Higher education problems and solutions #
Search the internet for “higher education” and “cybersecurity,” and you’ll find no shortage of FUD-dy articles similar to the following:
- Report Shows Malware Attacks on the Rise in Higher Education
- Higher ed’s response to ransomware attacks lagged other sectors, survey suggests
- The State of University Cybersecurity: 3 Major Problems in 2023
Regrettably, constantly using "shocking" headlines only highlights problems rather than offering solutions. A better approach is to understand why higher education is so often in the sights of the adversary. Let’s examine the information security and asset inventory challenges unique to academia.
Higher education institutes have the complexities of a city #
Higher education institutions share many similarities with municipalities. On campuses, you will find:
- Offices
- Housing
- Athletic centers
- Medical centers
- Galleries and theaters
- Food and beverage services
- Sanitation and composting facilities
- Law enforcement and emergency response
It’s not just classrooms and lecture halls. The campus looks like a small city with lots of network-connected equipment, including power generators. Virginia Tech’s steam power plant generates an annual steam output greater than 943 billion BTUs, providing campus buildings with a portion of their heat, hot water, and electricity. It’s on the network.
Universities have more complexity and less control than a company with a collection of offices. So they need cybersecurity tools and services to handle various devices and environments. Nevertheless, cybersecurity vendors focus on industry first rather than academia, reflecting the budget gap in these sectors. Education ranks lowest regarding security budget as a percentage of IT budgets. (See chart.)
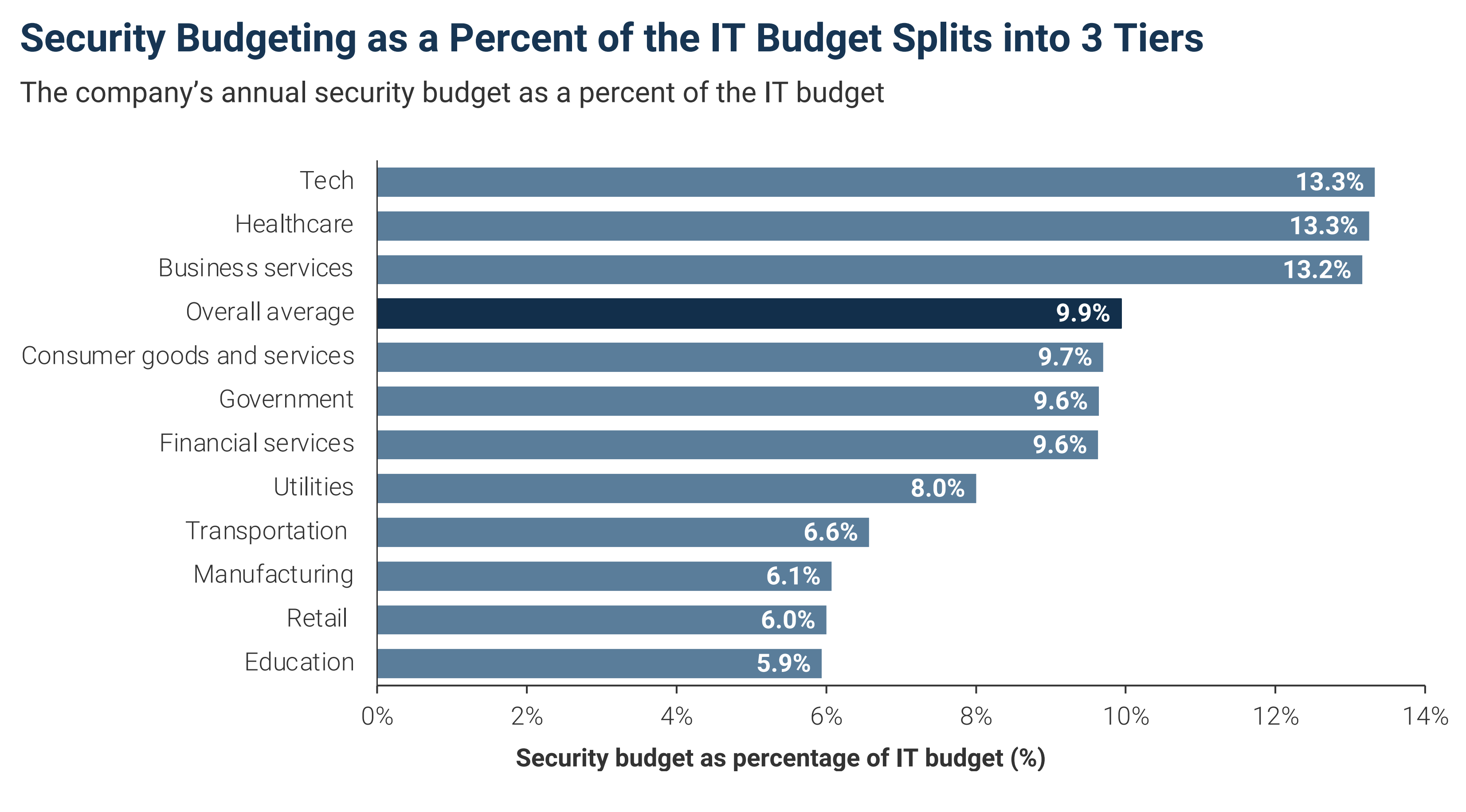
Source: IANS & Artico, Security Budget Benchmark Summary Report, 2022
The security tools at a university only cover certain areas on campus and some devices are protected while others are not.
