In the realm of industrial automation, communication protocols play a crucial role in ensuring seamless interaction between various components and systems. One such protocol in the TwinCAT 3 ecosystem is the Automation Device Specification (ADS) protocol. Developed by Beckhoff Automation, ADS is integral to the TwinCAT 3 software suite, facilitating robust and efficient communication between different automation devices.
What is ADS? #
The Automation Device Specification (ADS) protocol is a communication protocol designed to enable interaction between TwinCAT 3 automation devices. ADS functions as a gateway for data exchange and command execution between software applications and hardware components. It operates over TCP/IP networks, ensuring reliable and real-time communication. Both TCP and UDP are supported by the protocol as well as a secure version called Secure ADS which uses TLSv1.2 to secure the TCP connection.
The Role of ADS in TwinCAT 3 #
TwinCAT 3 leverages ADS to connect its various components. Within this environment, ADS facilitates communication between the TwinCAT runtime, PLCs, and HMI systems. By providing a standardized interface for data exchange, ADS simplifies the integration of different elements within the TwinCAT ecosystem. This integration capability is instrumental in developing sophisticated automation solutions that require interaction between multiple devices and software modules.
runZero Speaks ADS #
The runZero research team has been working hard to increase the OT protocols available in runZero. We recently added the ADS protocol for passive scanning to identify devices that speak ADS. We have a very good understanding of the OSI model so we have started layering in support for any of these Ethernet-based protocols.
After reviewing the ADS specification we discovered that it operates on TCP port 48898 and UDP port 48899. By adding these ports to our broader global ports list we can start to decode the new traffic and identify the communicating devices. Although we see all of the traffic on those ports, we are only interested in a very specific packet to identify devices. The ADS specification outlines a ReadDeviceInfo command (Figure 1) which would tell us the version, build, and name of the device.
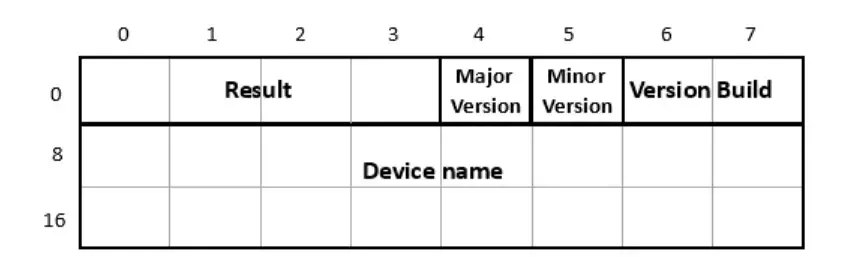
FIGURE 1 - ReadDeviceInfo packet layout courtesy of Beckhoff Automation LLC
If the packet is successfully decoded into this command we can assert that it is a legitimate device since the packet originated on the documented ports above. This gives us a high degree of confidence to continue fingerprinting this device and place it into your asset inventory.
Future Trends and Developments #
As industrial automation continues to evolve, so too will the ADS protocol. Future developments may include enhancements to support emerging technologies such as IoT and Industry 4.0. There is potential for increased integration with cloud-based systems and advanced analytics, further expanding the capabilities of ADS. Staying abreast of these trends will be essential for us to further improve our fingerprinting capabilities as this protocol makes its way into other domains outside of industrial automation.
Subscribe now to stay up to date on runZero support for discovery of OT protocols.

















