
A proactive security program begins with knowing what is on your network through a comprehensive asset inventory. Instead of searching for a fit-for-purpose solution, many organizations use their existing configuration management database or CMDB for asset inventory. On the surface, it makes sense. CMDBs are designed to track data relating to managed IT assets, such as routers, switches, or servers. CMDBs should contain all the configuration items (CIs) needed for IT service management (ITSM), IT asset management (ITAM), or IT operations management (ITOM).
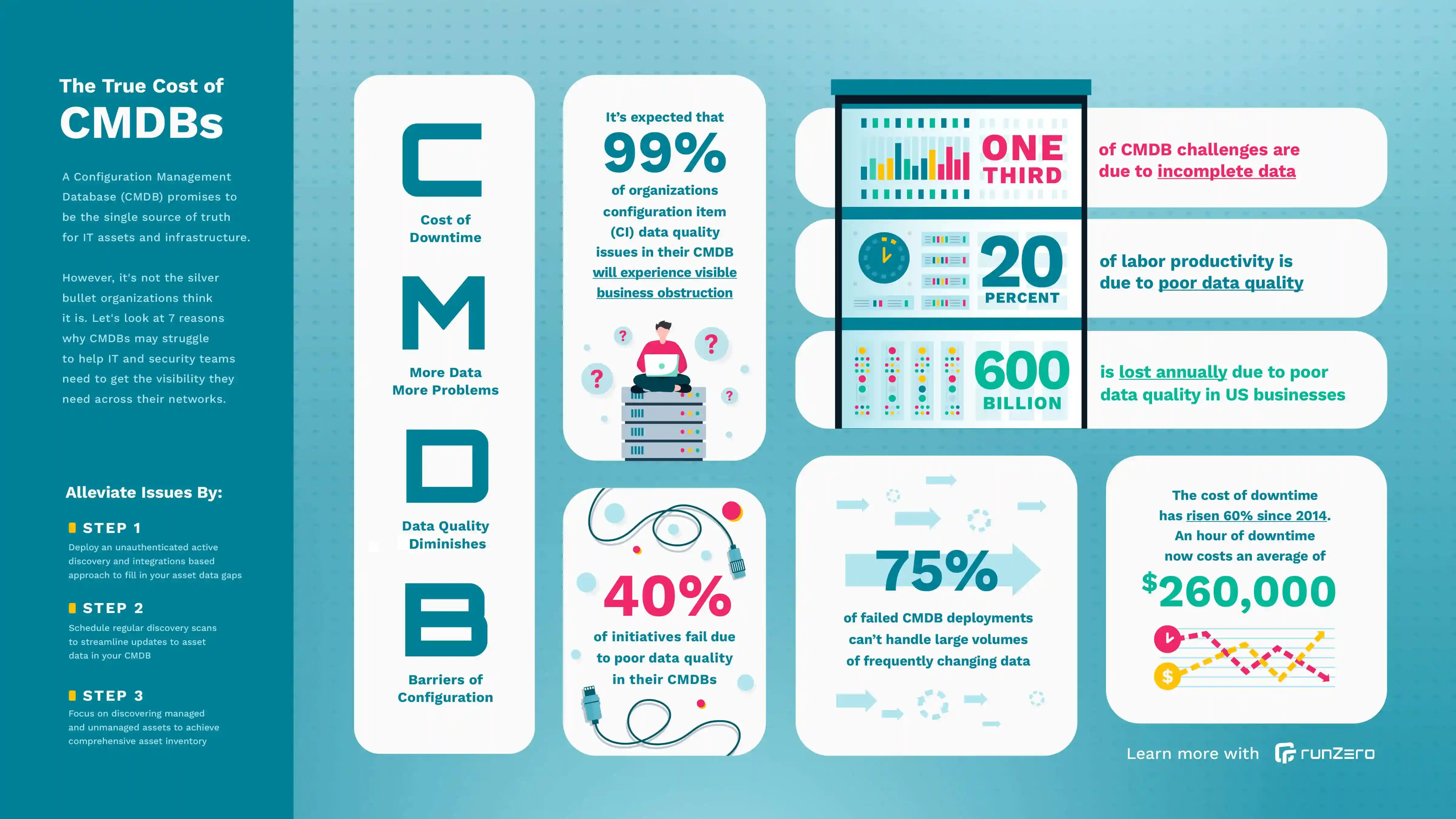
The reality does not live up to the promise, though. According to Gartner, only 25% of organizations achieve meaningful value with their CMDBs. Let’s dig into why and how a cyber asset attack surface management solution can improve the accuracy and fullness of your CMDB data.
CMDBs store data, cyber asset attack surface management discovers assets #
CMDBs track CIs but do not discover anything themselves. CMDBs learn of these CIs through a companion discovery tool which is likely not getting the information you need. Examples of these discovery tools include ServiceNow Discovery, BMC Discovery, and Atlassian Insight Discovery.
On the other hand, a cyber asset attack surface management solution discovers and maintains an accurate inventory of all assets on the network, not just IT but also IoT and OT devices. The rich data it stores on all types of assets goes beyond details relating to IT operational efficiency but also security controls, insecure configurations, vulnerabilities, and more. It’s not to be confused with ITAM, which manages the end-to-end lifecycle of assets, or ITSM, which strives to deliver IT services to end users efficiently.
