The CISA KEV Catalog updates throughout the week. CVSS scores shift. EPSS probabilities fluctuate. Exploit code appears and evolves. But so many vulnerability workflows treat all this movement like background noise, something to acknowledge but not really use.
That's the gap our new tool, KEV Collider, fills. This is our daily-updated web application that lets you layer signals, test filters, and watch how different risk indicators interact across the catalog in real time. No installation. No credentials. Just open it and start experimenting.
What you can actually do with it #
The KEV Collider is designed to help you figure out what’s most important for your organization and your team by making the data interrogatable. Here's what that looks like in practice.
Filter for your infrastructure #
Every environment has its own risk profile. Maybe you care about network-accessible vulnerabilities that require no user interaction. Or maybe you need to identify everything Microsoft released on Patch Tuesday that's since appeared on the KEV.
KEV Collider allows you to filter across:
CVSS metrics: Attack vector, privileges required, user interaction, impact scores
KEV metadata: Date added, date due, vendor, product, ransomware usage
EPSS signals: Current probability, trending direction, magnitude of change
Exploit availability: Public “commodity” exploits vs targeted, private exploitation
Want to see only straight-shot remote code execution vulnerabilities? There's a preset for that. Need to track EPSS vulnerabilities where exploitation probability is actively shifting? Filter for it.
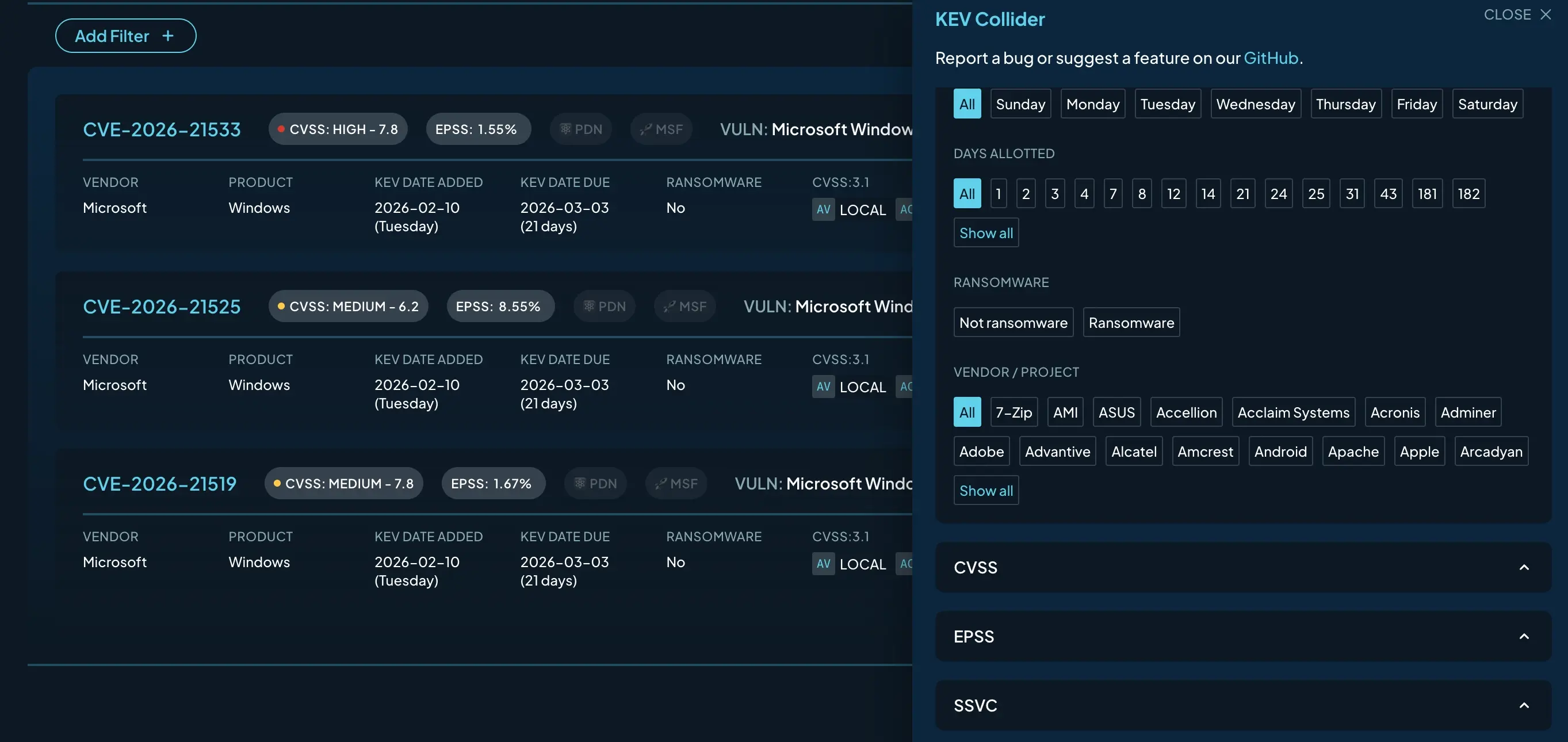
Test signal combinations, not just individual scores #
One of the KEV Collider's core design principles is that single metrics don't tell the whole story. A high CVSS score without active exploitation is different from a moderate score that's trending on EPSS. A KEV entry added last month behaves differently than one added this week, even if both have the same due date.
