From the creation of the Australian Cyber Security Centre in 2014 to the publication of its first national Cyber Security Strategy in 2016, the Australian Government has been at the forefront of nationstate cyber security for many years. In 2018, the Australian Government passed the Security of Critical Infrastructure (SOCI) Act 2018 to protect critical infrastructure in the electricity, gas, water and maritime port sectors. Additional legislation has since been passed in 2021, 2022 and 2023 to both broaden and strengthen the SOCI Act.
Despite these efforts, the Minister of Home Affairs felt that Australia was falling behind on cyber security following a series of breaches in 2022 and 2023 that impacted millions of Australian citizens. This led to the publication of the Australian Government's 2023-2030 Cyber Security Strategy (the Strategy), which is being implemented with the vision of becoming a world leader in cyber security by 2030.
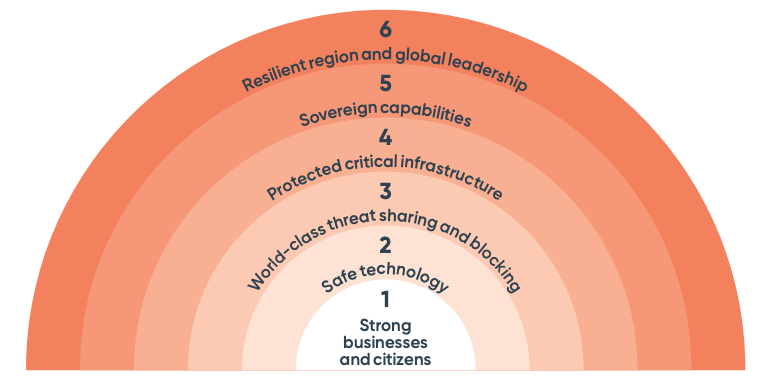
The 6 Cyber Shields #
To achieve its vision, the Strategy introduces 20 initiatives grouped into six Cyber Shields:
Shield 1: Strong Business & Citizens ensures that Australia's citizens and businesses are better protected from cyber threats and possess the ability to recover quickly following a cyber attack.
Shield 2: Safe Technology focuses on ensuring Australians can trust that their digital products and services are safe, secure, and fit for purpose.
Shield 3: World-Class Threat Sharing & Blocking means that Australia will have access to real-time threat data and the capacity to block threats at scale.
Shield 4: Protected Critical Infrastructure aims for Australia's critical infrastructure and essential government systems to be able to withstand and bounce back quickly from cyber attacks.
Shield 5: Sovereign Capabilities strives for Australia to achieve a flourishing cyber industry, enabled by a diverse and professional cyber workforce.
Shield 6: Resilient Region & Global Leadership works to ensure Australia's region is more cyber resilient and benefits from the digital economy, while Australia upholds international law and norms and shapes global rules and standards consistent with shared interests.
The timeline of implementing the Strategy over a seven-year period is structured across three distinct horizons to ensure phased work and ongoing collaboration between the Government and industry to uplift national cyber maturity.
The three phases of implementation are:
Horizon 1 (2023-2025): Strengthening Foundations. This initial phase focuses on addressing critical gaps in Australia's cyber shields.
Horizon 2 (2026-2028): Scaling Cyber Maturity. We will scale cyber maturity across the whole economy. We will make further investments in the broader cyber ecosystem, continuing to scale up our cyber industry and grow a diverse cyber workforce.
Horizon 3 (2029-2030): Advancing the Global Frontier We will advance the global frontier of cyber security. We will lead the development of emerging cyber technologies capable of adapting to new risks and opportunities across the cyber landscape.
The Strategy demands immediate and decisive action during the foundational and critical Horizon 1 (2023–2025) phase. In this two-part blog series, we will focus on how runZero can help operationalize Australia's Cyber Shields, specifically targeting Shield 2: Safe Technology and Shield 4: Protected critical infrastructure where the convergence of expanding digital frontiers and looming regulatory deadlines presents the greatest need for an exposure management platform. The imperative for action is underscored by Shield 4 which mandates the Critical Infrastructure Risk Management Program (CIRMP) obligation that commenced on 17 August 2023.
Cyber Shield 2: Safe technology #
The vision for Cyber Shield 2 is that "Australians can trust that their digital products and services are safe, secure and fit for purpose." The Australian Government plans to achieve this vision through the following initiatives.
Initiative 8: Ensure Australians can trust their digital products and software #
This initiative focuses on the security on IoT and smart devices and calls for adoption of international security standards for safeguarding IoT devices. This initiative also includes exploring options to legislate mandatory security standards. Feedback received from industry supports adoption of the ETSI EN 303 645, a standard published by the European Telecommunication Standards Institute for safeguarding consumer-grade IoT devices.
