Mergers and acquisitions (M&A) are accelerating across industries, with companies racing to gain market share, adopt new technologies, and outpace competitors. Global M&A value nearly doubled in a decade, rising from $2.4T in 2010 to over $5T in 2021.
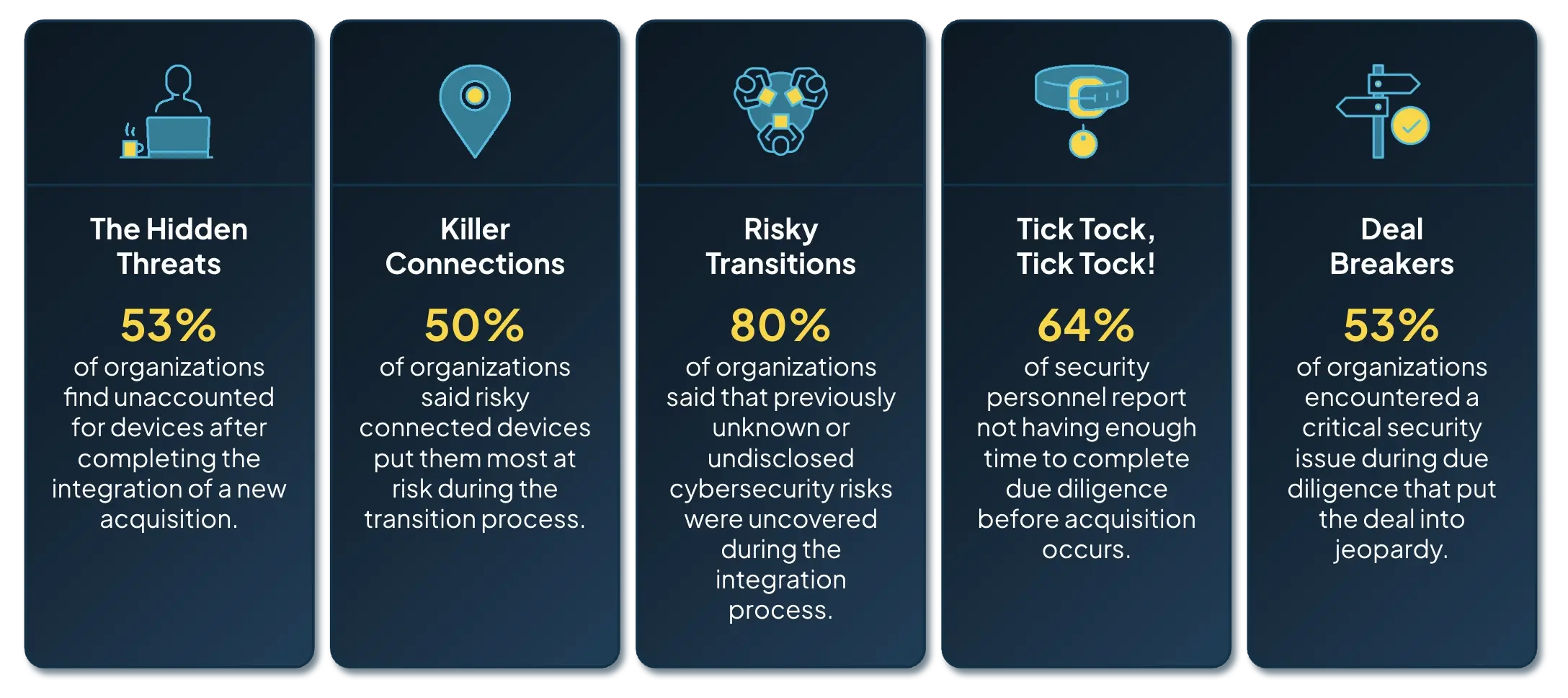
But with compressed timelines and rising stakes, security teams face mounting pressure to move fast — often with incomplete information. Cybersecurity is no longer just a checkpoint in M&A. It's a critical component. Hidden vulnerabilities, unknown assets, and compliance gaps can derail even the most strategic deals. 80% of organizations said that previously unknown or undisclosed cybersecurity risks were uncovered during the integration process. That’s too late.
In this post, we explore how security teams can facilitate a successful M&A — and how runZero can help.
Align Your Stakeholders #
Security due diligence isn’t the responsibility of one team. It’s a collaborative effort across business, legal, and technical functions, all of whom bring different lenses to the risks that could be inherited. Here are the key stakeholders, and the roles they play:
Key stakeholders include:
-
Information Security Teams evaluate the target’s cybersecurity posture, uncover vulnerabilities, review incident history, and assess exposure.
-
Legal and Compliance ensure alignment with data privacy regulations (e.g., GDPR, HIPAA, CCPA) and identify areas of potential legal risk.
-
CIO & CISO lead the technical and security evaluation of the target and align security findings with integration planning.
-
Chief Risk Officer & General Counsel oversee broader risk management, regulatory exposure, and reputational impact.