Academic freedom #
Academic freedom has been a core tenet of higher education since the earliest days of university education. In the 1150s, the University of Bologna’s academic charter allowed scholars to travel freely for educational purposes. Fast-forward 800 years, unfettered access expanded beyond travel to include access to data and the free exchange of ideas across institutions of higher education (IHEs). Universities’ culture of openness has no doubt cultivated numerous advances in art, science, technology, and beyond.
The internet (and its predecessors like Arpanet) is an example of such advancement. Universities, alongside some government agencies, adopted interconnected networks early on and created the infrastructure later adopted for commercial applications. For early university adopters, the notion of openness implied the following:
- Wired and wireless access
- Use of public IP addresses
- Free exchange of data
Open access stood on the bedrock of assumed good intent. Many universities offer internet access beyond campus to close the “digital divide,” a meaningful way to democratize broadband. On campus, there was a time when anyone who could access an Ethernet jack could get on the university network without authentication. As the rise of bad actors ruined a good thing for everyone, universities needed to balance open access against data privacy and information security governance. Not doing so leads to a proliferation of unmanaged devices on the network to be compromised or weaponized by the adversary.
Another nuance of open access includes public IP addresses, made available even to students. Frontline exposure to the internet significantly lowers the barriers for technology students. This author credits his first off-campus job to learning Unix and networking while hosting his FreeBSD server in the dorm. (It wasn’t just a public IP. It was a static IP and a registered hostname, too. Those were the days!) The public IP debate still lingers today, though. MIT only moved away from public IPv4 addresses in 2017, and much criticism and indictment of stifling innovation soon followed. Allowing students and faculty to self-host publicly-available services with minimal governance creates a petri dish of unmanaged devices, adding more uncertainty to the school’s external attack surface. Universities have a tough challenge balancing that attack surface against the mission of academic freedom.
Part of that attack surface includes the services students and faculty would host to collaborate with counterparts at other IHEs. Case in point, Tim Berners-Lee invented HTTP in 1989 to share and collaboratively edit physics papers. Anonymous FTP continues to be a go-to method to support that collaboration through data exchange. Like HTTP, numerous tools exist to stand up an FTP server, and anonymous FTP does not require authentication. Businesses have phased out FTP and entirely shut down shadow IT FTP long ago. On the other hand, many IHEs must settle for educating the user population and accepting the associated risks.
The open-access culture and campus-as-a-city concept goes hand in hand with the federated nature of universities. Departments have a lot of freedom regarding their curricula and methodologies. Tenured faculty members often have a more sustained influence over policy than administrators that come and go. Thus, they have a lot of autonomy over their digital infrastructure. A departmental website may be self-hosted (there are those public IPs again) instead of a centralized managed server or DMZ. What each faculty member does with that autonomy also varies from department to department–the business school’s digital infrastructure will differ from the art department’s.
Similarly, faculties have unfettered access to connect all sorts of devices, including uncommon research devices. With the rise of research at community colleges, this practice goes beyond R1 and R2 universities. While this helps learning and research, these are precisely the devices that are hardest to protect. There’s no EDR for an electron microscope, and the adversary is looking for it. With no governance, the security team does not even know it’s a risk.
Students bring more than a laptop #
The rise of personal technologies ushered in another set of device management challenges for higher education cybersecurity. Students no longer just bring their laptops but also their tablets, phones, game consoles, and other IoT/smart devices. Digital LED lava lamps might seem like toys, but are also a target for the adversary to compromise or weaponize. Bitcoin mining using campus electricity is a ubiquitous problem in universities, with security and financial ramifications.
Universities cannot simply ban student-own devices. Some well-endowed schools issue university-managed laptops to all students, but that’s not common. The student’s device may be behind on patches, but the school can’t tell them to stop using the only device they have. Sometimes, that outdated Chromebook is the only laptop the student can afford, and security policy cannot widen the gap among students from different socio-economic backgrounds.
