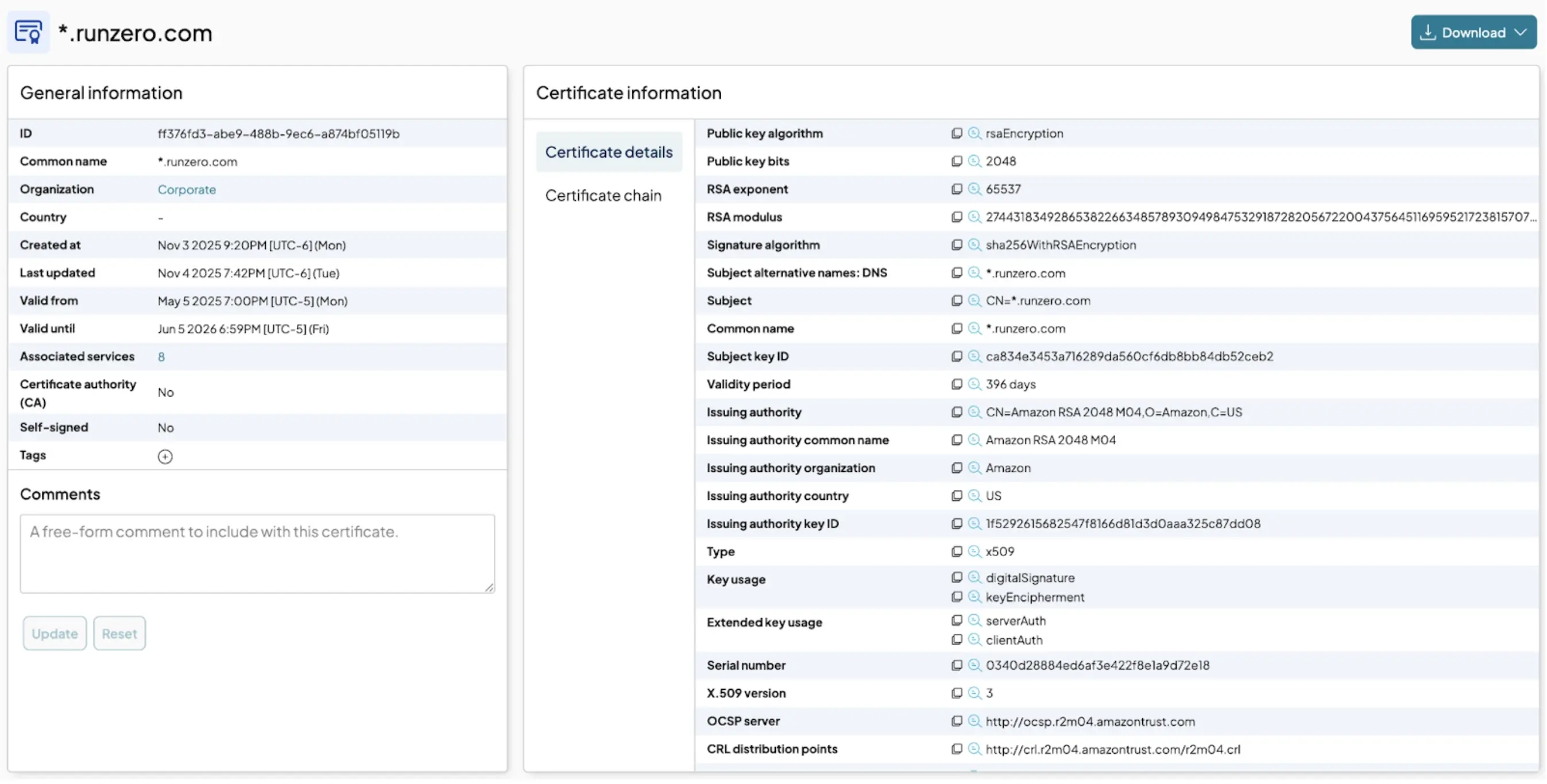
We’ve also made it much easier to see where certificates are found so you can quickly understand where to update a certificate. The certificate details page shows a list of assets where a certificate is installed and information about the TLS service using the certificate, including the address and port. This crucial link is essential for remediation, helping you immediately identify which assets need an update when a certificate is expiring or misconfigured.