The tool makes these combinations visible. For example, maybe you want to look at just Microsoft vulnerabilities, cross-referenced against reported ransomware campaign usage, and really only those rated as a CVSS “High” or worse, then sort what’s left by the KEV due date rather than the KEV add date. Here’s a sample filter for just that, all through the magic of HTTP GET parameters. The goal is to surface patterns that only emerge when you look at multiple signals together.
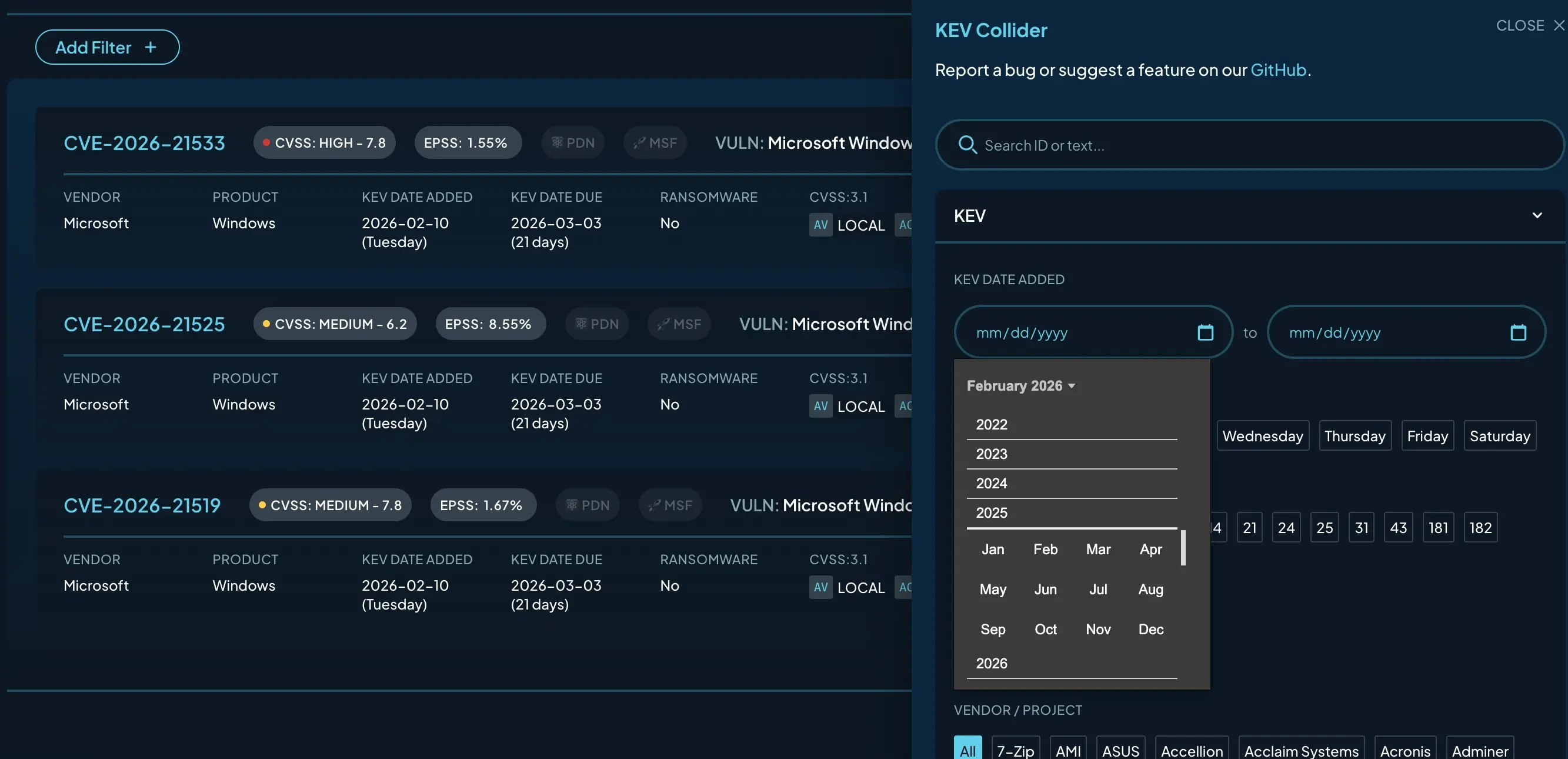
Understand timing #
When a vulnerability appears on the KEV matters as much as whether it appears at all. The KEV Collider tracks:
Date added to the KEV
Date due under BOD 22-01
Day of the week it was added (useful for spotting Patch Tuesdays or unusual Friday to Sunday additions)
EPSS momentum: whether exploitation probability is increasing, decreasing, or stable, as of today.
This temporal context helps distinguish between commoditized mass exploitation and newly emerging threats. A vulnerability added to the KEV three months ago with stable EPSS tells a different operational story than one added yesterday with a sharp EPSS spike.
Three ways to start using KEV Collider today #
1. Run the presets, then modify them #
Start with one of the built-in presets and see what they return. Then adjust the filters to reflect your own priorities. The presets are hypothesis starters, not final answers.
2. Compare vendor behavior #
Filter by specific vendors and watch how their KEV entries cluster. Do certain vendors show up disproportionately on particular days? Do their vulnerabilities trend differently on EPSS? These patterns can inform patching cadence and vendor risk assessments.
3. Test your assumptions #
