There is a truth every security pro knows in their gut, even if they don’t like to say it out loud: the attacker will get in.
Maybe it’s a clever phish. Maybe it’s a zero-day exploit. Whatever the vector, the reality is, perimeter defense is no longer about building an impenetrable fortress. It’s about accepting the inevitability of a breach and being prepared for the real fight, which starts after the initial compromise.
Once an adversary has a foothold inside your network, their goal isn’t to hang out on a single compromised laptop. It’s to move, explore, and escalate. They’re hunting for the pathways — the forgotten servers, the weak credentials, the misconfigured services — that let them move laterally, gain privileges, and get to the crown jewels. This is how a minor incident spirals into a catastrophic ransomware event or a massive data breach.
The game has changed. The winning strategy is all about making your internal network an absolute nightmare for an attacker to navigate. It’s about building internal resilience. And that starts with seeing your network for what it really is.
The attacker’s playground: Your internal network #
Modern networks are a tangled mess of on-premise servers, cloud containers, remote devices, and a sprawling universe of OT and IoT gear. This complexity is a gift to attackers. They thrive in the blind spots created by traditional security tools, which often can’t see unmanaged devices or shadow IT assets.
The runZero research team found that on average 60% of the attack surface contains devices with limited to no visibility.
This is where the "assume breach" mindset becomes critical. Data shows that only ~20% of initial compromises are traced back to a known CVE. The other 80%? It’s phishing, stolen credentials, and the exploitation of simple misconfigurations. Attackers aren't just looking for a bug in your software; they're looking for an open door in your architecture.
Once they’re past the perimeter, they leverage your own infrastructure against you. Here’s how to start locking those doors.
Hardening the Pathways: A Practical Guide #
The secret to containing a breach is to proactively find and fix the internal exposures that fuel lateral movement. You must clean up your network before an incident forces you to.
1. Lock down file servers and backups #
File shares and backup repositories are high-value targets. An attacker who lands on a desktop can quickly pivot to nearby storage, leading to data destruction or exfiltration.
runZero lets you hunt down these common weaknesses with precision:
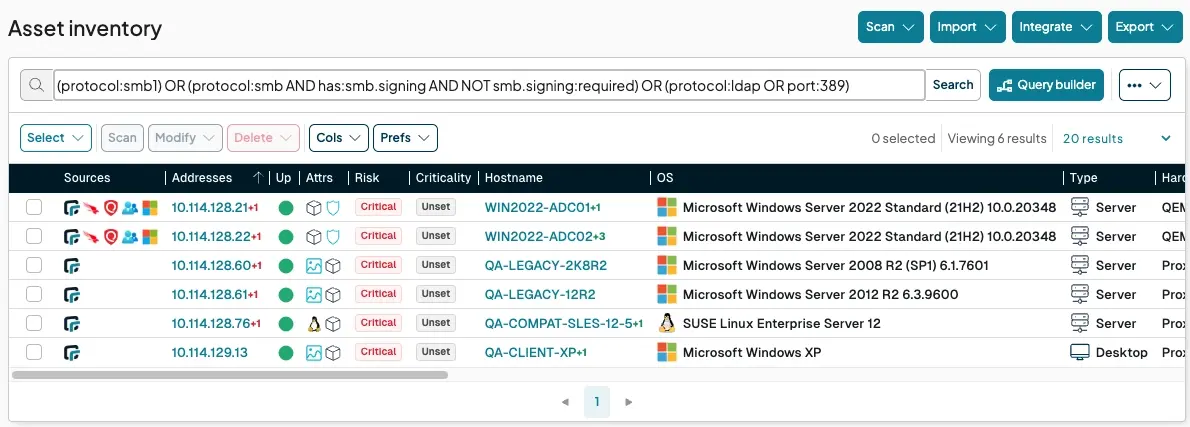
Find legacy file-sharing protocols: The ancient SMBv1 protocol is notoriously insecure. Find every last instance with a simple query:
protocol:smb1Enforce SMB Signing: When SMB signing isn’t required, an attacker can perform man-in-the-middle attacks to steal credentials. Find this misconfiguration before they do:
protocol:smb AND has:smb.signing AND NOT smb.signing:requiredEliminate cleartext protocols: Services like unencrypted LDAP transmit credentials in the open, making them easy for an attacker to sniff from the network:
protocol:ldap OR port:389
2. Secure your vulnerable databases #
Databases often hold the most sensitive data, yet they are frequently left wide open to anyone already on the internal network. A low-level compromise can become a massive data breach in minutes.
