Products
| Product | |
| 1 | Multiple multi-function printers |
CVE
CVE-2025-8452Executive summary #
Brother printer firmware advertises the serial number of the device over the network via the “uscan” protocol in its implementation of the eSCL specification. While serial numbers are rarely considered sensitive, in this case, the serial number can be used to derive the default administrator password of the device. Therefore, this is an instance of CWE-538: Insertion of Sensitive Information into Externally-Accessible File or Directory, and we estimate the CVSS 3.1 rating to be 4.3 (CVSS:3.1/AV:A/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N).
This flaw is quite similar to CVE-2024-51977, discovered and disclosed by Stephen Fewer of Rapid7.
Technical details #
Brother printers, like most other popular networked multi-fuction printers (MFPs) implement the eSCL technical standard from Mopria Alliance to communicate capabilities to printer clients. eSCL may stand for “Enhanced Scanner Communication Language,” but frustratingly, the technical specification and license agreement of eSCL does not expand this initialism in any formal capacity. Yay for proprietary standards.
One item exposed over eSCL is the device serial number, which is fetchable by discovery applications which implement the uscan functionality of eSCL. Two important things to consider with this revelation:
- Serial numbers are, by themselves, rarely considered particularly sensitive. They are written down on the device itself, after all, and often used as specific identifiers.
- While this client functionality is normally found only in clients that are specifically seeking printer capabilities, more general purpose network scanners, such as the runZero Explorer, does this by default when it encounters a multi-function printer, as seen in the screenshot below:
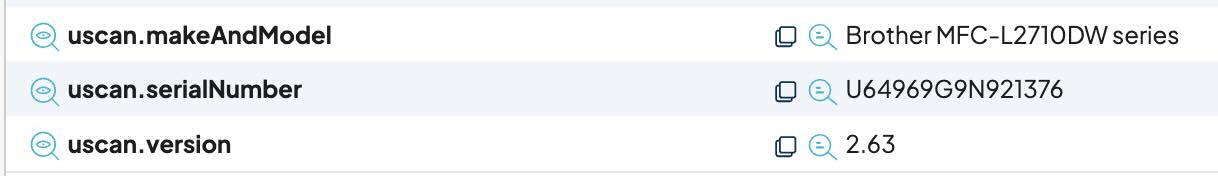
That said, Brother serial numbers are not merely non-secret “usernames” in many cases, thanks to CVE-2024-51978. This vulnerability describes the case where the serial number can be used to derive the factory-set default administrator password, as demonstrated by Stephen Fewer’s proof-of concept exploit:
$ ruby CVE-2024-51978.rb --printer_serial U64969G9N921376 [+] Generated default password: m#CJr6$S
The defense against this, of course, is to change the default administrator password of the affected device. It should go without saying, the serial number does not change.
Brother provided this advice, via JPCERT/CC in e-mail:
This vulnerability only affects devices impacted by CVE-2024-51978. Additionally, it does not affect products where the administrator password has been changed. To reduce the risk associated with this vulnerability, change the default administrator password via Web Based Management.
Attacker value #
On its own, this information leak is of little value to most attackers, thus the middling CVSS vectors. Scenarios can be concocted where a person might be surprised that their serial number has been exposed to an adversary. It is unknown if the affected printers implement printer tracking dots to link printed documents to specific printers. If so, this vulnerability could expose at-risk individuals such as whistleblowers and victims of harassment (as well as counterfeiters and blackmailers).
When combined with CVE-2024-51978, however, this vulnerability is the first of a two step process of discovering a local admin password. It’s commendable that the default password shipped with Brother firmware does not merely set admin:admin is the default administrator password, but this strategy is ultimately compromised by this vulnerability.
Credit #
This vulnerability was discovered and reported by Rob King of runZero, and is based on the work published by Stephen Fewer of Rapid7. The disclosure was coordinated by AHA! and JPCERT/CC.
Timeline #
- 2025-Jun-25 (Wed): Rapid7 and Stephen Fewer published their advisory.
- 2025-Jun-26 (Thu): Matthew Kienow from runZero noted the eSCL vector in a Rapid Response. runZero reached out to Rapid7 to update CVE-2024-51977. Rapid7 advised a new CVE.
- 2025-Jun-30 (Mon): Disclosed to Brother. (Case 250630-000684)
- 2025-Jul-07 (Mon): Brother PSIRT initially determined this was not a vulnerability.
- 2025-Jul-14 (Mon): Disclosed to JPCERT/CC (Case 94025271), citing the Nuclei template and Metasploit module that exercise the effect of CVE-2024-51978 has on disclosed serial numbers, and the fact that the issue is already public anyway.
- 2025-Aug-12 (Tue): JPCERT/CC noted Brother’s product advisory which mentions CVE-2025-8452. The CVE was then published several hours later to avoid confusion.
- 2025-Aug-14 (Thu): Coordinated disclosure through AHA! Published this advisory on CVE-2025-8452