New risk detections: Uncover misconfigurations & security gaps #
Visibility into your certificates is only half the battle; knowing where they pose a risk is the other. Our new risk detections expand runZero's ability to identify security issues associated with both X.509 certificates and the TLS services that use them.
runZero now detects and will create new findings and vulnerabilities for:
Insecure Configurations: Identify services running insecure TLS versions (like TLS 1.0), outdated ciphers, and certificates with insecure algorithms or key sizes (for example, RSA keys smaller than 2048 bits).
Missing Best Practices: Flag common misconfigurations such as missing HSTS headers and the use of untrusted or self-signed certificates.
Expiring and Expired Certificates: Easily surface certificates that are expired or expiring soon, helping you prevent costly outages.
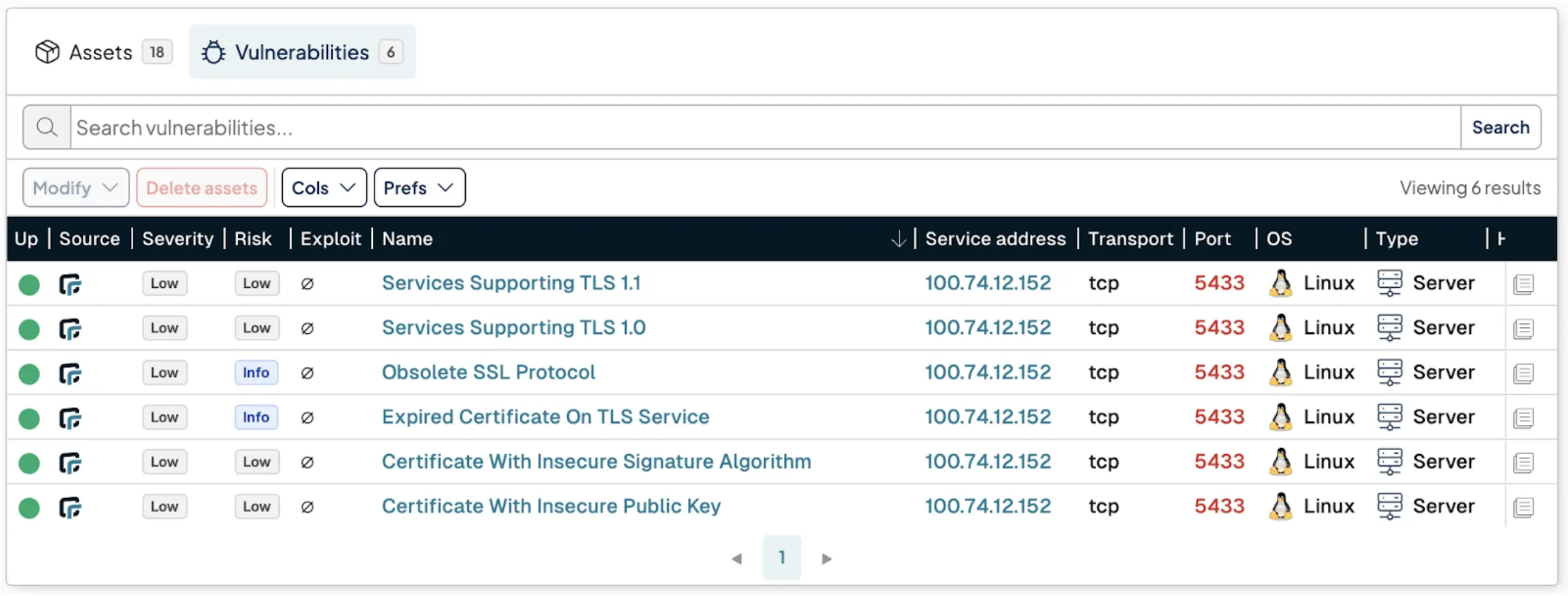
This expanded coverage ensures you can see where certificates are misconfigured or posing an immediate security risk, across both your external and internal environments.
Essential use-cases powered by certificates inventory #
runZero’s Certificate Inventory helps you address key initiatives and challenges, including:
1. Ensure certificates are automatically renewed #
The CA/Browser Forum's decision to reduce the maximum lifespan of public TLS certificates to just 47 days by 2029 makes manual certificate management impractical. Any environment where TLS certificates are deployed now needs automation to regularly renew certificates.
Identify long-lived certificates: Use runZero to quickly find certificates with long validity periods that will violate the new standard.
The CA/Browser Forum has a phased schedule for decreasing the max validity period (the amount of days an X.509 certificate can be issued for):
In 2025, the max validity period is currently 398 days.
On March 15, 2026, the max validity period will change to 200 days.