These teams must work together — quickly and decisively — to understand the full scope of the target’s cyber risk. But to do that, they need one thing above all: visibility.
How to Navigate the Visibility Challenge #
Modern M&A deals move fast, and traditional security tools can’t keep up. Compressed timelines and limited documentation often leave security teams with an incomplete view of the target’s environment — especially across nontraditional assets like IoT, OT, remote devices, and cloud infrastructure.
The visibility gap is real:
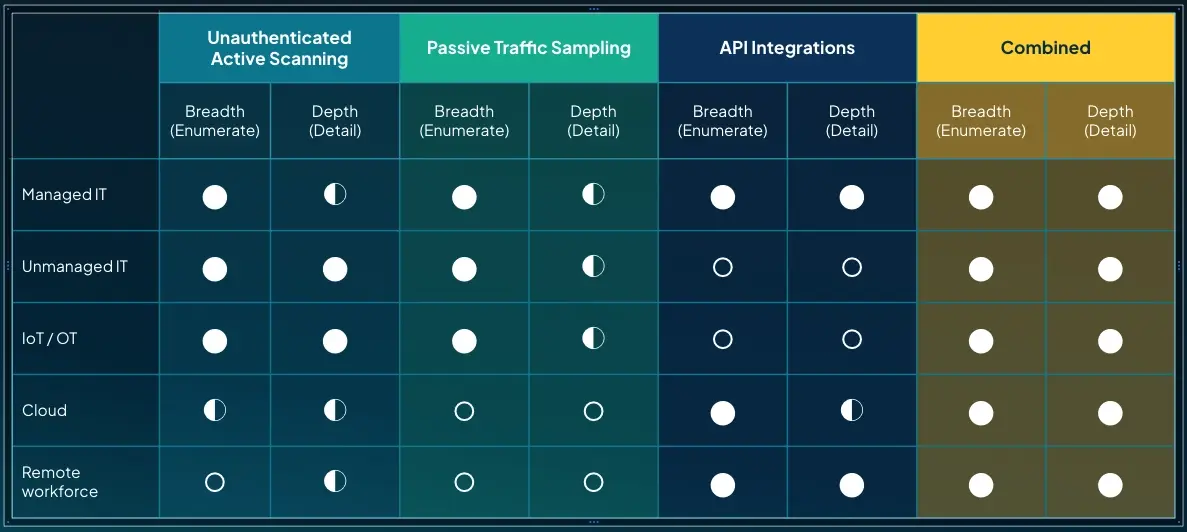
Legacy solutions typically focus on managed IT assets and overlook everything else. Many rely on siloed tools that don’t integrate, leaving teams to manually stitch together fragmented data. They struggle to detect remote endpoints and unmanaged devices, OT and IoT assets, air-gapped environments and external facing infrastructure.
The result? Blind spots, missed vulnerabilities, and costly surprises post-acquisition.
M&A activity instantly expands an organization’s attack surface, increasing exposure to:
- Outdated and unpatched systems
- Misconfigured infrastructure
- Devices that may already be compromised
- Compliance failures and unknown risks
- Shadow IT and unmanaged technology
And once the acquisition is finalized, these risks become your responsibility. Without proactive, full-spectrum discovery, organizations may face:
- Data breaches
- Operational disruptions
- Regulatory penalties
- Delayed IT integration and inflated post-deal costs
In today’s high-pressure environment, the lack of visibility makes it even harder to identify these threats in time to act. To fully assess risk and protect your investment, security teams need real-time, unified visibility across every environment — without agents, credentials, or installed software.
The runZero Advantage #
runZero is an exposure management platform built for speed, depth, and coverage, delivering the visibility needed to support M&A cyber due diligence across all environments.
With runZero, security teams get:
- Active scanning: Proprietary scanning identifies assets in both online and air-gapped networks. These scans are designed to be safe and non-intrusive, ensuring minimal impact on network performance and device operations.
- Hosted Explorer: For discovering internet-facing assets.
- CLI Scanner: Ideal for disconnected environments — no runZero Console required.
- Passive discovery: Captures network traffic to identify devices without actively probing them.
- Third-party API integrations: Pulls data from EDR, MDM, network management systems, and vulnerability tools to enrich asset context.
- Advanced fingerprinting: Uncovers OS, services, misconfigurations, and security posture—without credentials.
This multifaceted approach uncovers hidden risks, eliminates blind spots, and empowers security teams to:
- Accurately identify assets before the deal closes
- Prioritize real risks over noisy vulnerabilities
- Avoid costly surprises post-acquisition
- Work faster and smarter across legal, compliance, and risk teams
Get Started #
Cybersecurity is foundational to protecting your investment and ensuring successful integration. Without visibility, you’re flying blind. With runZero, you see everything before it becomes your responsibility. Ready to make your next acquisition safer and smarter? Start your free trial or request a demo today.
















