What's new with runZero 3.2? #
- Integrations with Microsoft 365 Defender and Microsoft Intune
- Query and report on Active Directory users and groups
- Fingerprint updates
- User experience improvements
Complete visibility into your Microsoft assets #
Over the last few months, runZero has added support for Microsoft Azure cloud assets, Azure Active Directory and on-premise Active Directory users, groups, and assets, in addition to a community integration with Microsoft Sentinel. The runZero 3.2 release fills in the missing pieces by bringing endpoint visibility into the runZero inventory through new integrations with Microsoft 365 Defender and Microsoft Intune. runZero Enterprise users can view, search, analyze, export, and alert on attributes from the Defender and Intune metadata.
Mobile device management (MDM) solutions have become essential to organizations with a remote or transient workforce because of their ability to manage and secure devices even when they aren’t on the corporate network. Similarly, endpoint detection and response (EDR) platforms are commonly used on all sorts of assets for security monitoring and automatic response. While these IT management and security tools are an important part of many security stacks, reviewing what has been onboarded to those sorts of solutions only tells you about the devices that someone is already responsible for. Those lists can’t tell you about all the assets on your network that are unprotected or unmanaged, or all the assets disconnected from your network that haven’t been scanned.
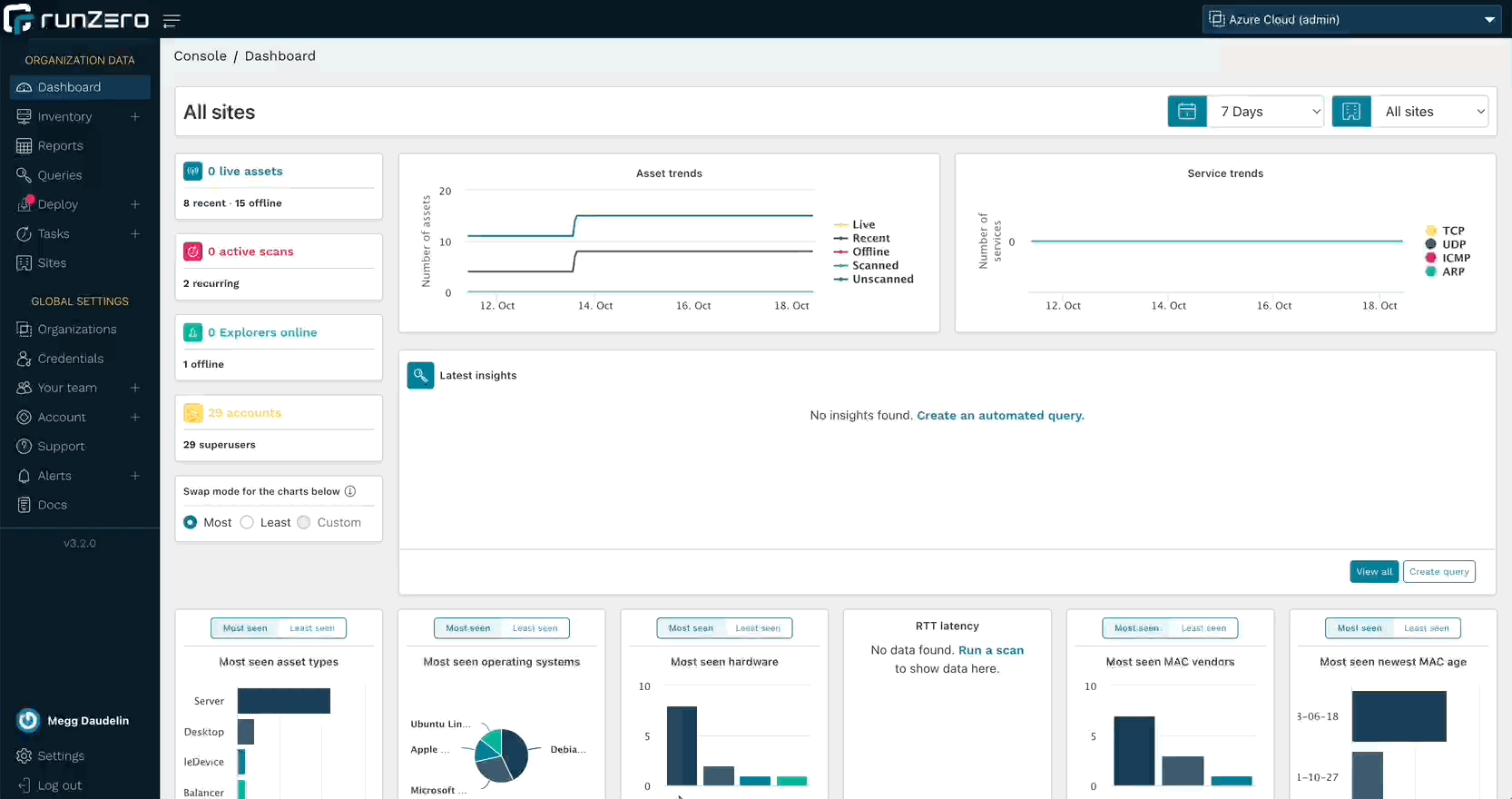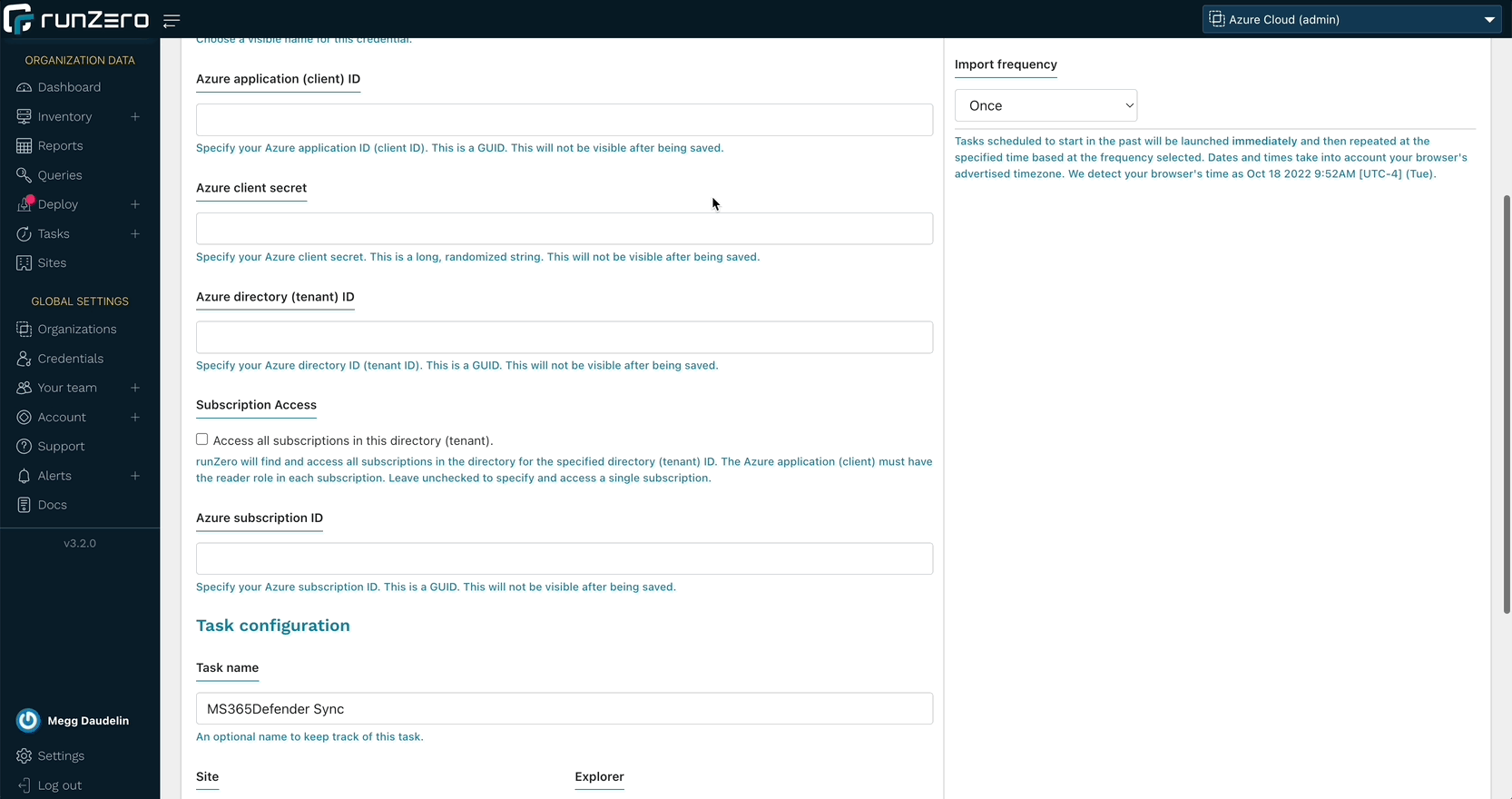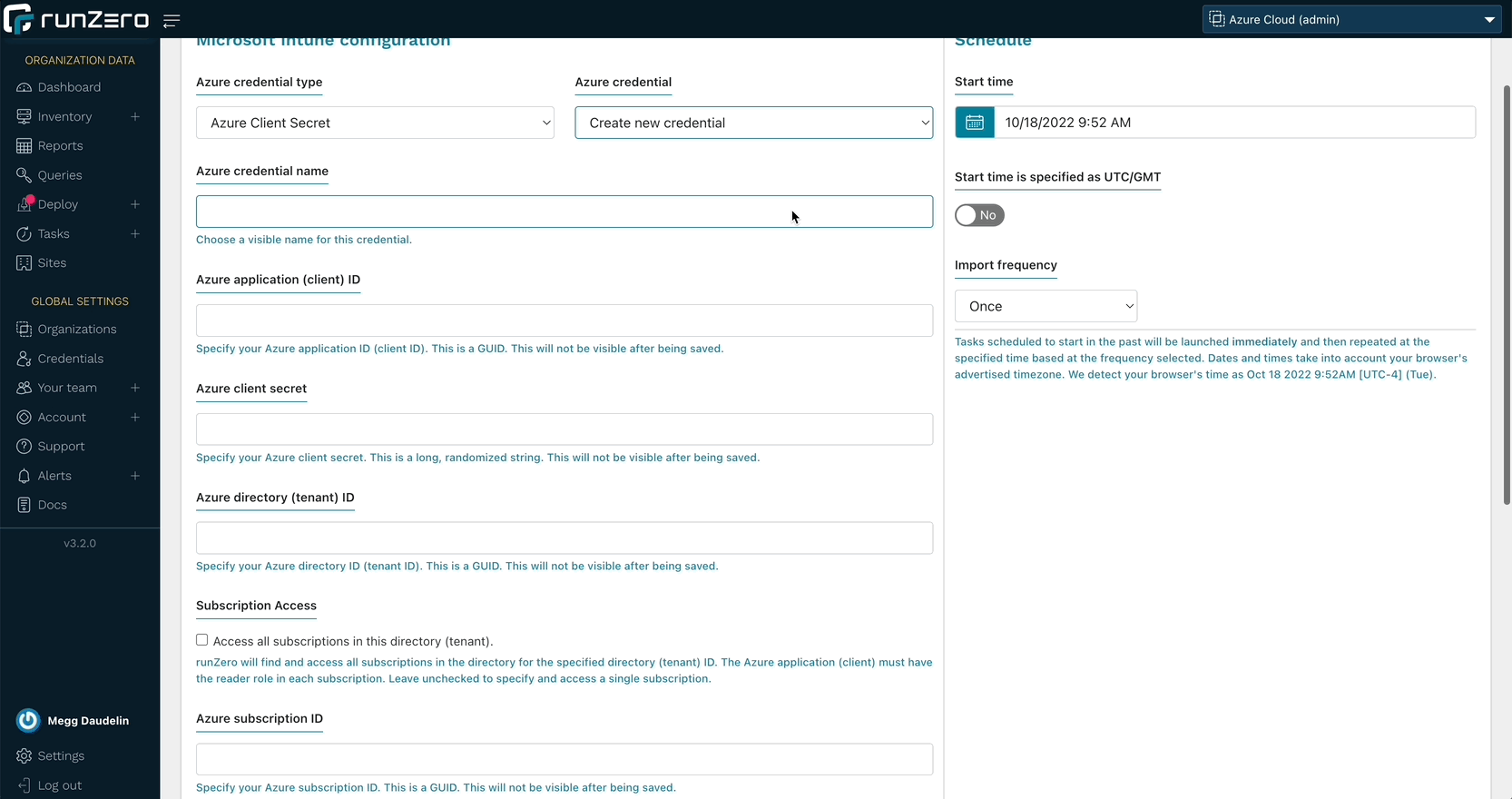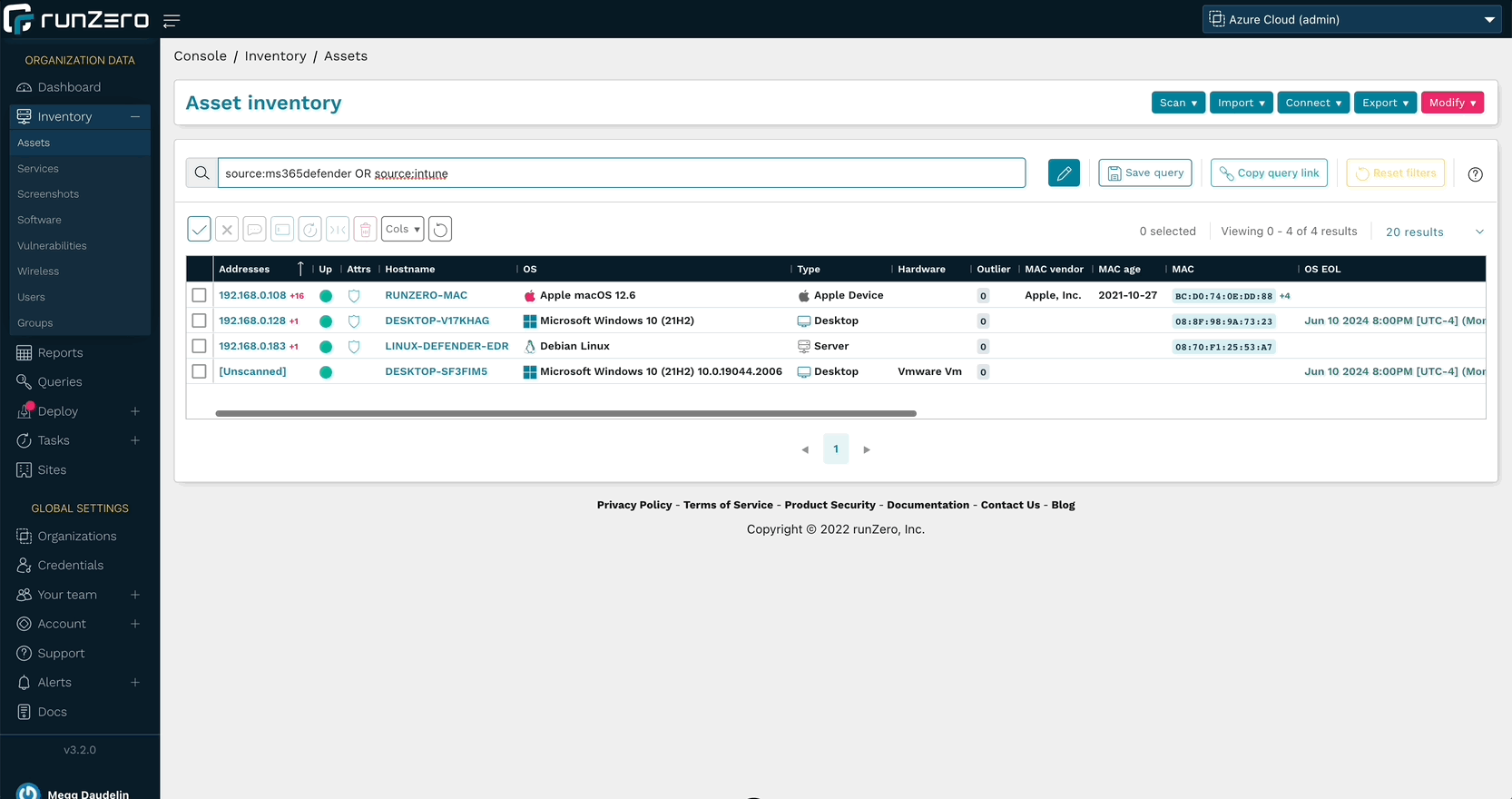
Unprotected and unmanaged devices are the bane of many organizations, and runZero can help you find them. Quickly identify unmanaged assets through a runZero query: filtering on source:runzero AND NOT (source:ms365defender OR source:intune) will return a list of assets that were found by your Explorers, but are not registered onboarded to Defender or Intune.