Default CMDBs discovery tools cover only managed IT assets #
The majority of default CMDB discovery capabilities perform authenticated active scans against managed assets. These scans cover a limited range of devices across the IT infrastructure–including virtual machines, servers, and laptops, all managed IT. By taking the approach of relying on the CMDB’s discovery tools, you miss other critical asset types, including:
- Unmanaged devices:
These devices have slipped through the cracks due to scenarios ranging from staffing changes to updates to business strategy to mergers & acquisitions. Unmanaged devices can take many forms, including shadow IT, rogue devices, and orphaned devices. If you’re only monitoring managed devices, you’re completely overlooking unmanaged devices, so you can’t keep an eye on them. Additionally, they carry with them unknown exposure or risk. - Corporate IoT devices:
In recent years, the use of IoT devices has skyrocketed in the workplace. With this surge, organizations have even more devices to manage and secure from potential threats than ever before. From internet-connected camera systems and locks to the smart fridge in the break room and temperature and humidity management systems, these can all pose additional opportunities for hackers to fly under the radar to recon the rest of your network. With only a partial view into what’s on the network, you’re missing valuable insight for full protection. - OT devices:
Businesses in industries ranging from manufacturing and energy to government and healthcare all leverage operational technology (OT) devices. They can include field devices, programmable logic controllers (PLC), and human-machine interfaces (HMIs), vital to these businesses. These devices use real-time operating systems (e.g., Wind River VxWorks), often incompatible with the authenticated scans that log in via WMI or SSH, which you find on time-sharing operating systems like Windows and Linux. Additionally, IT and security teams often intentionally exclude OT devices from active scans because they are prone to disruption. By capturing only a portion of the assets on your network, you’re left with an incomplete asset inventory.
CMDBs aren’t trusted sources for all assets if the data is inaccurate #
Beyond incompleteness, data inaccuracy is also a major concern. If you are relying on your CMDB to be a source of truth, you need to be able to trust the information in it. The data in a CMDB will only be as good as its sources.
According to Gartner, nearly one-third of CMDB challenges stem from data completeness or quality concerns due to how data is entered into the system. There are a few input methods, but the most commonly used are manual entry and authenticated active scanning. While authenticated active scans are relatively accurate for managed IT devices, they often misidentify the hardware. Manual entry, on the other hand, does not scale and is prone to error. In fact, 60% of data manually input by employees is inaccurate.

CMDBs’ challenges around completeness and accuracy compound as asset counts continue to rise. If teams struggle to keep their CMDBs up-to-date, accurate, and therefore beneficial, then it’s not a big surprise that, according to Gartner, 80% of CMDB projects have been shown to add no value to the business.
Discover the true cost of CMDBs in the infographic below.
CMDBs powered by runZero #
If your investment in a CMDB will come up short in value and ROI, how do we avoid some of these pitfalls and improve the outlook? Use a cyber asset attack surface management solution to inform and guide your CMDB. You can make the most of your investment with both solutions working together.
runZero was purpose-built to combat the challenges and requirements of cyber asset attack surface management, which is not what default CMDB discovery tools were designed to do and why they fall short. Below are the key areas where runZero can improve your CMDB accuracy:
Full Coverage #
While the default CMDB discovery tools are effective at only capturing managed IT devices, runZero performs unauthenticated active scans to safely and quickly provide a complete and accurate asset inventory of all IT, IoT, and OT devices, whether they are managed or unmanaged.
Accurate Data #
Default CMDB discovery tools rely on authenticated scanning or manual entry as their data source, which can misidentify and miss devices not on your corporate network. They are also not purpose-built for asset inventory, so their fingerprinting falls below expectations. runZero’s source of data comes from a combination of API integrations and unauthenticated active scanning, which allows for highly accurate fingerprinting and offers real-time updates and accurate data synchronization automatically for data you can trust.
Quick Time To Value #
Discovery for CMDBs typically requires large, specialized teams following a complex process consisting of many steps for successful implementation. Alternatively, getting started with runZero involves the deployment of Explorers, after which you can run initial scans. You can get started in minutes without the hassle and time of coordinating a large team effort.
An authoritative source of asset data, including IT, IoT, OT #
runZero is a cyber asset attack surface management solution that can help you build complete, comprehensive asset inventories of your managed and unmanaged assets on any network–corporate, cloud, or home–and in any infrastructure, IT, IoT, or OT. Since runZero combines APIs with active scanning, doesn’t require credentials, and has extensive fingerprinting capabilities, it can discover and identify a wider breadth of assets with far more depth. You can integrate runZero seamlessly with CMDBs, like ServiceNow, to enrich their data, or you can leverage runZero as a standalone asset inventory solution.
runZero scales up to millions of devices, but it’s easy to try. The free 21-day trial even downgrades to a free version for personal use or organizations with less than 256 devices. Find out what’s connected to your network in less than 20 minutes.

















