Latest Control Web Panel (CWP) vulnerability: CVE-2025-48703 #
Security researcher Maxime Rinaudo reported an authentication bypass and OS command injection vulnerability in certain versions of CWP (Control Web Panel). This flaw, caused by improperly sanitized user input, exists within the file management feature, specifically in the component responsible for changing file permissions.
Successful exploitation allows a remote, unauthenticated adversary, who knows a valid non-root CWP username, to inject arbitrary OS commands. This attack is performed by sending a changePerm request containing shell metacharacters in the t_total parameter. This vulnerability has been designated CVE-2025-48703 and has been rated critical with a CVSS score of 9.0. There is evidence that this vulnerability is being actively exploited in the wild.
The following versions are affected
- CWP versions prior to 0.9.8.1205
What is CWP (Control Web Panel)? #
CWP (Control Web Panel), formerly CentOS Web Panel, is a free web hosting control panel that provides a graphical interface to simplify the management of Linux servers, websites, and user accounts.
What is the impact? #
Successful exploitation of the vulnerability would allow an adversary to execute arbitrary commands on the vulnerable host, potentially leading to complete system compromise.
Are updates or workarounds available? #
Users are encouraged to update to the latest version as quickly as possible:
- CWP upgrade to version 0.9.8.1205 or later
How to find potentially vulnerable systems with runZero #
From the Software Inventory, use the following query to locate potentially impacted assets:
vendor:="CentOS WebPanel" product:="CentOS Web Panel"
Please note that although the older product name is used in the query, the underlying match logic is valid for the latest product name.
January 2022: CVE-2021-45466, CVE-2021-45467 #
Security researcher Paulos Yibelo shared findings this week on two new vulnerabilities within the popular Control Web Panel (formerly CentOS Web Panel) web hosting management software. Both CVE-2021-45466 (a file write vulnerability) and CVE-2021-45467 (a file inclusion vulnerability) are interesting individually, but they provide a powerful attack vector when chained together to achieve pre-authentication remote code execution (RCE) on a vulnerable target. Taking into account the 200k+ unique, public-facing servers currently running CWP, there could be many systems at risk of exploitation.
The maintainers of CWP have patched CVE-2021-45467 in the most recent release (v0.9.8.1122), with the guidance for administrators of CWP installations to upgrade to this version as soon as possible. No interim mitigation strategies have been shared.
How to find Control Web Panel (CWP) instances with runZero #
From the Asset Inventory, use the following pre-built query to locate potentially vulnerable Control Web Panel instances within your network:
service.product:"CentOS Web Panel"
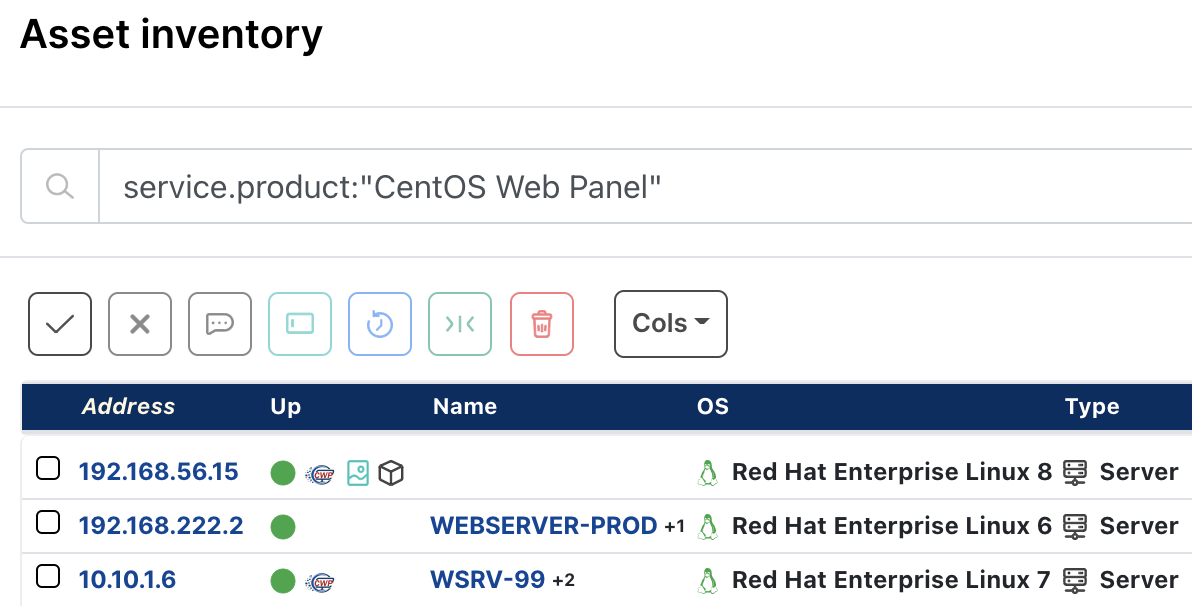
Please note that though the older product name is used in the query, the underlying match logic is using the web server value found in HTTP header responses from the CWP server, which has remained the same across the product name change.
As always, any prebuilt queries we create are available from our Queries Library. Check out the library for other useful inventory queries.

