The inverse of this query can be used to ensure off-network assets are included in your asset inventory: (source:ms365defender OR source:intune) AND NOT source:runzero. This will give you a list of targets that may be missing from your scans and can ensure you’re gathering all the available network and asset data.
With runZero’s unmatched active network scanning and an ever-growing list of integrations, you’ll have a complete asset inventory at your fingertips. To get started, set up a connection to Microsoft 365 Defender or Microsoft Intune.
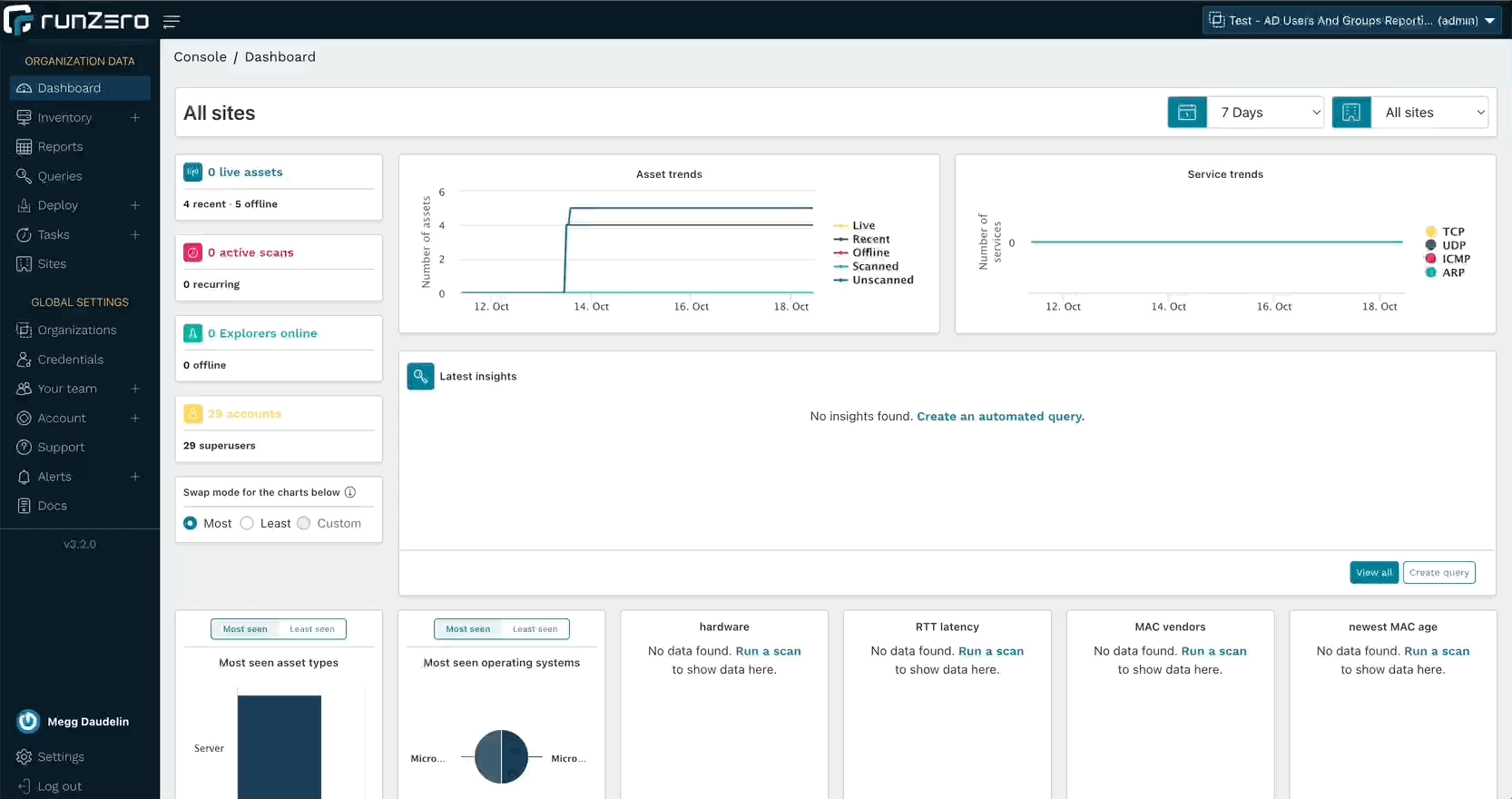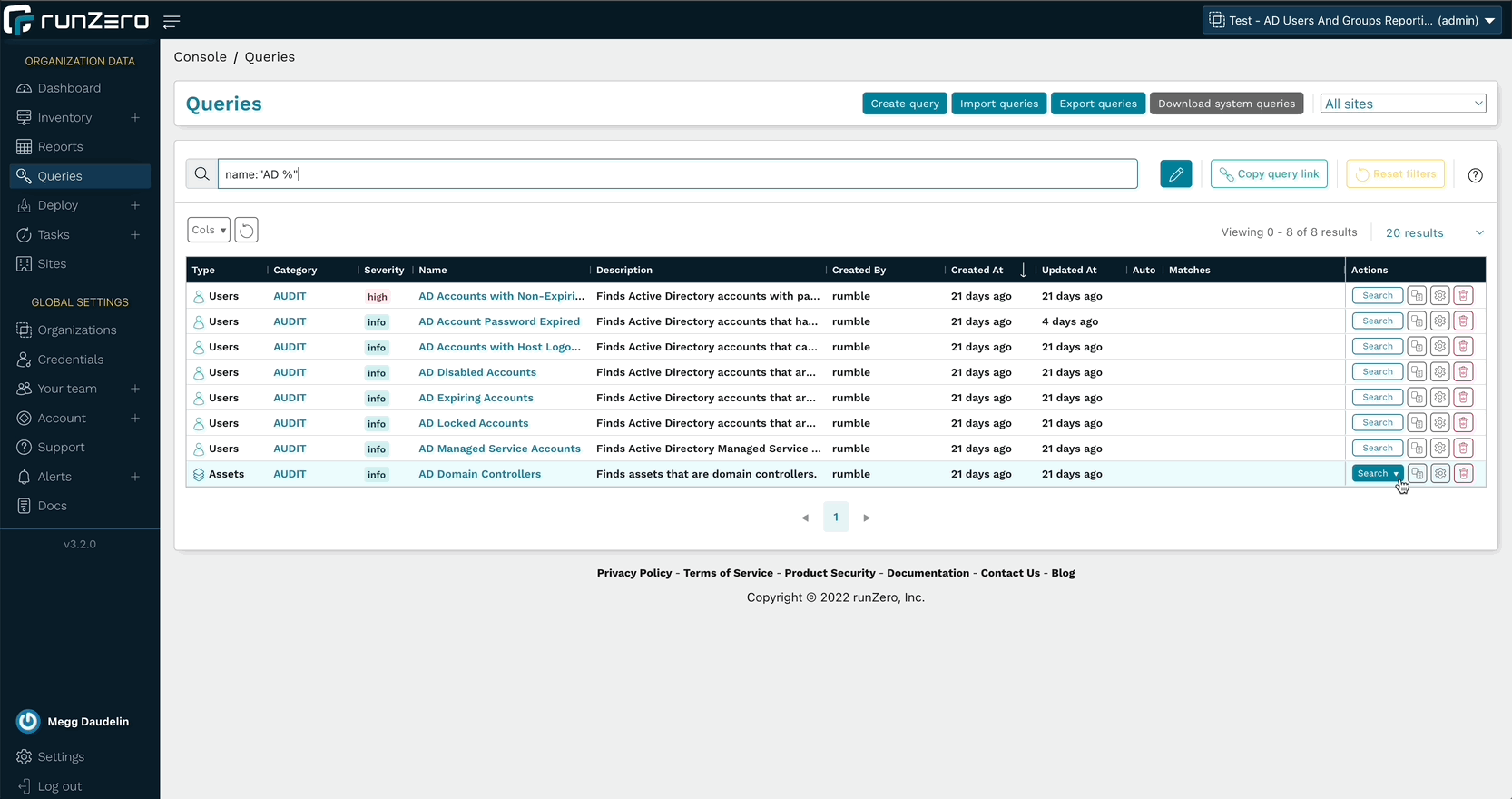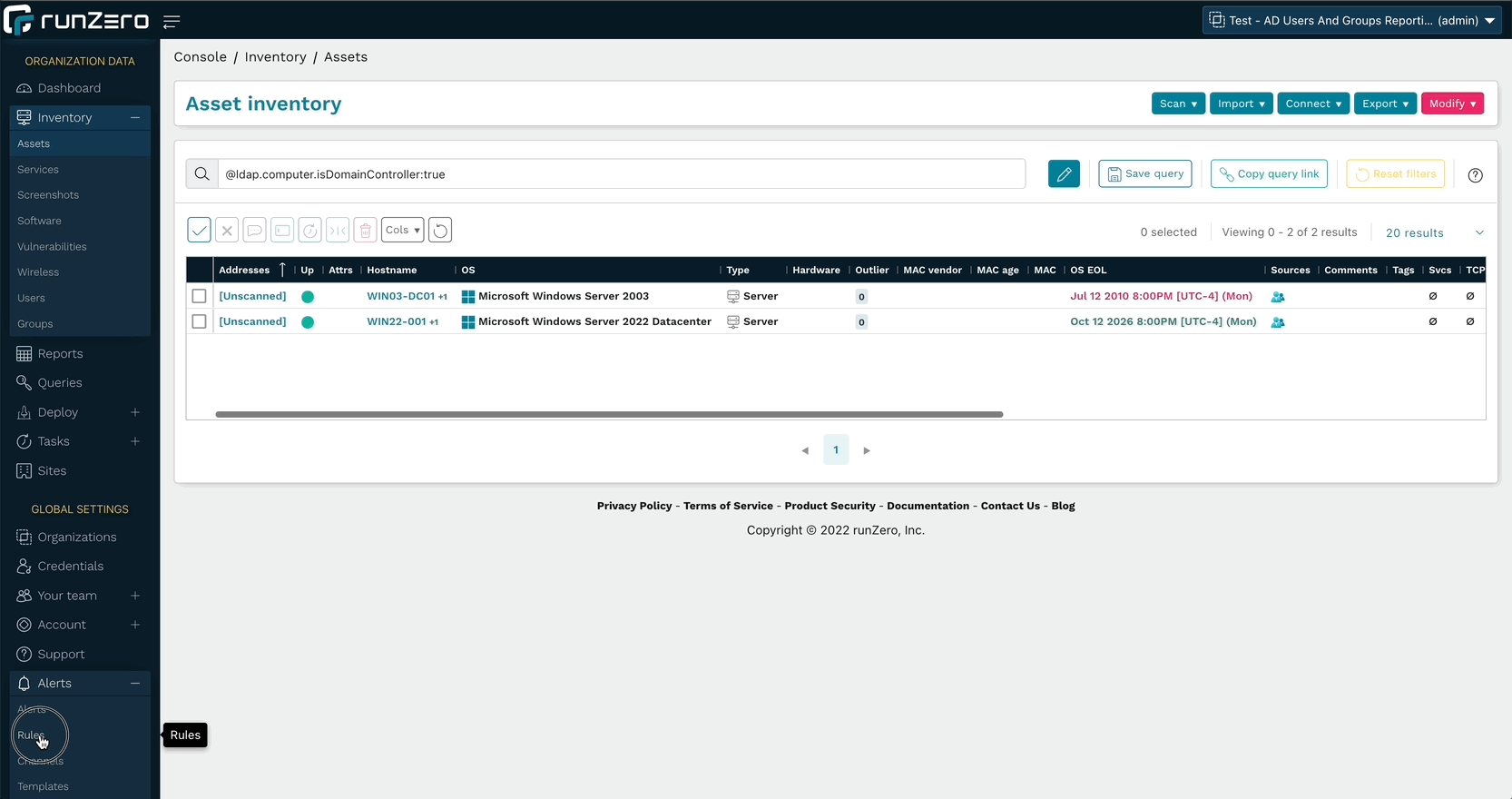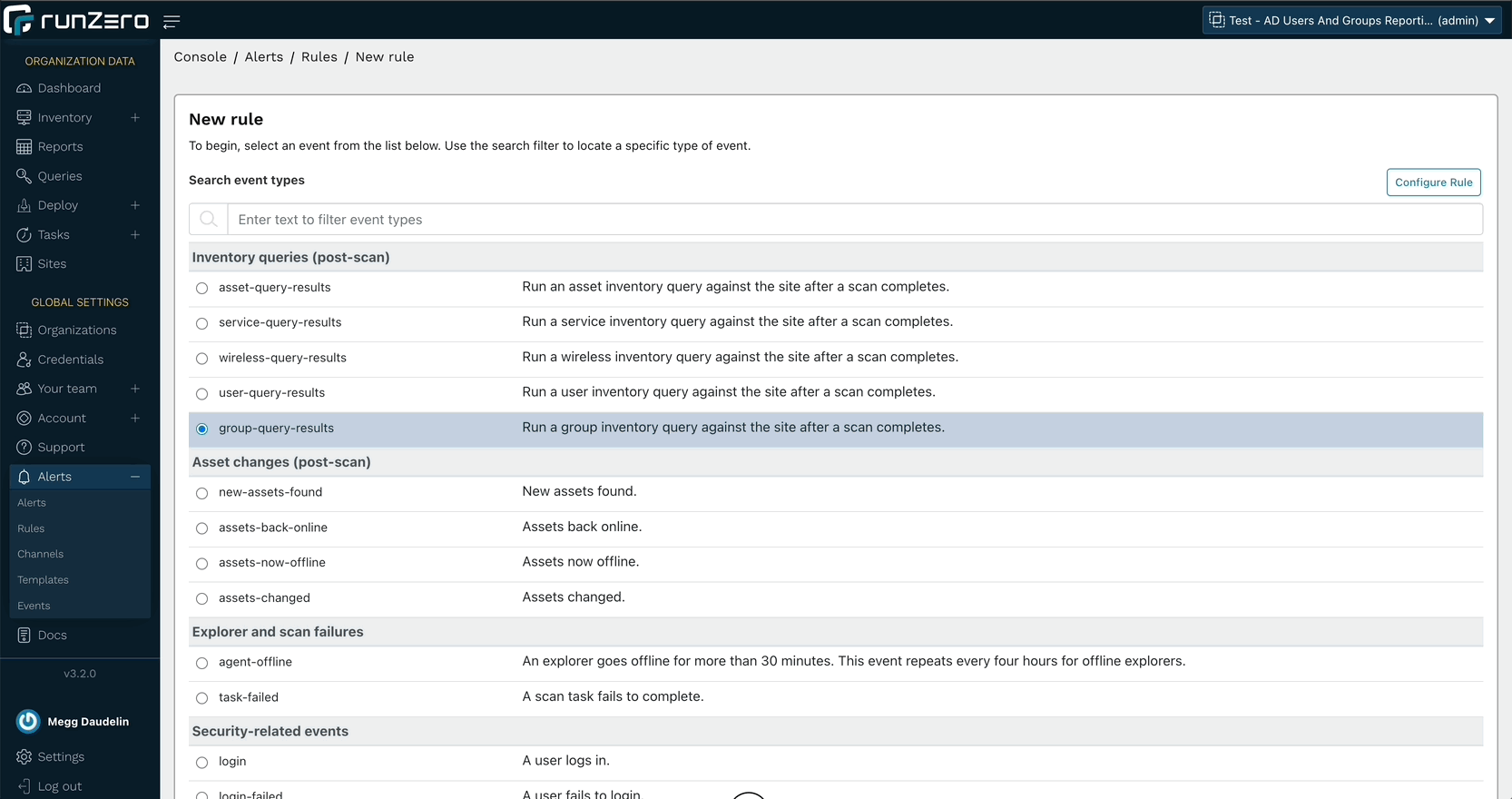
Query and alert on Active Directory users and groups #
In addition to running searches in the Users and Groups inventories, runZero Enterprise users can leverage the Azure AD or Microsoft Active Directory integrations to quickly find accounts that match specific parameters. Quickly identify expired, disabled, or locked accounts, as well as managed service accounts and accounts with non-expiring passwords. These queries are included in the Query Library and can also be used to create alerts.
The Organization Overview report has also been updated to include counts of users and groups for the whole organization as well as per site.
Run queries about AD users or create an alert rule to find accounts of interest.
Fingerprinting Microsoft assets #
runZero includes fingerprints for the metadata returned by the Microsoft integrations. This leads to more accurate operating system and hardware data within the runZero inventory. These fingerprints cover every aspect of the Microsoft ecosystem, from Azure cloud VMs to off-network endpoints running Microsoft Defender.
