Version 1.1.5 of the Rumble platform is live! This release includes a new Switch Topology report, updates to the Network Bridges report, and improvements to how SNMP data is collected during scans. Combined, these updates can shine a light on misconfigured network segmentation and help identify assets that may not have been scanned at all. This post will walk through these updates and highlight how these reports can be used to identify unknown risks.
The Switch Topology report uses data enumerated via SNMP to map switch ports to assets. In environments where SNMP v2 with public or private communities are in use, this enumeration happens automatically, but non-default communities can also be provided in the scan configuration, with ~~SNMP v3 support planned for the near future~~ SNMP v3 support available. Clicking on a node in this report will highlight its connections, while mousing over the connections will indicate the specific switch interface associated with the connection. This report is available for all organizations with SNMP-enabled switches and covered by a recent scan (Rumble Agent/Scanner v1.1.4 or newer).
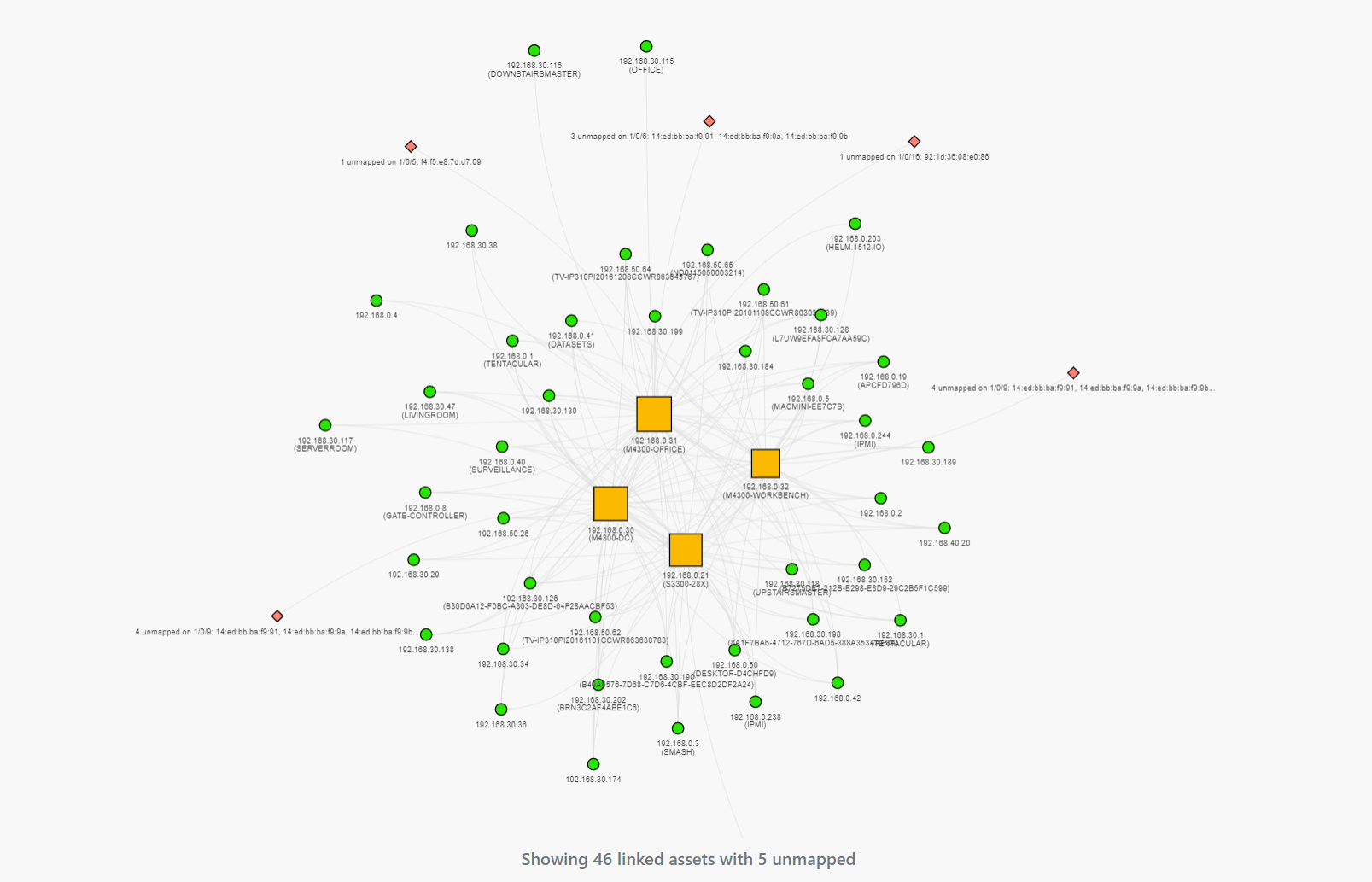
This topology view is helpful when trying to understand how a given asset or switch is connected, but also provides a critical data point related to risk; the number of unmapped assets. An unmapped asset is a MAC address connected to a switch, but not found in an ARP cache or through any of the other techniques Rumble uses for remote MAC address discovery. For environments where a Rumble agent is connected to each network segment, unmapped assets may highlight VLANs or network segments that are missing from the scan scope. In environments where Rumble is scanning assets multiple hops away, the unmapped asset count can provide an estimate of how well the remote segment is being identified.