Legislating the first three provisions of ETSI EN 303 645 is also being evaluated. These include eliminating the use of shared default passwords, implementing processes to manage reports of vulnerabilities and implementing mechanisms to keep software updated on IoT devices.
Initiative 9: Protect our most valuable datasets #
Australia has been protecting sensitive data since the publication of the Privacy Act of 1988 and, later, the SOCI Act of 2018. This initiative focuses on identifying sensitive datasets that are not protected by existing legislation and determining whether additional safeguards are needed to protect these sensitive datasets. It also calls for the development of a voluntary data classification model and for a review of existing data retention legislation.
Data protection is also an area where Shield 2 works with Shield 4. Initiative 13 of Shield 4, which will be discussed in part 2 of this blog, proposed extending the definition of an 'asset' to include business critical data storage systems operated by critical infrastructure providers. This has already been implemented in the Security of Critical Infrastructure and Other Legislation Amendments (Enhanced Response and Prevention) Act of 2024, also simply known as the ERP Act.
Initiative 10: Promote the safe use of emerging technology #
While Initiative 10 makes reference to a variety of next-generation technologies, its primary focus in the Cyber Security Strategy is on safe and responsible use of artificial intelligence and advancements in quantum computing. While no specific legislation is referenced, the Australian Government does indicate that updates will be made to the Information Security Manual as advancements in quantum computing render current cryptographic methods insecure.
The runZero advantage #
runZero supports Cyber Shield 2 through its comprehensive asset discovery capabilities and exposure detection. Our unauthenticated active scanning approach is especially well suited for discovery and fingerprinting of IoT devices. While Initiative 8 is largely focused on consumer grade IoT devices, these devices are often prevalent on enterprise networks too. While smart TVs, IP phones and video cameras are common on enterprise networks, we also find robot vacuums, exercise equipment and smart lightbulbs connected to these networks. Not only is it critical to understand what IoT devices are lurking on your enterprise network, but identifying the security posture of those devices is equally important.
A runZero Research report highlights that 42% of enterprise devices are agentless which includes IoT that can’t be monitored or managed by existing security tools. Couple that with the fact that unfortunately many of those IoT devices lack built-in security creating easily exploitable vulnerabilities.
runZero’s exposure detection capabilities identifies difficult-to-detect exposures such as misconfigurations, segmentation issues, open access, default credentials, issues with cryptographic keys, and missing security controls. Our recent collaboration with Nuclei from Project Discovery expands further our detection capabilities when it comes to vulnerabilities and non-CVE exposure across all types of devices including IoT. For example, our default login tests and end-of-life software tracking can help organizations identify assets that do not align with the ETSI EN 303 645 standard.

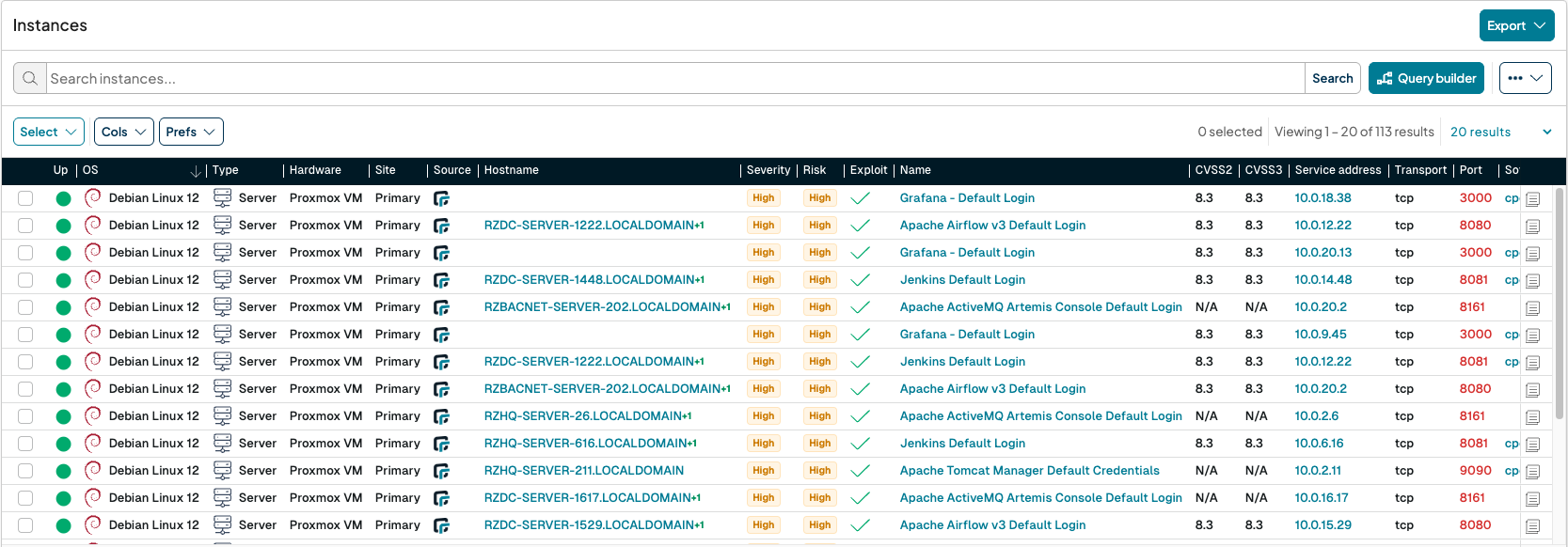
Identifying who is responsible for an asset or additional context such as location is foundational for proper data governance and security uplift. runZero enables geolocation tracking through its robust tagging capabilities as well as asset ownership tracking through various methods, including rules based asset ownership assignment and discovery of last known user from one or more agent-based integrations (e.g: Endpoint Protection platforms such as EDR). These are important data points when identifying and protecting your most valuable assets.
