The Final Beta #
Beta 6 of Rumble Network Discovery is live with a new Service Inventory, per-organization roles for team members, Site import and export, and much more!
This will be our last beta release as we focus on the official launch. If you haven't tried the platform yet, it is now better than ever thanks to the amazing feedback from our Beta community. Beta 6 is free to use until early October and all Beta participants will receive a discount code good for 50% off the first year of service. Please reach out if we can answer any questions about the platform or the upcoming launch (pricing, licensing, security, etc).
Service Inventory #
This release adds the Services tab to the Inventory. Use this interface to find configuration issues, investigate unknown devices, and explore the network from a different angle. Results can be sorted, filtered, and exported into JSON or CSV formats.
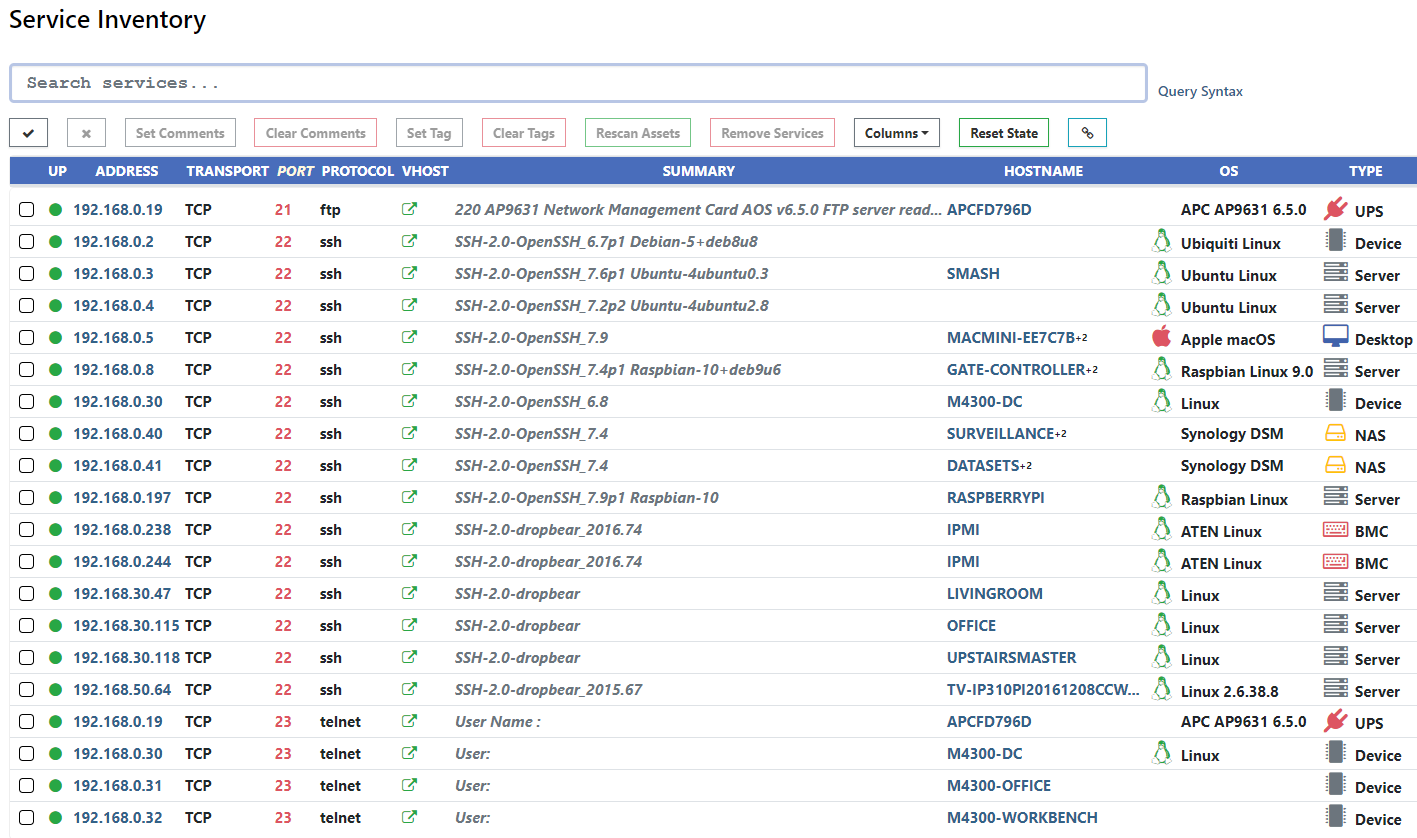
A fun example is finding all SSH servers running on a port other than 22.