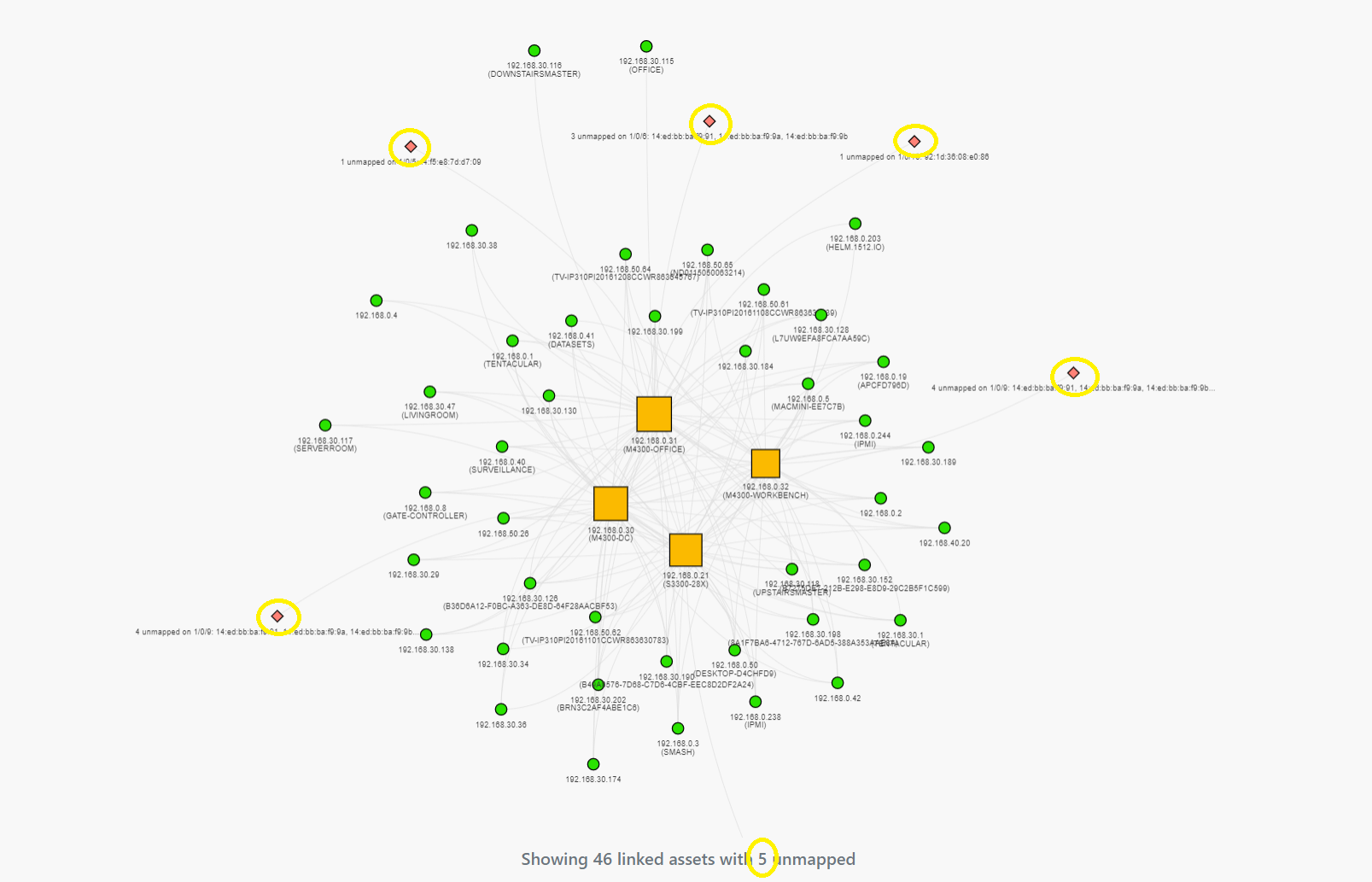
In the graph above, we can see that Rumble identified five unmapped assets across five different switch ports. These unmapped assets could not be correlated with scan data and should be investigated to determine where they are coming from and why they aren't turning up as part of a normal scan. Ports with unmapped assets are identified as red diamonds on the map, with the total count summarized at the bottom.
