On February 5th, 2026 the Cybersecurity and Infrastructure Security Agency (CISA) published Binding Operational Directive BOD 26-02: Mitigating Risk From End-of-Support Edge Devices directing agencies to update or remove End-of-Support (EOS) Edge devices.
For context, a Binding Operational Directive (BOD) is a “compulsory direction to federal, executive branch, departments and agencies for purposes of safeguarding federal information and information systems.” 1 While BODs do not apply to certain agencies whose systems are classified as national security systems (NSS), they do apply to all federal civilian executive branch agencies.
What is BOD 26-02? #
BOD 26-02 mandates a two-year program requiring all affected agencies to identify and address unsupported edge devices, effective February 5, 2026.
All federal agencies under CISA’s authorities must immediately update all supported edge devices.
In three months (May 5, 2026), federal agencies must identify those devices in production listed on the “CISA EOS Edge Device List.” These agencies must also have a mechanism in place to identify all supported and unsupported edge devices in production, regardless of CISA’s list.
In a year (Feb 5, 2027), all devices on CISA’s list of unsupported devices should be updated or replaced by all federal agencies.
In 18 months (August 5, 2027), all unsupported edge devices must be updated or replaced by all federal agencies, regardless if they’re on CISA’s list or not.
In two years (Feb 5, 2028), all federal agencies must have a continuous mechanism to identify all edge devices, and ensure that only supported devices are in production.
While BOD 26-02 specifically calls out the risk of having EOS edge devices on a network, CISA states that “EOS devices should not reside anywhere on federal networks.” Here at runZero, we couldn’t agree more! But, for the purposes of BOD 26-02, “edge devices” are often, but not limited to, devices such as firewalls, switches, routers, load-balancers, proxies, reverse proxies, VPN gateways, or combinations thereof. Interestingly, security vendors products whose devices often live at the edge were the most frequently exploited devices in 2024. Unsupported devices, no matter where they exist in an organization, pose a significant risk to organizations.
We go into this in some depth in our recent report, "Undead by Design, Benchmarking end-of-life operating systems," where we concentrate specifically on operating systems and their prevalence across industry sectors, and more importantly, why unsupported systems linger for so long in production.
BOD 26-02 compliance challenges #
When it comes detecting and discovering unsupported edge devices, two main challenges arise almost immediately:
Accurate discovery and fingerprinting of EOS devices
Defining the Edge
The first challenge, accurate discovery and fingerprinting of EOS devices, has been traditionally solved via manually managed Excel spreadsheets, IPAM, or not at all. That is to say, having and maintaining an accurate and up to date asset inventory has traditionally been a collection of disjointed systems, programs, or procedures, leading to an incomplete and inaccurate list of what's on the network, starting from the moment that list is produced. This spotty and laggy coverage makes it difficult to impossible to identify with accuracy anything on the network, let alone unsupported devices.
This takes us to our second challenge of defining the edge. Oftentimes, organizations think they know where their perimeter lies, but shadow IT, network misconfigurations, and wandering “bring your own devices” (BYODs) all can extend the perimeter beyond what was known. This exposure of unknown devices, supported or otherwise, represents a real risk to agencies that are often under constant attack from adversaries looking to steal, disrupt, or destroy US infrastructure.
How runZero supports BOD 26-02 #
Accurately and expediently discovering assets can be a daunting task, especially if you don't know where to start. runZero can help agencies discover all of their assets, validate the edge, and identify EOL and EOS devices, before the adversaries do. With runZero, agencies can:
1. Discover all assets #
Through novel unauthenticated active scanning, passive discovery, and API integrations, runZero can identify, fingerprint, and report on your entire systems risk and exposure, including aging, unmaintained, and forgotten EOS devices.
