What is Samba? #
Samba is an incredibly popular open source software project that describes itself as "the standard Windows interoperability suite of programs for Linux and Unix". Samba is used in most implementations of SMB/CIFS outside of Microsoft Windows, Apple macOS, and a few commercial network storage vendors. In short, Samba is used to enable SMB file transfers, and to power Active Directory implementations without Microsoft Windows servers.
Latest Samba vulnerability #
On October 10th, the Samba team announced an interesting vulnerability that could allow a remote attacker to connect to unix stream sockets on the Samba server. The issue occurs when a RPC service name is requested that contains a unix directory traversal sequence (../). The vulnerability is being tracked as CVE-2023-3961 and may enable remote code execution and esclation of privilege attacks using system-specific unix stream sockets. These sockets are typically used for interprocess communication and commercial NAS vendors may be more exposed than a standard systemd-based Linux installations. The Samba project scored this as CVSS 3.1: AV:N/AC:H/PR:N/UI:N/S:C/C:N/I:H/A:N (6.8), but the actual risk may vary drastically by implementation.
What is the risk? #
The actual risk may vary wildly given the different implementations of Samba across open source and commercial systems. On a typical Ubuntu Linux (22.04) system, unix stream sockets associated with the core systemd service (system_bus_socket) may enable denial of service at the least. In commercial implementations, such as Synology NAS devices, the exposed unix stream sockets may expose much more:
/run/filestation/thumbd.sock
/run/postgresql/.s.PGSQL.5432
/run/recycle_bin/daemon.sock
/run/samba/nmbd/unexpected
/run/syno_background_task.sock
/run/synocached.sock
/run/synologan.sock
/run/synoscgi_domain_socket.sock
/run/synoscgi-fastapi.sock
/run/synoscgi.sock
/run/synoscgi_socket.sock
/run/syslog-ng/syslog-ng.ctl
/run/systemd/journal/stdout
/run/systemd/private
/run/udev/control
/tmp/iscsi/plugin_server.sock
/tmp/rtsp_socket_server
/tmp/S2S/daemon.sock
/tmp/ssmessaged.sock
/tmp/ssmobiled.sock
/tmp/ssrtpdataprovider.sock
/tmp/sswebstreamd.sock
/tmp/synosnmpcd.sock
/tmp/synotaskmgr.sock
/tmp/synotokenmgr.sock
/tmp/synowstransfer.sock
/var/run/dbus/system_bus_socket
/var/run/synobackupd.socket
/var/run/synocgid/synocgid.apikey.get.socket
/var/run/synocgid/synocgid.checkreplayattack.socket
/var/run/synocgid/synocgid.htua.socket
/var/run/synocgid/synocgid.remove.by.attr.socket
/var/run/synocgid/synocgid.remove.user.socket
/var/run/synocgid/synocgid.session.add.socket
/var/run/synocgid/synocgid.session.check.socket
/var/run/synocgid/synocgid.session.crypto.box.socket
/var/run/synocgid/synocgid.session.exist.socket
/var/run/synocgid/synocgid.session.getbyid.socket
/var/run/synocgid/synocgid.session.getid.socket
/var/run/synocgid/synocgid.session.get.socket
/var/run/synocgid/synocgid.session.resume.socket
/var/run/synocgid/synocgid.session.update.socket
/var/run/synocgid/synocgid.session.write.to.file.socket
/var/run/synocgid/synocgid.ssldecrypt.socket
/var/run/synoelasticd.sock
Are updates available? #
The Samba team has issued updates in versions 4.19.1, 4.18.8 and 4.17.12 to address this issue. Samba is widely used across many devices and virtual appliances, including common network attached storage (NAS) and file server functionality on Linux-based routers. Updates to all distributions, packaging formats, and commercial variants may take considerable time to become available.
How to find potentially vulnerable versions of Samba with runZero #
Samba v4 services can be found by navigating to the Service Inventory and using the following pre-built query:
_asset.protocol:smb protocol:smb product:samba _service.product:"Samba:Samba:4"
Results from the above query should be triaged to determine if they require patching or vendor intervention.