This challenge is also an issue of scale. Imagine a campus with 10,000 students, each with four devices. That’s 40,000 new devices coming on campus each school year. Most universities do not have the bandwidth or tools to onboard these many BYO devices, partly explaining why some universities allow unfettered network access. Capabilities for fingerprinting IoT devices are limited, which also hampers universities’ abilities to manage this transient device proliferation. One large university in Maryland uses a network access controller (NAC) to adjudicate which devices can access the network via MAC address. Their tooling only provides superficial fingerprinting, so the best they can do is limit each student to five devices without considering the type of devices.
Cybersecurity threats; the network is not just campus #
The COVID-19 pandemic accelerated an existing trend in hybrid and online learning. Overnight, universities had to shift to using the Internet as the primary channel for education. The use of SaaS learning tools has increased and expanded the area where security teams must provide protection.
Some universities issue laptops to students upon enrollment. The pandemic disconnected these universities-managed devices from the campus network, at risk of falling out from management and behind on patches and updates. In some cases, these devices were off-network for two years. Upon return, they were in unknown states regarding functionality and security posture. As universities shifted to hybrid learning, the need to keep tabs on devices no matter their physical location is a sustaining concern.
Sometimes the extended campus goes beyond geopolitical borders with international students. These students may need to alternate between VPN and direct access when working with university resources. Geolocation-based threat detection controls often fail to differentiate between remote students and attackers, masking their IP addresses from abroad. Faculty members who frequently visit other campuses and institutions worldwide present the same issues. A university’s inventory of assets knows no borders.
Regulation upon regulation #
Despite the extraordinary challenges of securing IHEs, they are held to standards just as strict as industry, if not more.
- Like businesses, they must comply with PCI-DSS for all the credit card processes, just like a mini-city.
- IHEs that take federal grants as part of government research must also comply with NIST and DFARS.
- Most universities provide some form of medical care, which brings them under regulation by HIPAA in the US and PIPEDA in Canada.
- Gramm-Leach-Bliley Act requires compliance from schools participating in the US Federal Student Aid program by June 9, 2023. One requirement is to discover “reasonably foreseeable internal and external risks to the security, confidentiality, and integrity of customer information (as the term customer information applies to the institution or servicer).”
- In the United States, FERPA is the primary privacy regulation governing the protection of student information governed by the Department of Education.
Asset Inventorying is a recurring requirement among these regulations, a foundational component for a security program. So what does that mean? As FERPA states, “The inventory should include both authorized and unauthorized devices used in your computing environment. These devices are often scanned and discovered by automated programs (continuously searching the internet for vulnerabilities) and if unsecured devices are discovered they can be compromised. Inventorying, when used in conjunction with network mapping, will give your organization a better understanding of the security requirements needed to protect your assets.”
Staffing challenges abound #
Cyberdefense in higher education is an albatross. Reliance on staff only partially solves the problem. In the head-heart-wallet triad of compensation, IHEs usually lose on the wallet. It’s not unheard of for infosec analysts at a university to be paid half or a third of jobs in the industry. Many universities outsource part of their security program. Many were early adopters of fractional CISOs. According to one EDUCAUSE statistic, universities have three security staffers per 10,000 students, faculty, and staff. Therefore, smaller universities manage with a CISO with no direct reports, or the IT team takes on the entire responsibility of fulfilling the security function. These are the same IT teams already inundated with help desk functions. One consequence is IHEs are more likely to publish their tools, giving the adversary insights they wouldn’t usually have with targets in industry.
Another consequence is that student workers are filling in the talent gap. Student-run SOCs are a common feature of higher education cyber defense. For example, the University of South Carolina - Aiken powers their SOC by college seniors as part of their capstone project. While an excellent opportunity for students to learn and significant cost savings for the university, it also means the team often needs more experience. Tooling must be easy to understand and easy to use to compensate.
Rising to the challenge #
runZero is a cyber asset attack surface management solution that can uncover and maintain an inventory of all devices:
- In power plants, research labs, or any other OT environment
- In student dorms with accurate fingerprints of all sorts of IoT devices
- In students’ homes, if university-managed devices have disconnected from the campus
Beyond a simple list of assets, the runZero inventory also keeps tabs on the services exposed on the external attack surface, even ones hosted without governance.
All of this functionality is available in a discreet way to minimize the impact on learning, research, and academic freedom.
runZero scales up to millions of devices, but it’s easy to try. The free 21-day trial even downgrades to a free version for personal use or organizations with less than 256 devices. Find out what’s connected to your network in less than 20 minutes.