With runZero, you can find these ticking time bombs:
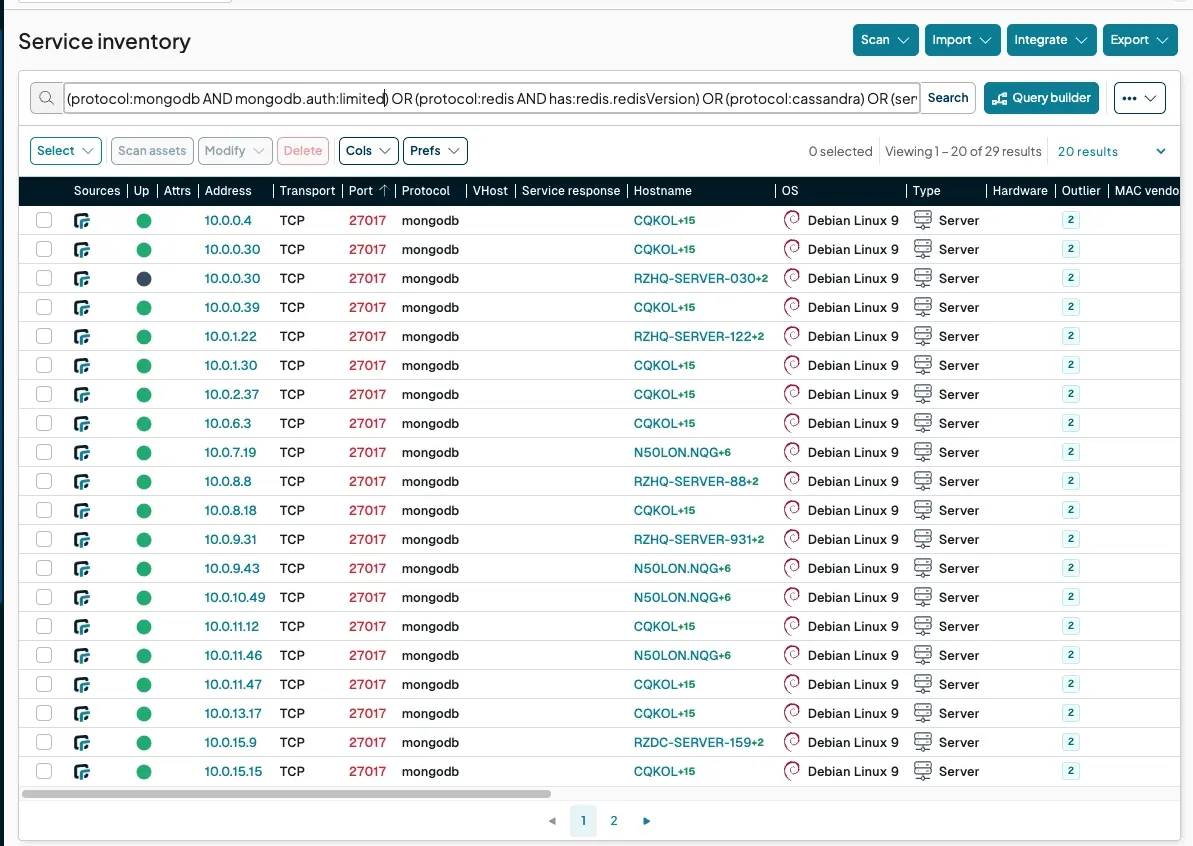
Discover unauthenticated databases: Find NoSQL and key-value stores that are completely open to internal connections.
MongoDB:
protocol:mongodb AND mongodb.auth:openRedis:
protocol:redis AND has:redis.redisVersionCassandra:
protocol:cassandra
Find exposed config servers: Critical services like ZooKeeper or Consul should never be exposed to the public:
internet.service_has_public:t AND ( _asset.protocols:zookeeper OR _asset.protocols:etcd2 OR _asset.protocols:consul )
3. Fortify Active Directory #
For most attackers, Active Directory is the ultimate prize. Gaining control of AD means gaining control of the kingdom. They’ll use credentials from a phished user to poke and prod for common policy weaknesses.