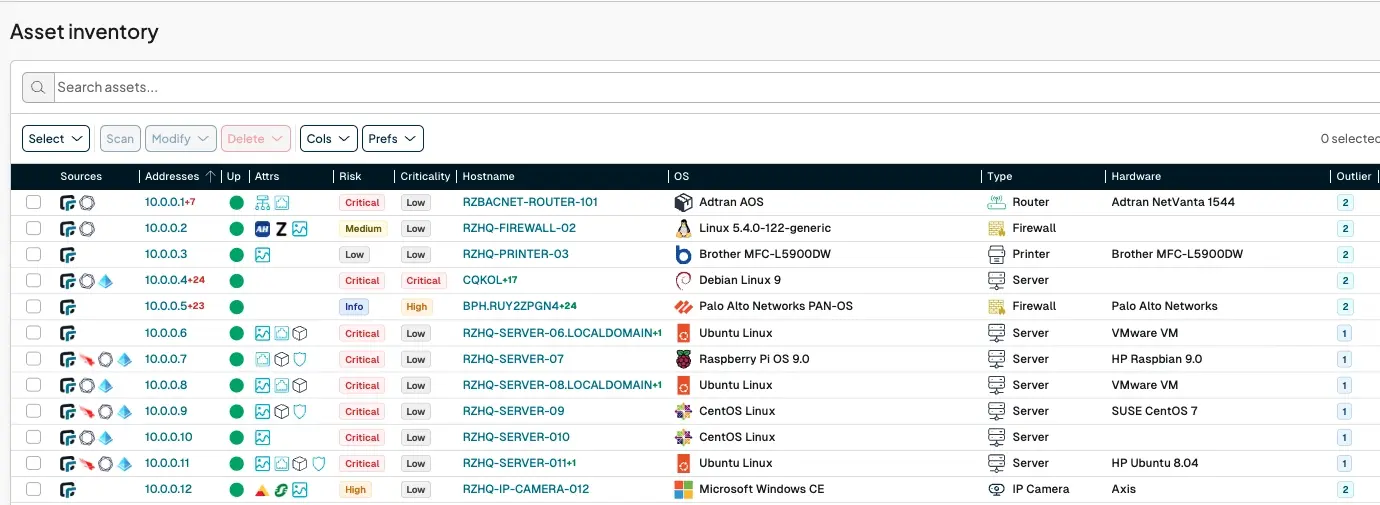
2. Identify all edge assets (supported or otherwise) #
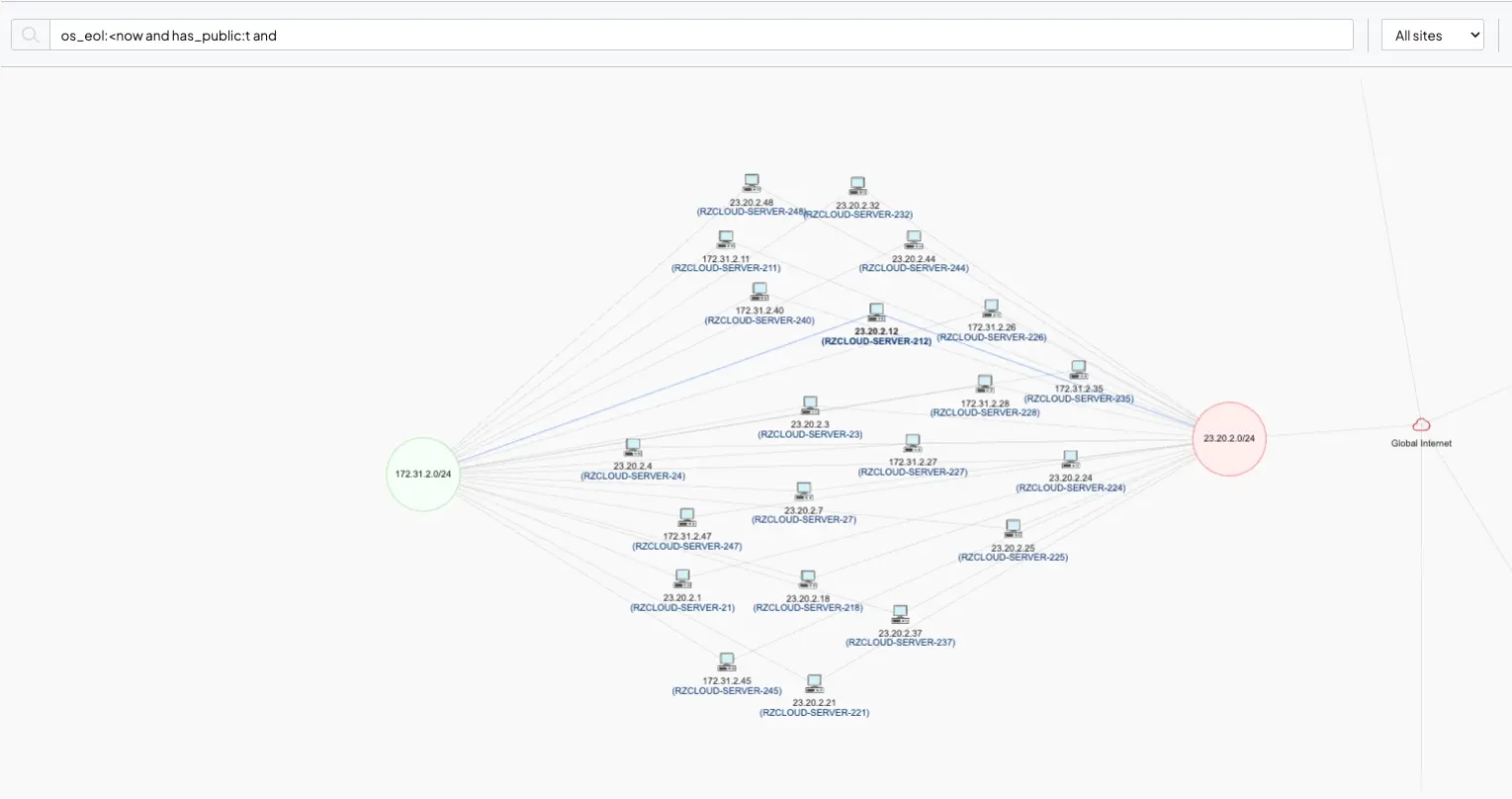
runZero can scan both internally and externally, providing agencies a comprehensive view of the internal and external attack surfaces. Utilizing native reporting, agencies can