With our Rumble 2.1 release, we added alert templates. That means you can receive custom Slack messages to alert on events you care about, like new, unmanaged, or modified devices. Yay, another Slack channel and more notifications! But, sometimes, it's critical to have–especially if you need to actively stay on top of your inventory.
What are alert templates? #
Alert templates let you contextualize and enrich notification messages with custom messaging and data from runZero. To build templates, you'll need to know the Mustache syntax. We'll walk through an example to show you how it works.
How to set up Slack notifications #
Let's take a look at how we can use templates and the Rules Engine to notify us on newly discovered or modified devices.
Step 1. Set up a webhook for Slack #
First thing you need to do: set up a webhook to send data to a Slack channel.
After you set it up, you'll need the incoming webhook URL for the next step. Your webhook URL will look something like:
https://hooks.slack.com/services/T00000000/B00000000/XXXXXXXXXX
Step 2. Create a new channel in runZero #
-
Now that you have your webhook URL, go to the Channels page in your console and click Create channel.
-
When the New channel page appears, enter a name for the channel. We'll call ours
Slack. Then select Webhook as the channel type and enter your webhook URL.
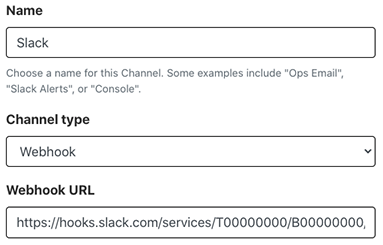
- Save your channel.
Step 3. Build an alert template #
-
Go to the Templates page.
-
Webhook channels accept plaintext or JSON data types. For our example, we'll use JSON to structure our data.
-
Give the template a name. We'll name ours "Slack notification - New or modified devices found." We'll want to create an alert that provides the:
- Scan completion timestamp
- Scan site
- Scan results
- New asset details
- Modified asset details
- Link to task details
- Name of rule triggering the alert
In the body, we'll add the following JSON:
{
"blocks": [
{
"type": "section",
"text": {
"type": "mrkdwn",
"text": "*runZero event*: {{#event}}{{source_name}} - {{action}} on {{target_type}} {{target_name}} at {{created_at}}{{/event}}"
}
},{{#rule.is_scan}}
{
"type": "section",
"text": {
"type": "mrkdwn",
"text": "*Site:* {{site.name}}\n*Scan result:* {{#scan}}{{assets_new}} new and {{assets_changed}} changed assets.{{/scan}}"
}
},
{
"type": "section",
"text": {
"type": "mrkdwn",
"text": "*New assets*\n\n{{#report.new}} * {{addresses}}: {{names}} ({{type}})\n{{/report.new}}"
}
},
{
"type": "section",
"text": {
"type": "mrkdwn",
"text": "*Changed assets*\n\n{{#report.changed}} * {{addresses}}: {{names}} ({{type}})\n{{/report.changed}}"
}
},{{/rule.is_scan}}{{#task}}
{
"type": "section",
"text": {
"type": "mrkdwn",
"text": "*Task details:* {{url}}"
}
},{{/task}}
{
"type": "section",
"text": {
"type": "mrkdwn",
"text": "_Rule triggering this notification: {{rule.name}}_"
}
}
]
}
We use the Mustache syntax–the double curly braces {{variable}}–to insert data into the Slack message.
{{% doc-callouts type="cross-reference" %}}
What other data can you include? A lot. Visit our Object and Field Reference to see everything you can include in your templates.
{{% /doc-callouts %}}
Step 4. Create a rule #
Now that you have your channel and template, you're ready to create your rule.
-
Go to the New rule page and choose an event type. For our example, we'll select
new-assets-foundand name our rule something likeNew assets rule. -
Configure the rule to trigger if the number of matches is
greater or equal to 1. -
Configure the action to notify you via Slack using the template created in step 3.
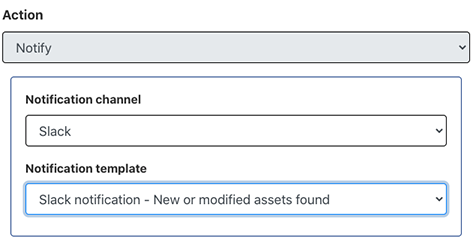
- Save the rule.
The next time the scan runs, runZero will alert you when it identifies new or modified assets.
Try the runZero Rules Engine #
The Rules Engine is available with the free trial of runZero Professional and Enterprise editions. Sign up for a free trial to see what you can do with runZero.
















