Latest Veeam vulnerabilites #
Veeam has disclosed two vulnerabilities found internally within their Veeam Service Provider Console (VSPC).
- CVE-2024-42448 is rated Critical with a CVSS score of 9.9, which potentially allows remote code execution.
- CVE-2024-42449 is rated High with a CVSS score of 7.1, which potentially leaks the NTLM hash of a service account and allows for the deletion of files on the server.
What is the impact? #
Although there an no known exploitations of the vulnerabilities in the wild, CVE-2024-42448 could allow remote code execution by an attacker on the server. An attacker would need to launch their attack from an authorized VSPC management agent server in order to exploit either of the disclosed vulnerabilities.
Are updates or workarounds available? #
No mitigations are available for the disclosed vulnerabilities. Instead, the vendor is strongly encouraging customers to "update to the latest cumulative patch".
How to find potentially vulnerable systems with runZero #
From the Service Inventory, use the following query to locate systems running potentially vulnerable software:
has:"html.title" html.title:"Veeam Service Provider Console"December 2022 Veeam vulnerabilities #
Veeam published information on two vulnerabilities in the Veeam Backup & Replication product, originally reported by Nikita Petrov of Positive Technologies.
As of December 16th, CISA had announced the addition of two critical vulnerabilities (tracked as CVE-2022-26500 and CVE-2022-26501) to the KEV catalog. These CVEs were actively being exploited, putting systems at risk. It was critical that these systems were updated to patch these vulnerabilities as soon as possible.
Which versions were affected? #
These vulnerabilities affected Backup & Replication versions 9.5, 10, and 11, allowing for exploitation by attackers to achieve unauthenticated remote code execution via the Veeam Distribution Service API. Details on the vulnerabilities (identified as CVE-2022-26500 and CVE-2022-26501) were not published at the time of writing, though Veeam had assigned a "critical" CVSS score of 9.8.
Were updates made available? #
Patched releases of Veeam Backup & Replication were made available (see the "Solution" section). Guidance from Veeam was for administrators to update to these newer versions as soon as possible. If near-term updating was not possible, Veeam offered a temporary mitigation strategy via stopping-and-disabling the Veeam Distribution Service (see the "Solution->Notes" section).
How runZero users found potentially vulnerable Veeam instances #
We added the default port (9380) for the Veeam Distribution Service API to our runZero Explorer and Scanner. If you were using Explorer or Scanner v2.11.5 or later, you just needed to ensure you had performed a recent scan of your assets prior to running the query below. If you were using an older Explorer or Scanner, users simply added port 9380 to the "Included TCP ports" (under the Advanced tab) and then ran a scan to gather the necessary data.
From the Asset Inventory, users ran the following pre-built query to locate Veeam Distribution Service instances within their network that could have potentially ran vulnerable versions of Veeam Backup & Replication:
tcp_port:9380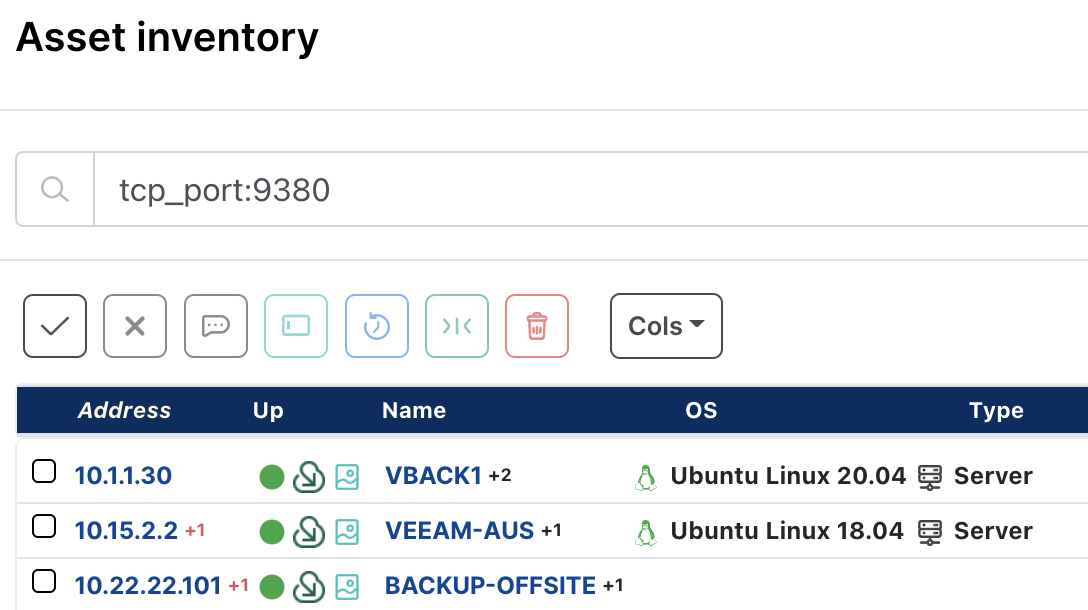
As always, any prebuilt queries we create are available from our Queries Library. Check out the library for other useful inventory queries.

