On March 15, 2027, the max validity period will change to 100 days.
On March 15, 2029, the max validity period will change to 47 days.
In anticipation of these dates, many Certificate Authorities are already issuing certificates for shorter validity periods when certificates are automatically renewed. You can use runZero to search for certificates with a longer validity period using the following Certificates Inventory query:
validity_period:>398dAutomate certificate renewals: By instantly showing you the assets where a certificate is installed, runZero provides the necessary context to help your teams set up automatic certificate renewal and find assets where this isn’t enabled.
2. Prevent costly outages #
Expired certificates can cause unexpected downtime. runZero helps you identify certificates that are expiring soon, even if those certificates are only deployed internally or deployed on non-standard services and ports.
Find expiring certs: Using runZero, you can instantly search for certificates set to expire soon. For example, the following Certificates Inventory query will find certificates that are either expired, or expiring in the next 14 days:
valid_until:<14dIf you want to ignore certs that have already expired, you can use the following query to find non-expired certificates that expire in the next 14 days:
valid_until:>=now AND valid_until:<14dPinpoint assets for remediation: When certificates with risk are discovered, runZero shows which devices and services are using the certificate, allowing your teams to quickly replace or renew the certificate and prevent service interruption.
3. Enforce security and compliance standards #
runZero makes it quick and easy to search for TLS service and certificate risks and misconfigurations, enabling you to meet compliance requirements.
Identify insecure TLS configurations: runZero has built in detections that inform you when an X.509 certificate or TLS service is misconfigured. To see certificates and TLS services with risks, search Certificate Inventory for:
has_vulnerability:trueFind untrusted certificates: Self-signed certificates are common in development and test environments, but sometimes make their way into internal production services. Unless specific self-signed certificates are trusted by a system administrator they can result in bad user practices such as bypassing browser protections. This can lead to man-in-the-middle and other attacks. To see self-signed certificates, search Certificate Inventory for:
self_signed:true AND is_ca:false4. Search certificates #
Finding certificates in your environment is effortless with Certificates Inventory. Certificates can be searched by nearly any X.509 attribute.
Find all certificates from a specific issuer: If you are consolidating certificates to a single provider, or looking for certificates that need to be upgraded to a different Certificate Authority, you can search certificates by issuer. For example, to find all certificates issued by DigiCert, search Certificates Inventory for:
issuer:digicertIf a Certificate Authority is compromised, or a Certificate Authority is being removed from browser trust stores, you can search for certificates by the issuer’s subject key identifier. For example, to find all certificates issued by the StartCom Class 1 DV CA, search Certificates Inventory for:
authority_key_id:="d7914e01c4b0bff8c86793449ce733faad930caf"Find certificates with a specific signature algorithm: A weak hashing algorithm increases the chances that an attacker can obtain a fraudulent certificate. Most browsers will not trust certificates signed using a weak algorithm. runZero will automatically create vulnerabilities for any certificates with weak signature algorithms attached to an asset. You can also search for these certificates directly by searching Certificates Inventory for:
signature_algorithm:="md5WithRSAEncryption" OR signature_algorithm:="sha1WithRSAEncryption"Find certificates issued for specific domains: Sometimes you just need to find every certificate issued for a specific domain to help track down specific assets. runZero allows searching across the common name and subject alternative names of a certificate using the name attribute. For example, to find all certificates issued for localhost search Certificate Inventory for:
name:localhost5. Identify all services using a wildcard cert #
Wildcard certificates are useful when securing many different virtual hosts and domain names. But it can be easy to lose track of every place a wildcard certificate is installed. With runZero you can easily pinpoint every asset where a wildcard cert is installed, even if you don’t know all of the virtual hosts associated with the certificate.
To find wildcard certificates, search Certificate Inventory for:
subject:"CN=*"Then click into a certificate you are interested in, and look at the Assets data table to see where the certificate is installed.
Or to find all assets with wildcard certificates, search Asset Inventory for:
certificate_subject:"CN=*"Get started today #
The health and security of external and internal TLS services is important to maintaining secure communications and security posture. The updated Certificates Inventory is available today in the Inventory → Certificates section of runZero. Certificates can be searched directly using a variety of certificate search keywords.
Whether you're preparing for the new 47-day certificate lifespan, hunting for insecure TLS services, or just trying to get a complete view of your machine identities, the runZero Certificates Inventory is an essential tool for seeing and securing every certificate in your environment.
