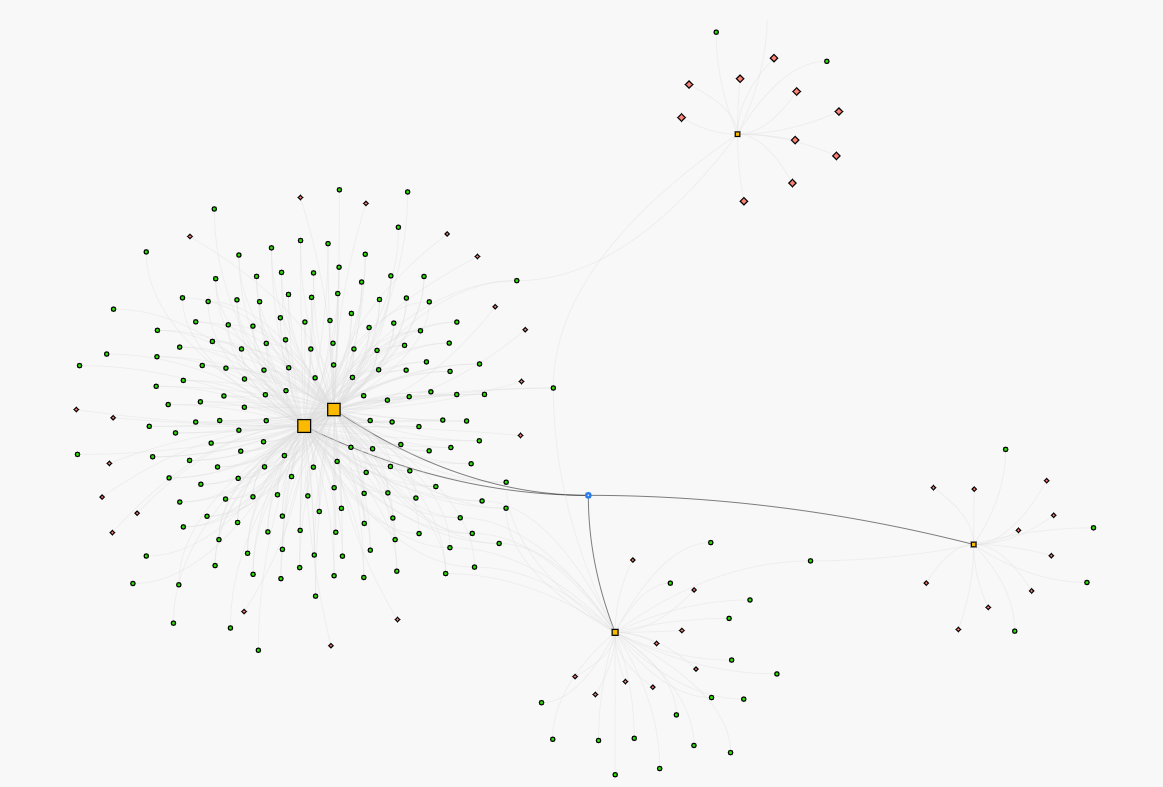
In more complex environments, the Switch Topology report makes it possible identify subnets missing from the discovery scope. In the graph above, we can see that for two switches, our visibility is almost perfect, but there are two segments with limited visibility, and another with almost none. To improve the discovery process, the IP ranges of those subnets should be identified and rescanned.
This graph also highlights broadcast domain visibility for connected assets. The highlighted asset in the center can see layer-2 broadcast data across four different switches. This may highlight a risk; an attacker running NetBIOS or LLMNR spoofing tools such as Responder or Metasploit could launch attacks against a large number of assets from this node.