runZero helps you find and fix AD misconfigurations:
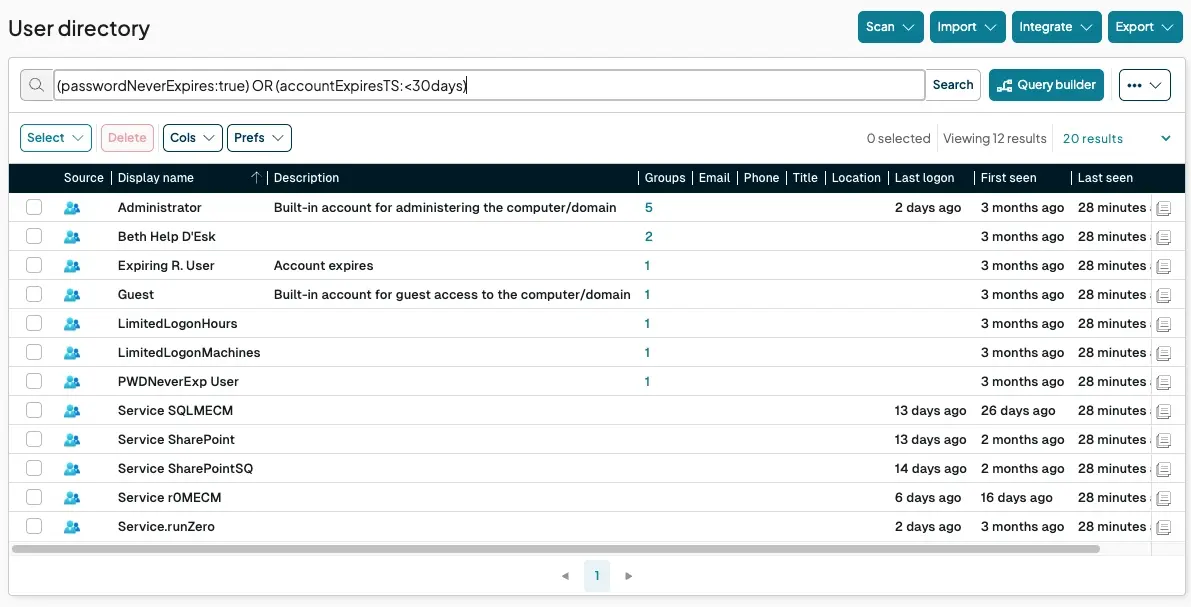
Find non-expiring passwords: Accounts with passwords that never expire are static targets for credential theft:
passwordNeverExpires:trueIdentify soon-to-expire accounts: This can be a sign of poor de-provisioning hygiene for temporary or contractor:
accounts.accountExpiresTS:<30days
4. Harden exposed web apps and API servers #
Your internal network is filled with web applications — from official software to forgotten admin panels. These often have outdated software or, even better for an attacker, default credentials. runZero’s integration with the Nuclei scanner safely checks for these flaws.
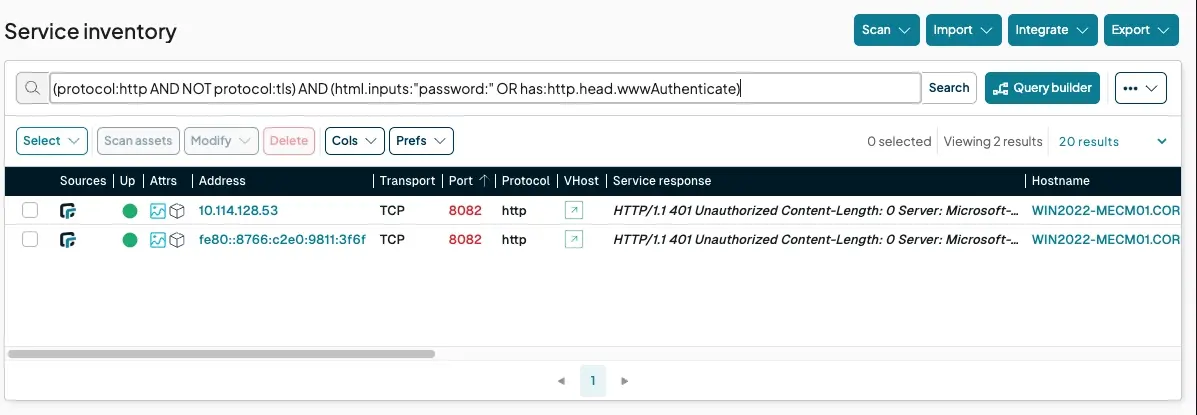
Find unencrypted login forms: Sending passwords over HTTP is a cardinal sin. Find every service doing it:
(_asset.protocol:http AND not _asset.protocol:tls) AND ( html.inputs:"password:" OR has:http.head.wwwAuthenticate )Detecting default credentials: We’ve curated a set of safe Nuclei templates to find default logins on dozens of common applications, including Jenkins, SolarWinds, and Apache Tomcat.
