End-of-life (EOL) operating systems don’t just fade away. They linger in enterprise networks like the undead — unchanging, unpatched, and increasingly easy for attackers to exploit.
In our new research paper, "Undead by design: Benchmarking end-of-life operating systems", the runZero research team analyzed millions of assets across hundreds of U.S. enterprises. The findings reveal that EOL assets are more prevalent (and more dangerous) than many organizations realize. And with the looming October 14 Windows 10 deadline, the stakes are about to rise sharply.
The state of the undead #
Across all enterprises studied 8.56% of assets are running an EOL OS, which means they don’t get the usual level of feature work and bug fixes. More concerning are the 5% are already beyond extended support, which means they miss out on even critical security patches.
Certain industries like retail, machinery and electronics manufacturing carry above-average concentrations of these “undead” systems. And in sectors like healthcare and social services, where legacy applications are tied to patient care, unsupported OSes present direct risks to safety.
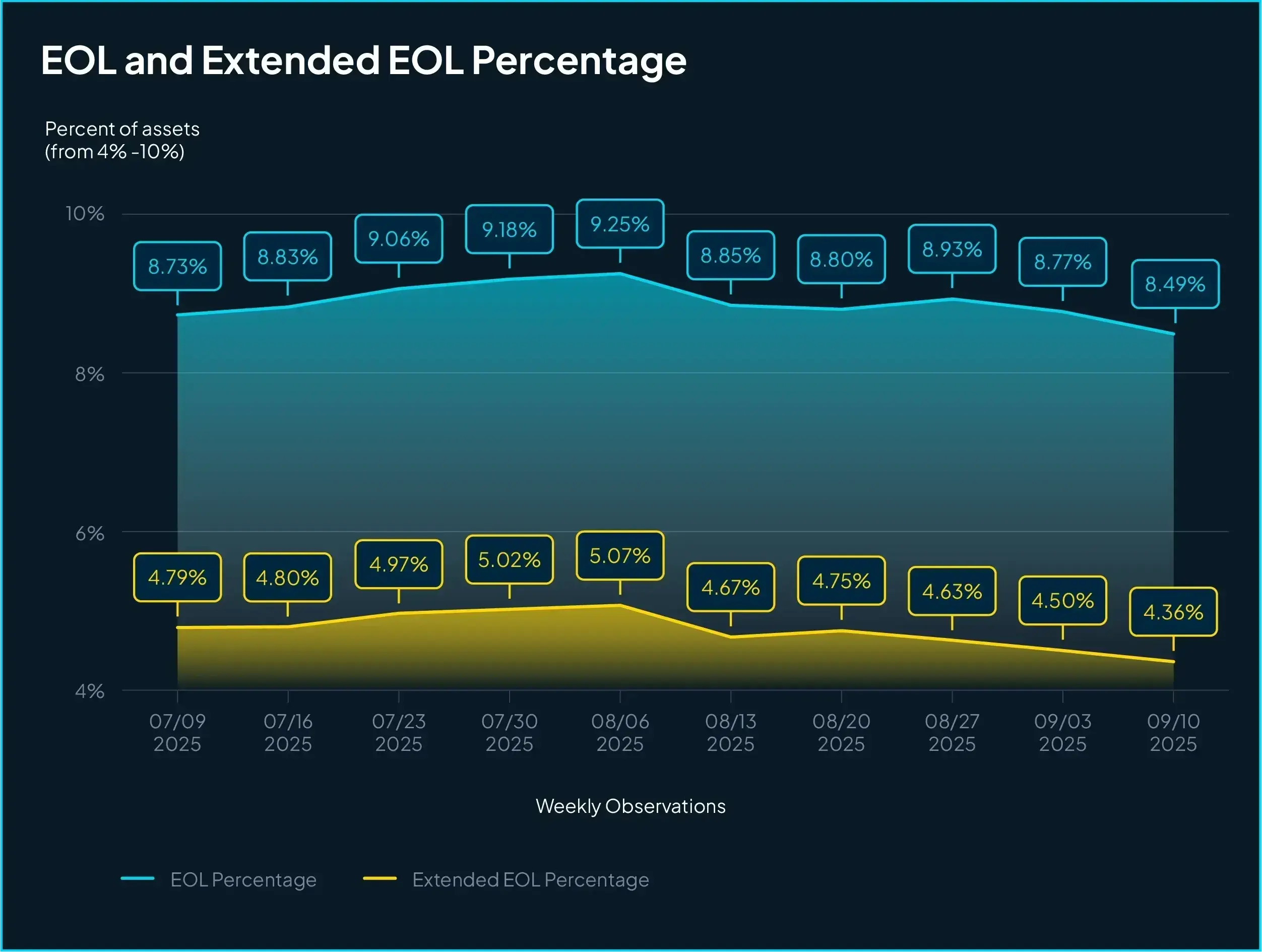
The coming Winpocalypse #
The challenges of managing EOL systems aren’t distributed evenly. Some industries already face outsized concentrations of unsupported assets. But even organizations that feel “average” today are about to see a dramatic shift.
On October 14, 2025, Windows 10 reaches end of its life. That means:
Roughly one-third of enterprise Windows assets will lose support
The overall enterprise-wide EOL population will triple — from 5% to ~16%
Healthcare and social services will see the steepest exposure increases
Despite years of warnings, many organizations remain tied to Windows 10 and earlier dependencies. What happens when millions of suddenly unpatchable systems remain critical to business operations?
