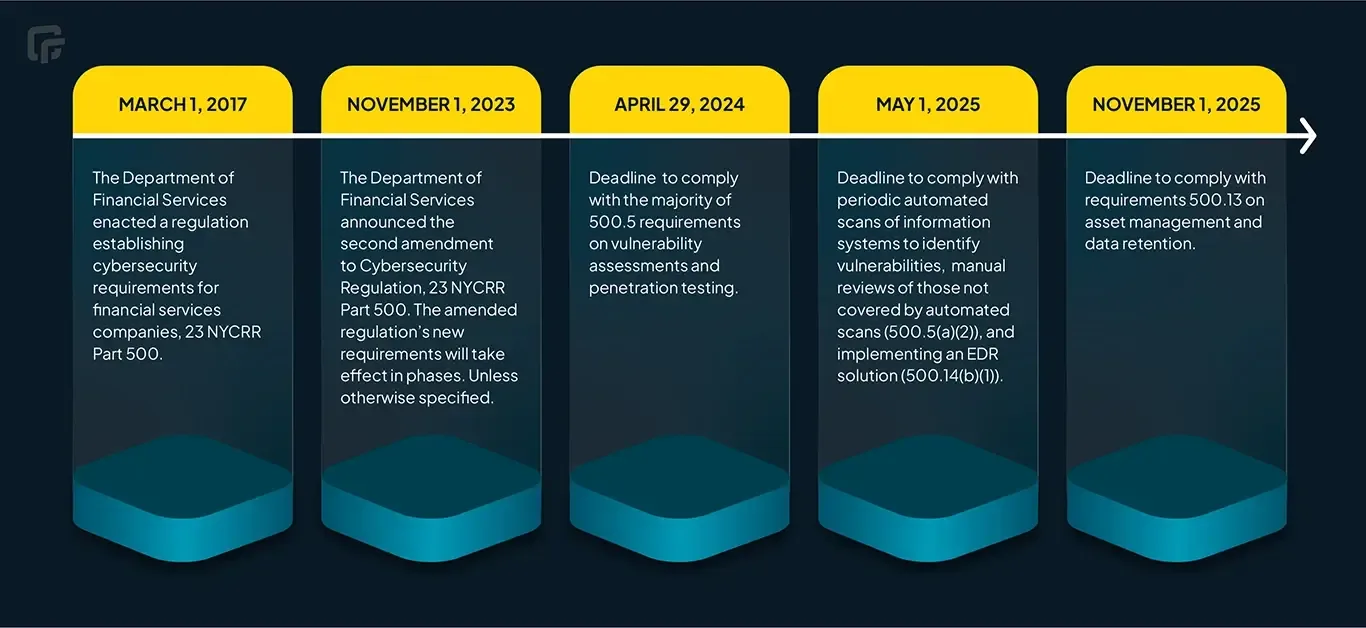
Is your business prepared for the approaching deadlines for complying with the latest version of the NYDFS Cybersecurity Regulation (23 NYCRR 500)?
Here, we recap the regulation’s key requirements, and the newest requirements from its second amendment in November 2023.
Then, we focus on how you can ensure you’re ready for pending compliance deadlines for two important aspects of these new requirements: vulnerability assessments (deadline: April 2024) and asset management (deadline: November 2025).
What is the 23 NYCRR 500 at a glance? #
23 NYCRR 500 is a set of cybersecurity requirements imposed by the New York State Department of Financial Services (NYDFS) in 2017. It is also known known as the DFS Cybersecurity Regulation or NYDFS 500. These requirements apply to all ‘Covered Entities’. At a high level, that means financial institutions and financial services companies licensed or authorized to do business in New York.
Why is the regulation for one state so important? #
Well, many financial institutions do business in New York. 23 NYCRR 500 is one of the most stringent cybersecurity regulations in the United States and has been adopted by other states as a model.
The main goals of 23 NYCRR 500 are:
- Protecting customer data and the information technology systems of financial institutions. This includes social security numbers, account numbers, and credit card information.
- Proactively addressing cybersecurity risks. Covered Entities must conduct regular risk assessments and implement controls to mitigate identified risks.
- Improving the overall cybersecurity posture of the financial services industry in New York.