validate their edge devices, including EOS devices.
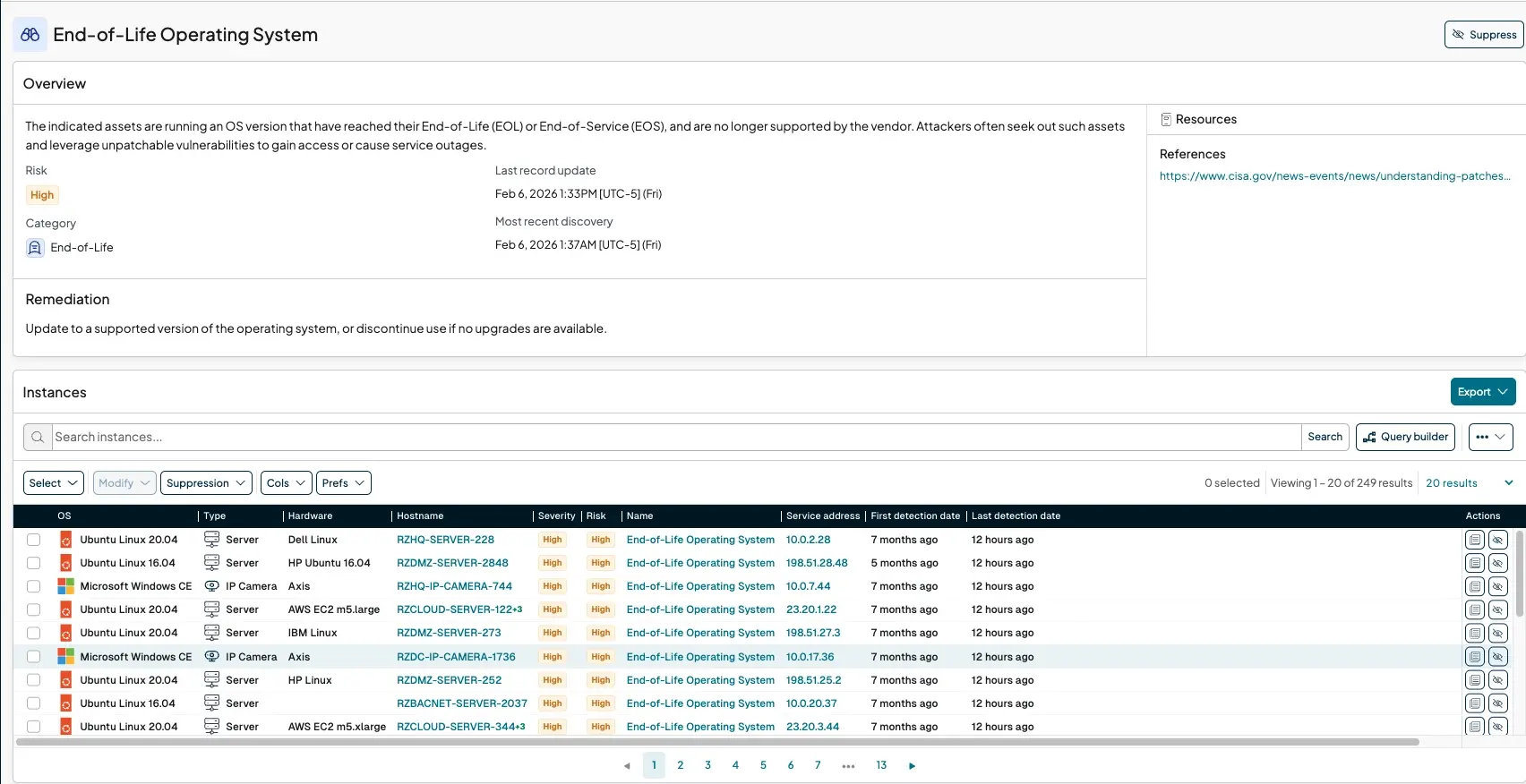
3. Native EOL asset discovery #
runZero includes native alerting capabilities when EOL devices are discovered:' or 'runZero includes a native alerting capability when EOL devices are discovered:
If there are devices that runZero cannot track support for, Government off-the-shelf (GOTS) or classified devices for example, custom queries allow agencies to build and track their own inventories:
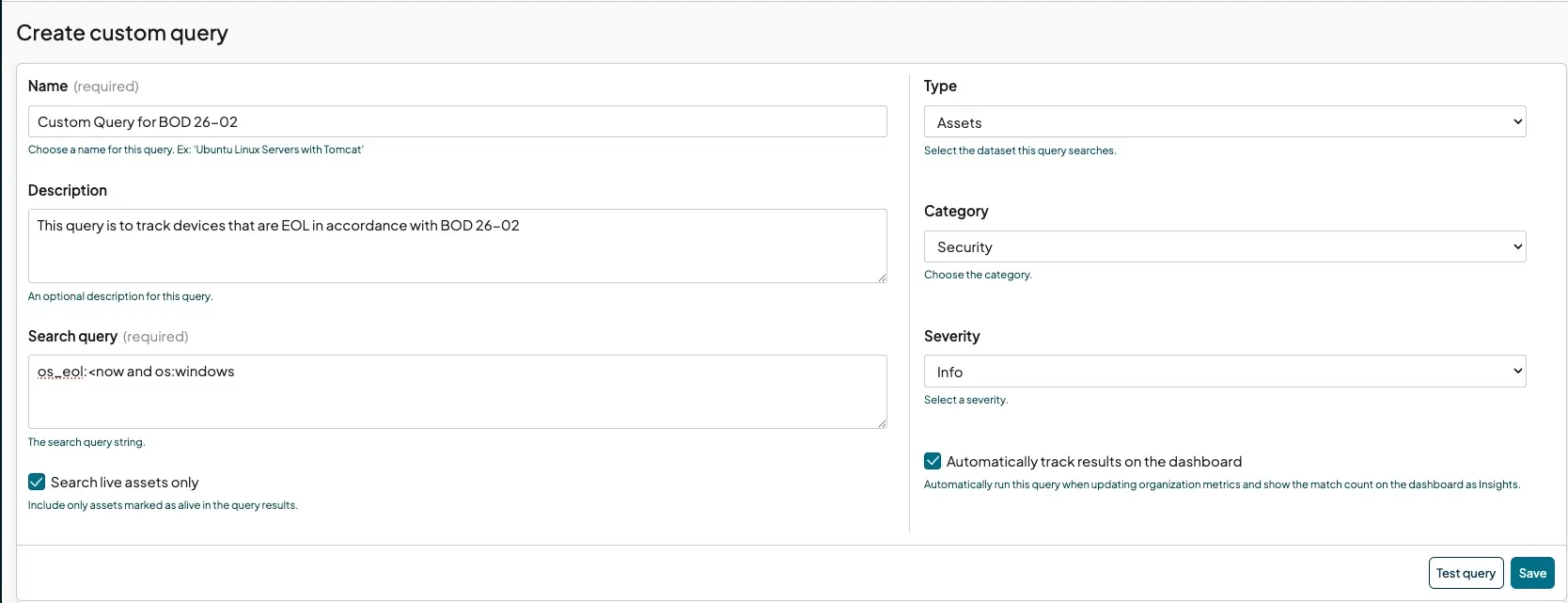
These queries can then be tracked on a simple dashboard, allowing for easy access to offending assets.