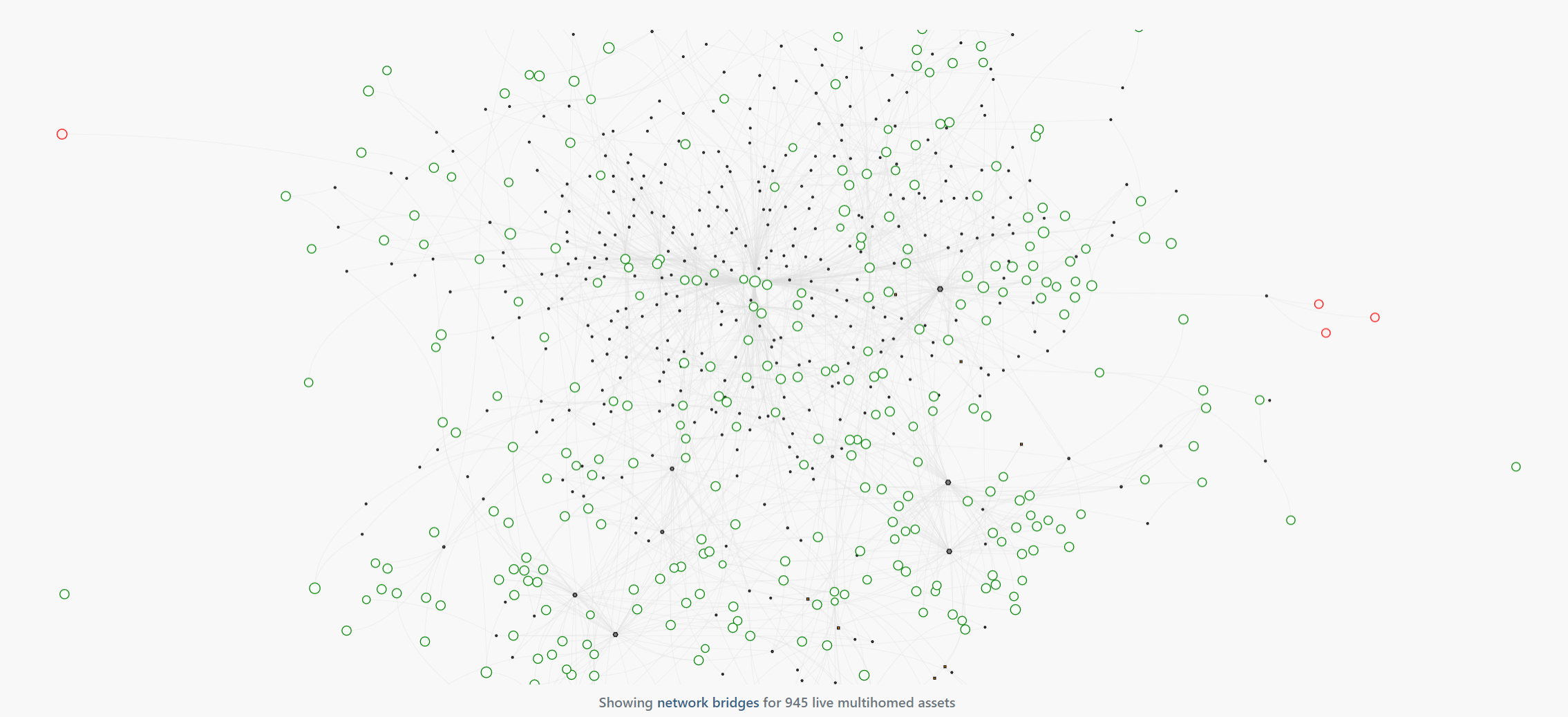
The Network Bridges report received an overhaul in this update, with changes to weights, layouts, and interactivity. Assets that have been identified as network switches are now shown as orange squares to match the Switch Topology report, multi-homed assets are now shown as gray hexagons, and assets are now weighted based on the number of networks they bridge. In the graph above, we can see four internet-facing subnets (red circles) are bridged into the internal network, along with seven highly interconnected assets (the larger gray hexagons). From a risk perspective, these may be worth investigating, as a breach of one of these assets could provide across to the rest of the environment.
We hope you find these updates useful and we would love your feedback about what we can improve.
Don't have a Rumble account? Sign up for a free trial and let us know what you think!