Or conversely, find things running on port 22 that are not SSH servers.
To identify all systems where a screenshot was captured, the has keyword can be used.
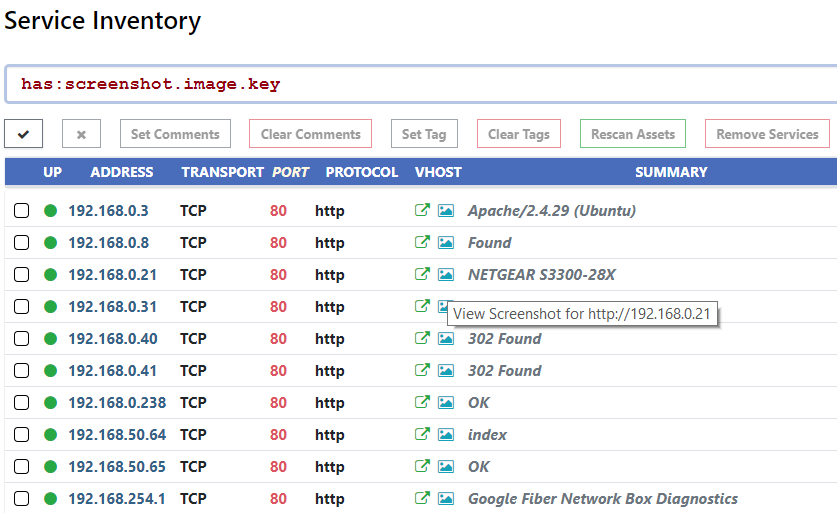
Applying the not prefix to has can identify services that are missing a specific field. The query below identifies all HTTPS services that are missing the Strict-Transport-Security header.
protocol:tls and protocol:http and not has:http.head.strictTransportSecurity
Asset service details now directly link to the inventory search, making it simple to drill down into a specific service, attribute, application, or type of asset.
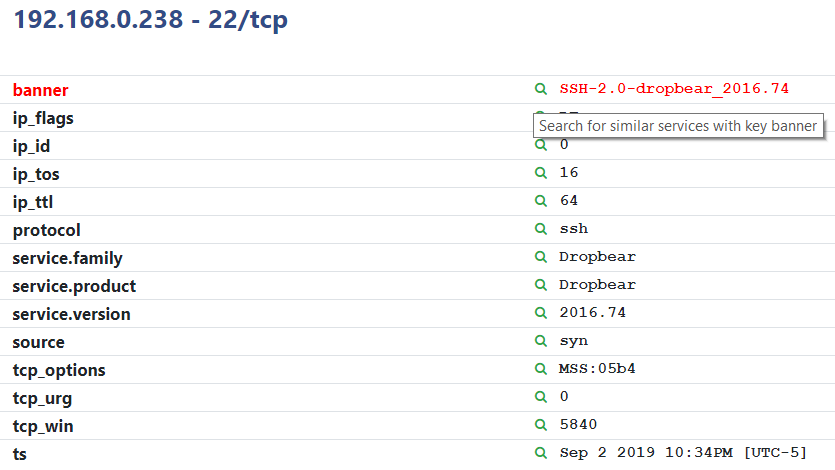
Nearly all asset search fields also apply to service searches, allowing results to be filtered by asset attributes such as operating system as well as service attributes like banners. Take a look at the updated search query syntax documentation for additional information and let us know what you think.