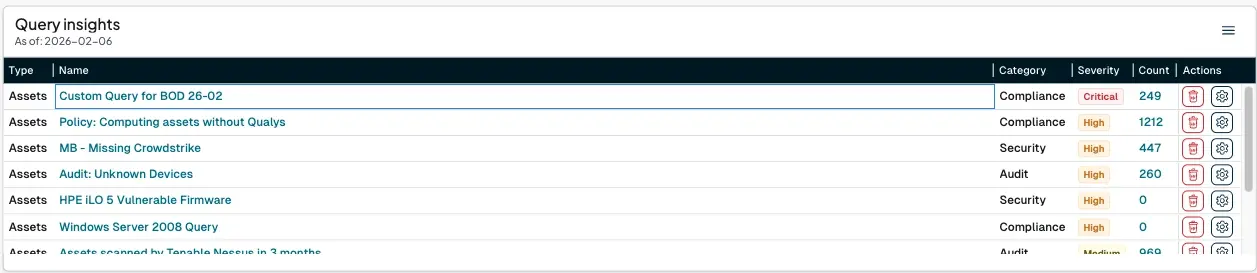
4. Goals for tracking #
runZero queries can also be used to build custom Goals, so progress can be tracked toward BOD compliance.
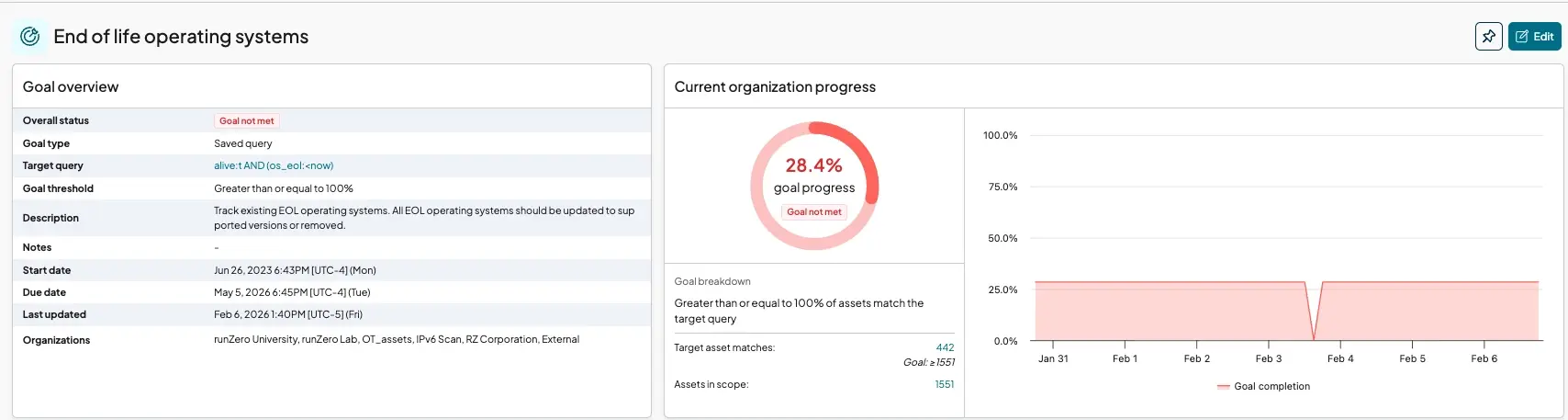
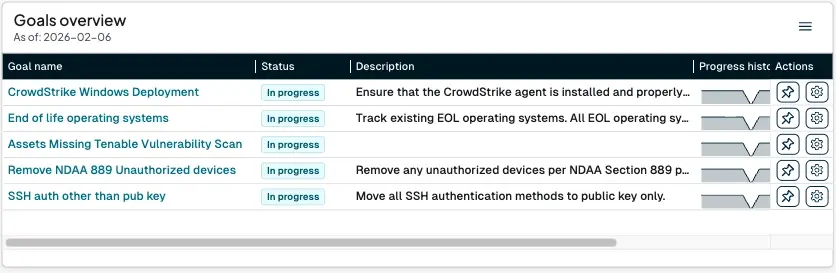
What’s next for your BOD 26-02 strategy #
runZero’s unparalleled asset discovery and fingerprinting can empower agencies to expeditiously discover and maintain an asset inventory for their entire systems. Even more immediately, runZero can help agencies accomplish the requirements of BOD 26-02 before the milestones laid out by CISA.
Start a free trial in minutes or book a demo for a guided tour.

