In addition to Microsoft fingerprints, runZero has also improved the coverage of Tenable.io and Nessus assets, public and private AWS AMI images, and IMAP services. Additional support was added for products by Advidia, Aiphone, Apple, ARRIS, Fortinet, Honeywell, iDevices, Lutron, Midnite Solar, Netgear, Sapling, SEH, Silex, Yeelight.
User experience improvements #
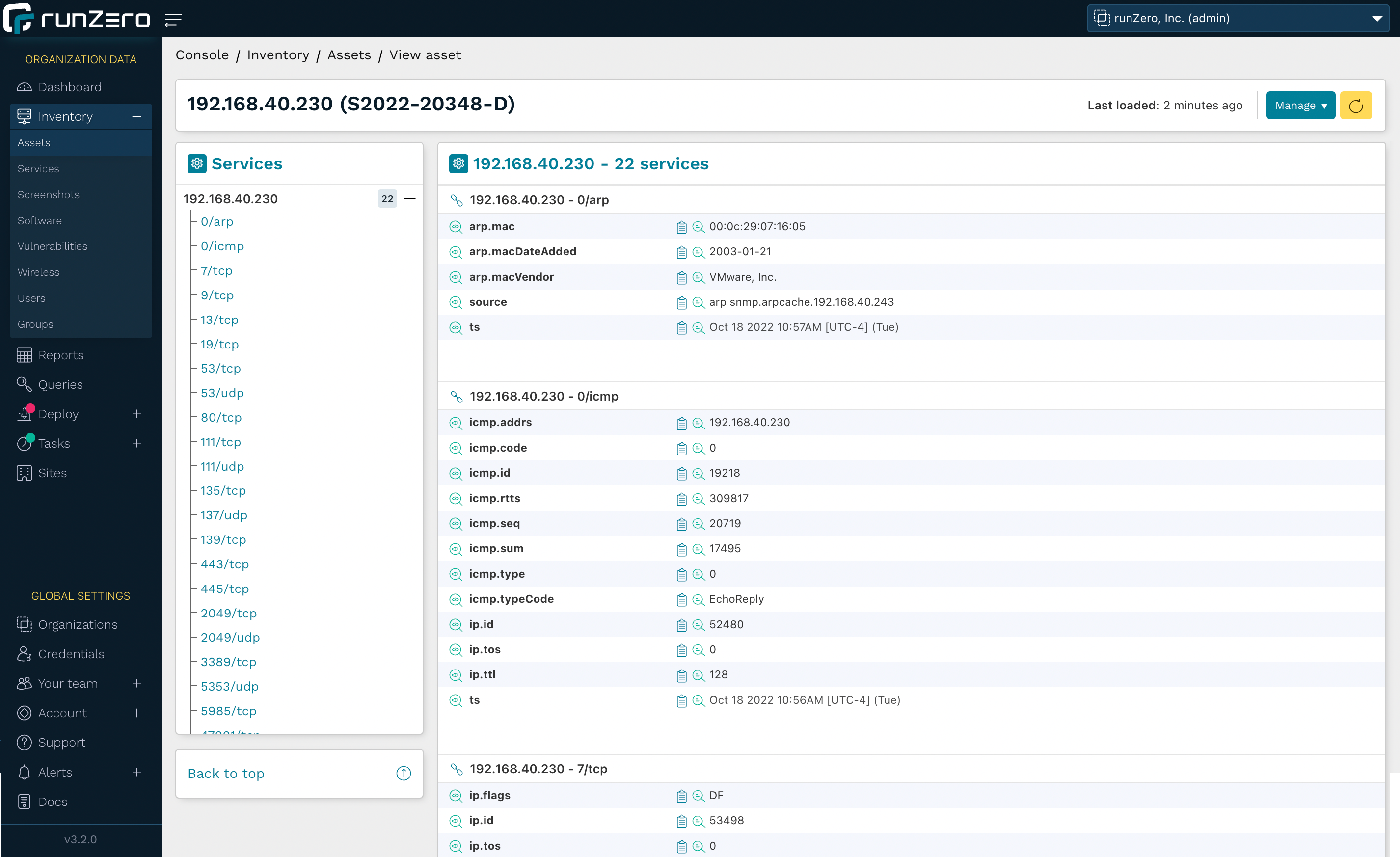
The 3.2 release includes several changes to the user interface to improve the performance of the runZero console, as well as a change to how page navigation transitions happen. As a result, the pages will load faster as you move between sections like the inventories and asset details pages. Additionally, the asset details page provides better performance and efficiency when loading all of the details for an asset.
Enhancements have also been added to make using the data easier than ever. On the asset details pages, the "last loaded" timestamp indicates when the asset details were loaded, and a refresh button has been added to be able to quickly reload the data without refreshing the whole webpage. The Vulnerabilities and Software tables on these pages now perform and load faster. Additionally, the navigation list for the Services table now displays the protocols and ports as a navigation tree to make finding the information you're looking for simpler and a button has been added to quickly bring you back to the top of the page from the services table. As we continue to make progress on the architectural modernization of the runZero Console, you will see improvements to the performance and user experience of the product.
Release notes #
The runZero 3.2 release includes a rollup of all the 3.1.x updates, which includes all of the following features, improvements, and updates.
New features #
- runZero Enterprise customers can now sync assets from Microsoft 365 Defender.
- runZero Enterprise customers can now sync assets from Microsoft Intune.
- Fingerprint updates.
Security fixes #
- Three stored cross-site scripting vulnerabilities were identified and fixed as part of our annual third-party security assessment.
- A bug that could lead to stored cross-site scripting in the scan templates view was fixed. This issue could be exploited by an authenticated, but unprivileged user to take over the session of another authenticated user.
