What's new in Rumble 2.4? #
-
Integrations - Rumble's integration efforts to date have been focused on bringing network inventory to platforms like Splunk and ServiceNow. The 2.4 release expands this to inbound integrations, with initial support for cloud assets via AWS EC2 APIs and endpoints via the Miradore MDM API. These integrations deliver better visibility and centralize your cloud and on-premises asset information.
-
Self-hosted improvements - The Rumble self-hosted platform now supports Red Hat Enterprise Linux (RHEL) and CentOS in addition to LTS versions of Ubuntu. The self-hosted CLI has been overhauled with new features and better help output.
-
Guided tour - New Rumble users are welcomed with a guided tour that walks through the steps needed to get immediate network visibility.
In addition to all the new goodness, this release also includes a rollup of all the 2.3.x updates. Keep reading to learn more about some of new 2.4 capabilities or check out the detailed release notes at Rumble 2.4 changelog.
Cloud, endpoints, and network assets–all in one place #
Our new Amazon AWS EC2 and Miradore MDM integrations enable you to incorporate asset data from your cloud and endpoint devices into Rumble. As a result, you'll have a more unified, comprehensive view of all the assets across your organization. You can leverage this centralized view to find, investigate, and track assets that you haven't discovered with Rumble yet. Assets that Rumble already knows about can be enriched with additional details such as associated users, instance types, external IP addresses, and more!
Miradore MDM
Ever wondered, "How can I scan home devices if they're not on the VPN?" Or "Which devices on my network are missing an MDM agent?" With the Miradore integration, you can compare your Rumble data against your Miradore data to identify any discrepancies in your asset inventory, and vice versa.

To add Miradore asset data to Rumble, you will need to set up and activate a connection to your Miradore instance by providing the hostname and Miradore API key.
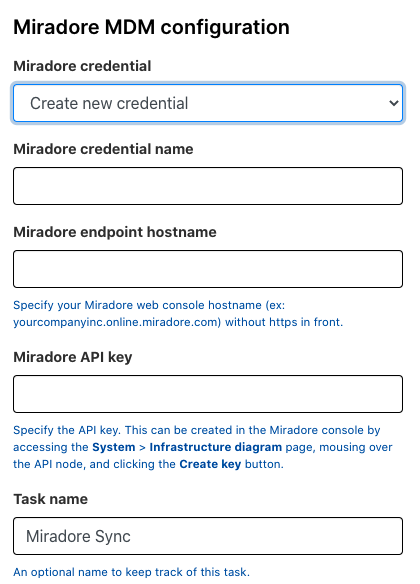
Activating the connection runs the import on a recurring schedule. This import will load all active Miradore devices into the Rumble inventory. Assets identified through Miradore will show a new icon in the Sources column of the inventory view and have a new attribute table populated with Miradore-specific information. These attributes include fields like the device name, model, OS version, serial number, UDID, and user name. These fields are searchable and can be used to generate reports like any other attribute.
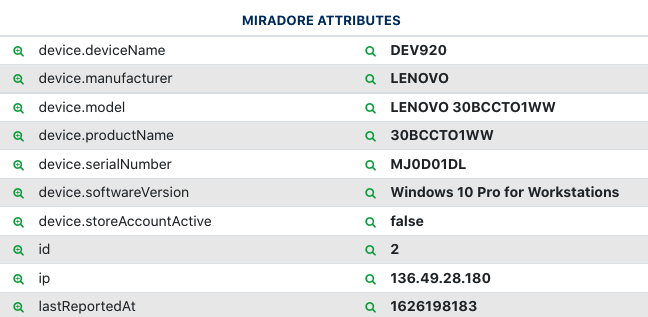
Amazon Web Services EC2 #
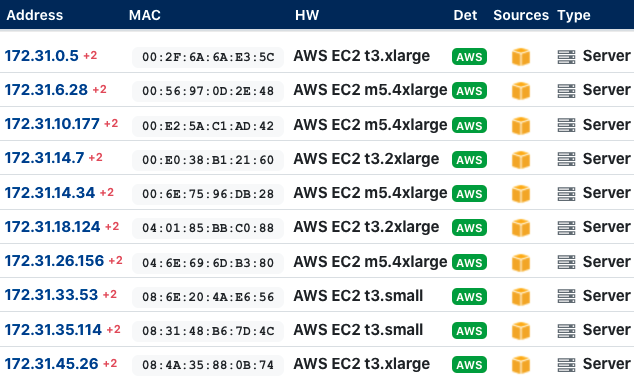
The new AWS EC2 connector brings in all running EC2 instances, across multiple regions, into the site you choose. In contrast to the EC2 probe in the Rumble scanner, this connection brings in assets regardless of location, region, or reachability from a deployed explorer, providing better visibility across your cloud environment. This integration allows you to quickly identify how many EC2 instances are running, in what region, under what account, and with what SSH keys and AMIs.