Key requirements of 23 NYCRR 500 include:
- Developing and implementing a cybersecurity program.
- Appointing a Chief Information Security Officer.
- Conducting regular penetration testing and vulnerability assessments.
- Maintaining an audit trail.
- Implementing multi-factor authentication.
- Encrypting sensitive data.
- Having a data breach notification plan.
23 NYCRR 500’s second amendment #
The second amendment to 23 NYCRR 500 was finalized on November 1, 2023. The new requirements include:
- Boards and senior officers must now have “sufficient understanding of cybersecurity-related matters” to exercise appropriate oversight.
- Covered entities must submit an annual compliance certification or acknowledgment of material non-compliance to the NYDFS Superintendent.
- Continuous improvement in risk assessments, requiring updates based on changes to the entity, technology, or threat landscape.
- Expanded notification requirements.
- Automated scanning and manual review: New requirements mandate periodic automated scans of information systems, and manual reviews of systems not covered by scans, to identify, analyze, and report vulnerabilities.
- Enhanced asset inventory: More robust written policies and procedures are required for creating and maintaining an asset inventory, including tracking key information and updating/validating it at defined intervals.
- An endpoint detection and response solution to monitor anomalous activity, including but not limited to lateral movement.
In this article, we’re focusing on the last three requirements.
Vulnerability assessments and penetration testing #
Financial institutions must comply with requirement 500.5 on vulnerability assessments and penetration testing.
Specific requirements of 500.5 on vulnerability assessments and penetration testing:
- Compliance is required by April 29, 2024
- Written policies and procedures for vulnerability management
- Processes to document, analyze, and report identified vulnerabilities.
- Penetration testing at least annually, or more frequently based on risk.
- Vulnerability assessments are conducted at a frequency aligned with risk and after any material change to a system.
- Testing and assessment of all critical systems and those containing sensitive data.
- Timely remediation of identified vulnerabilities.
- Compliance is required by May 1, 2025.
- Periodic automated scans of information systems to identify vulnerabilities.
- Manual reviews of systems not covered by automated scans.
In short, you need to scan for vulnerabilities continuously, or at least as often as your risks require. If a system can’t be scanned automatically, it must be reviewed manually. You can’t simply ignore it.
Once uncovered, vulnerabilities need to be remediated in a timely fashion. You must also conduct penetration tests at least once a year.
Asset management and data retention #
By November 1, 2025, financial institutions must comply with requirement 500.13 on asset management and data retention.
Specific requirements of 500.13 on asset management:
- Written policies and procedures for creating and maintaining a complete, accurate, documented asset inventory of their information systems.
- Key information tracking: The inventory must track key information for each asset, including:
- Owner
- Location
- Classification or sensitivity
- Support expiration date
- Recovery time objectives
- Policies and procedures must define the frequency of updating and validating the asset inventory.
- Secure disposal of non-public information.
In short, you need a comprehensive and up-to-date asset inventory for all information systems, which includes specific data.
By the way, when 23 NYCRR 500 says ‘information systems, ’ it doesn’t mean just laptops and servers.
According to 500.1(e) of the original regulation, information systems include “any specialized system such as industrial/process controls systems, telephone switching and private branch exchange systems, and environmental control.”
That means IoT and OT devices as well as phones, IP cameras, building automation, and even your HVAC systems.
EDR for larger institutions #
Companies classified as “Class A” must comply with requirement 500.14(b)(1) by implementing an endpoint detection and response solution to monitor abnormal activity, such as lateral movement. “Class A” institutions are those with over 2,000 employees and grossed over $20M for each of the last two years, or those that grossed over $1B for each of the last two years. Compliance is required by May 1, 2025.
How runZero can help you achieve compliance #
To comply with the new regulations, you must have the correct tools and processes. runZero provides a single, consolidated solution to help you comply with the regulatory requirements on asset inventory and vulnerability assessments.
Asset inventory #
Let’s start with asset inventory, since that’s a prerequisite for vulnerability enumeration. After all, you can’t scan what you don’t know.
The good news is that managed devices are easy to inventory. You can get a complete list of assets an organization already knows by integrating via APIs with other sources in their tech stack.