- A bug that could lead to stored cross-site scripting in the SSO group mappings view was fixed. This issue could be exploited by an authenticated superuser to take over the session of another authenticated user.
- A bug that could lead to stored cross-site scripting in the team view was fixed. This issue could be exploited by an authenticated, but unprivileged user to take over the session of another authenticated user.
Product improvements #
- SNMPv2 options have been moved to the
Probestab (now labeledProbes and SNMP). - The toggle switch to use or not use SNMP now correctly reflects whether it is overridden by the "Use defaults" option on the
Probestab. - The asset details pages now include a "last loaded" time indicator and the ability to refresh the page data.
- Alert notifications, user invitations, and password reset emails are now sent from the
runzero.comdomain name instead ofrumble.run. - The
rumblectlutility now has a diagnostics command to run or save a diagnostic script for self-hosted customers to collect information for runZero support. - Inventory pages now offer “all” and “none” column visibility selection options.
- The search keyword os_eol_expired is now supported on the Assets inventory.
- The rumblectl command can now be used with self-hosted deployments to configure additional superusers.
- Email notifications are now enabled for non-recurring Organization Overview reports.
- Relative time searches now accept negative numbers.
- Scan tasks and templates now allow empty SNMPv1 and SNMPv2 community strings.
- Credential validation has been improved to prevent common misconfigurations.
- Support for Explorer hosts running virtual machines has been improved.
- MAC vendor display behavior on inventory datagrids has been improved.
- Tooltips on datatable icons have been improved.
- Changes to directory users and groups are now included in the task change report.
- Error messages related to API tokens have been improved.
- Asset exports now filter subnet results to those containing the assets’ addresses.
- Improved LDAP connector and probe logging.
- Added group_count keyword to Users search.
- Improved grouping of inputs in connector forms.
- Search keyword has_group is now supported on the Users page.
Performance improvements #
- The asset details pages have been redesigned for improved performance.
- Improved performance of asset exports with many subnets.
- Improved loading times of the directory groups inventory page.
- Improved loading times of the inventory screens, including multi-page selection.
Fingerprinting changes #
- Improved Active Directory collected data and fingerprint coverage.
- Improved LDAP attributes for Active Directory objects.
- Added new queries for quickly surfacing various Active Directory scenarios.
- Improved fingerprinting coverage of Azure AD assets.
- Improved fingerprinting coverage of Tenable assets.
- Improved fingerprinting coverage of public AWS AMI images.
- Added custom fingerprint support for private AWS AMI images.
- Improved fingerprinting coverage of IMAP services.
- Additional support added-or-improved for products by Advidia, Aiphone, Apple, ARRIS, Fortinet, Honeywell, iDevices, Lutron, Midnite Solar, Netgear, Sapling, SEH, Silex, Yeelight.
Integration improvements #
- Recent users from Microsoft Intune, SentinelOne, and CrowdStrike are now included on the asset details page.
- The Azure AD integration now imports additional assets and no longer requires a Microsoft Intune license.
- The Azure AD integration can now be configured to optionally import assets, users, and groups.
- The Active Directory integration service options have been adjusted for consistency.
- Directory users and groups can now be included in custom queries.
- The Organization Overview report now contains summary information for directory users and groups when present.
- The Tenable.io integration now supports a configurable API URL.
- The Active Directory integration now supports optional import of assets, users, and groups.
- The minimum TLS version supported by new Active Directory credentials has been increased from TLS 1.0 to TLS 1.2, with a configurable option to support older TLS versions.
- The handling of Qualys concurrency and rate limiting has been improved.
Bug fixes #
- A bug that could prevent repeated import of task data that includes directory users and groups has been resolved.
- A bug that caused subnet sampling and screenshots to be enabled for all scan tasks has been resolved.
- A bug that could prevent modifying the maximum concurrent scans setting was resolved.
- A bug that could result in an inaccurate task count on the credentials page was resolved.
- A bug that could result in inaccurate searches by credential on the tasks page was resolved.
- A bug that could result in inaccurate reporting of credential reuse was resolved.
- A bug that could cause certain browser extensions to prevent configuring scans was resolved.
- A bug that could prevent reuse of SNMP credentials for recurring scans was resolved.
- A bug that could prevent initializing a scan in some cases was resolved.
- A bug that prevented recurring scans from being saved in some cases was resolved.
- A bug that prevented the first_seen timestamp from being set has been fixed.
- A bug that could cause large Qualys imports to fail has been resolved.
- A bug that prevented import of Azure AD users and groups when missing an active Intune license has been resolved.
- A bug that could result in partial import of Azure AD users and groups has been resolved.
- A bug which prevented the report.changed value from working in notification rule templates has been fixed.
- A bug that prevented the use of client tokens to authenticate to the API has been fixed.
- A bug that could cause insight queries for hosted zones to fail has been resolved.
- A bug in the Shodan integration asset-mode query has been resolved.
- A bug that could cause MAC vendor names to be cut off in datagrids has been resolved.
- A bug that could result in missing Shodan services has been resolved.
- A bug that incorrectly imported Active Directory Managed Service accounts as assets has been resolved.
- A bug that could cause the Switch Topology report to not show all switches in certain situations has been resolved.
- A bug that could result in a 500 error when exporting assets from sites with many assets and/or subnets has been resolved.
- A bug that could result in UI elements becoming unresponsive has been resolved.
- A bug that could prevent some service values from being saved has been resolved.
- A bug that could result in all subnet tags being applied to exported assets has been resolved.
- A bug that could result in missing Shodan services has been resolved.
- A bug that could cause Azure AD imports to fail for certain configurations has been resolved.
- A bug that could cause excessive export sizes has been resolved.
- A bug that could obscure task errors from the task log has been resolved.
