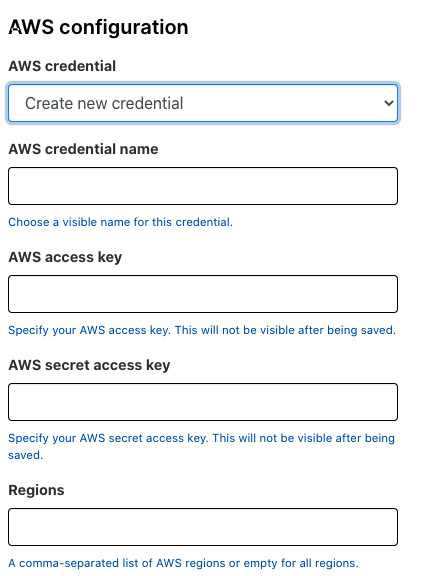
To add AWS asset data to Rumble, you will need to add and activate a connection to your AWS API by providing the AWS region, Access Key ID, and Secret Access Key. This credential should have access to the AmazonEC2ReadOnlyAccess policy.
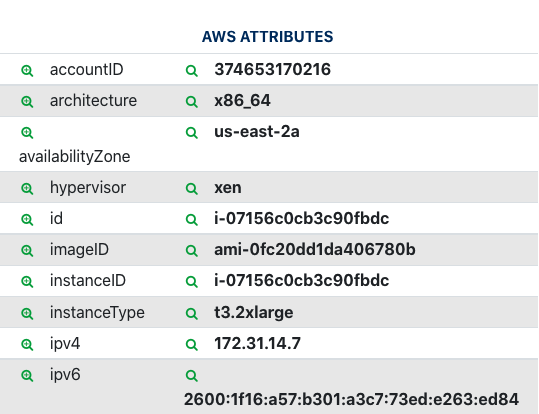
After a successful import, EC2 assets will be shown with the AWS icon shown in the Sources column. The asset attributes will include AWS and EC2-specific fields such as the architecture, availability zone, hypervisor, ID, instanceID, private and public IP, region, state, and VPC.
Centralized credential management #
As part of our efforts to expand third-party integrations, Rumble now has a central area to store and manage credentials. Credentials can be reused across organizations without exposing their secrets to Rumble users.
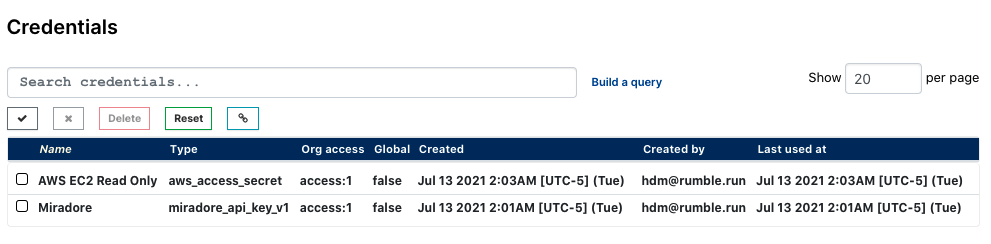
Each credential is assigned a type that associates it with a specific connector. Based on the current integrations available, Rumble has credential types for AWS EC2 and Miradore MDM. Credentials can be allocated globally or assigned on a per-organization basis. Going forward, we plan to expand this to cover credentials used by scans as well (SNMP v2, v3, etc).
Deploy Rumble on RHEL and CentOS #
The self-hosted version of Rumble now supports RHEL 7 64-bit and RHEL 8 64-bit, as well as the related CentOS distributions. For enterprise customers interested in learning how to deploy Rumble on-premises, we recently published this article on how to self-host our platform.
In addition to the new self-hosted documentation, we've also added help in the CLI. Running --help that shows all commands and help for them. Adding the -h flag to a specific command will show the subcommands and its corresponding documentation.
A guided tour through Rumble #
Something we've observed with some of our new users: getting started wasn't intuitive. We've added a guided tutorial in-product to help our first-time users deploy Rumble and start seeing data in their inventory faster. The tutorial goes through setting up an explorer, running a scan, and exploring the asset inventory. Hopefully, this helps everyone get value out of Rumble as quickly as possible.
Release notes #
Read the Rumble 2.4 changelog to see all the improvements and updates in this release.
Try Rumble #
Want to try runZero? Sign up for a free trial to try out these capabilities for 21 days.
