Think high CVSS scores correlate perfectly with KEV urgency? Filter for CVSS 9+ and sort by date due. Believe all network-accessible RCE is equally critical? Layer in EPSS to see which ones are actually being exploited at scale. The tool is designed to challenge conventional wisdom by letting you measure it.
Built to help empower defenders like you #
The KEV Collider is a community resource. It's hosted by runZero, updated daily, and built entirely on open-source data. There's no paywall, no required sign-up, and no attempt to prescribe priorities. We're releasing it because defenders need tools that support thoughtful, repeatable reasoning, not just checkbox coverage.
Compliance-driven patching treats every KEV entry the same because regulations can't accommodate nuance. But operational security requires exactly that: distinguishing signal from noise, urgency from ceremony, and real risk from theoretical possibility.
Where it fits in your workflow #
The KEV Collider doesn't replace your vulnerability management platform or patching process. It's a layer above those tools, offering a place to validate assumptions, explore signal combinations, and test prioritization hypotheses before translating them into operational decisions.
Use KEV Collider to: #
Audit whether your current patching priorities align with actual threat behavior
Identify blind spots in your vulnerability triage process
Build evidence-based arguments for resource allocation
Train your team to think critically about risk signals instead of treating scores as gospel
The CISA KEV is an operational signal, not a static list. The KEV Collider treats it that way.
Get started #
Explore the KEV Collider. For the research foundation behind it, read our new KEVology report. And if you want to see how KEV entries map to your actual asset inventory, try runZero for free.
