Teams & Roles #
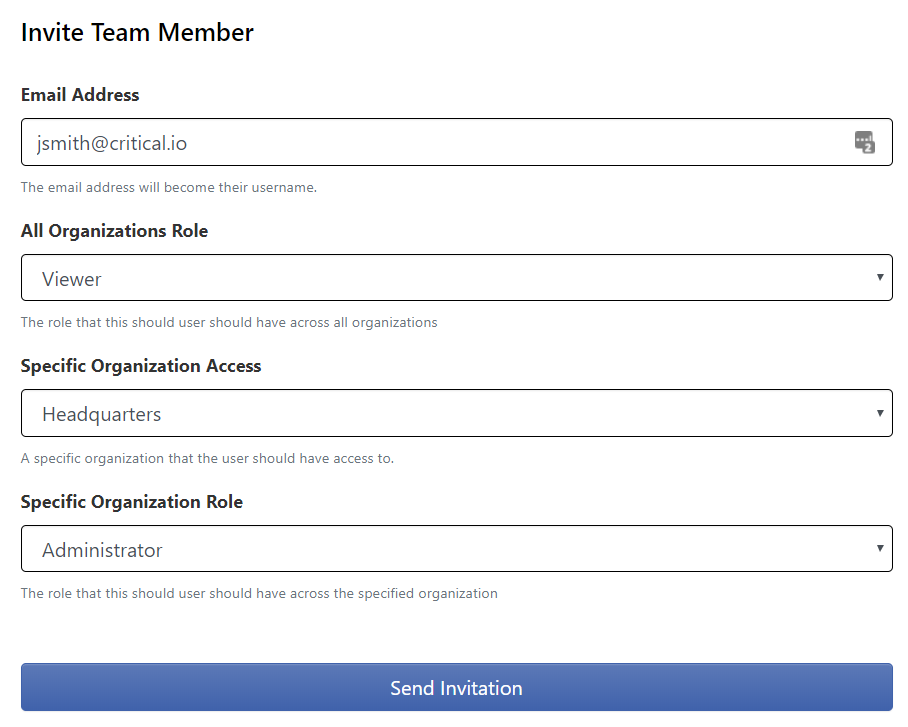
Collaborate with coworkers, create single-organization administrators, and provide view-only access to the inventory with Your Team in Rumble Network Discovery. Beta 6 adds a full permissions matrix, enabling users to have one level of access to all organizations as well as a separate per-organization role. In the example below, a new user is being configured with view access to all organizations and Administrator access to Headquarters. Roles can be used for cross-department collaboration, limiting view-only guest users to a single organization, and much more.
Rumble Agent #
The agent now reports remaining scan time, has improved protocol coverage, updated fingerprints, and bug fixes for race conditions that can occur during high-speed scans. Also a new installation screen.
runZero Scanner #
The scanner now reports the estimated time remaining, writes out a CSV file as a default artifact, and includes all the same fingerprint improvements and bug fixes as the agent. Raw IP interfaces are now supported
on Linux, including the OpenVPN tun adapter.
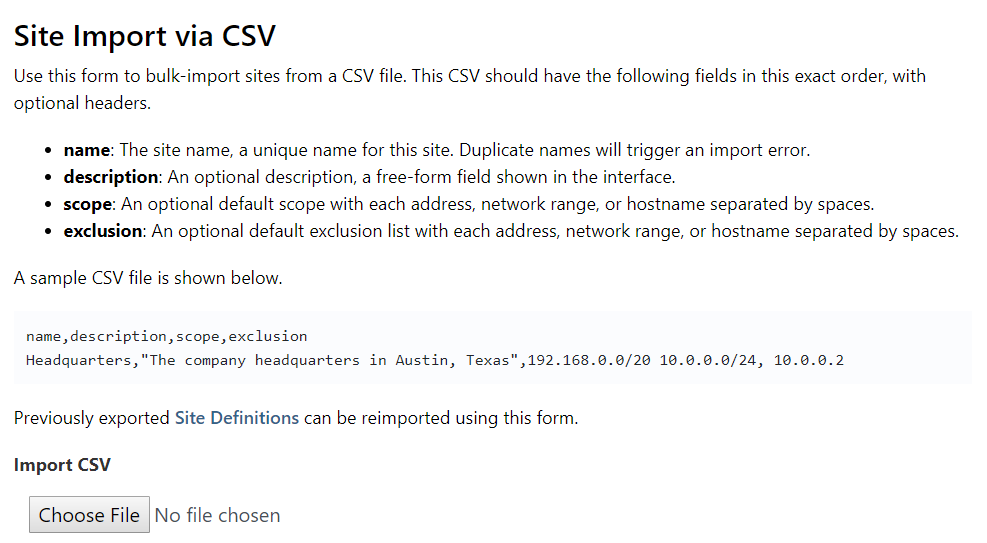
Import & Export Site Definitions #
Site definitions (name, scope, exclusions, description) can now be imported and exported from the Sites page, enabling Site creation using Excel, scripts, or an existing CMDB.
Additional Release Notes #
- Export file names now refer to the organization name, date, and search query if specified.
- Updating a recurring scan no longer triggers an immediate scan unless the schedule is changed.
- Updating a recurring scan in an error status now re-enables the scan.
- A corner case that could trigger overlapping scans has been resolved.
- TCP port ranges are now validated at scan configuration time.
- Services can now track multiple protocols per port (tls, http, http2).
- HTTP/2 services are now tracked separately from HTTP/1.
