What’s likely to cause gaps in a financial institution’s asset inventory is the Achilles heel of asset discovery — unmanaged devices. These include rogue devices, orphaned assets, and shadow IT. For this 20 in the 80:20 rule, you need unauthenticated active scanning.
Under 500.13, IoT and OT devices must be inventoried as well. Even financial institutions may have OT devices through smart building automation. runZero can inventory those as well with its unauthenticated active scanner.
runZero customers have seen great success with using a combination of API integrations and unauthenticated active scanners to learn more about the assets they already knew about, and discover the assets, and even subnets, they didn’t already know.
Although fulfilling the requirements in 500.13 isn’t as simple as documenting: ‘use runZero’, it’s helpful to be able to achieve this asset inventory with a single solution. You won’t need separate documentation for different device types or environments (e.g. network, mobile, cloud).
One of runZero’s advantages is that it tracks all the details that matter to security teams: hardware, software, services, vulnerabilities, insecure configurations, security controls, and user/ownership. Specific requirements of 500.13, like ownership and support expiration date, are both provided as top-level asset details. Location, classification and RTOs are supported through tags that can be applied based on flexible criteria.
Vulnerability enumeration #
Even though requirement 500.5 allows for manual review of systems that fall outside automated scans, obviously you’ll want to keep the manual work to a minimum since exceptions always take an inordinate amount of time.
runZero provides three vulnerability management capabilities that are relevant here:
- Native capabilities to identify assets potentially vulnerable to a CVE, without a rescan.
Based on asset detail, runZero uses proxy indicators that point to the presence of a vulnerability. This allows a security team to identify potentially vulnerable devices without waiting for a rescan of the network. This capability goes a long way towards helping with timely remediation, especially for new in-the-wild vulnerabilities.
- Native capability to identify assets that have insecure configurations.
Common best-practice failures include reusing SSH keys, using insecure protocols like telnet, and outdated configurations like expired certificates on web servers. Such vulnerabilities — that would not be included in the National Vulnerability Database — are just as dangerous for organizations as vendor-caused vulnerabilities.
- Native capability to identify outliers, which is highly correlated with vulnerable devices.
Typically, your security program and business continuity plan will cover common devices first. Those are the devices that will have security controls and proper security governance.
It’s the devices you have only one or a few of that often fall through the cracks. As such, they often don’t have up-to-date security controls, if any at all.
By our reckoning, there is a high correlation between vulnerable devices and outliers. Identifying one can lead to finding the other, which helps to prioritize targets for remediation before compromise.
- Integration with vulnerability scanners for prioritization and exposure context
runZero integrates with vulnerability scanners like Qualys, Rapid7, and Tenable to bring their findings into a consolidated view of your exposure.
Not only does this bring on-box vulnerabilities into runZero, but it also augments runZero’s vulnerability prioritization capabilities. Over 50% of vulnerabilities are considered highly or critically severe, but only 5% are exploited. Security teams must prioritize fixing the most risky and critical assets. runZero can prioritize exposure issues using asset details, network location, ownership, attack surface context, and criticality. With data from vulnerability scanners, you can also prioritize using exploit status (is it being used in the wild) and exploitability (has exploit automation been developed for it).
Most importantly, runZero learns and analyses this information continuously. This allows you to proactively and quickly identify vulnerabilities across all assets in an automated fashion to support timely remediation.
Ensuring EDR coverage #
Many organizations struggle with covering their endpoints with EDR due to gaps in their inventory. They specifically overlook orphaned devices, rogue assets, and shadow IT - servers, laptops, and desktops are not protected by EDR. This could be because someone forgot to install it or nobody knew the machine existed. runZero can integrate with your EDR solution. Compare your EDR install base to its inventory and list endpoints missing your EDR. This makes it easy to develop a remediation list to comply with requirement 500.14(b)(1).
Wrapping up #
Financial institutions need to act now to get the right policies, processes, and tools in place before the pending NYCRR 500 compliance deadlines come into effect. runZero provides a useful tool in your arsenal to ensure you meet regulatory requirements on asset inventory and vulnerability enumeration — start your free trial today.
