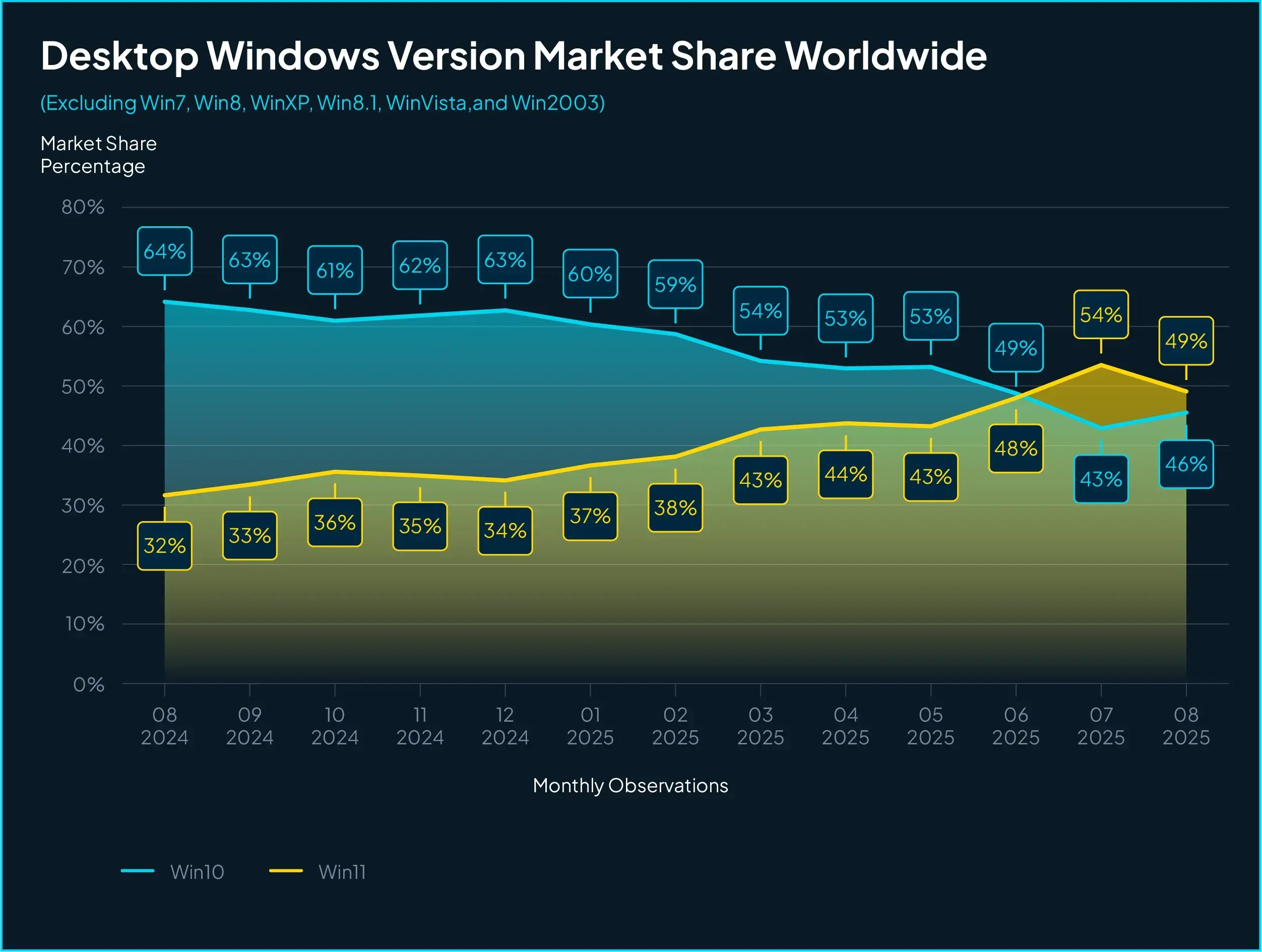
Why Windopocalypse matters #
The situation with Windows 10 is certainly dramatic, and Microsoft continues to update guidance and offer post-EOL solutions for home and enterprise users, for a price. But failing any special action, those millions of machines will not be serviceable beyond October.
Unsupported OSes are more than compliance headaches. They reshape the attack surface:
Patchless: unprotected against new exploits
Easily fingerprinted: stand out in reconnaissance scans
Signal neglect: suggest weak IT hygiene, emboldening attackers
Unsupported software in critical infrastructure is dangerous and elevates national security, economic, and public health risks.
How defenders can respond #
There’s no magic fix, but defenders can start reducing exposure today:
Get visibility: Identify where EOL assets sit across IT, OT, and cloud.
Segment and isolate: Contain them while planning migrations.
Pressure vendors: Push for updated versions of apps that force reliance on outdated OSes.
Advocate for budget: Use data to frame the business risk, especially if your network has outsized exposure against your industry’s average.
Want to see where your own risks lie? #
runZero customers can shine a light on soon-to-expire systems with a simple Asset Inventory query:
os_eol_extended:>0 AND os_eol_extended:<60daysThis returns all devices that are, or will be, EOL in the next 60 days. Note the >0 syntax—0 means "no EOL known," so this ensures you’re capturing only assets with a defined EOL date since the beginning of time (which of course started January 1, 1970).
Step inside the morgue #
The risks tied to end-of-life operating systems are measurable, industry-specific, and about to get much worse as Windows 10 goes dark. The good news is you don’t have to navigate the Winpocalypse blind. Read the full report, “Undead by design: Benchmarking end-of-life operating systems”, to get the full picture. See how your industry stacks up, where the biggest concentrations of unsupported systems lurk, and what the numbers really mean for defenders.
















