What is the Barracuda Email Security Gateway? #
The Barracuda Email Security Gateway (ESG) is offered as a complete email management solution. In addition to traditional email service and management, ESGs provide security-focused capabilities such as message encryption and email filtering (for catching threats and data exfiltration). ESGs exist as both physical appliances and virtual appliances.
Latest Barracuda ESG vulnerability #
Exploitation of Barracuda Email Security Gateway (ESG) appliances has made the news recently, including on-going investigation into the attacks. Leveraging a zero-day vulnerability as far back as October 2022, attackers compromised ESG targets to deploy malware that created persistent backdoor access on victim networks. This unauthorized access could have been used by attackers as a foothold for further network exploration or lateral movement, and evidence does exist that some attackers stole data via these compromised ESG targets. Barracuda identified the exploited vulnerability (known as CVE-2023-2868 with a "critical" CVSS score of 9.8) and has pushed fixes out to ESG devices worldwide, but even with these fixes, unauthorized presence on compromised networks can still exist if attackers already located and leveraged another exploitable target on the victim network. CISA has also added this vulnerability to their KEV catalog, with a BOD 22-01 due date of June 16th, 2023.
What is the impact? #
Barracuda identified a command injection vulnerability (CVE-2023-2868, CVSS score 9.8) that exists in ESG versions 5.1.3.001 through 9.2.0.006. Due to ineffective input sanitization, a specially crafted tar archive file can be sent to vulnerable ESG targets to trigger unauthorized command execution as the ESG user. While Barracuda has made software updates available, the possibility that attackers used exploited ESG targets to pivot to – and potentially establish persistence on – other systems in a victim network is a real threat.
Are updates available? #
UPDATE: As of June 6, 2023, Barracuda is recommending immediate replacement of impacted ESG appliances regardless of their software patch level.
On May 20th, Barracuda pushed out a fix to all ESGs worldwide. This was followed by a script pushed out on May 21st to "contain the incident and counter unauthorized access methods." Barracuda continues to push security patches as part of their containment strategy. Owners or admins of Barracuda Email Security Gateway appliances should verify their ESG instances are accepting and applying current updates being sent out by Barracuda, and can also check for indicators of compromise.
How do I find potentially vulnerable Barracuda Email Security Gateways with runZero? #
From the Asset inventory, use the following prebuilt query to locate all Barracuda Email Security Gateway instances in your network:
hw:"Barracuda Email Security Gateway"
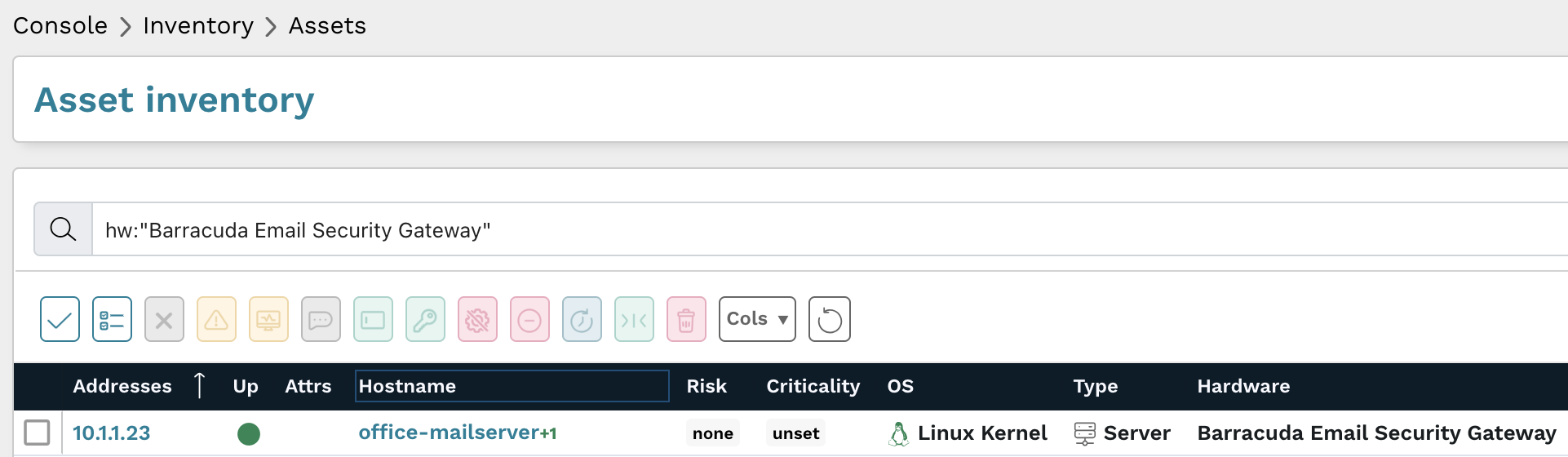
Results from the above query should be triaged to verify they are running Barracuda's latest patches.
As always, any prebuilt queries are available from your runZero console. Check out the documentation for other useful inventory queries.
















