We are thrilled to announce the general availability of Rumble Network Discovery!
This release is the result of six months of beta testing by nearly 3,000 users tracking almost 3,000,000 assets. We feel like the product is finally taking shape and are more excited than ever to tackle the problem of unauthenticated network discovery and asset inventory.
A HUGE thanks to our beta community for their relentless (and awesome) feedback about every part of the product, from specific network probes to the look and feel of the inventory. This feedback has driven our development process and helped us define the roadmap ahead.
For those who have already subscribed or started the purchasing process, we really appreciate your support, and are looking forward to working with you as we continue to improve the platform.
If you haven't had a chance to try runZero before, or just haven't seen a recent version, we recommend signing up for a free trial and taking this release for a spin.
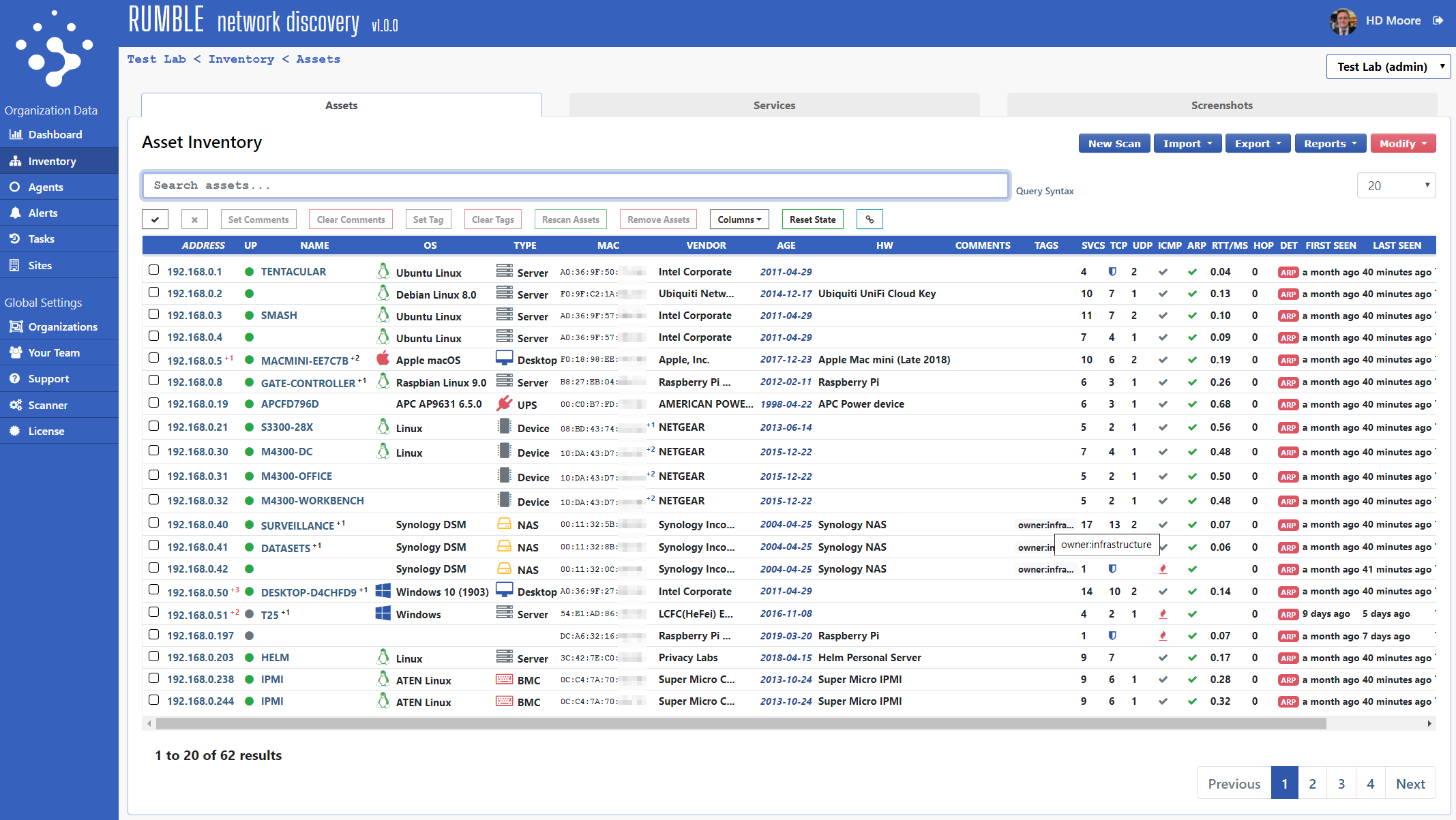
Release Notes Since Beta 6 #
-
Rumble scans now pull the ARP cache, MAC table, and VLAN table of SNMP v2 network devices when a community string is available (or the device responds to public). This feature allows Rumble to obtain even more MAC addresses from routed networks. ARP entries found in another device's cache are noted in the
sourcefield of the ARP service. -
The Inventory now offers a Screenshots tab that can be sorted by image size (the screenshots column). This makes it easy to browse all screenshots quickly. A gallery-mode experience can be achieved removing all columns from the table except for the screenshot itself.
-
Rumble now uses an
IPSEC IKEprobe to identify responsive hosts. This helps find even more devices, especially VPN gateways with minimal services exposed. -
The Rumble agent now reports additional data about scans as they are running. This includes finer-grained estimate of the completion time, the total runtime, and the number of datapoints gathered so far.
-
Asset correlation now takes into account SMB computer names and TLS certificates for RDP when deciding whether a newly found asset matches an existing entry. This should result in less churn for DHCP environments with short leases.
-
Asset correlation now looks at a broader set of TCP/IP stack fingerprints when determining whether an IP-based match is credible. This should result in less churn for highly-filtered environments (many external networks).
-
Rumble now intentionally skips sending probes to and reporting results from network broadcast addresses. The benefits of identifying a few extra systems were outweighed by buggy behavior by certain networking equipment.
-
Security improvements were made in response to our first third-party security assessment.
-
Bug fixes for occasional deadlocks in the runZero Scanner (CLI).
