5. Control remote management and support servers #
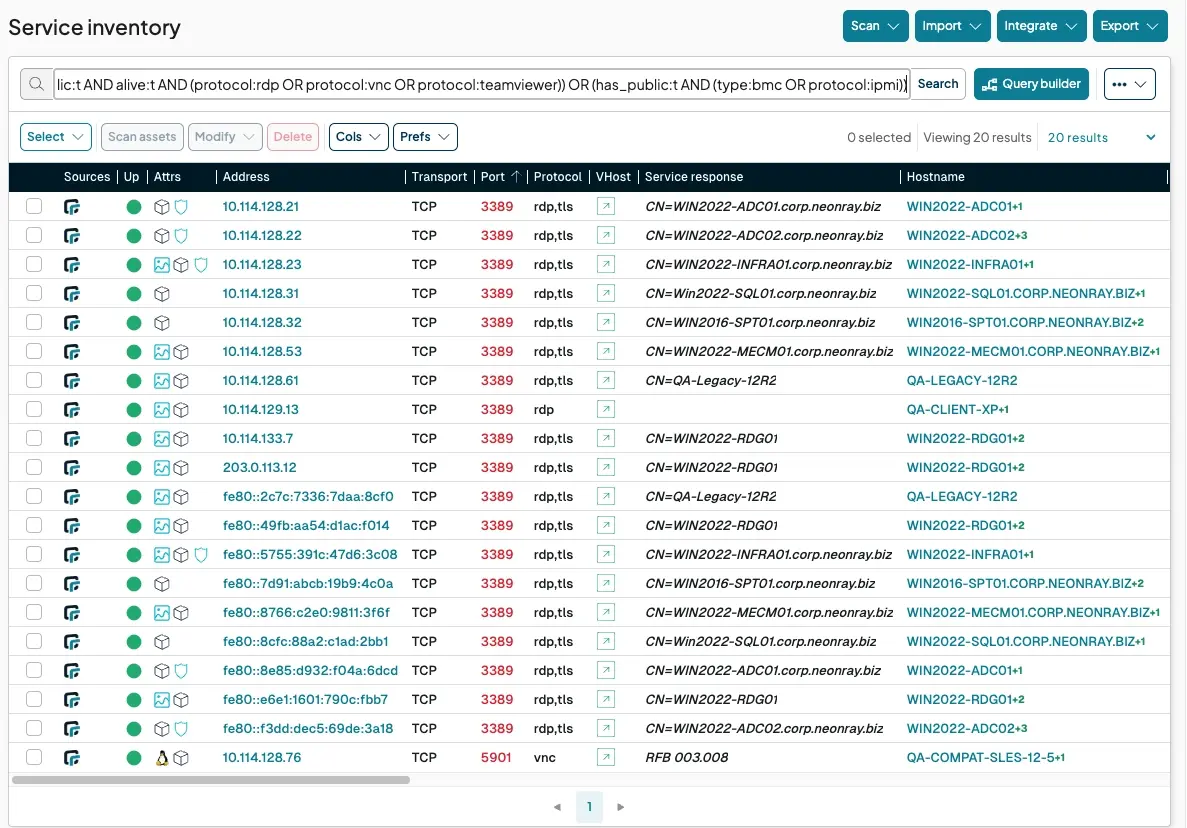
Remote access tools like RDP and VNC are essential for admins, but they’re also juicy targets for attackers seeking persistent, privileged access. Even more critical are Baseboard Management Controllers (BMCs) like iDRAC and IPMI, which give an attacker complete hardware-level control, bypassing the host OS entirely.
Find all remote access protocols: Get a full inventory of RDP, VNC, TeamViewer, and more:
protocol:rdp OR protocol:vnc OR protocol:teamviewerPrioritize publicly exposed remote access: Any remote access service facing the internet needs to be your top priority:
has_public:t AND alive:t AND (protocol:rdp OR protocol:vnc OR protocol:teamviewer)Locate exposed BMCs: These out-of-band management devices are incredibly powerful and should never be publicly accessible:
has_public:t AND (type:bmc OR protocol:ipmi)
From contained inconvenience to catastrophe #
Adopting an "assume breach" mindset means shifting the fight to where it matters most. Attackers count on defenders being overwhelmed and blind to the realities of their own networks.
By focusing on proactively remediating these common, exploitable internal exposures, you fundamentally change the game. You turn a successful phish from the start of a disaster into a contained, manageable incident. With comprehensive visibility, you can see your network through an attacker’s eyes and build a resilient environment that stops them in their tracks.
Ready to see what’s really lurking on your network? Try runZero for free.
