Vulnerable vfs_fruit Modules #
In February 2022 a vulnerability surfaced in Samba, which had the potential to provide unauthenticated remote code execution to attackers. Popular as Windows-compatible file sharing and print services software via the SMB protocol, Samba typically runs under Linux and other non-Windows OSes. You can usually find Samba on servers, appliances, desktops, and IoT devices. This out-of-bounds heap read write vulnerability (tracked as CVE-2021-44142 with a "critical" CVSS score of 9.9) resides in Samba's vfs_fruit module and was discovered-and-disclosed by security researchers Nguyễn Hoàng Thạch and Billy Jheng Bing-Jhong, along with Lucas Leong, and also separately by security researcher Orange Tsai.
For this vulnerability to be successfully exploitable by an attacker, the vfs_fruit module must be in use with default configuration settings for the fruit:metadata and fruit:resource options. The attacker must also have write access to a file share (which could allow guests and unauthenticated users, based on the configuration) that supports extended attributes (i.e., ea support = yes, which is the default for Samba).
While the list of potentially vulnerable vendors is lengthy, some formerly-vulnerable major Linux distributions have patches available, including Red Hat, Ubuntu, and SUSE. Samba maintainers have also released patched versions, and they recommened everyone upgrade to Samba version 4.13.17, 4.14.12, or 4.15.5 as soon as possible. In the event that upgrading is not possible, Samba maintainers offer a mitigation path: removing the "fruit" VFS module from the list of configured VFS objects in any "vfs objects" line in the Samba smb.conf configuration file.
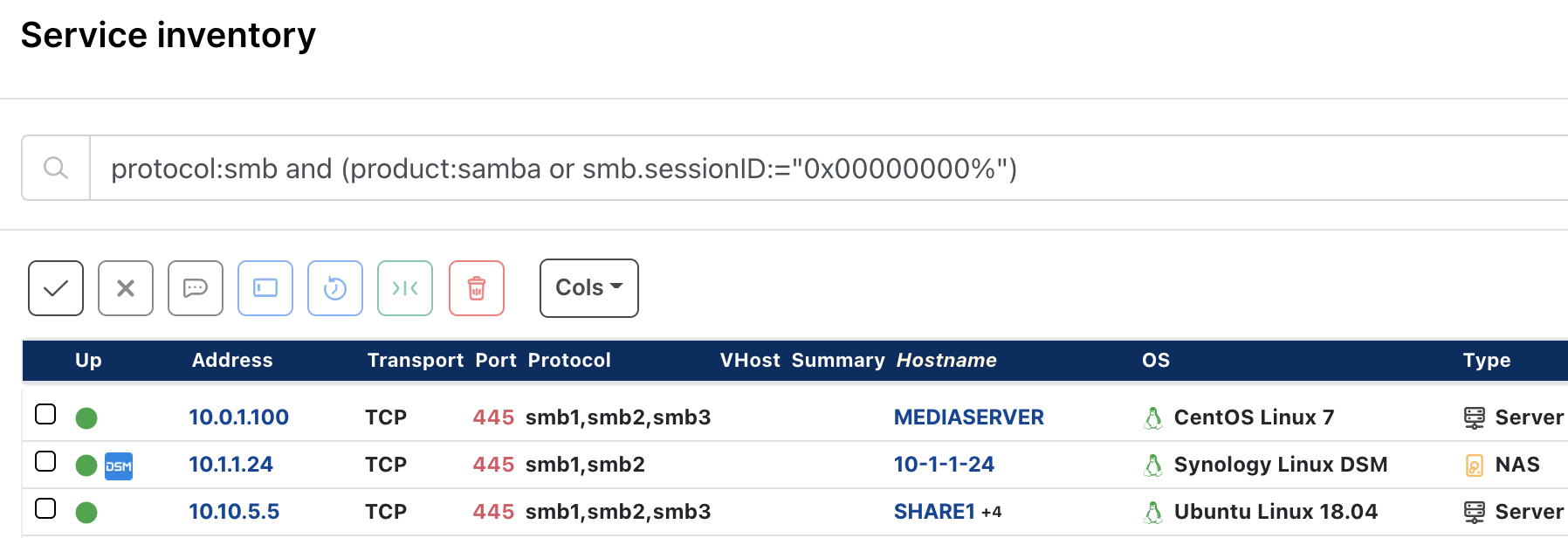
How to find potentially vulnerable Samba instances with runZero #
From the Service Inventory, use the following pre-built query to locate assets within your network that are potentially vulnerable:
protocol:smb and (product:samba or smb.sessionID:="0x00000000%")
As always, any prebuilt queries are available from your runZero console. Check out the documentation for other useful inventory queries.
