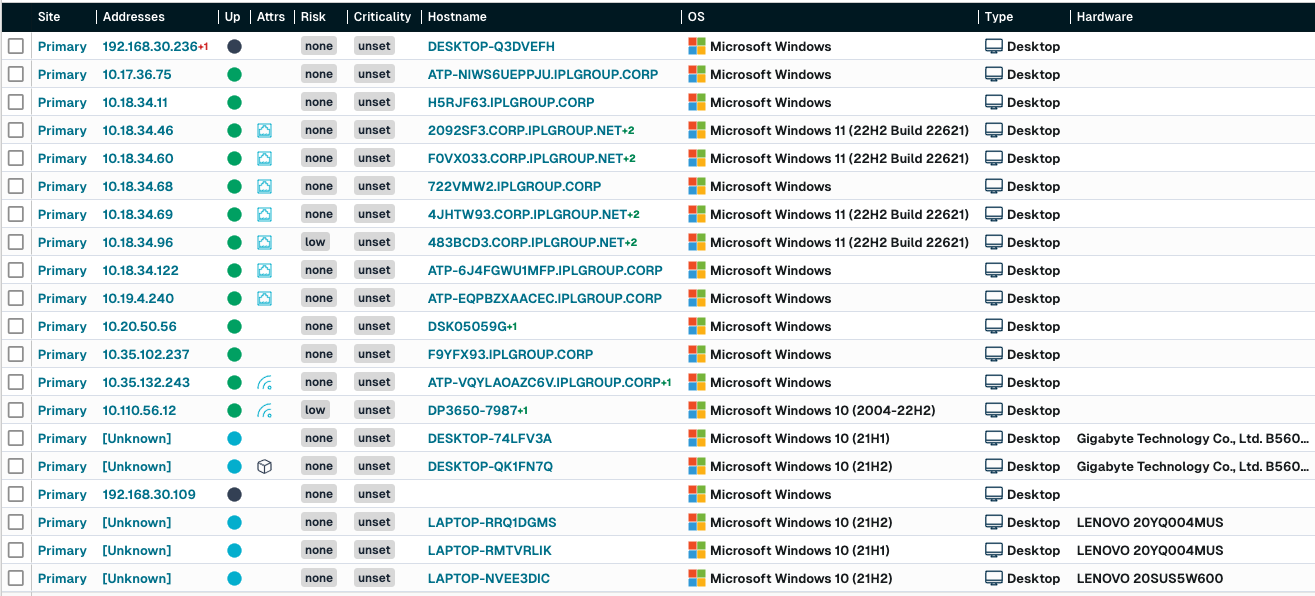
In a similar vein, runZero helps organizations identify critical assets that are missing security controls. A common use case is ensuring Endpoint Protection platforms are in place for all connected assets, especially ones that store or process critical data. runZero's dashboards can be utilized to monitor for unmanaged assets that are not running endpoint protection platforms or goals can be created to track progress toward remediation of these control gaps.
The following query example will surface any Windows assets that are missing a CrowdStrike EDR agent:
os:windows and not source:CrowdStrikeFrom the runZero console the results of the query shows you the list of assets that match:
Australia’s 2023–2030 Cyber Security Strategy sets a bold vision for national resilience and leadership in cybersecurity. As Horizon 1 nears completion and the Australian Government begins work on Horizon 2, organizations must take tangible steps to operationalize the Cyber Shields — especially Safe Technology and Protected Critical Infrastructure — where visibility and rapid response are key. runZero helps bridge the gap between policy intent and operational execution, enabling organizations to discover, assess, and secure every connected asset across their attack surface.
By leveraging real-time, accurate visibility and exposing hidden risks, runZero empowers critical infrastructure providers and enterprises alike to strengthen their cyber foundations and comply with evolving cybersecurity requirements.
Start your free trial or request a demo today.

















